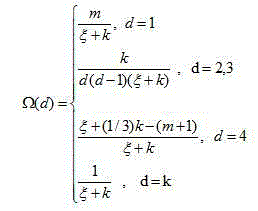Patents
Literature
70results about How to "Reduce bandwidth overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
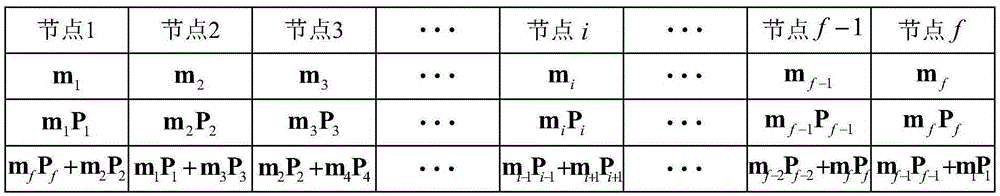
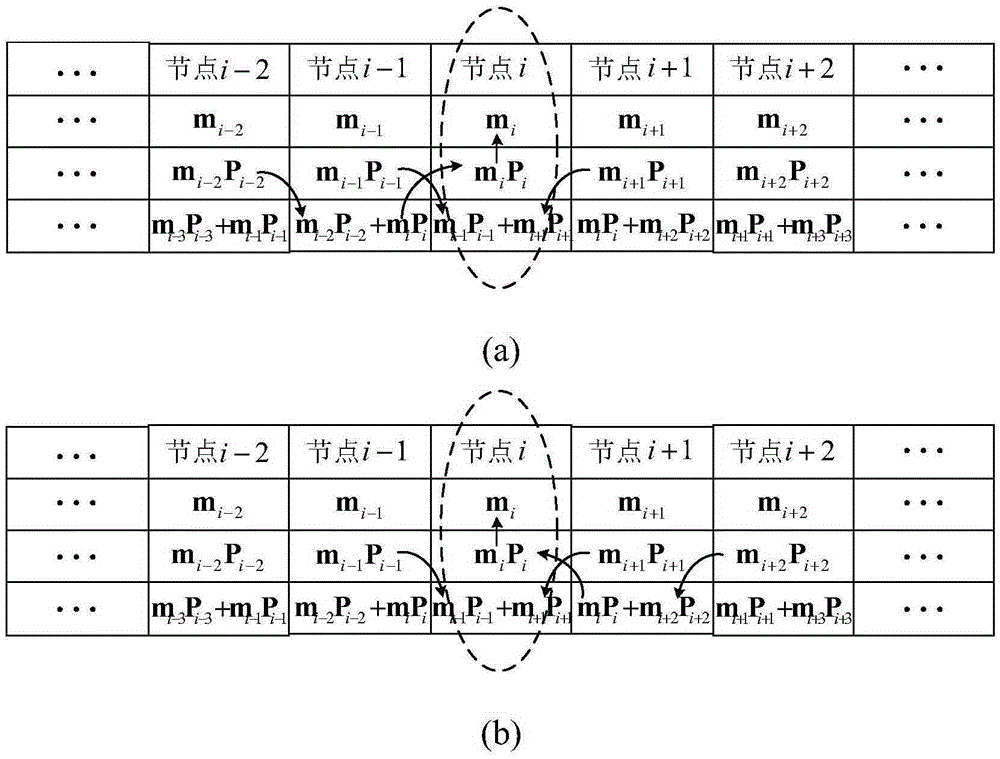
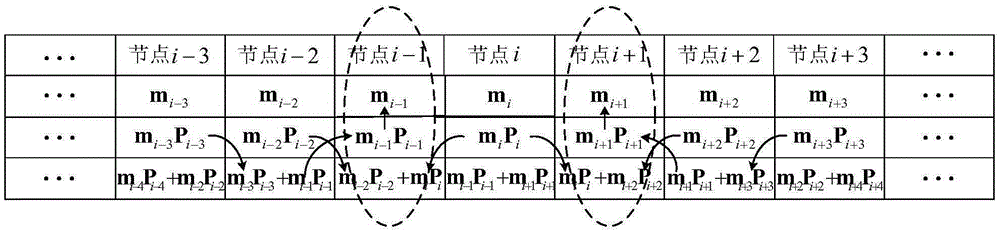
System minimum storage regeneration code based local repair encoding method
InactiveCN105260259AIncrease overheadReduce overheadRedundant data error correctionOriginal dataData reconstruction
The invention discloses a system minimum storage regeneration code based local repair encoding method. The local repair encoding method comprises: constructing a storage structure and a generation matrix of a system minimum storage regeneration code; establishing a local repair encoding structure based on the system minimum storage regeneration code; and repairing a single-node fault, a two-non-adjacent-node fault and a two-adjacent-node fault in a repair group by adopting the established local repair encoding structure. According to the local repair encoding method, the system minimum storage regeneration code is adopted as a local code, and storage nodes store original data copies, so that the disk I / O expenditure and the bandwidth repair expenditure in a storage node repair process are reduced; and a redundant data part in the storage nodes is generated by minimum storage regeneration encoding data parts of two successive storage nodes, and based on the encoding structure, when the single-node fault, the two-adjacent-node fault and the two-non-adjacent-node fault exist in the repair group, fault node data reconstruction can be quickly realized through the successive nodes to recover fault node data.
Owner:CHANGAN UNIV
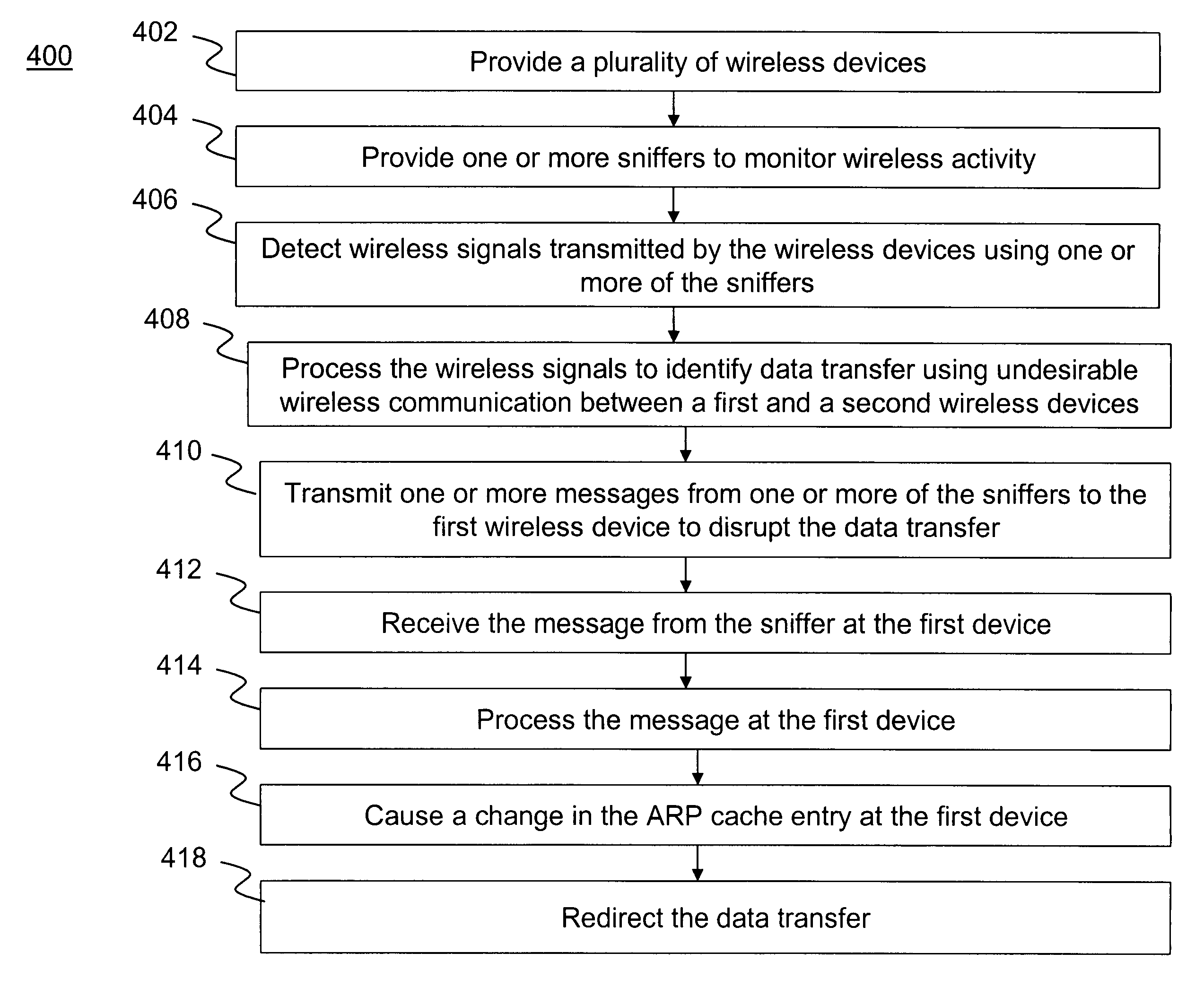
Method and system for disrupting undesirable wireless communication of devices in computer networks
ActiveUS7333481B1Easy to usePrevent channel hopping and access point hoppingDigital data processing detailsUser identity/authority verificationData transmissionAddress Resolution Protocol
A method for disrupting unauthorized communications between at least two communication devices is provided. The method comprises using an address resolution protocol (ARP) to redirect transfer of data that occurs using unauthorized wireless communication between a first wireless device and a second wireless device. In a preferred embodiment, the method maintains a layer two wireless link while the data are being redirected.
Owner:ARISTA NETWORKS
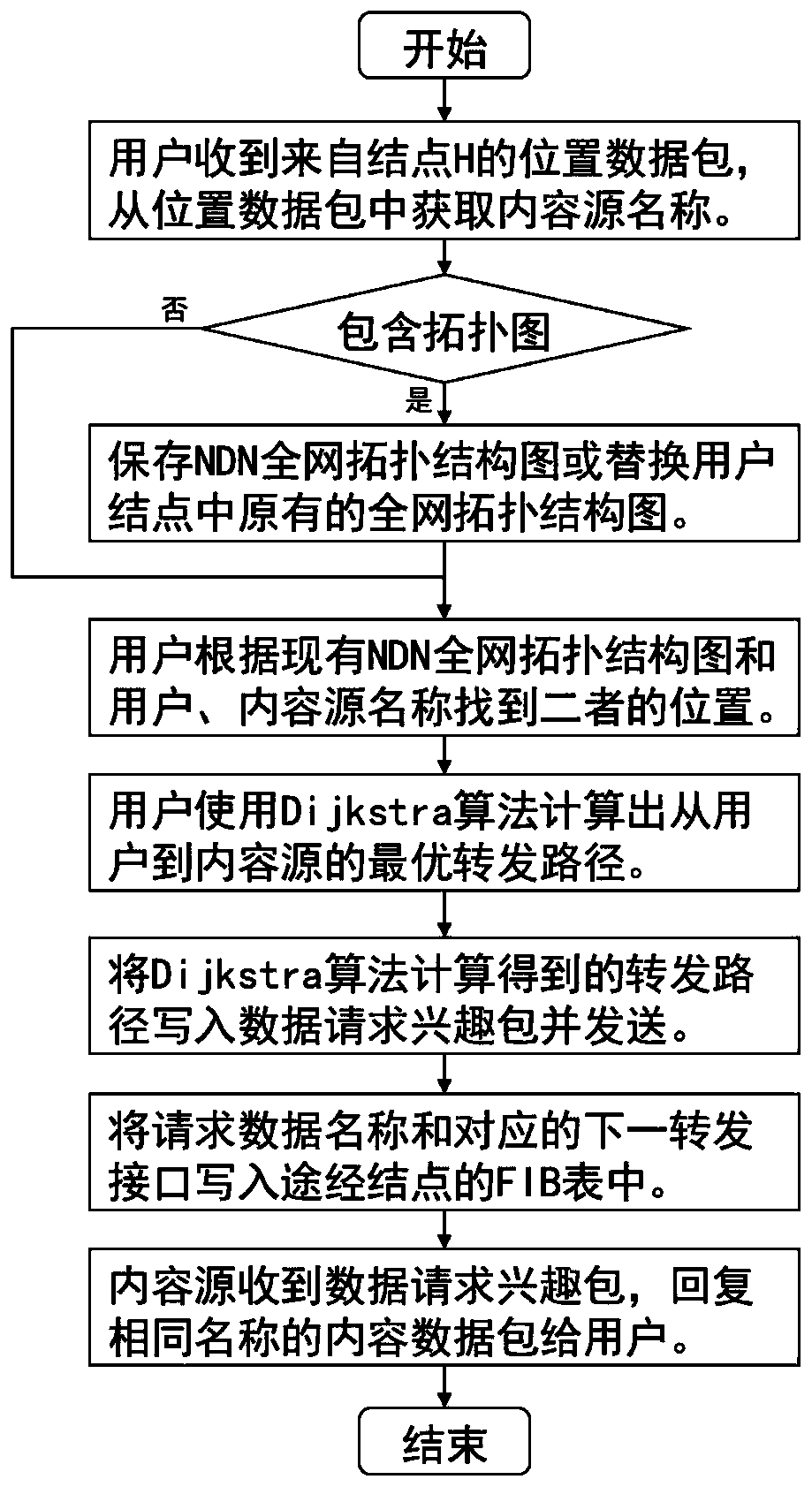
Named data network comprehensive routing method based on position information and content pushing
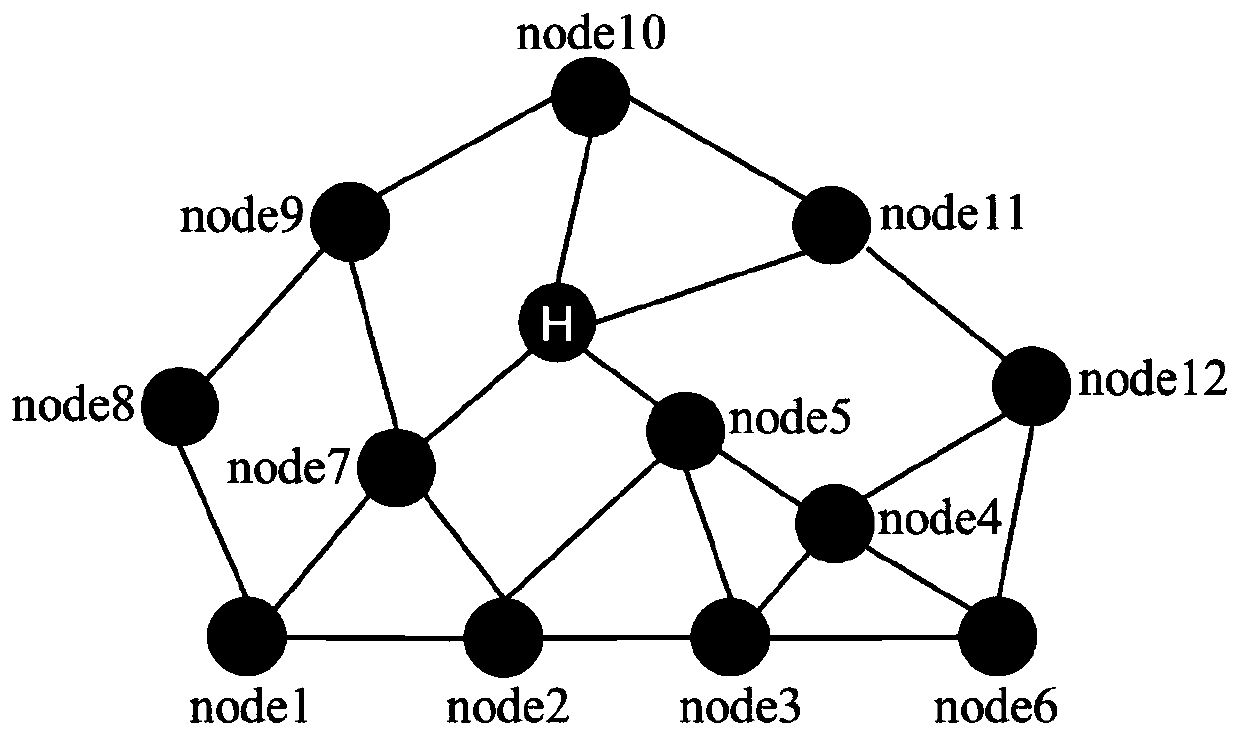
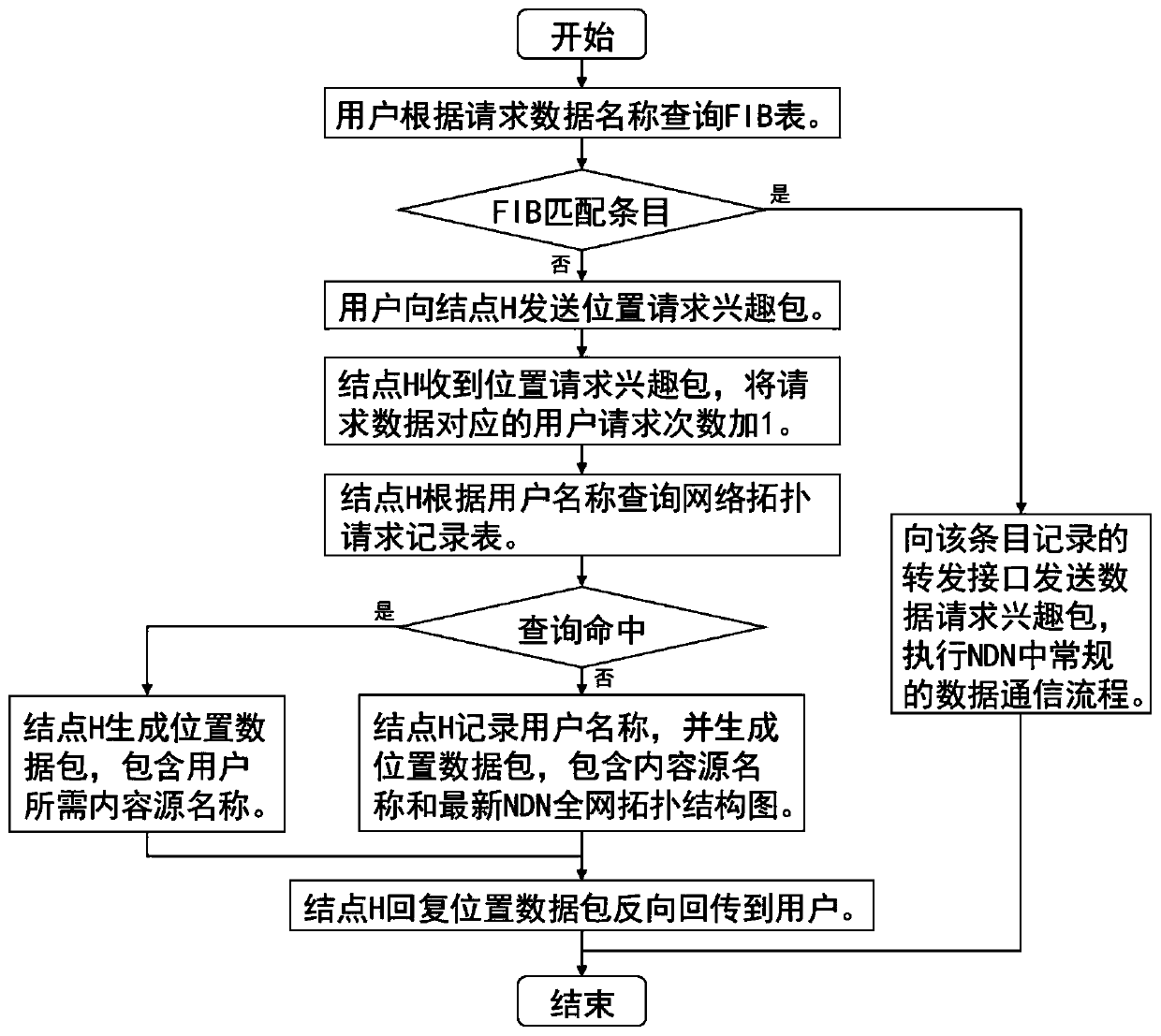
ActiveCN110149274AReduce complexityReduce bandwidth overheadData switching networksNetwork managementStructure chart
