Gateway protection method and device, computer equipment and storage medium
A gateway and message data technology, which is applied in the field of information security, can solve problems such as security risks and violent attacks, and achieve the effect of ensuring non-tampering and information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0041] Embodiment one
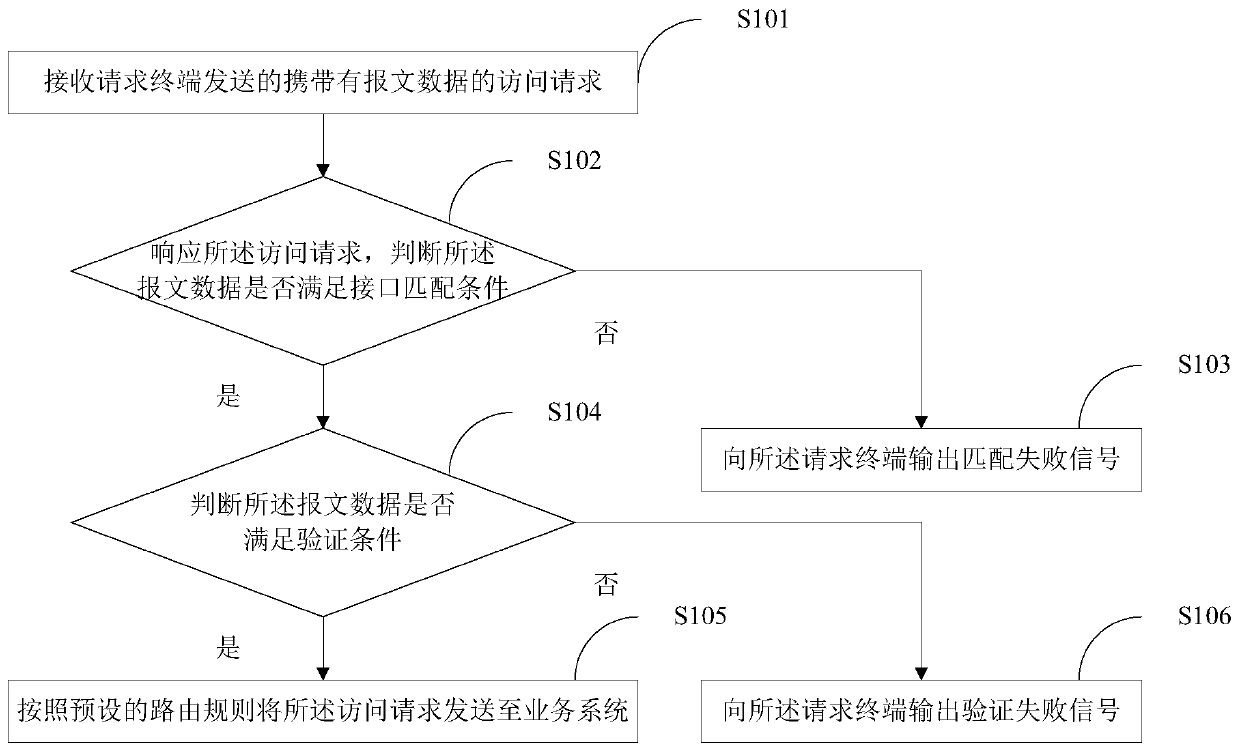
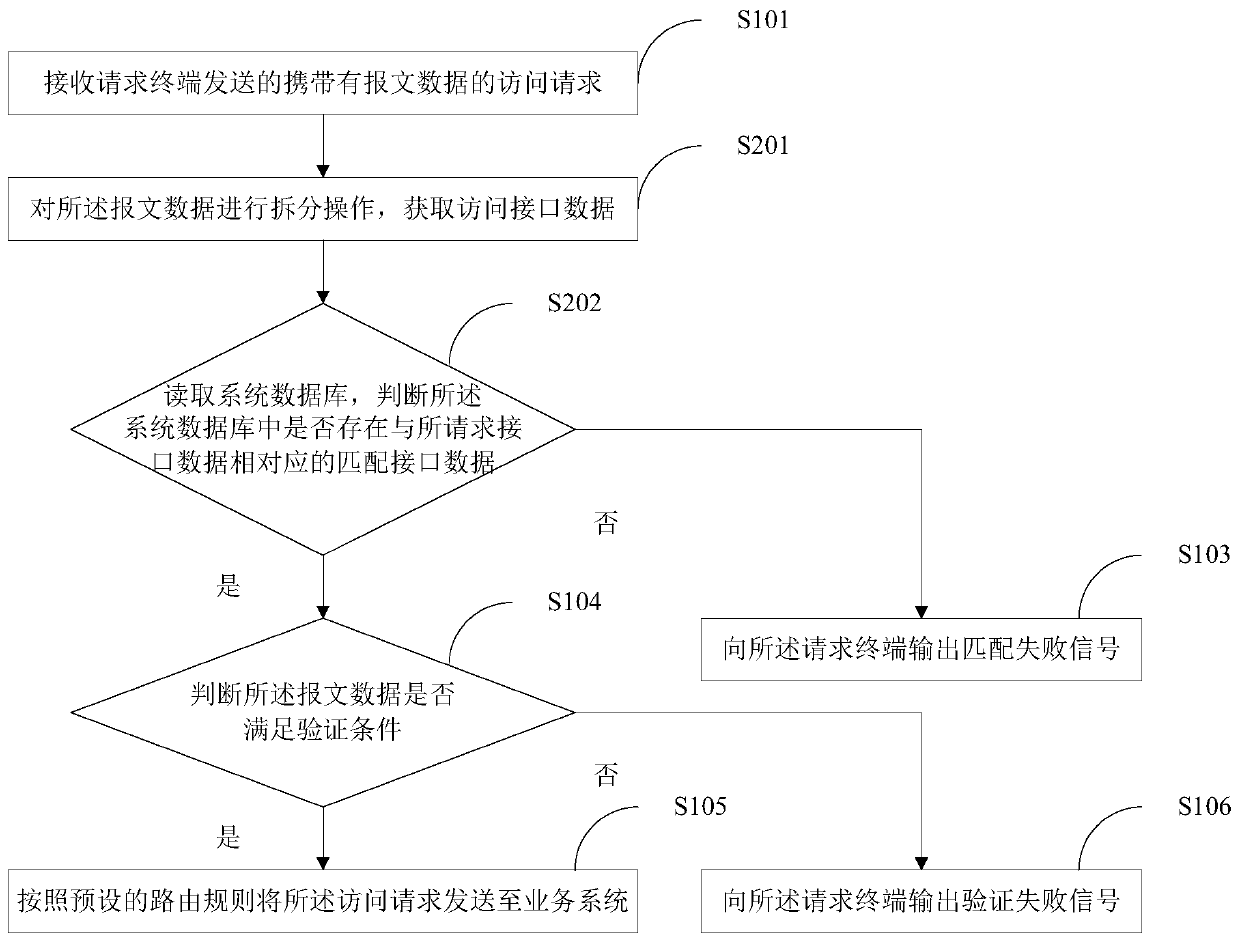
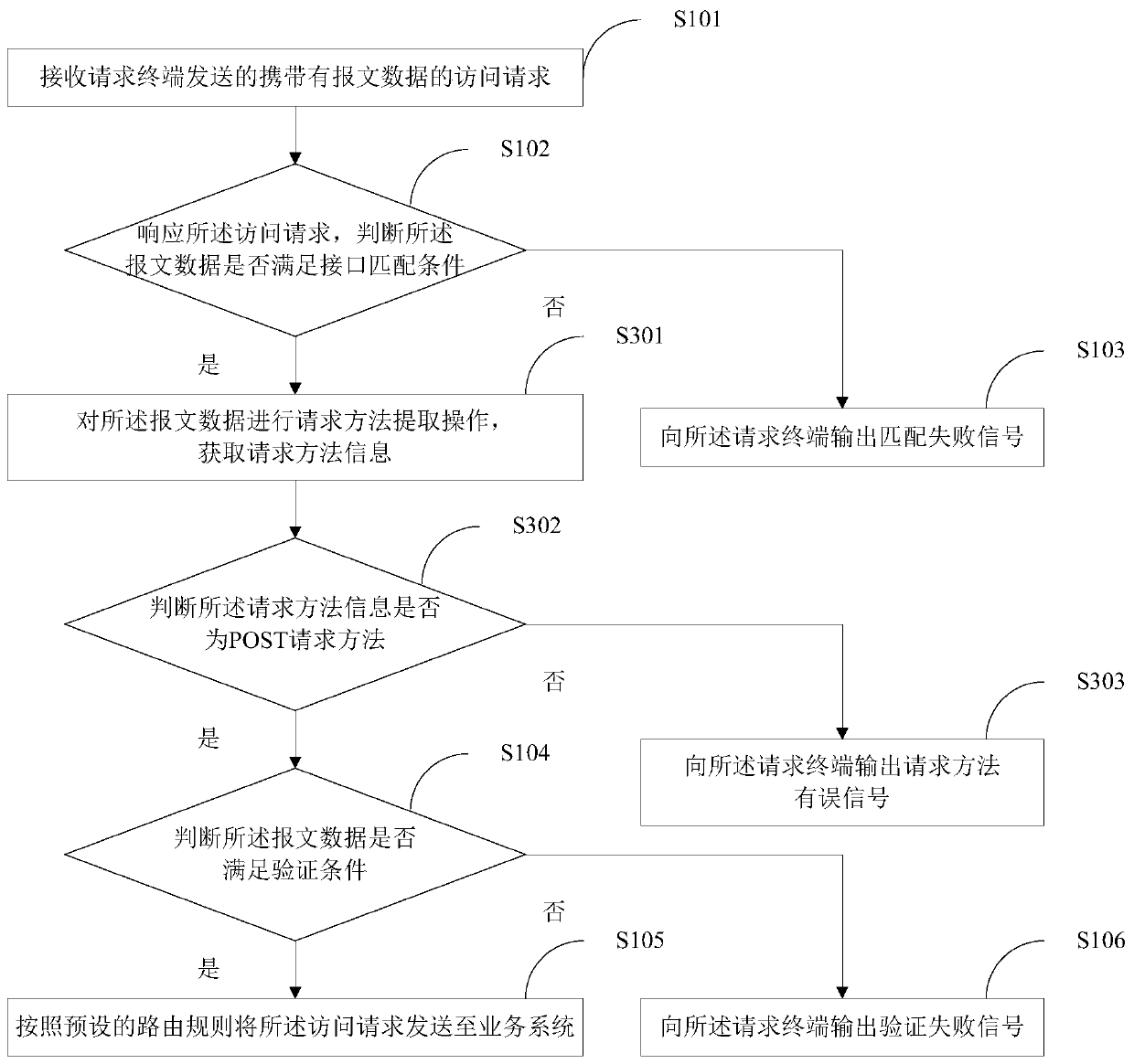
[0042] figure 1 A flow chart of the implementation of the gateway protection method provided by Embodiment 1 of the present invention is shown, and for convenience of description, only parts related to the present invention are shown.
[0043] In step S101, an access request carrying message data sent by a requesting terminal is received.
[0044] In the embodiment of the present invention, the requesting terminal may be, for example, a mobile phone, a smart phone, a notebook computer, a digital broadcast receiver, a PDA (personal digital assistant), a PAD (tablet computer), a PMP (portable multimedia player), a navigation device, etc. It should be understood that the example of the requesting terminal here is only for convenience of understanding, and is not used to limit the present invention.
[0045] In the embodiment of the present invention, message data refers to an information carrier that is used to exchange information when requesting and re...
Example Embodiment
[0110] Embodiment two
[0111] further reference Figure 7 as to the above figure 1 The realization of the method shown, the application provides a gateway protection device, the device embodiment and figure 1 Corresponding to the illustrated method embodiments, the apparatus can be specifically applied to various electronic devices.
[0112] such as with Figure 7 As shown, the gateway protection device 100 provided by Embodiment 2 of the present invention includes: a request receiving module 101 , an interface matching module 102 , a matching failure module 103 , a signature verification module 104 , a verification success module 105 and a verification failure module 106 . in:
[0113] The request receiving module 101 is configured to receive an access request carrying message data sent by the requesting terminal;
[0114] The interface matching module 102 is used to respond to the access request and determine whether the message data meets the interface matching condit...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap