Storage device data integrity protection method, controller thereof and system on chip
A technology of data integrity and storage device, applied in the computer field, can solve problems such as difficulty in resisting hacker attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
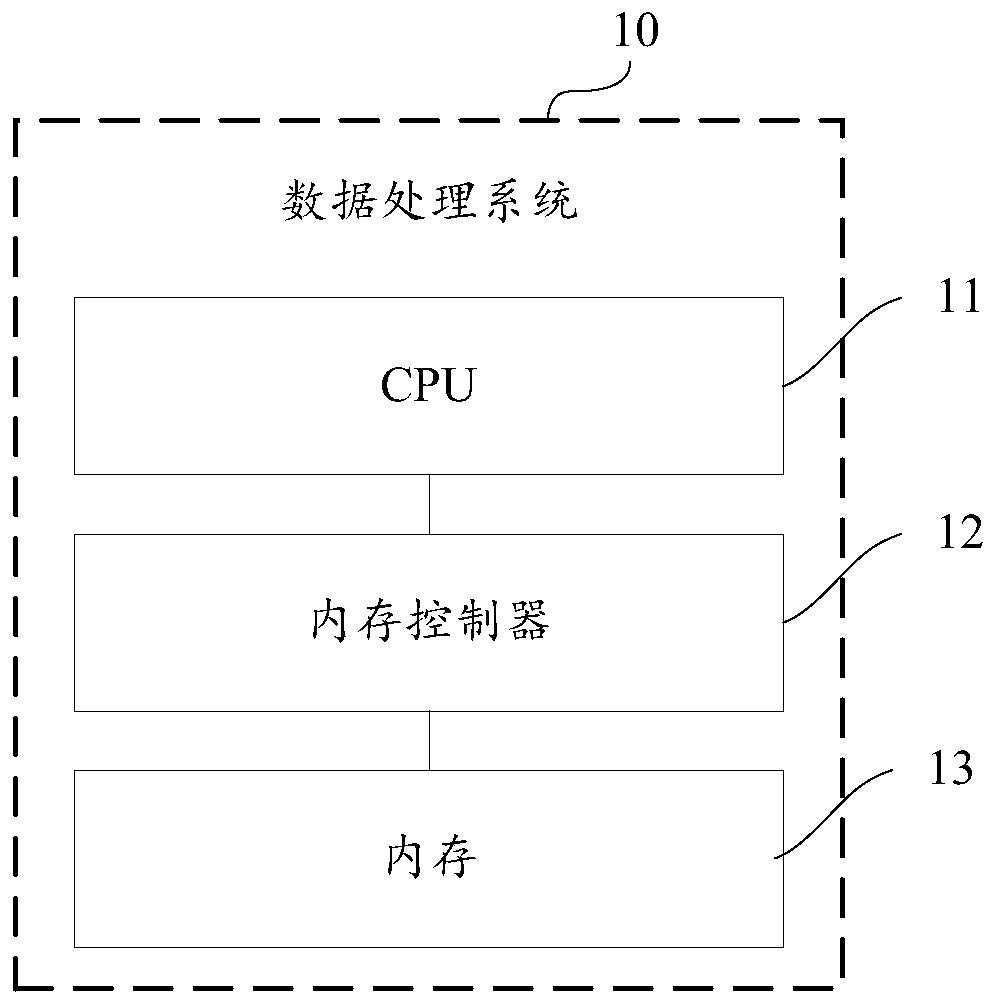
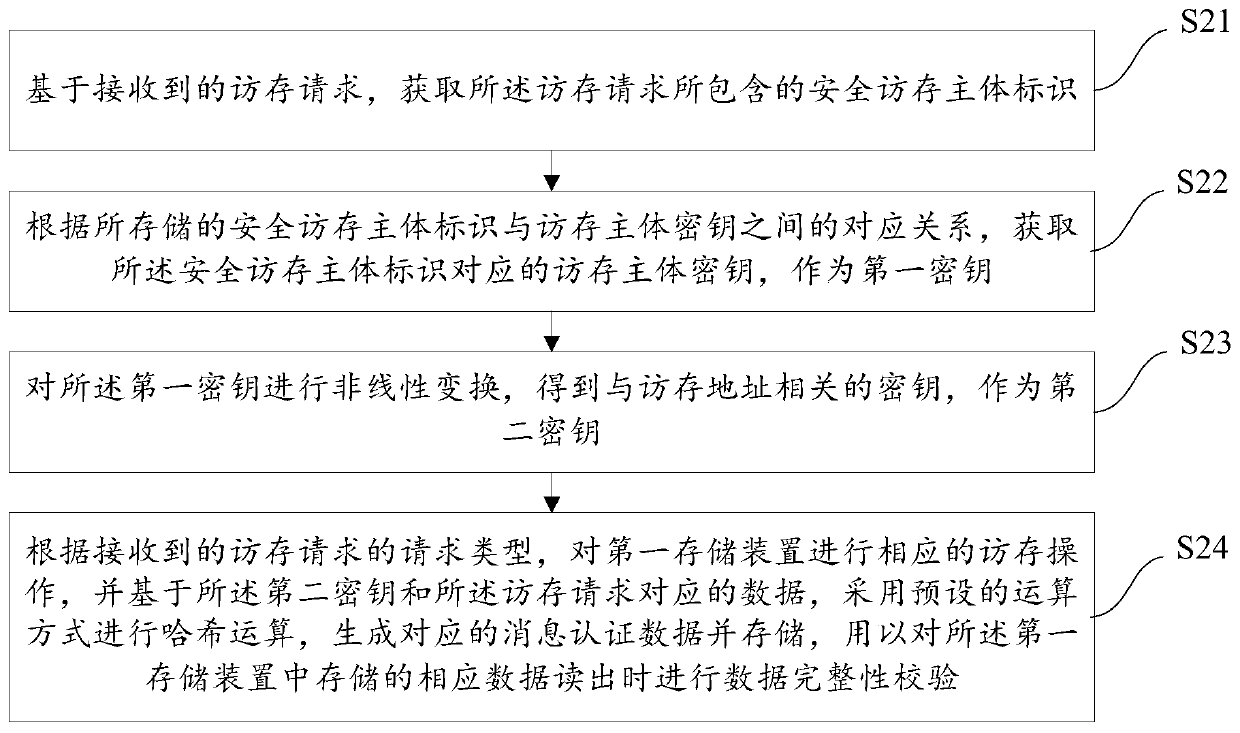
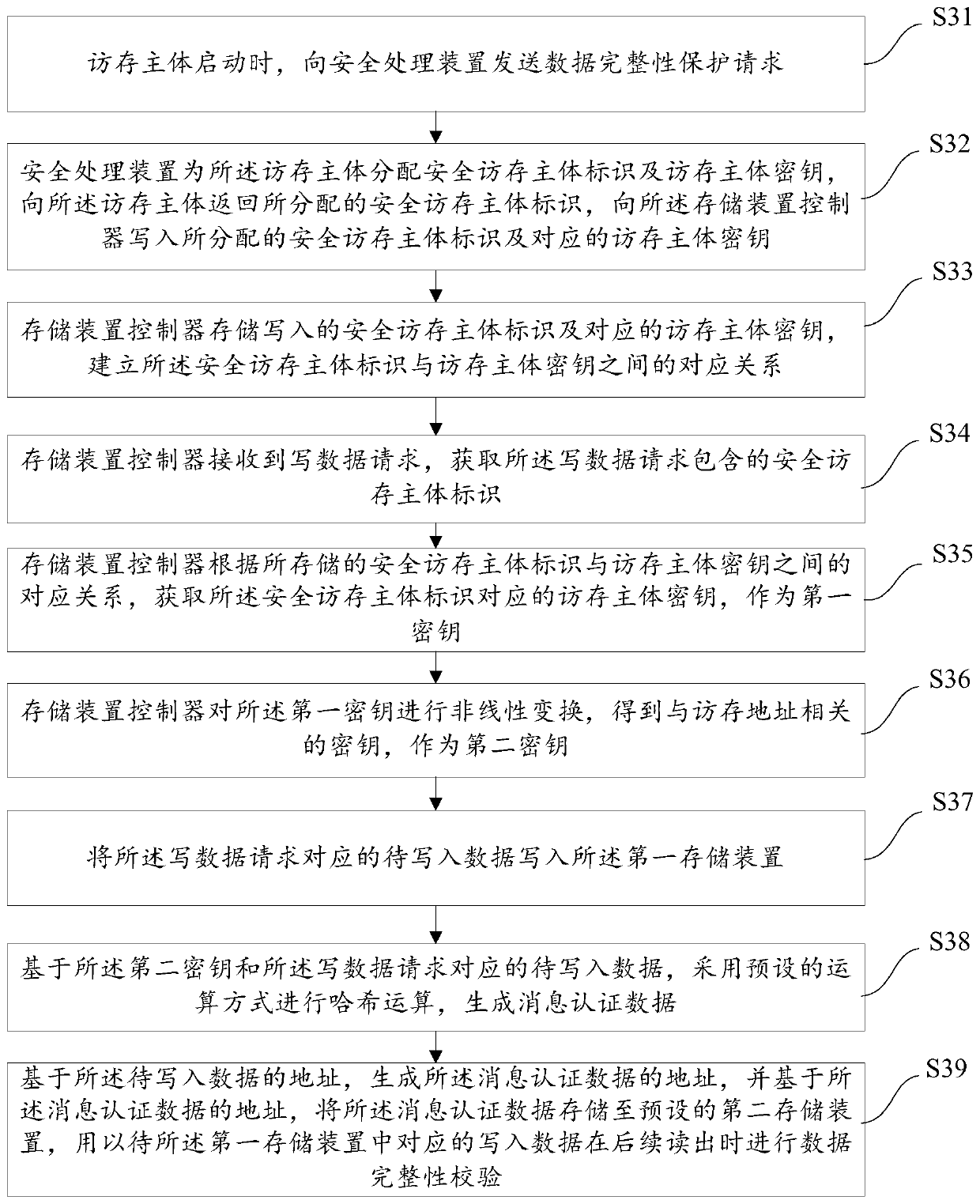
[0082] As described in the background, after the CPU data is written into the storage device, there is a risk of being tampered with. refer to figure 1 A schematic structural diagram of a data processing system is shown. The data processing system 10 includes: a CPU 11 , a memory controller 12 and a memory 13 . After the data in the CPU 11 is written into the memory 13, hackers can use the RowHammer method or physical hardware attacks to tamper with the data written in the memory 13 without the knowledge of the CPU 11, thereby maliciously invading the virtual memory. machine data purposes. Among them, the RowHammer method repeatedly accesses a row of memory, which may cause bit flips in adjacent rows, that is, hackers can change the value of the bit in the memory. When running on a machine vulnerable to the RowHammer attack, the process is able to gain read and write access to all physical memory, allowing it to arbitrarily tamper with data in all physical memory.
[0083] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com