The invention relates to a named data network comprehensive routing method based on position information and content pushing, and belongs to the technical field of computer network routing optimization. The method comprises: arranging a network management server, determining the link state of each node and starting a link state timer; establishing an NDN whole network topological structure chart and starting a network topological timer; establishing a network topology application record table; establishing a matching list of the whole network data name and the content source name and startinga statistical interval timer; the user sending a position request interest packet and the network management server replying the position data packet; a user calculating a forwarding path and sendinga data request interest packet and a content source reply content data packet, a network management server evaluating data popularity and a content source pushing data name to supplement an FIB tableof an NDN node, and regularly detecting a link state to update a network topology and pushing a high popularity data name. The method is relatively low in complexity and relatively low in bandwidth overhead, and can realize rapid establishment of the FIB table and efficient forwarding of the interest packet.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
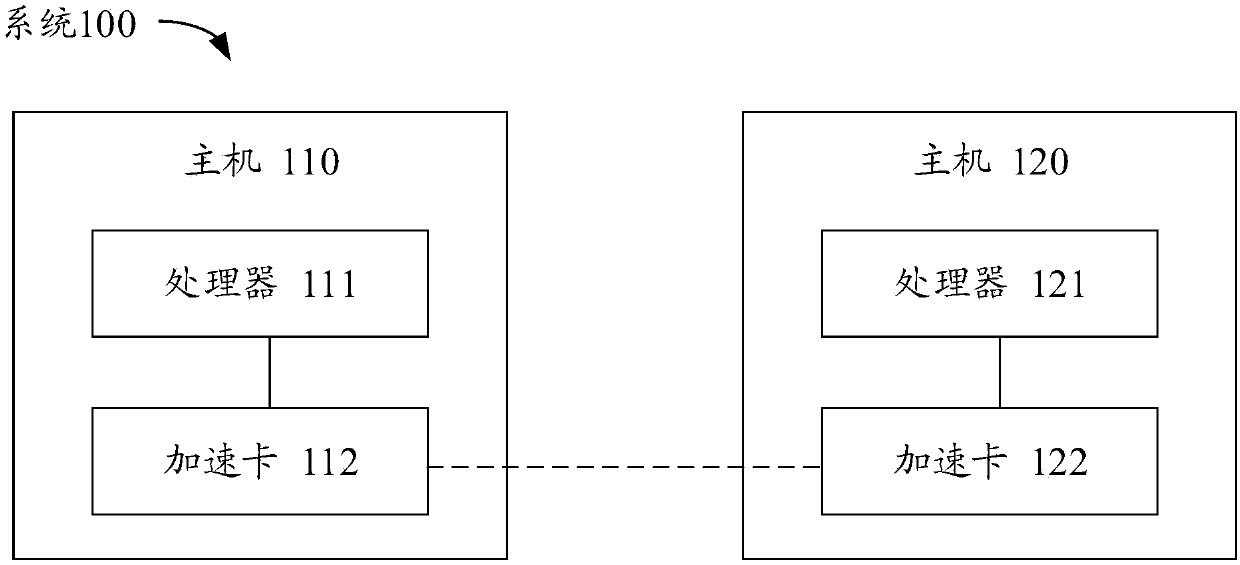
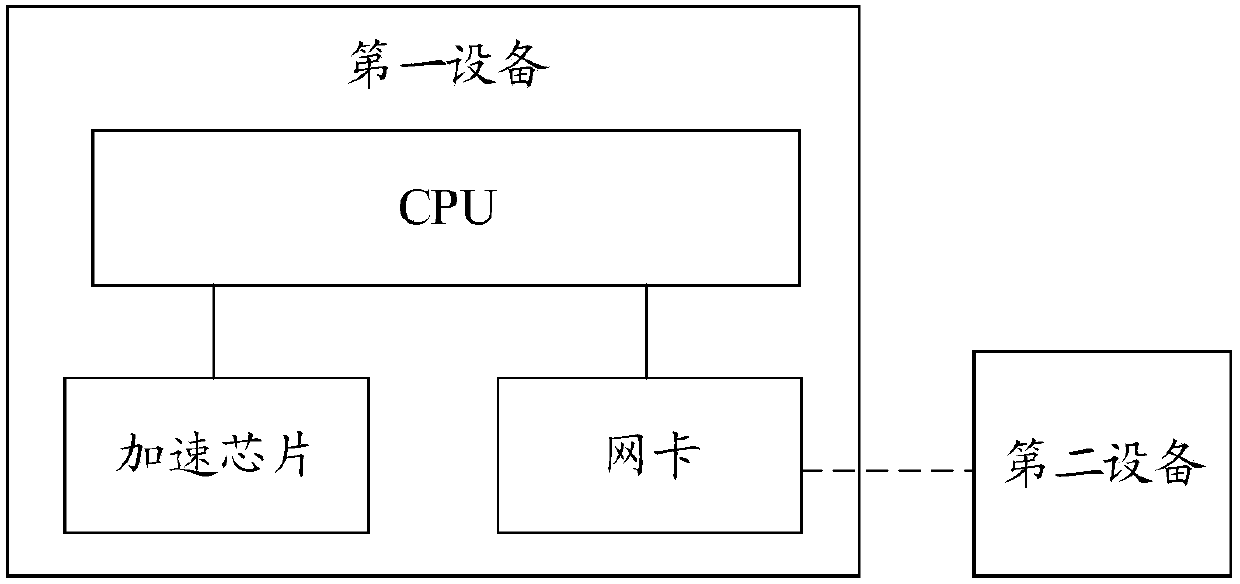
Message transmission method and device
ActiveCN109714292AReduce the number of round tripsHighlight the acceleration effectTransmissionData delayEncryption
The invention provides a message transmission method and device. The method is applied to first equipment provided with an acceleration card and a processor. According to the method, bandwidth overhead and data delay caused by transmission can be reduced, the method comprises the steps that an acceleration card receives a first transmission layer control protocol (TCP) message from a processor, to-be-encrypted data are carried in the first TCP message, and the to-be-encrypted data belong to secure socket layer (SSL) data; encryption information used for encrypting the first TCP message is determined according to a pre-acquired mapping relation, the mapping relation indicates a corresponding relation between an identifier of a TCP connection bearing the SSL data and encryption and decryption information, and the encryption information at least comprises an encryption algorithm and an encryption parameter; to-be-encrypted data carried in the first TCP message is encrypted according to the encryption information to obtain a second TCP message, the second TCP message is the encrypted first TCP message; And the second TCP message is sent to the second device.
Owner:HUAWEI TECH CO LTD
Application layer session routing
ActiveUS20150229562A1Reduced resourceSession routing is performed quicker and more efficientlyError preventionTransmission systemsTransit networkSession control
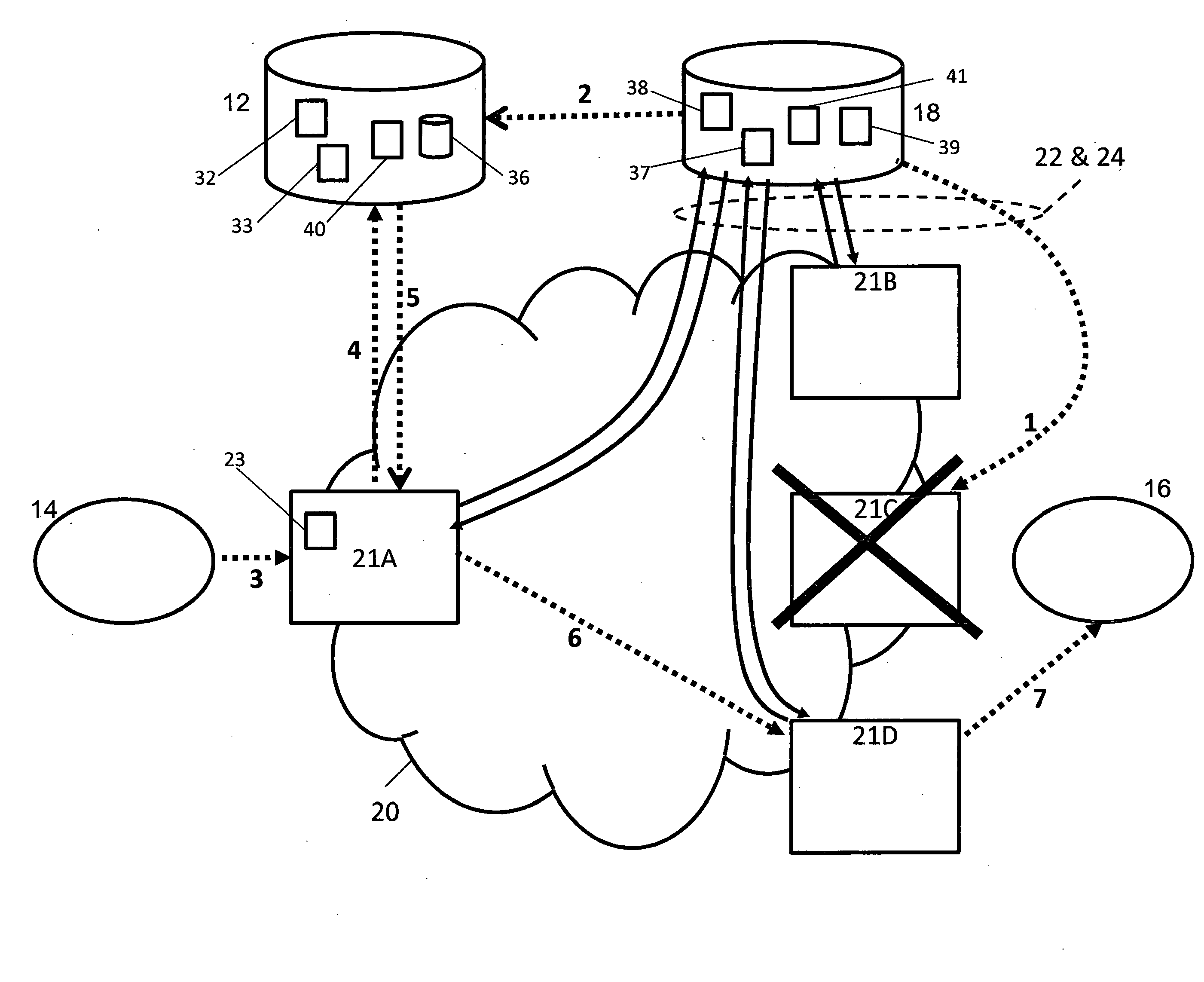
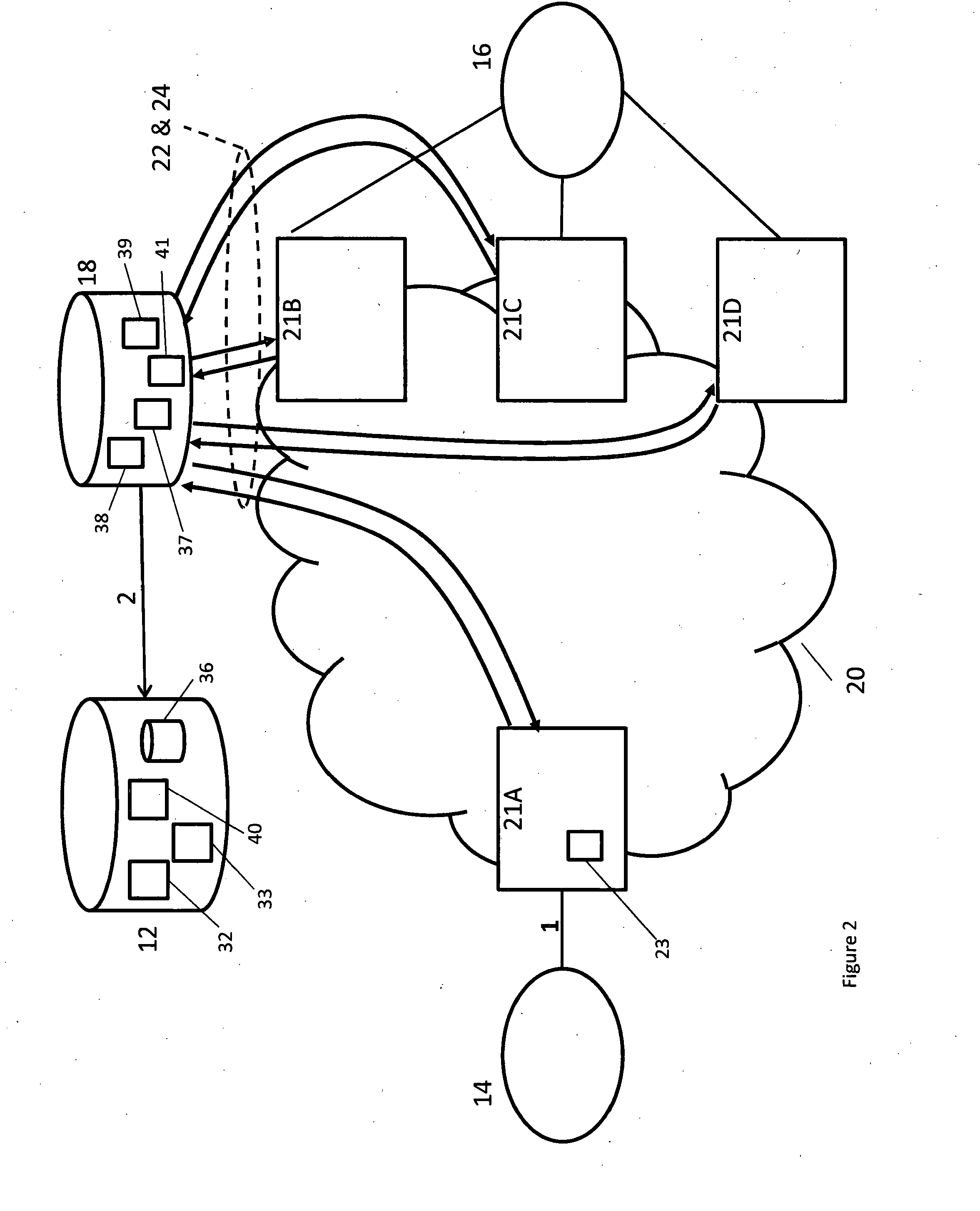
A method and server system for providing application layer session routing based on network element availability. A server system (12, 18) is arranged to monitor the abilities of session control edge nodes (21A-D) within a large VoIP and Multimedia transit network (20) to handle session set-up requests. A status module (38) in the server system receives status messages (22, 24) from the edge nodes and based on these messages a selection and modification module (40, 41) selects which edge nodes (21A-D) as well as which of their associated interconnects to other networks to include in a response (5) to a routing request (4) from a source node (21A-D).
