CEN/XFS SP implementation method and device based on security authorization and financial self-service equipment
An implementation method and security technology, applied in computer security devices, complete banking systems, complete banking systems, etc., can solve problems such as bank cash loss, loss of important credentials, etc., to prevent attacks, ensure security, and prevent people from being arbitrarily tampering effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
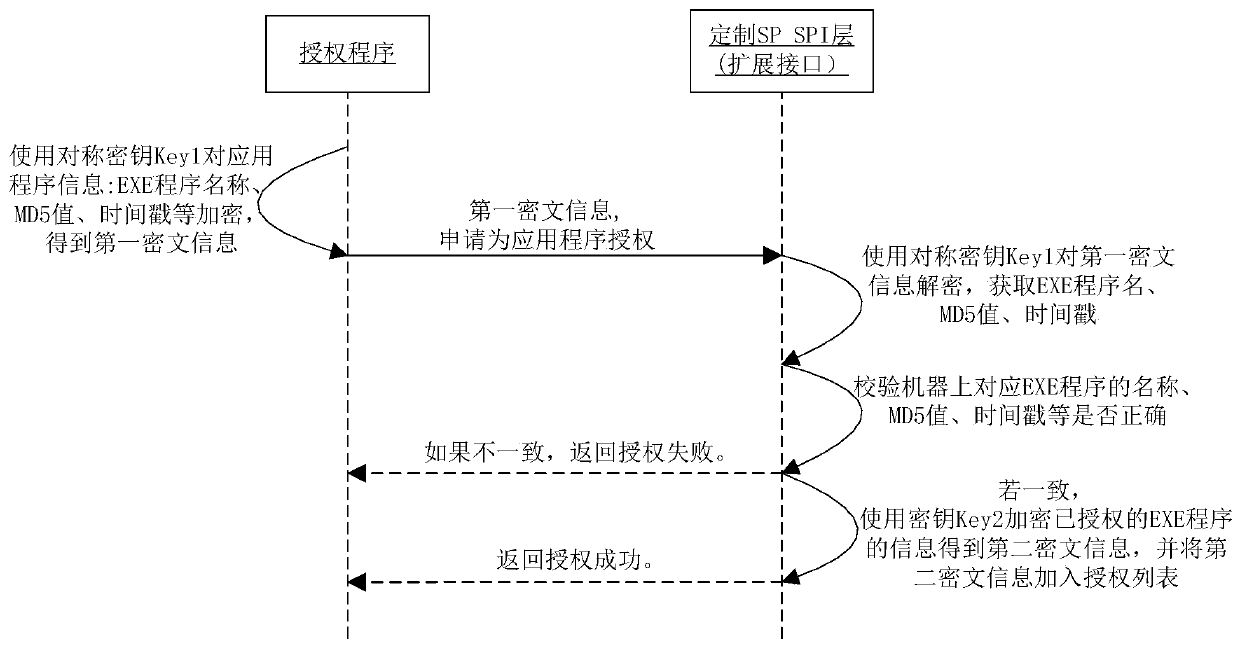
[0078] First of all, a special authorization tool selects the application program under the corresponding path, and registers the EXE information by calling the extended interface of the SP SPI interface layer, that is, performs security authorization for the application program, and authorizes the information of the legal application program through the encrypted The method is stored in the authorization list.
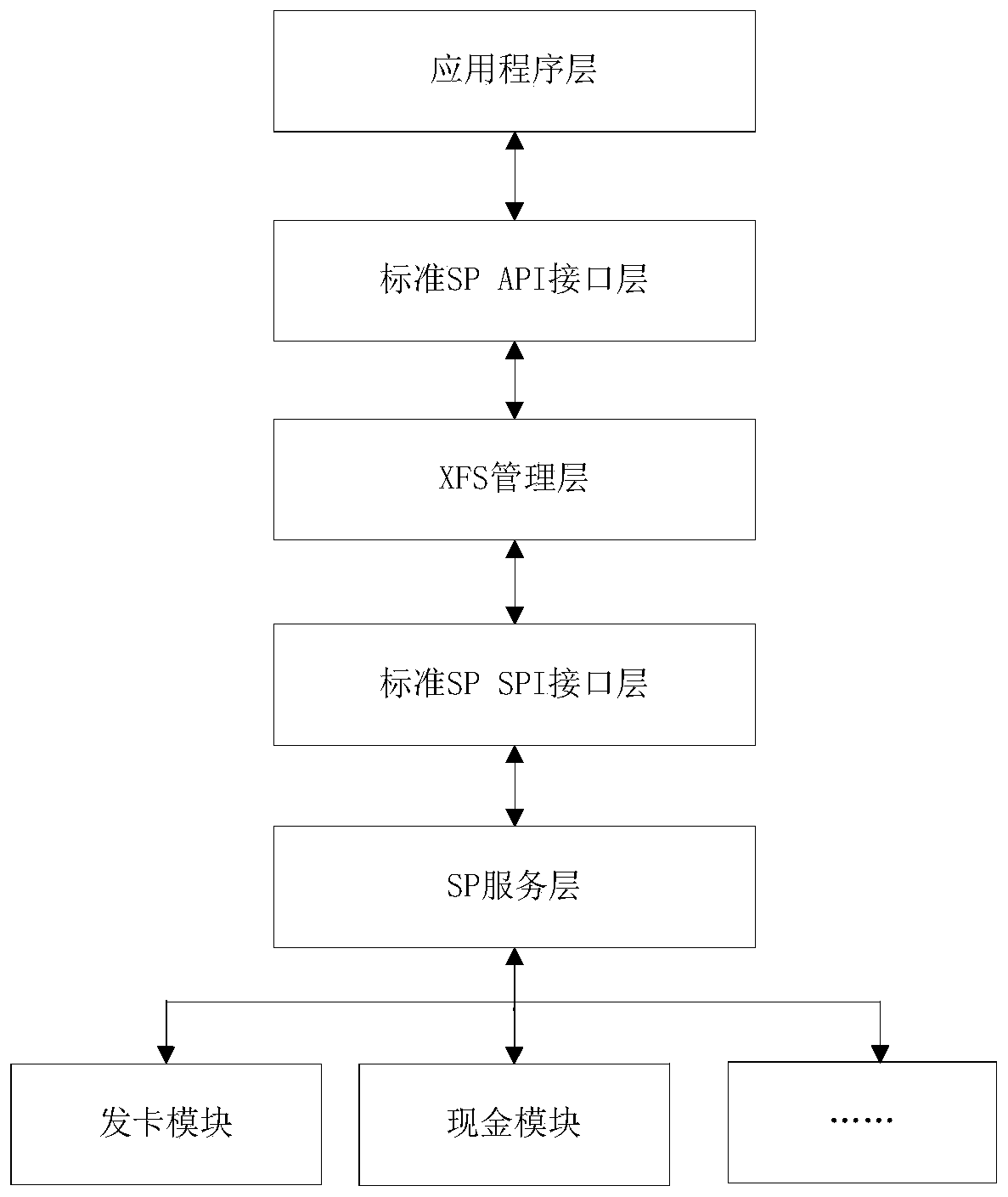
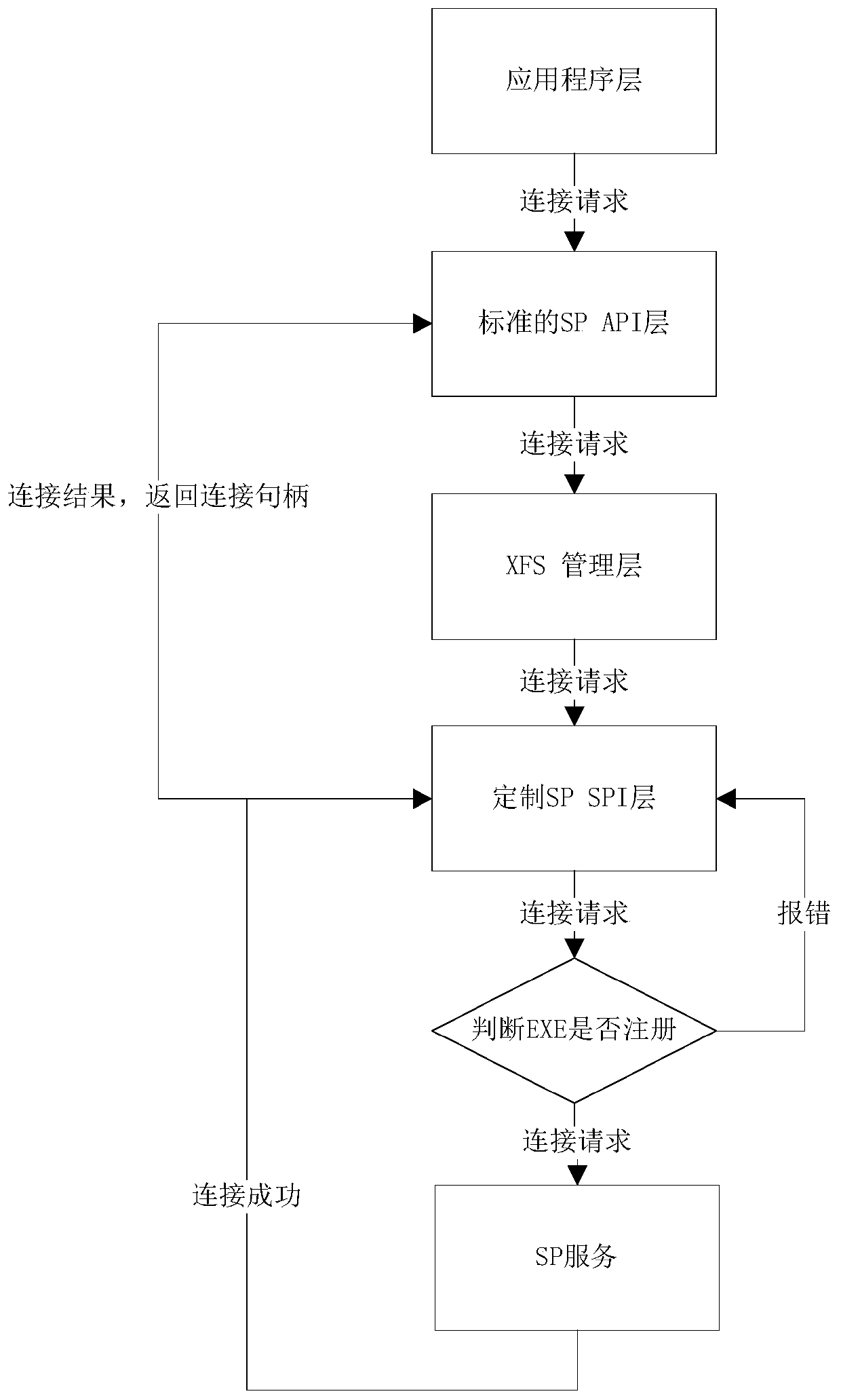
[0079] Then, the application layer calls and connects to the SP service, and the SP SPI interface layer judges whether there is an application program for calling and connecting to the SP service in the authorization list, and if it exists, it continues to call the SP service, otherwise it refuses to report an error;
[0080] Wherein, the application layer invokes the connection SP service, and the application sends the connection request to the SP SPI interface layer through the standard SP API interface layer. If the connection operation is successful, the SP SPI in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com