Owner:BRITISH TELECOMM PLC
Data access method and equipment
ActiveCN105095313AEnsure consistencyReduce overheadSpecial data processing applicationsAccess methodData access
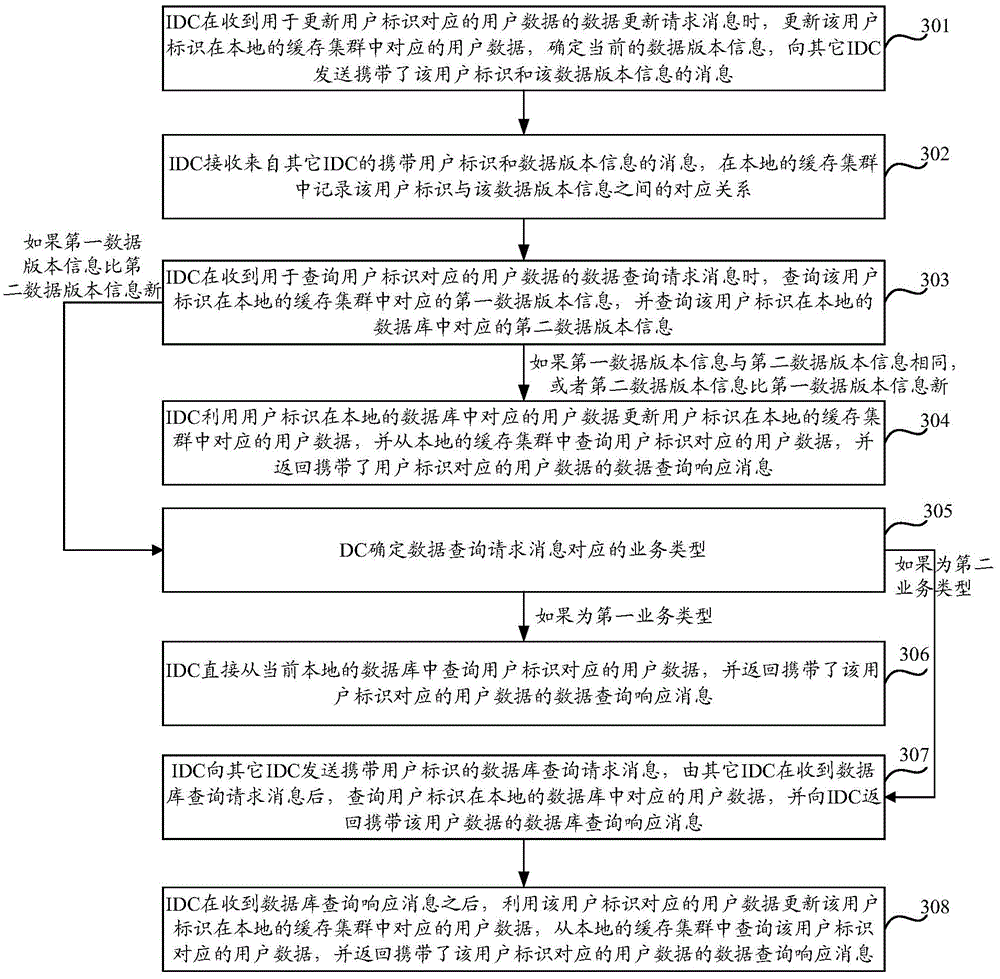
The invention discloses a data access method and equipment. The method comprises: when receiving a data query request message, an IDC queries first data version information corresponding to a user identifier in a local cache cluster and queries second data version information corresponding to the user identifier in a local database; if the first data version information is the same as the second data version information, or the second data version information is newer than the first data version information, the IDC updates user data corresponding to the user identifier in the local cache cluster via the user data corresponding to the user identifier in the local database; and the IDC queries the user data corresponding to the user identifier in the local cache cluster and returns a data query response message carrying the user data corresponding to the user identifier. The data access method in the embodiments of the invention can be used for reducing the network bandwidth cost and guaranteeing the uniformity of the user data obtained by the user, so as to greatly improve the probability of the user for querying the latest user data.
Owner:ADVANCED NEW TECH CO LTD
Method for control delay in interactive multiple vision point video stream media service
ActiveCN101459837AGuaranteed viewing qualityTake advantage ofSpecial service provision for substationPulse modulation television signal transmissionQuality of serviceData segment
The invention relates to a method for controlling relay in alternative multi-view-point video flow media service, which belongs to the technical field of multimedia data transmission. The method mainly comprises the following steps: firstly, carrying out the time synchronization between users and a server, wherein the server enables the users who watch the same view-point to build a view-point inner overlay network, all the view-point inner overlay networks together build an overlay network between the view-points, when the users watch multi-view-point video programs, the equal overlay networks are added on the two levels, key frame data in the multi-view-point programs is averagely divided into a plurality of key frame data segments and are respectively transferred to audiences who watch the different view-points, all the audiences mutually exchanges the key frame segments of their own, and the bandwidth spending of the server during the transmission process is reduced according to the transmission condition of the current data. The method reduces the dependence to the bandwidth resource of the server during the view-point switching process according to the neighbor node bandwidth resources, reduces the intermediate section during the view-point switching process, speeds up the switching speed of the view-points, improves the service quality and increases the watching experience of users.
Owner:TSINGHUA UNIV
Hop-by-hop reliable transmission control method for underwater wireless sensor network
InactiveCN104539387AReliable transmissionReduce codec complexityError prevention/detection by using return channelSimplex communicationReliable transmission
The invention discloses a hop-by-hop reliable transmission control method for an underwater wireless sensor network. Based on a digital fountain code technology irrelevant to a code rate, optimized degree distribution and recursive coding ideas are adopted, and an RLT (recursive LT) coding scheme is designed, so that rapid and efficient coding and decoding are realized; packet collision and end-to-end delay are reduced; and the network throughput is increased. Through collection of feedback information of a receiving node, the packet corruption probability of an underwater acoustic channel is accurately estimated, and the coding packet quantity of next transmission is further computed, so that the transmission overhead of extra packets is reduced. The fourth-layer reliable transmission mechanism and the second-layer medium access control mechanism of a conventional TCP / IP (Transmission Control Protocol / Internet Protocol) protocol stack are organically fused, so that block-by-block and hop-by-hop reliable transmission of the underwater wireless sensor network is realized on the basis of RLT coding, and transmission-reception conflicts, multi-transmission-single-reception conflicts and data-ACK conflicts caused by simplex communication of an underwater Modem are reduced. As an effective and practicable technical scheme, the method has a good application prospect.
Owner:杜秀娟
Key agreement devices and method
ActiveUS20200153618A1Simple protocolReduce communication overheadKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeComputer network
A first electronic network node (110) is provided configured for a key exchange (KEX) protocol, the first network node is configured to obtain a shared polynomial (a) shared with a second network node, coefficients of the shared polynomial a being selected modulo a first modulus q, generate a private key polynomial (skI), coefficients of the private key polynomial being bounded in absolute value by a bound (s) generate a public key polynomial (pkI) by computing a polynomial product between the shared polynomial (a) and the private key polynomial (skI) modulo the first modulus (q) and scaling the coefficients of the polynomial product down to a second modulus (p).
Owner:KONINKLJIJKE PHILIPS NV
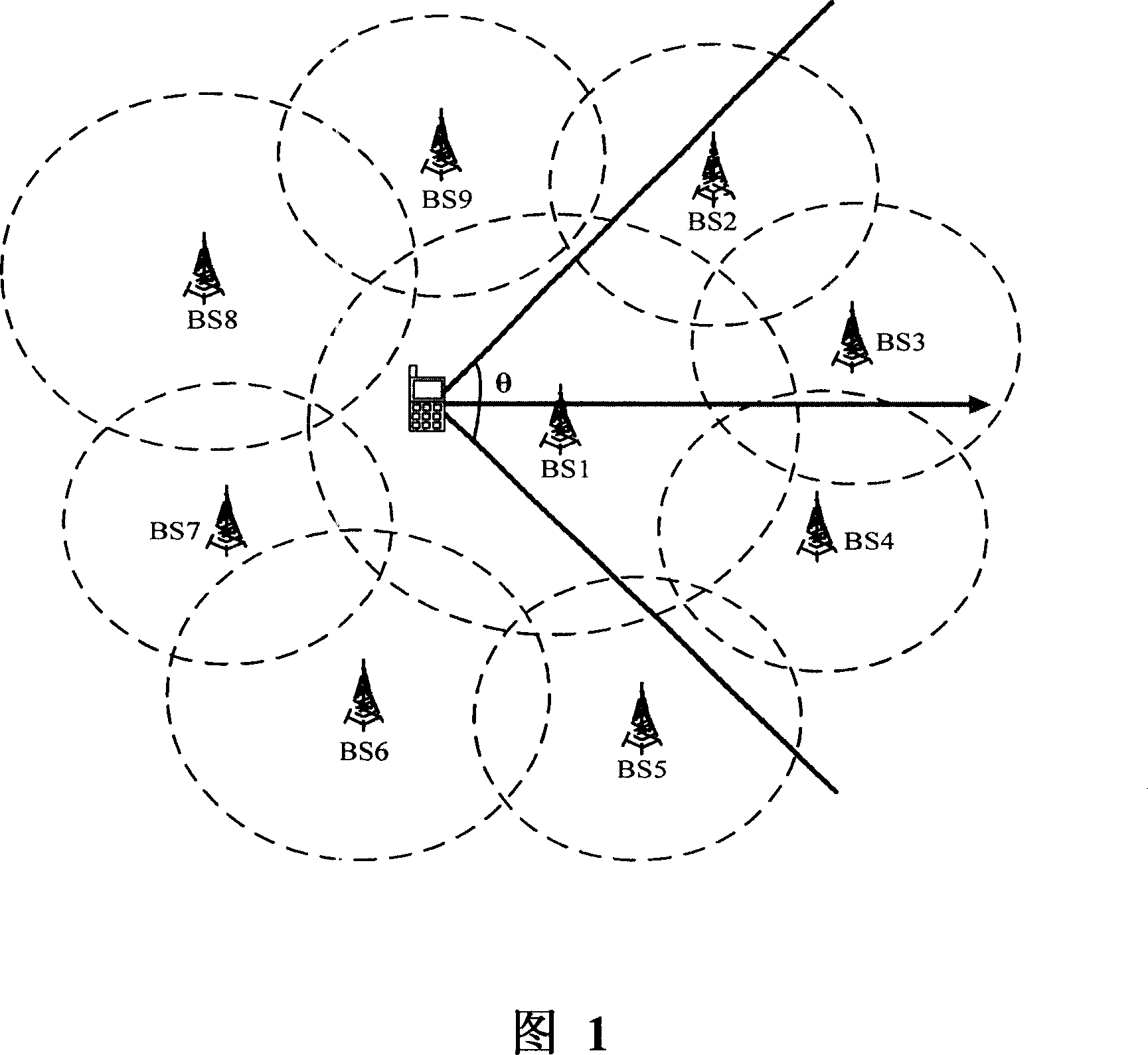
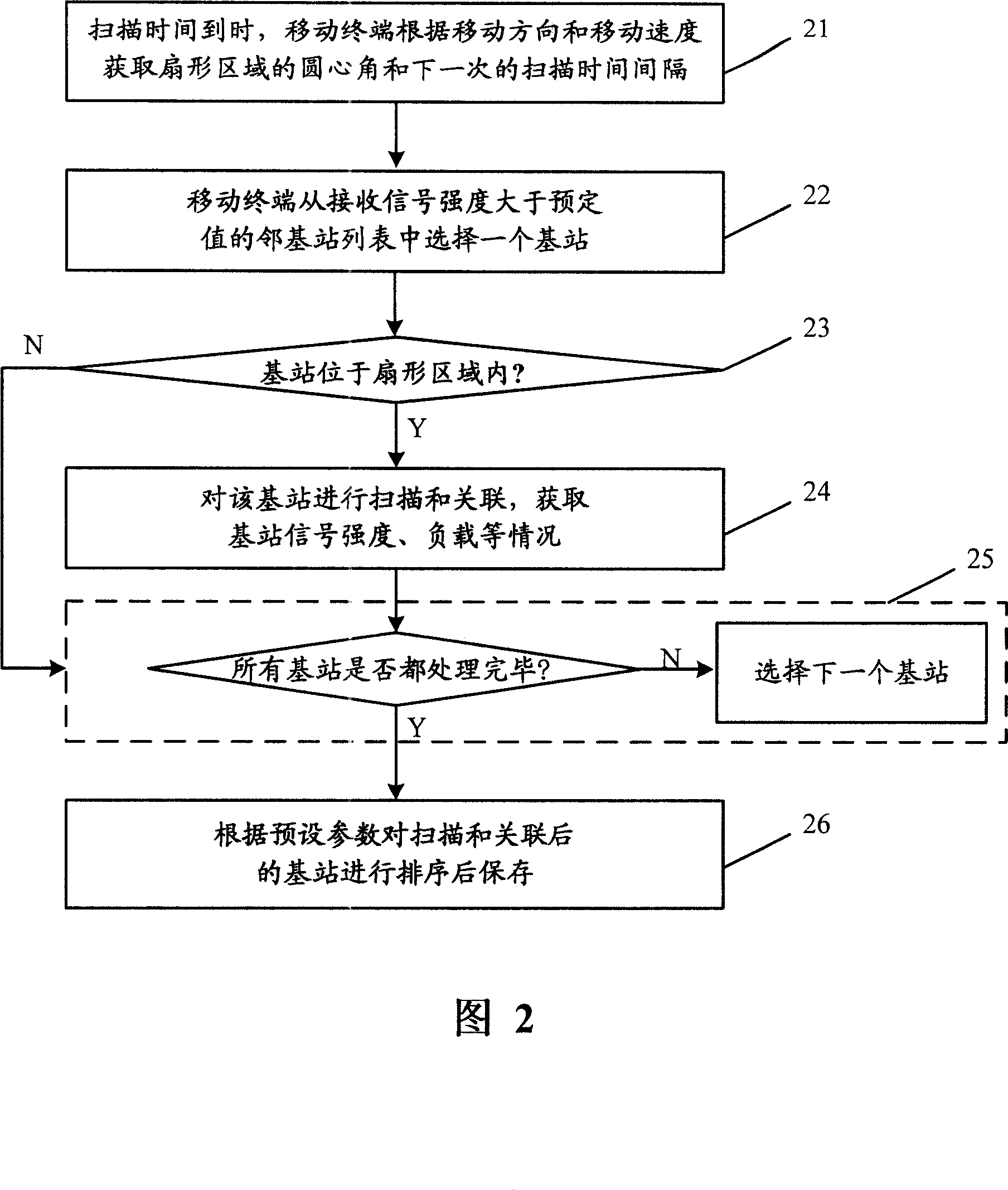
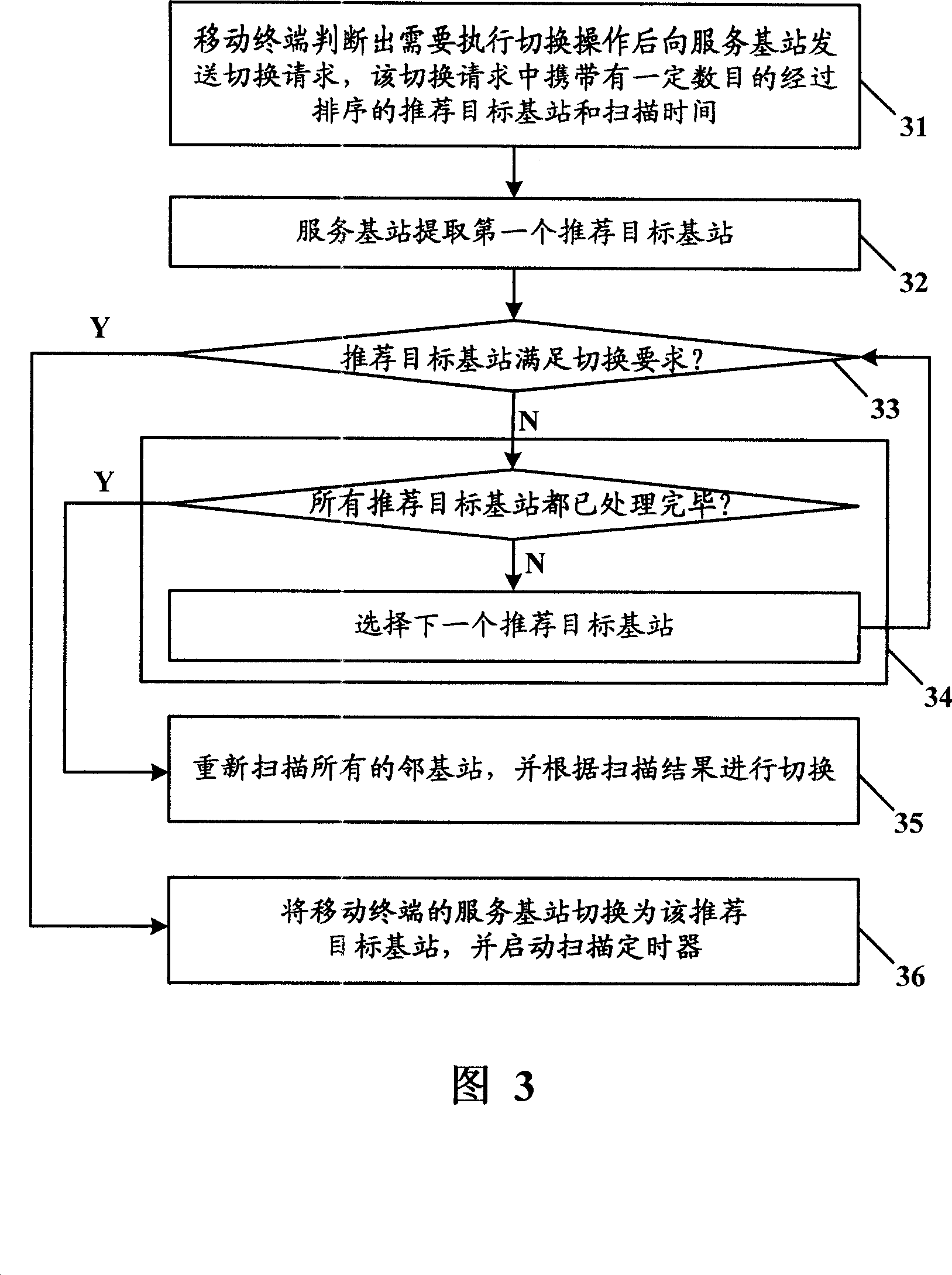
Method for selecting scanning and association base station in Wimax system and base station switching method
ActiveCN101146333AGuaranteed validityReduce the numberAssess restrictionRadio/inductive link selection arrangementsMoving speedWiMAX
The invention discloses a method for selectively scanning and associating with base station in Wimax system and a base station shifting method, wherein the method for selectively scanning and associating base station includes step S1, the mobile terminal identifies a sector area according to its moving speed and direction, the angle taking the mobile terminal as starting point and formed by the angular bisector of the central angle formed by the radial pointing to the moving direction and the sector area is smaller than the preset value; step S2, the mobile terminal scans the base stations in the sector area whose signal strengths are larger than the preset value, or meanwhile conducts scanning and associating; step S3, the mobile terminal sorts the base stations to be scanned or scanned and associated according to preset parameters. The method provided by the invention effectively reduces the number of scanned and associated base stations, thus reducing cost and meanwhile associating the cycle of scanning and associating with speed, so that the costs caused by the reduction in signal and command while ensuring the effectiveness of the results of the last scanning and associating.
Owner:LENOVO (BEIJING) CO LTD
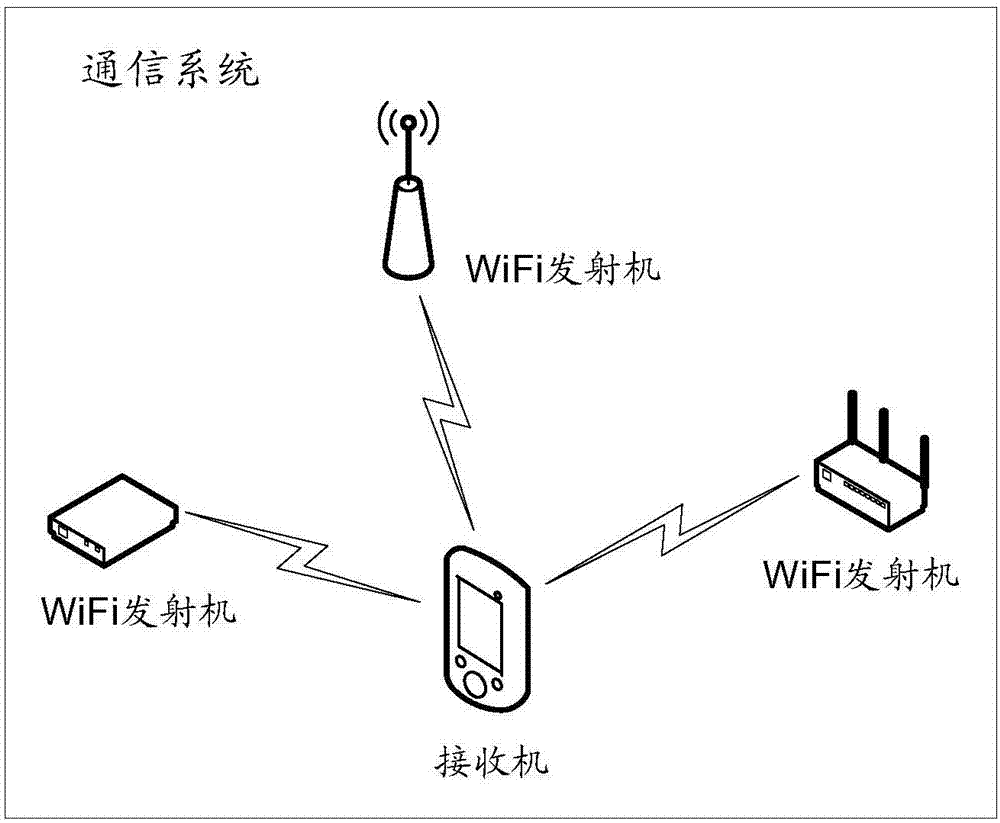
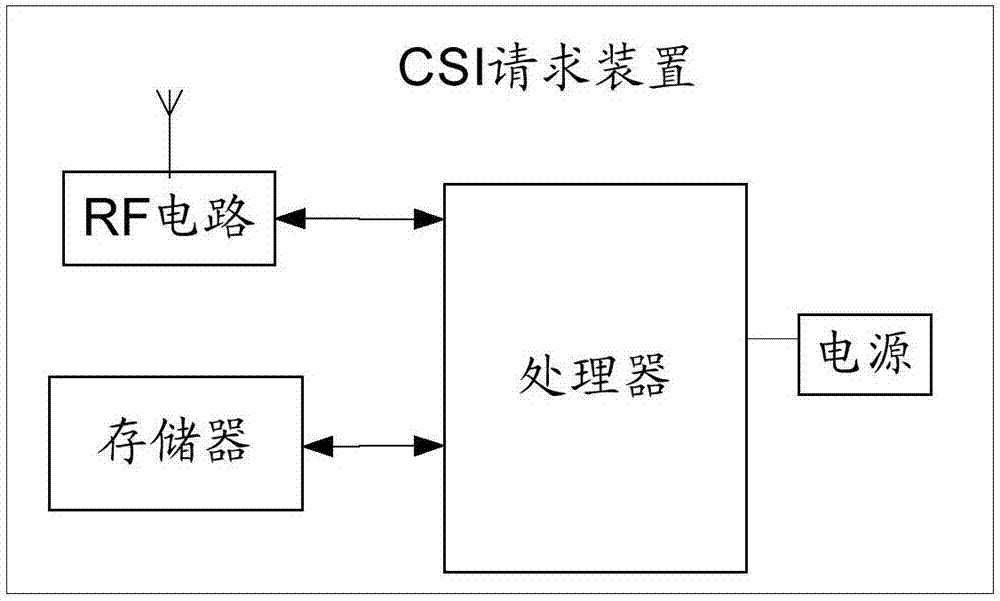
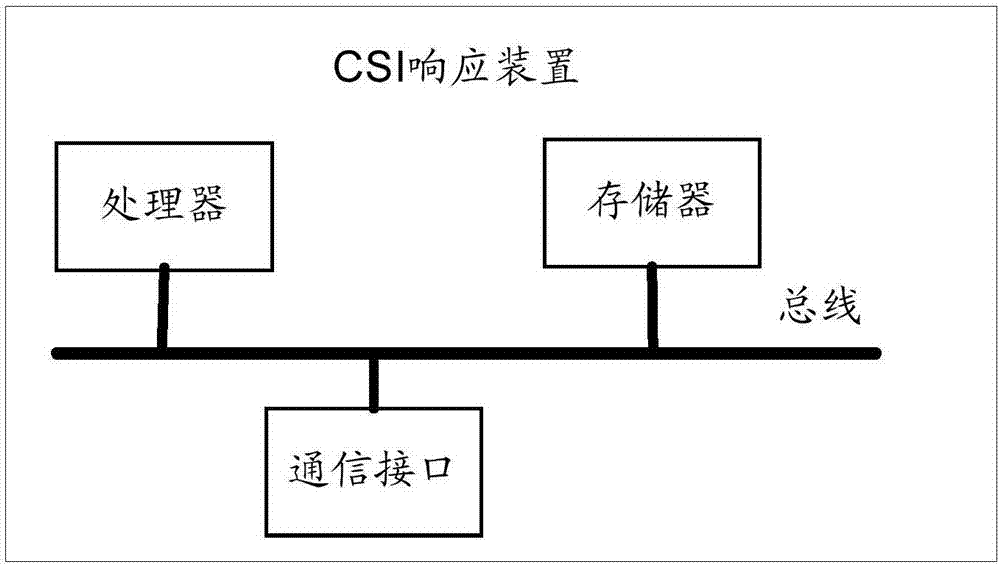
Channel state information (CSI) measurement method and device
ActiveCN107979402AReduce time delayReduce bandwidth overheadSpatial transmit diversityWireless network protocolsChannel state informationComputer science
The embodiment of the invention provides a channel state information (CSI) measurement method and device, relating to the technical field of communication, and aiming to ensure that a receiver can also measure CSI without joining a network of a WiFi transmitter. The method includes the following steps: a CSI request device sends a first CREQ frame, wherein the first CREQ frame is used for requesting a CSI response device that receives the first CREQ frame to determine a group of session parameters for transmitting a CS frame from at least one group of session parameters, and the CS frame is used by the CSI request device to perform channel state measurement; the CSI request device receives a CRSP frame sent by a first CSI response device, wherein the CRSP frame includes first session parameters, and the first session parameters are a group of session parameters in the at least one group of session parameters; the CSI request device receives the CS frame by using the first session parameters; and the CSI request device measures the CS frame to obtain the CSI. The method is applied in positioning scenes.
Owner:HUAWEI TECH CO LTD
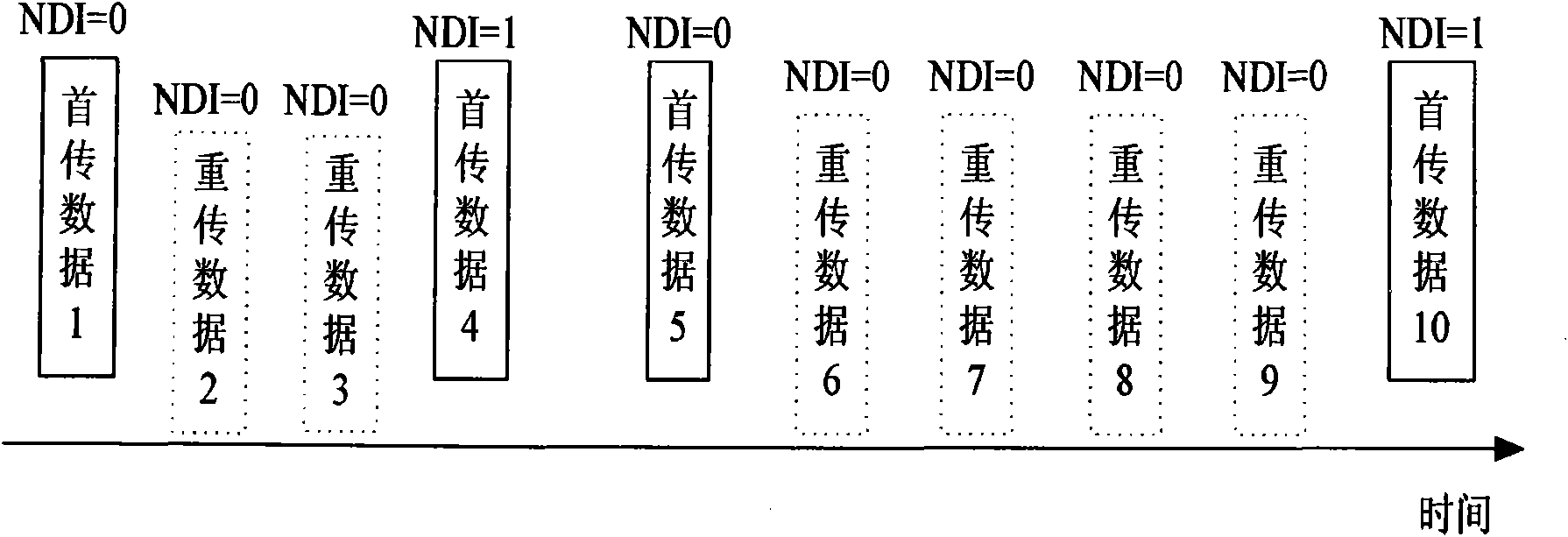
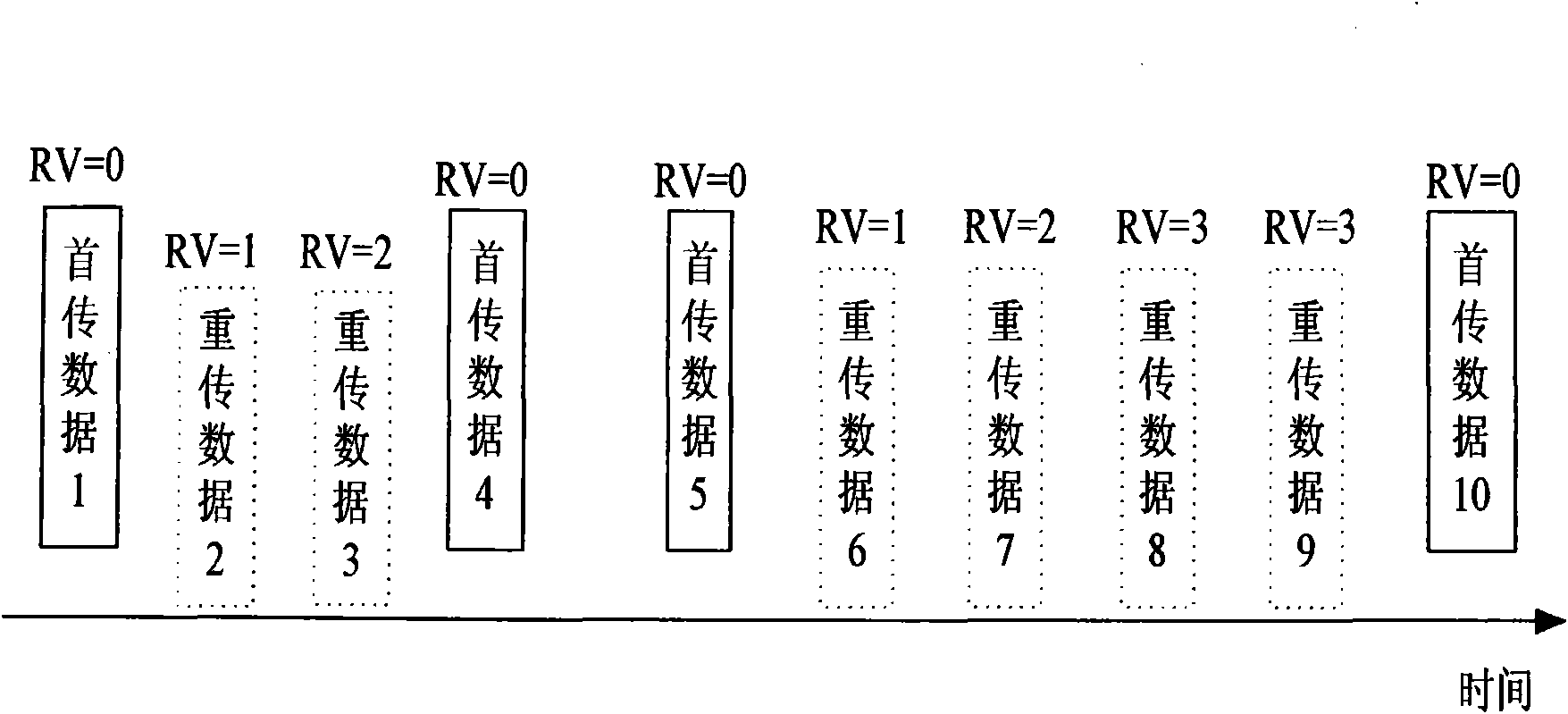
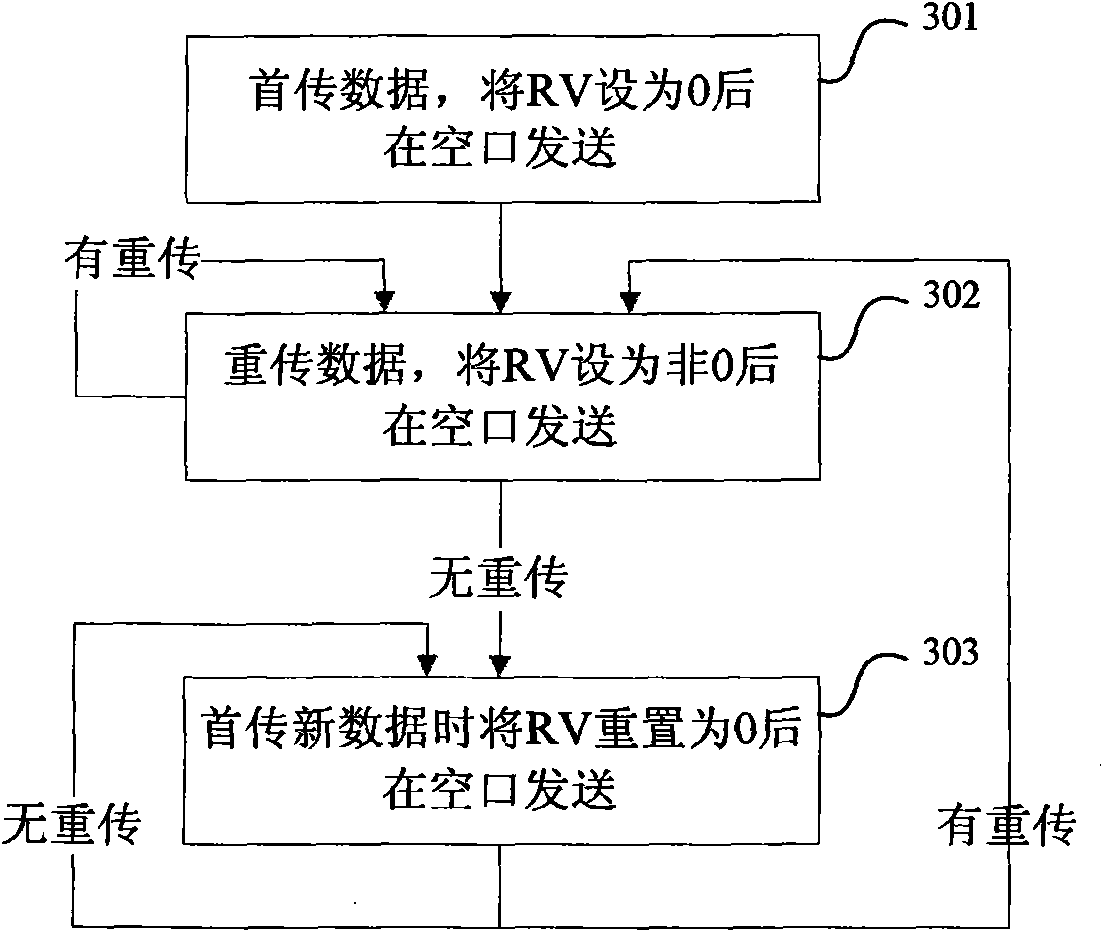
Method for sending and receiving redundancy version parameters of hybrid automatic retransmission
InactiveCN101645761AReduce bandwidth overheadReduce transmit power overheadError prevention/detection by using return channelComputer hardwareAir interface
The invention relates to a method for sending redundancy version parameters of hybrid automatic retransmission. A sending end sets a redundancy version RV parameter value of first transmission data as0 and sets an RV value of retransmission data as a non-zero value in an available RV set; and a receiving end takes a data packet in which the RV value is 0 as a first transmission data packet for processing, and takes the data packet in which the RV value is the non-zero value in the available RV set as a retransmission data packet for processing. The method distinguishes the first transmissiondata and the retransmission data by RV parameters, and does not use NDI so as to save the transmission of the bit of the NDI at an air interface and reduce the bandwidth overhead and transmission power overhead of the air interface.
Owner:ZTE CORP
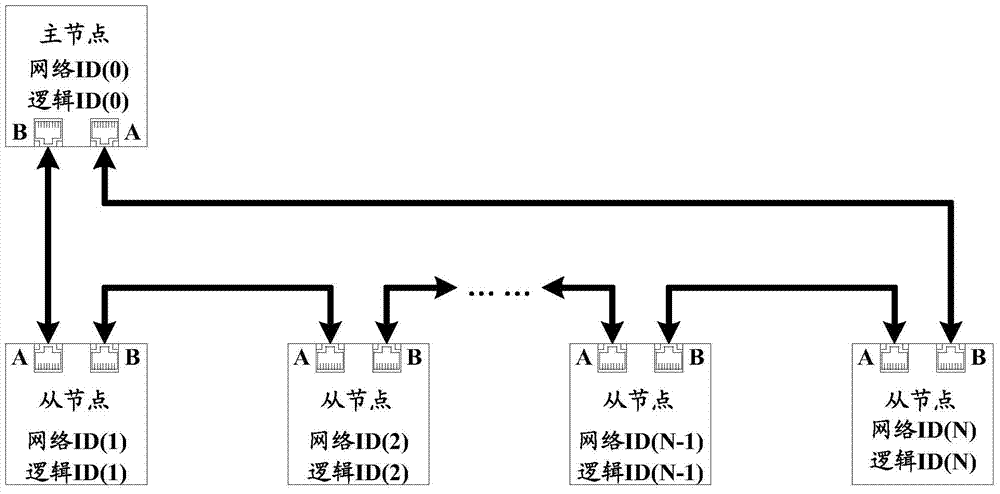
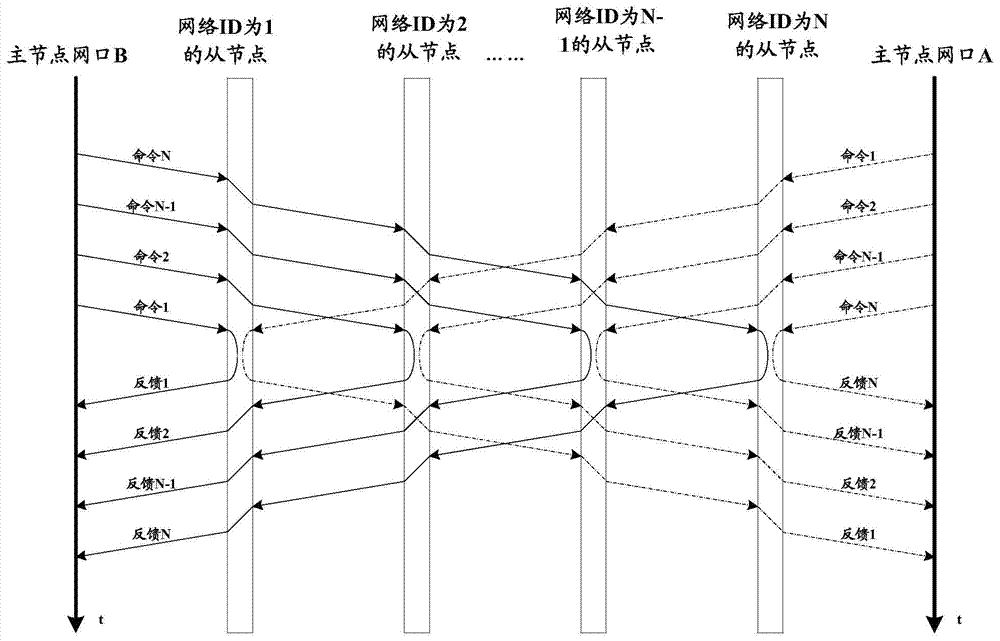
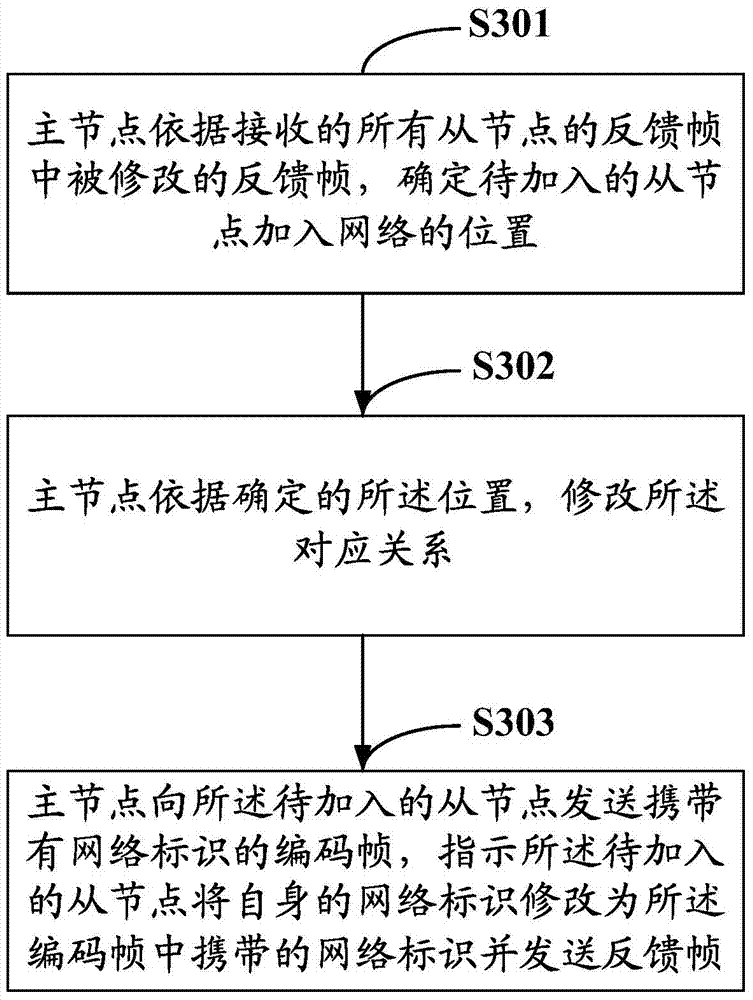
Ring communication network slave node increasing and decreasing method, device and system
ActiveCN104767664ASynchronization does not dropCommunication efficiency does not decreaseData switching networksPacket lossCommunications system
The invention discloses a ring communication network slave node increasing and decreasing method, a device and a system. The method comprises steps: according to modified feedback frames in received feedback frames of all slave nodes, a master node determines adding network positions of to-be-added slave nodes, and according to the positions, a corresponding relationship between logic identifiers and network identifiers is modified; encoding frames with the network identifiers are sent to the to-be-added slave nodes, and the to-be-added slave nodes are indicated to modify self network identifiers to be the network identifiers in the encoding frames. On one hand, a special query frame is needed, and thus extra bandwidth overhead can be reduced; on the other hand, the feedback frames are used for acquiring information of the adding network positions of the to-be-added slave nodes, network adding of slave nodes can be completed in only one communication cycle; and thus, no packet loss during node increasing and decreasing processes of the communication system can be ensured, synchronization performance does not fall, and the communication efficiency is not reduced.
Owner:EMERSON NETWORK POWER CO LTD
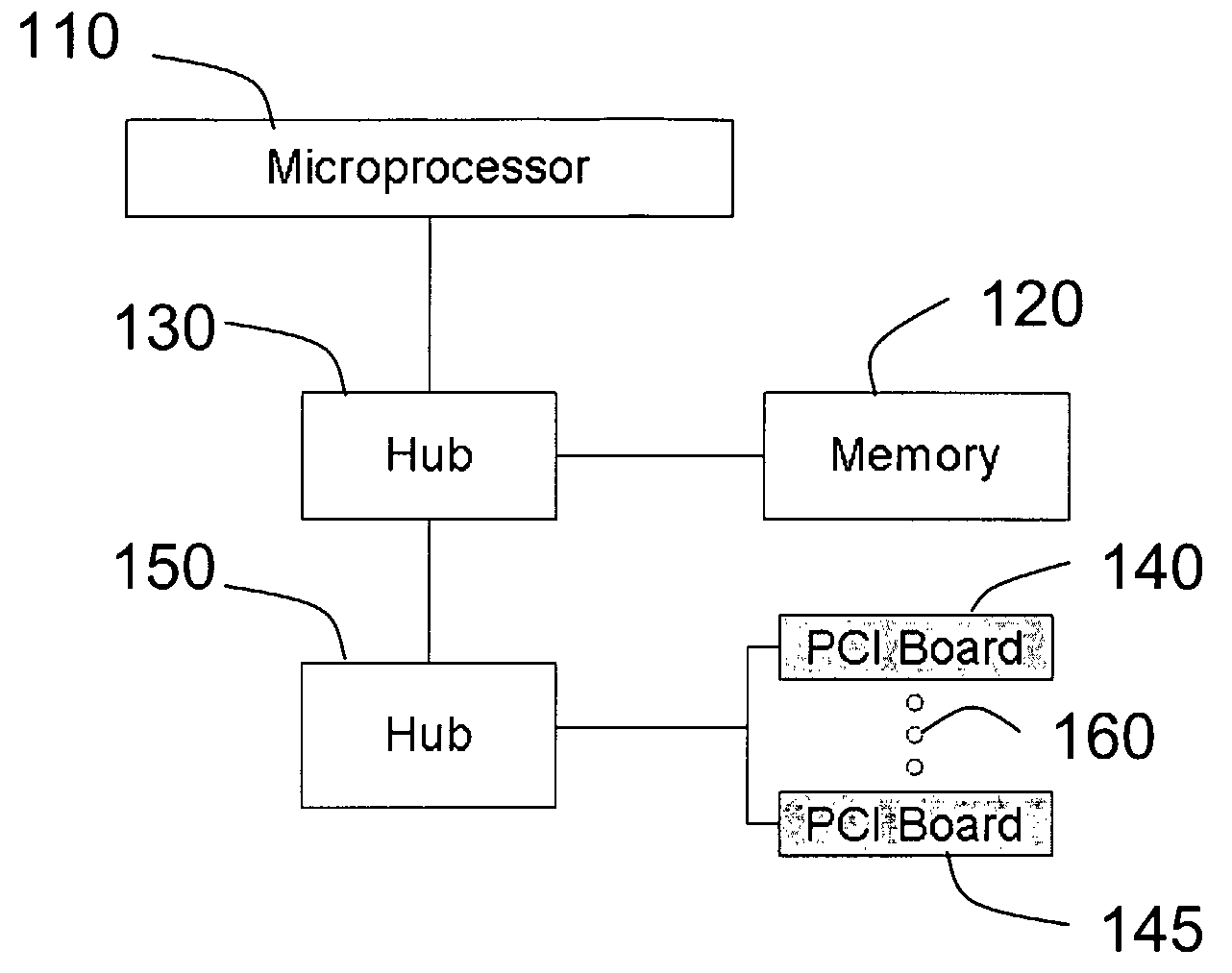
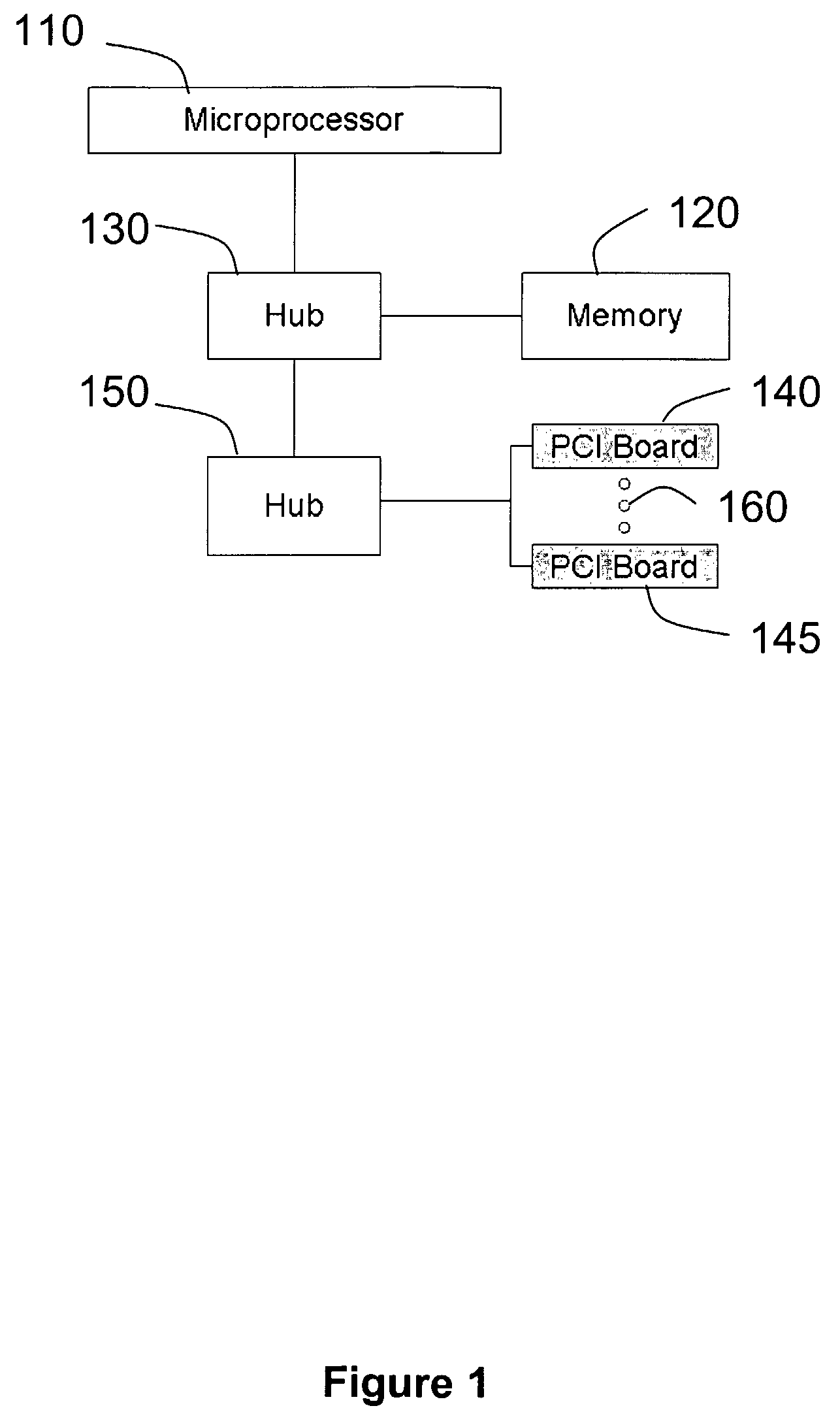
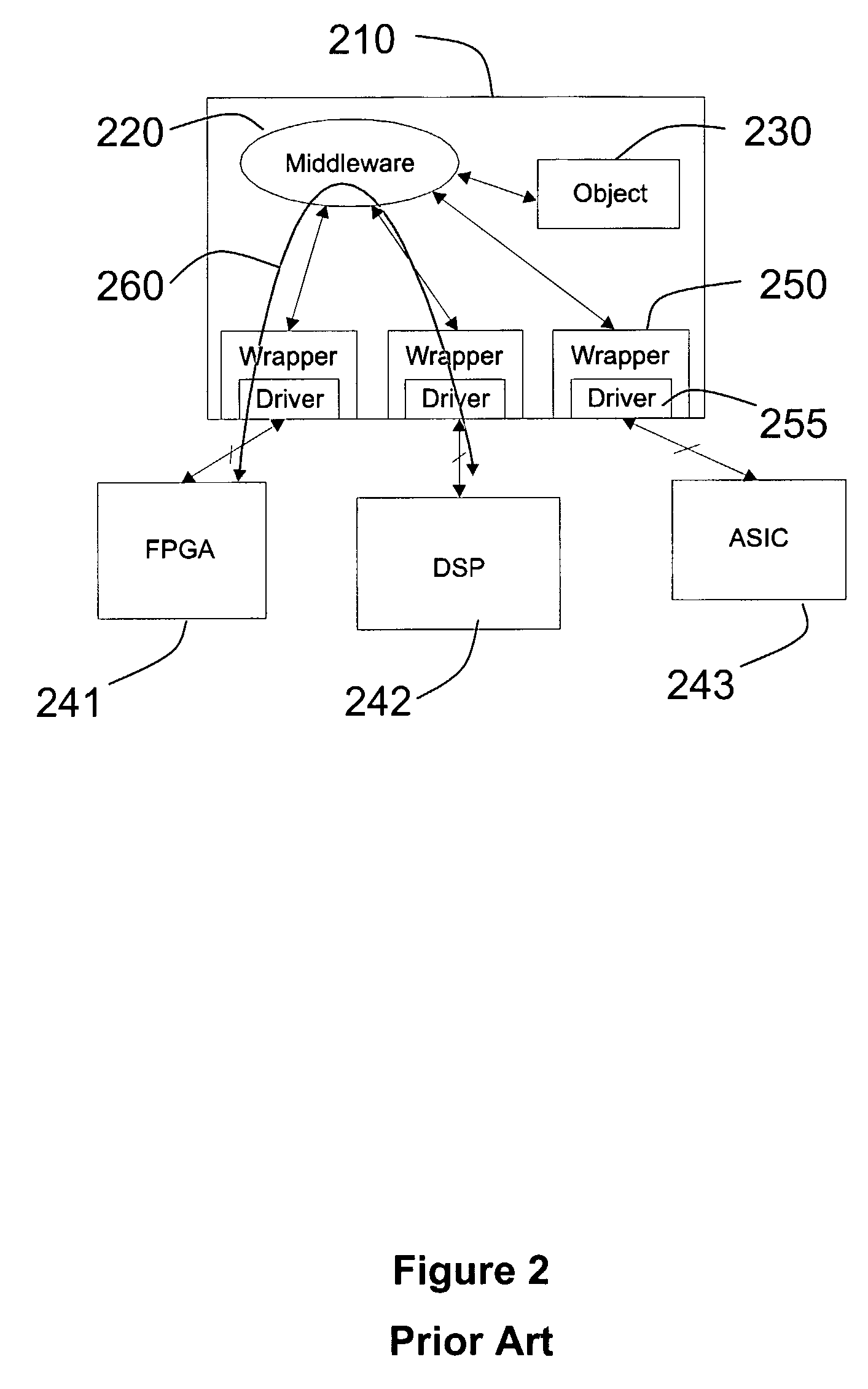
Hardware Object Request Broker on a Chip for Generating Separate Control and Data Channels for Improved Throughput Efficiency
InactiveUS20080235712A1Reduce bandwidth overheadInterprogram communicationDistributed object oriented systemsGeneral purposeDirect communication
A method and apparatus are disclosed for separating the functionality of middleware (320) in a device with embedded resources (341,342) so that data transfer between embedded resources used by an object (330) resident in a general purpose processor (310) of the device takes place directly, thereby minimizing bandwidth overhead at the general purpose processor. The control interface (371,372) for an embedded resource resides in the general purpose processor and uses the device driver of the embedded resource, whereas the data interface (381,382) is outside the general purpose processor and provides direct communication with a switch matrix (360) serving each embedded resource.
Owner:VIRGINIA TECH INTPROP INC
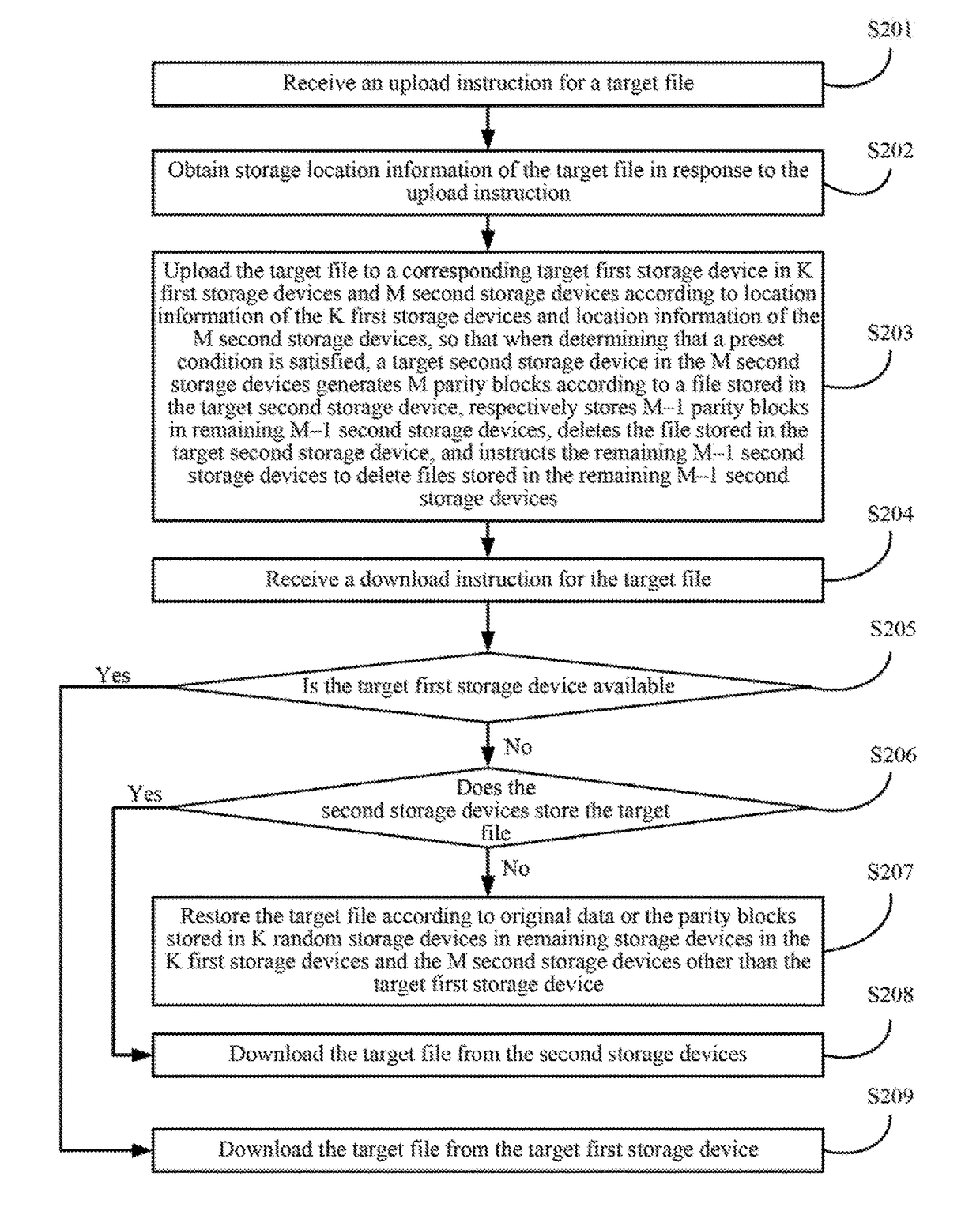
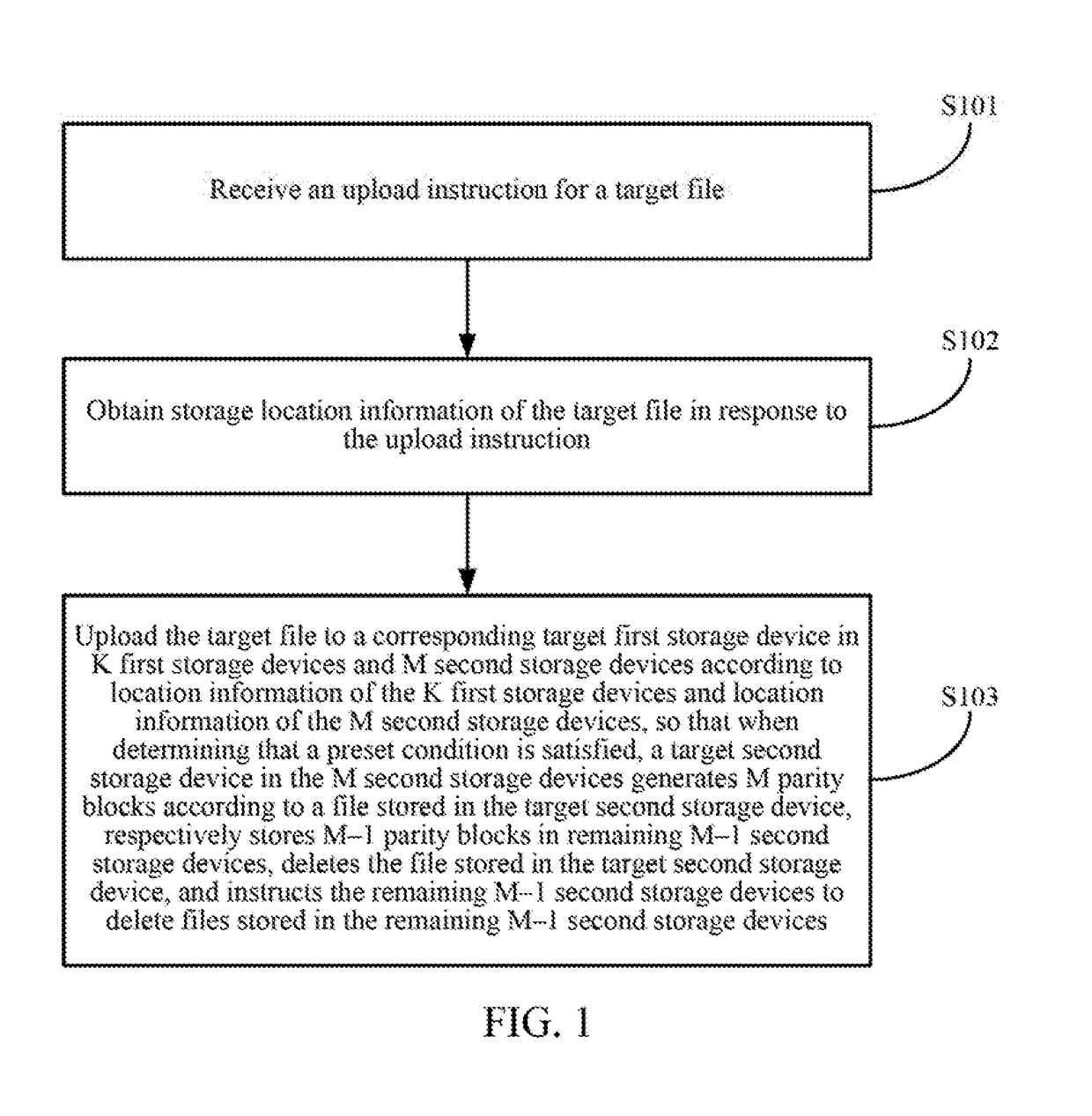
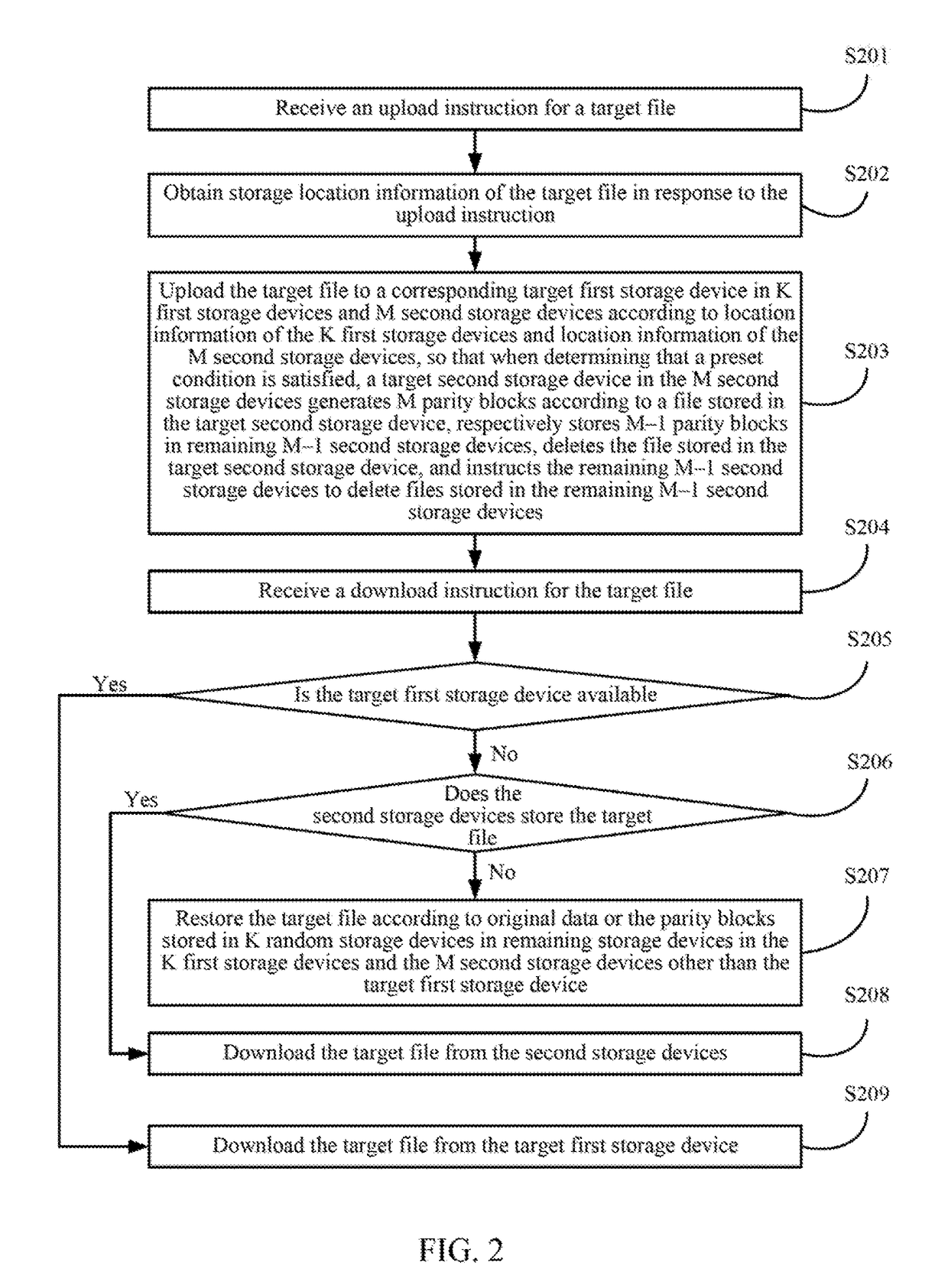
Data processing method and device
ActiveUS20170185615A1Reduce bandwidth overheadFile access structuresTransmissionComputer hardwareComputer science
Embodiments of the present disclosure disclose a data processing method, including: receiving an upload instruction for a target file; obtaining storage location information of the target file in response to the upload instruction; and uploading the target file to a corresponding target first storage device in K first storage devices and M second storage devices according to location information of the K first storage devices and location information of the M second storage devices, so that when determining that a preset condition is satisfied, a target second storage device in the M second storage devices generates M parity blocks according to a file stored in the target second storage device, respectively stores M−1 parity blocks in remaining M−1 second storage devices, deletes the file stored in the target second storage device, and instructs the remaining M−1 second storage devices to delete files stored in the remaining M−1 second storage devices. The embodiments of the present disclosure further disclose a data processing device. By implementing the embodiments of the present disclosure, network bandwidth overheads caused by cache writing can be effectively reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
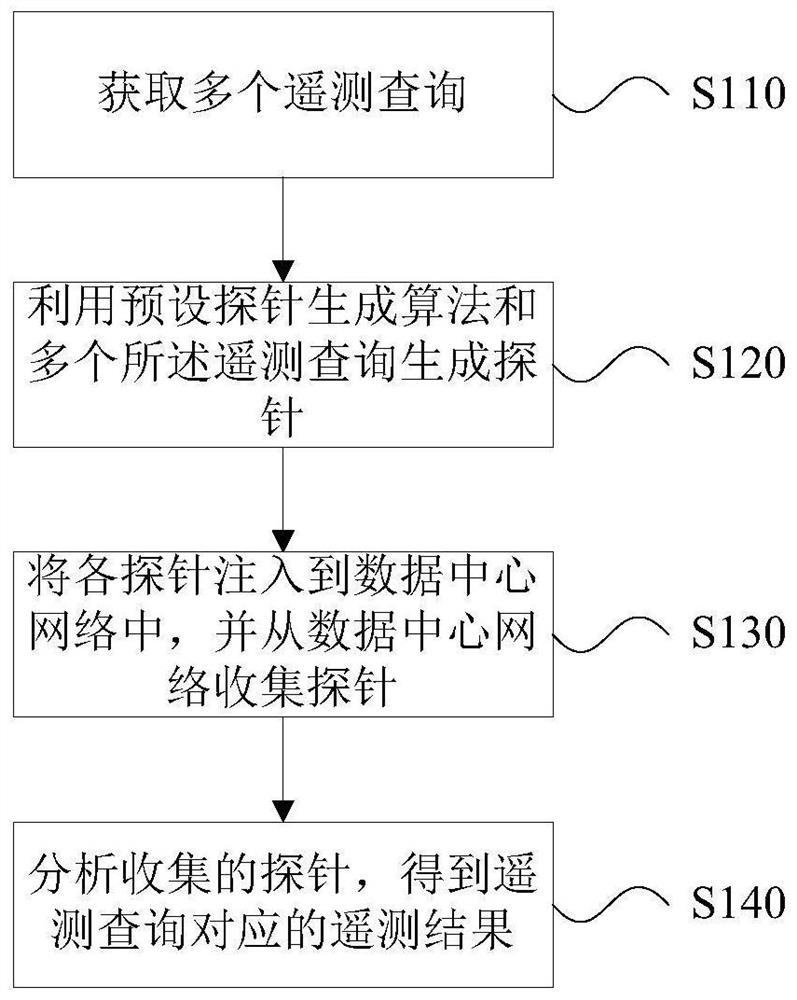
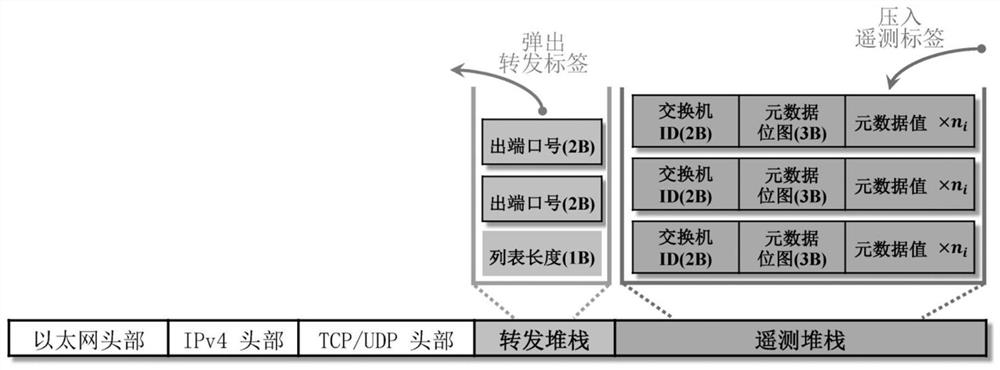
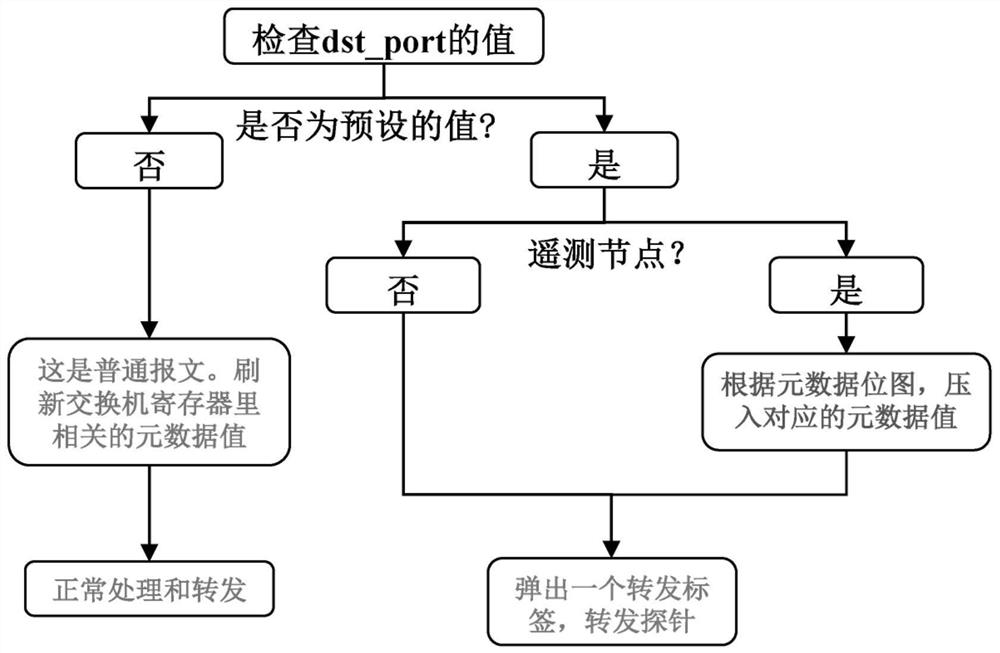
Data center network telemetering method and system, storage medium and telemetering server
InactiveCN112436984AAchieve full coverageImprove scalabilityData switching networksServerReal-time computing
The invention provides a data center network telemetering method, a data center network telemetering system, a storage medium and a telemetering server, which are used for carrying out on-demand telemetering on a data center network under the condition of meeting the requirements of full coverage and expandability. The data center network telemetering method comprises the following steps: acquiring a plurality of telemetering queries; generating a probe by using a preset probe generation algorithm and the plurality of telemetry queries; injecting each probe into the data center network, and collecting the probes from the data center network; and analyzing the collected probes to obtain a telemetry result corresponding to the telemetry query.
Owner:TSINGHUA UNIV
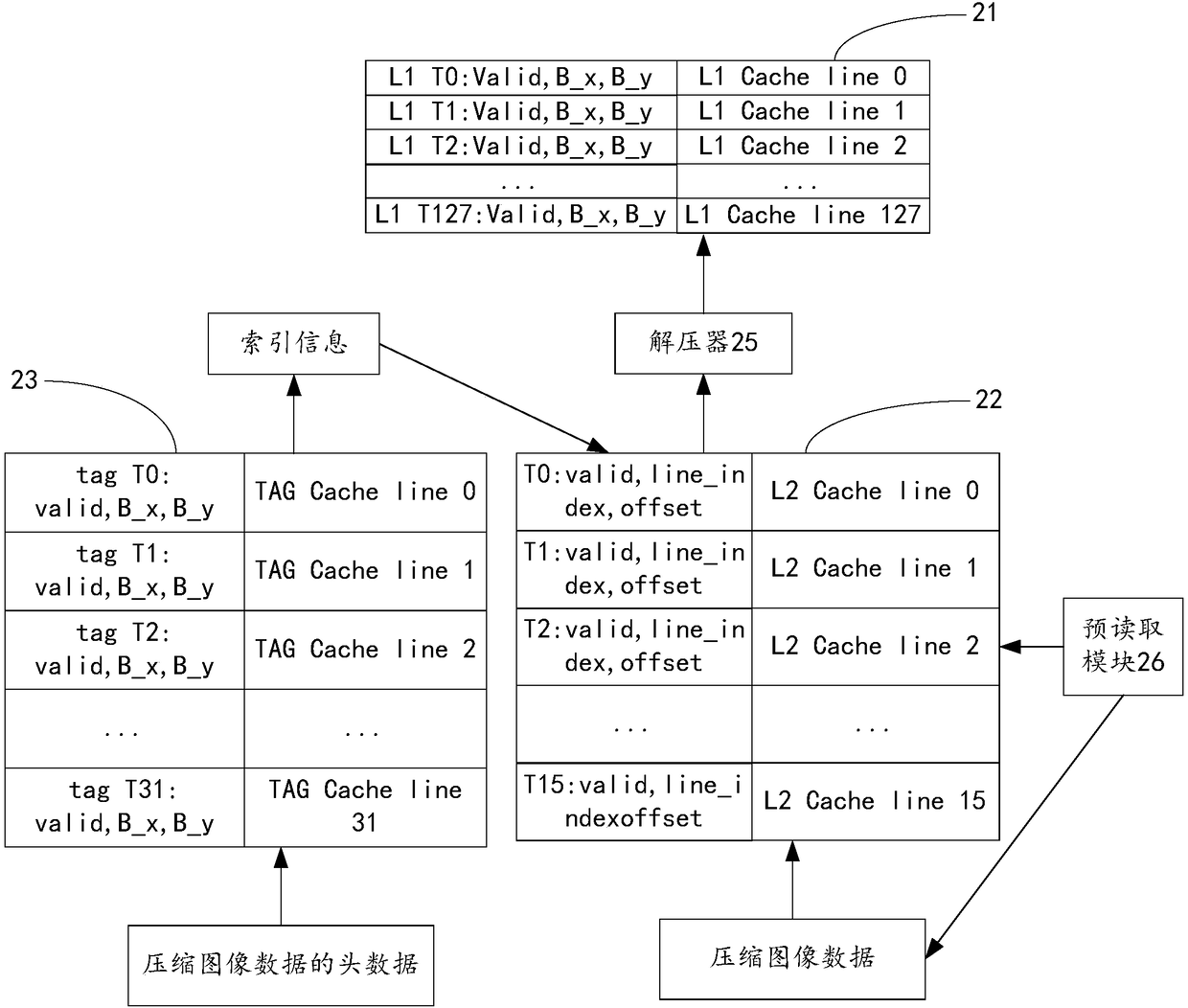
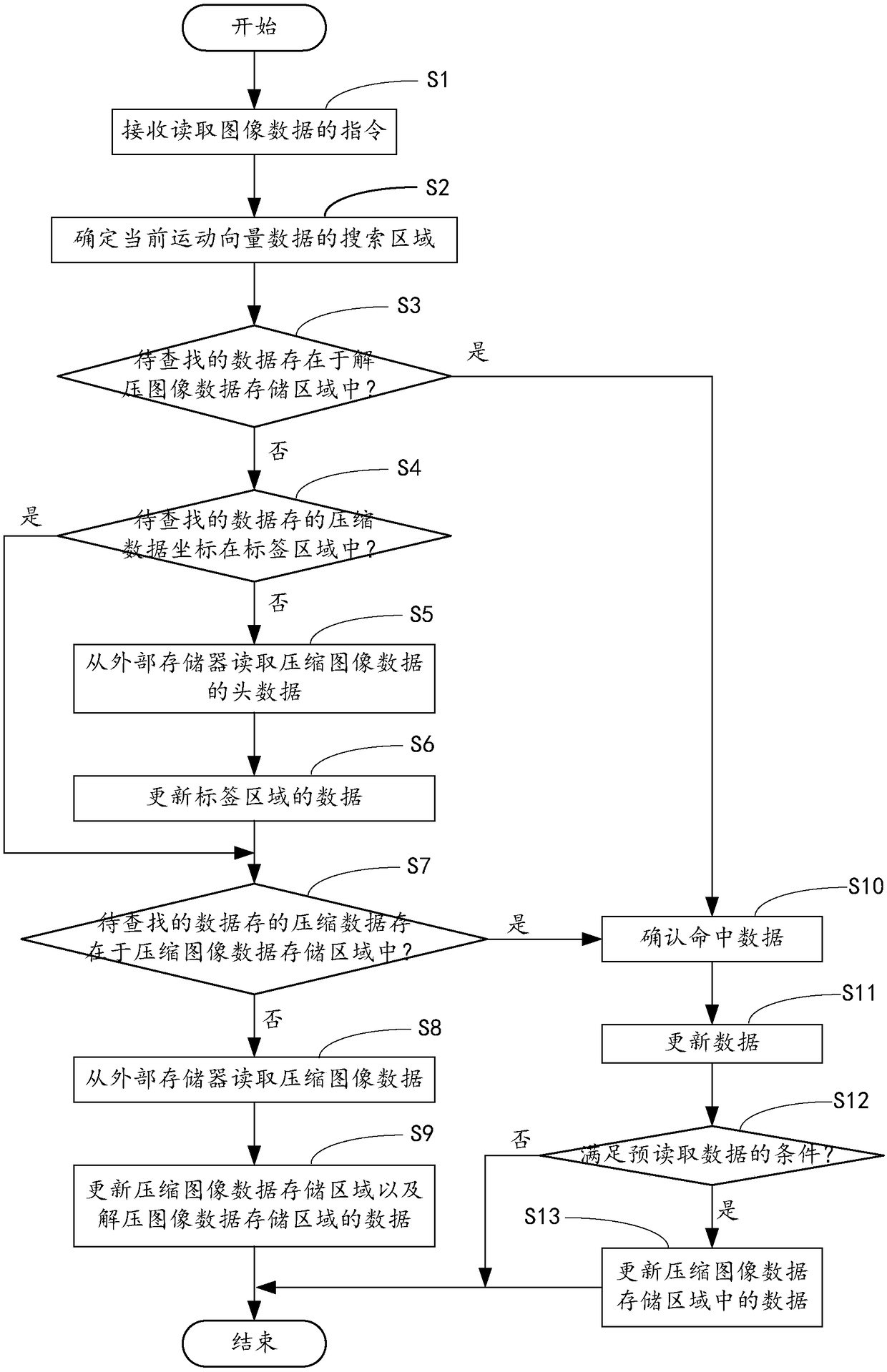
Image data reading method for video coder, computer device and computer readable memory medium
ActiveCN108377394ADoes not affect normal useReduce bandwidth overheadDigital video signal modificationExternal storageVideo encoding
The invention discloses an image data reading method for a video coder, a computer device and a computer readable memory medium. The method comprises the steps that a cache receives an instruction forreading video data, reads compressed image data from an external memory and stores the compressed image data to a compressed image data storage area; the compressed image data is decompressed and then is stored to a decompressed image data storage area of the cache; coordinates of image data are determined according to the instruction for reading the video data, to-be-searched image data is searched from the decompressed image data storage area according to the coordinates of the image data, and after the to-be-searched image data is stored to the decompressed image data storage area, the searched image data is sent to a subordinate data utilization module. According to the method, the computer device and the computer readable memory medium, the bandwidth cost of the memory in an image coding process can be reduced.
Owner:ALLWINNER TECH CO LTD
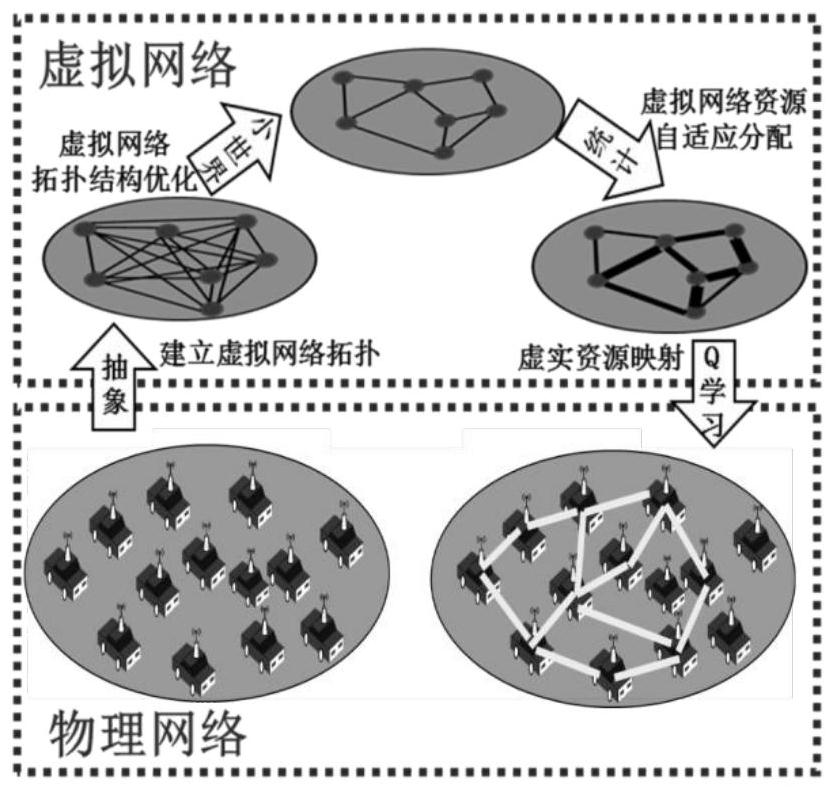
Resource virtual-real mapping method for virtual network construction in multi-hop network
ActiveCN112953761AGuaranteed virtual network requestsReduce controlMachine learningData switching networksPathPingVirtual network topology
The invention provides a resource virtual-real mapping method for virtual network construction in a multi-hop network, and the method comprises the following steps: S1, abstracting a physical network, and building initialized virtual network topological structures which are connected pairwise; S2, optimizing the virtual network topology through virtual network evaluation indexes by adopting a small world theory to obtain an optimized topology connection relationship; S3, endowing each link of the virtual network topology structure with equal communication resources in sequence, and allocating different communication resources to each link according to the parallel service transmission number for the remaining resources; S4, completing the end-to-end virtual link planning by adopting a path selection method based on reinforcement learning, and mapping virtual links between virtual network user nodes into actual links. According to the method, the link utilization rate can be improved and the network bandwidth overhead can be reduced under the condition that the requirement of congestion-free communication among multiple users is met.
Owner:CHINA ELECTRONICS TECH GRP NO 7 RES INST
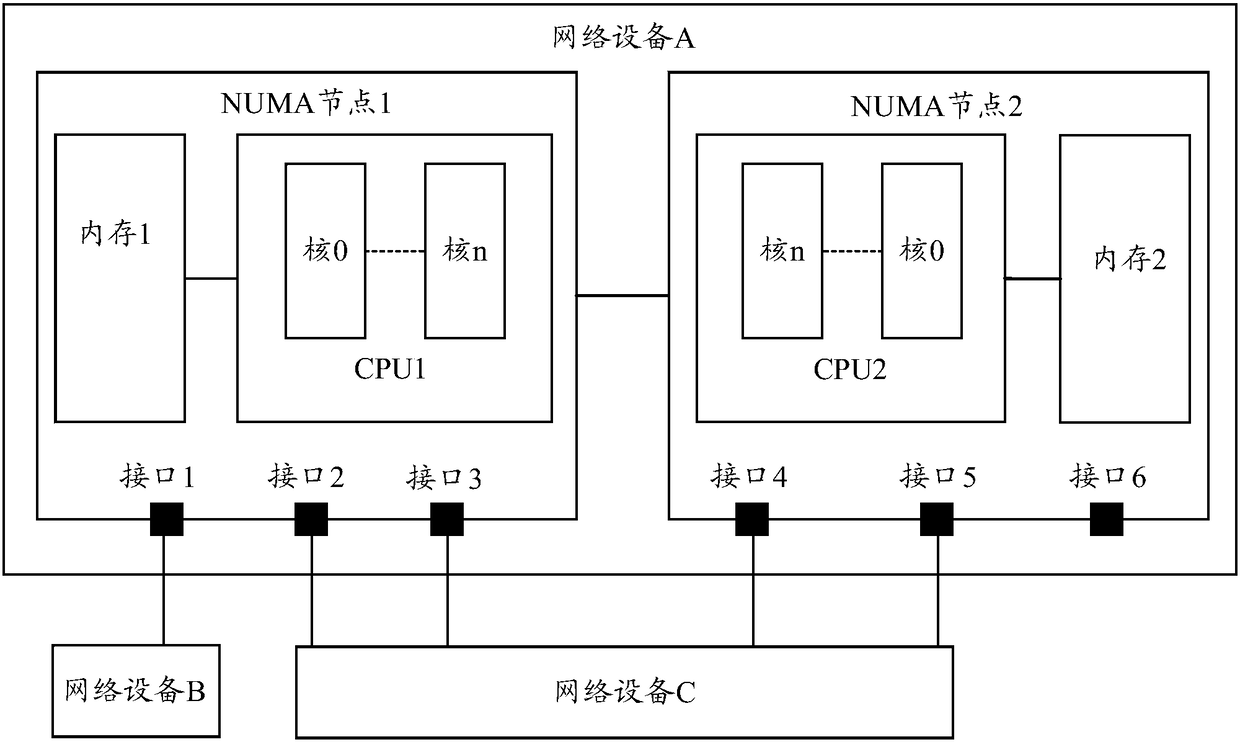
Message transmission method and device
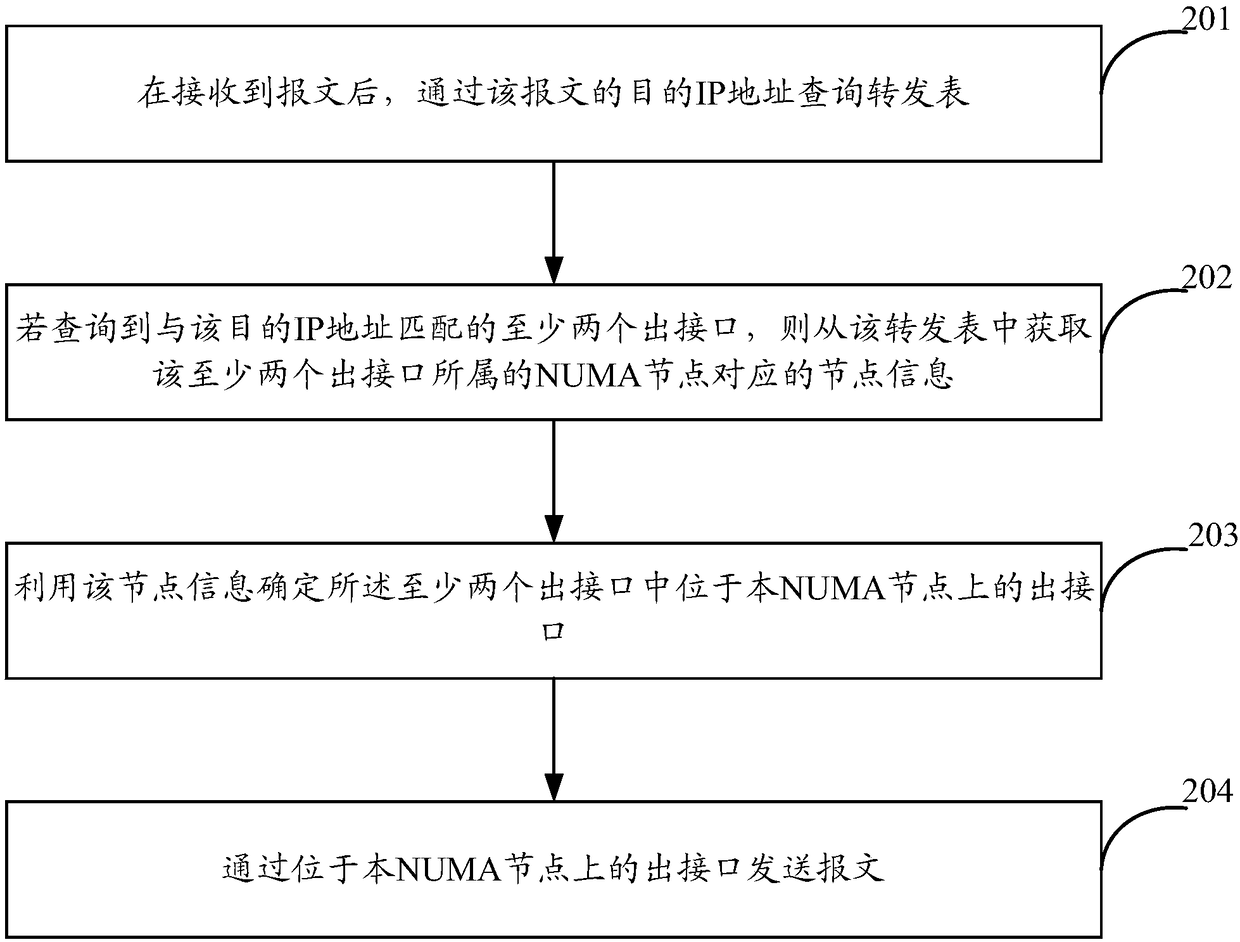
ActiveCN108123901AImprove forwarding efficiencyReduce bandwidth overheadProgram controlData switching networksIp addressDistributed computing
The application provides a message transmission method and device. The message transmission method comprises the following steps: querying a forwarding table through the destination IP address of a message after the message is received; obtaining the node information corresponding to a NUMA node that at least two outgoing interfaces belong to from the forwarding table if the at least two outgoinginterfaces matched with the destination IP address are queried; confirming the outgoing interface located on the NUMA node in the at least two outgoing interfaces by means of the node information; andsending the message through the outgoing interface on the NUMA node. Through the technical scheme provided by the application, the situation of message forwarding across the NUMA node is reduced, themessage forwarding efficiency is improved, the bandwidth overhead is reduced, and the throughput capacity is improved.
Owner:NEW H3C TECH CO LTD
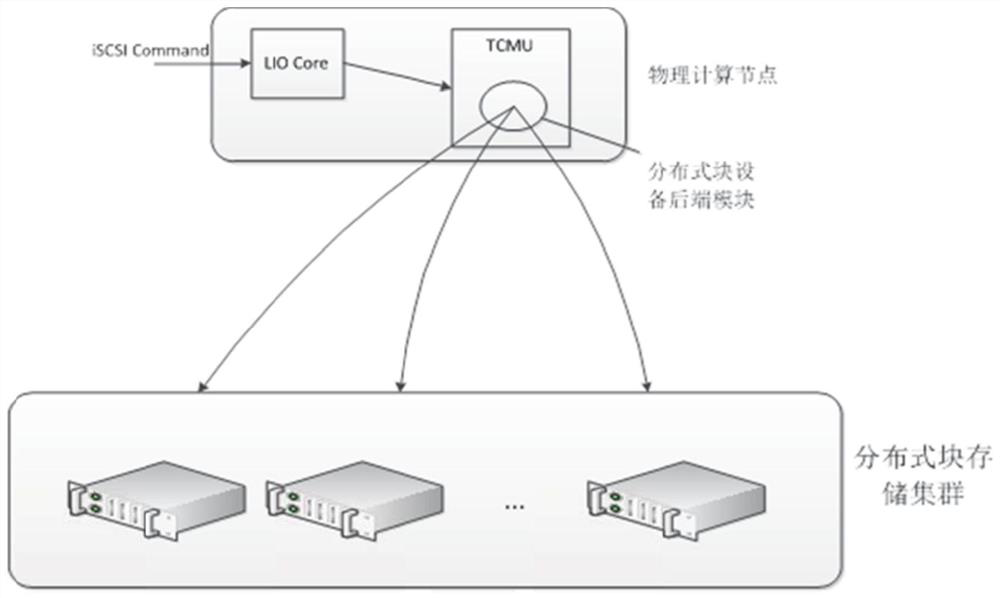
Method and system for accessing distributed block storage system in user mode
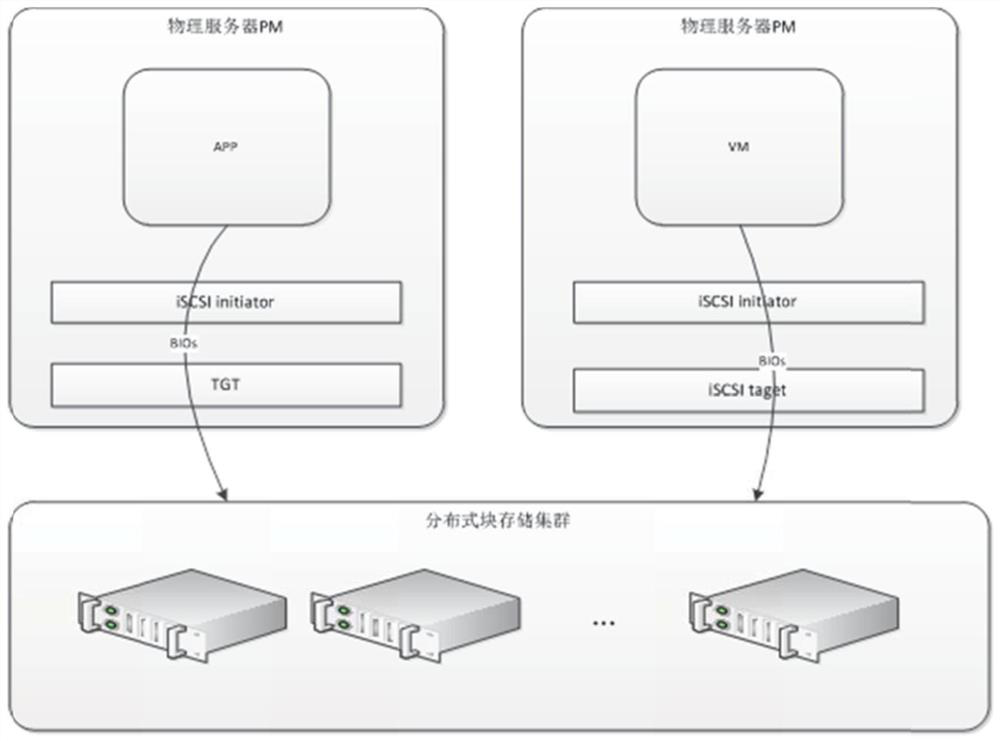
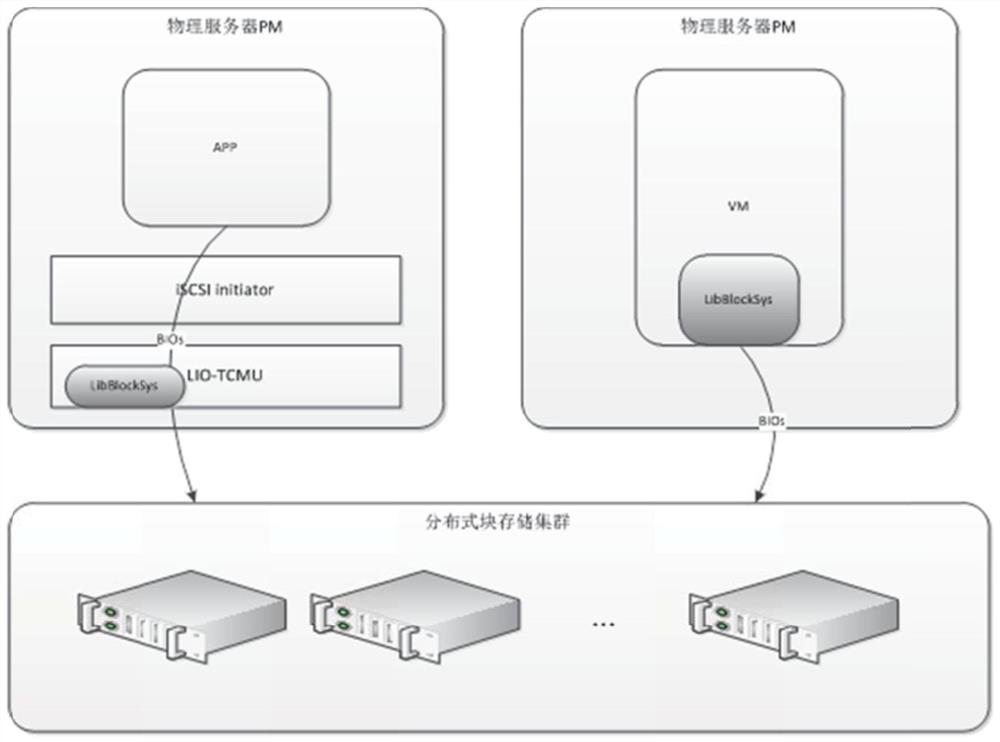
PendingCN112052291AImprove service capabilitiesImprove response speedDatabase distribution/replicationTransmissionData accessISCSI
The invention discloses a method and system for accessing a distributed block storage system in a user mode, an access module is arranged in an LIO TCMU of a computing node, and the method comprises the following steps: after the LIO TCMU is connected with an iSCSI initiator, receiving a data reading request from a data access party sent by the iSCSI initiator through the access module; determining whether target data corresponding to the data reading request exists in a cache of the access module or not; if so, returning the target data to the data access party; and otherwise, generating a corresponding thread in a pre-configured thread pool in the access module, so as to execute the thread to request target data corresponding to the data reading request from the distributed block storagecluster and return the target data to the data access party. The functions of caching, pre-reading, writing merging and the like are added to a client, so that tasks originally processed by the server are moved to the client, the service capacity and the response speed of the whole cluster are improved, and while the access performance is improved, the bandwidth overhead of the cluster is reduced, and services can be provided for more computing nodes.
Owner:SUNING CLOUD COMPUTING CO LTD
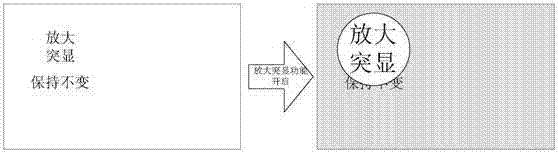
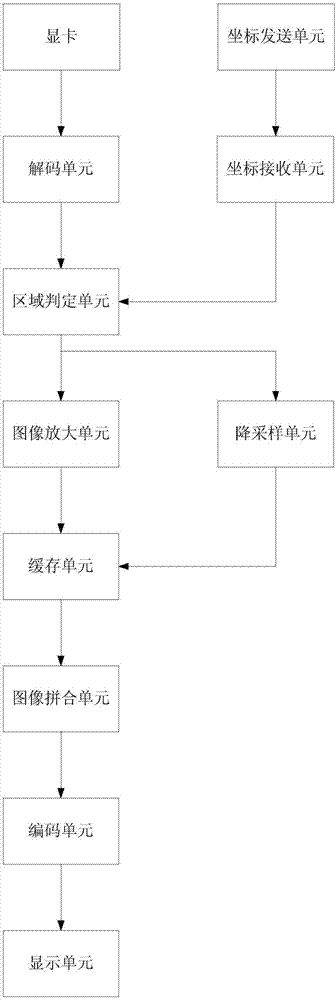
Display with regional enlargement and highlighting functions and highlighting method thereof
InactiveCN107122152AReduce brightnessImage contrast is obviousGeometric image transformationDigital output to display deviceComputer graphics (images)Display device
The present invention discloses a display with regional enlargement and highlighting functions, and a highlighting method thereof. The display comprises a video card, a decoding unit, a coordinate transmitting unit, a coordinate receiving unit, an area determination unit, an image enlargement unit, a down-sampling unit, a cache unit, an image stitching unit, a coding unit, and a display unit. The technical scheme of the present invention has the advantages that the attention area of the user can be enlarged, the non-attention area is down-sampled and is displayed in low brightness, the highlighting effect is reached, the image processor has a low requirement in bandwidth, and the user experience will not be affected by the down-sampling.
Owner:NANJING JUSHA DISPLAY TECH +1
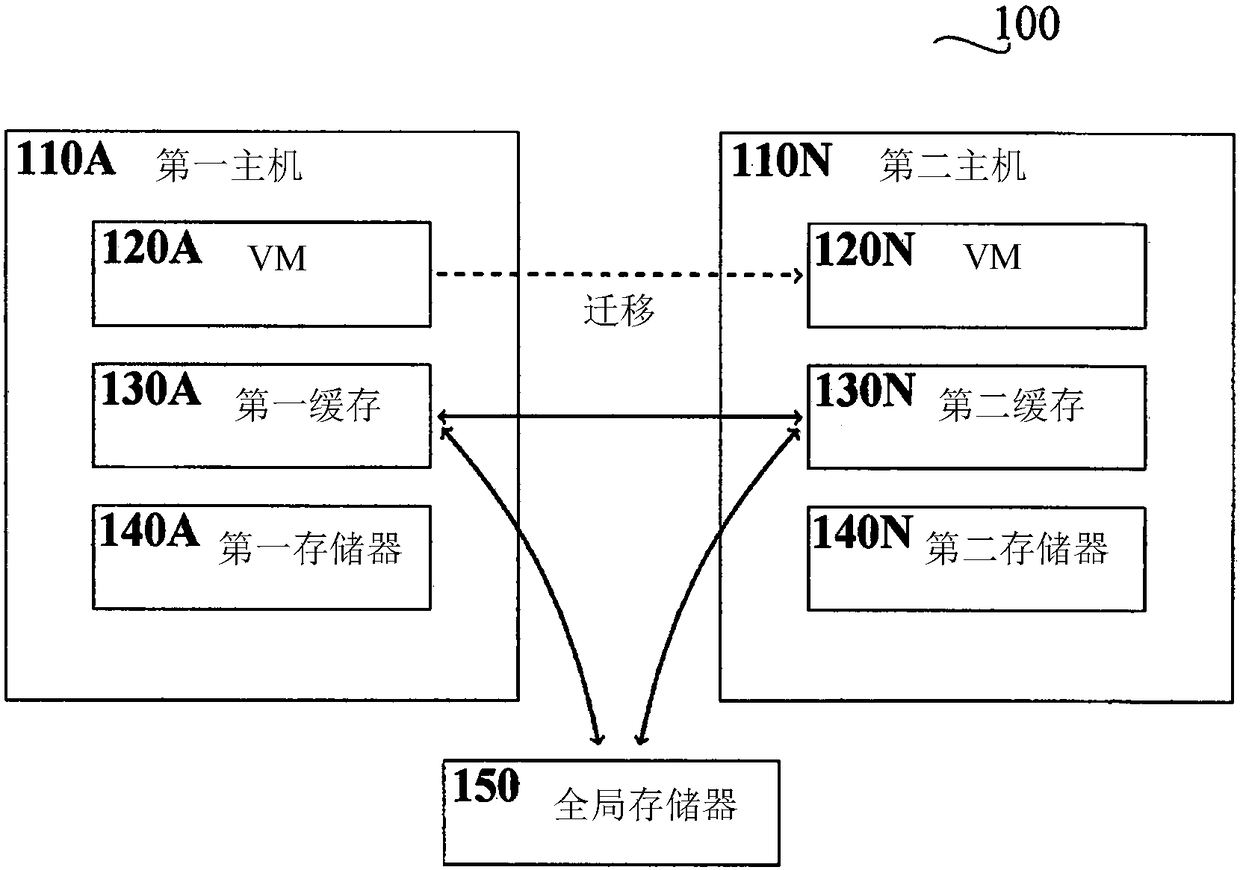
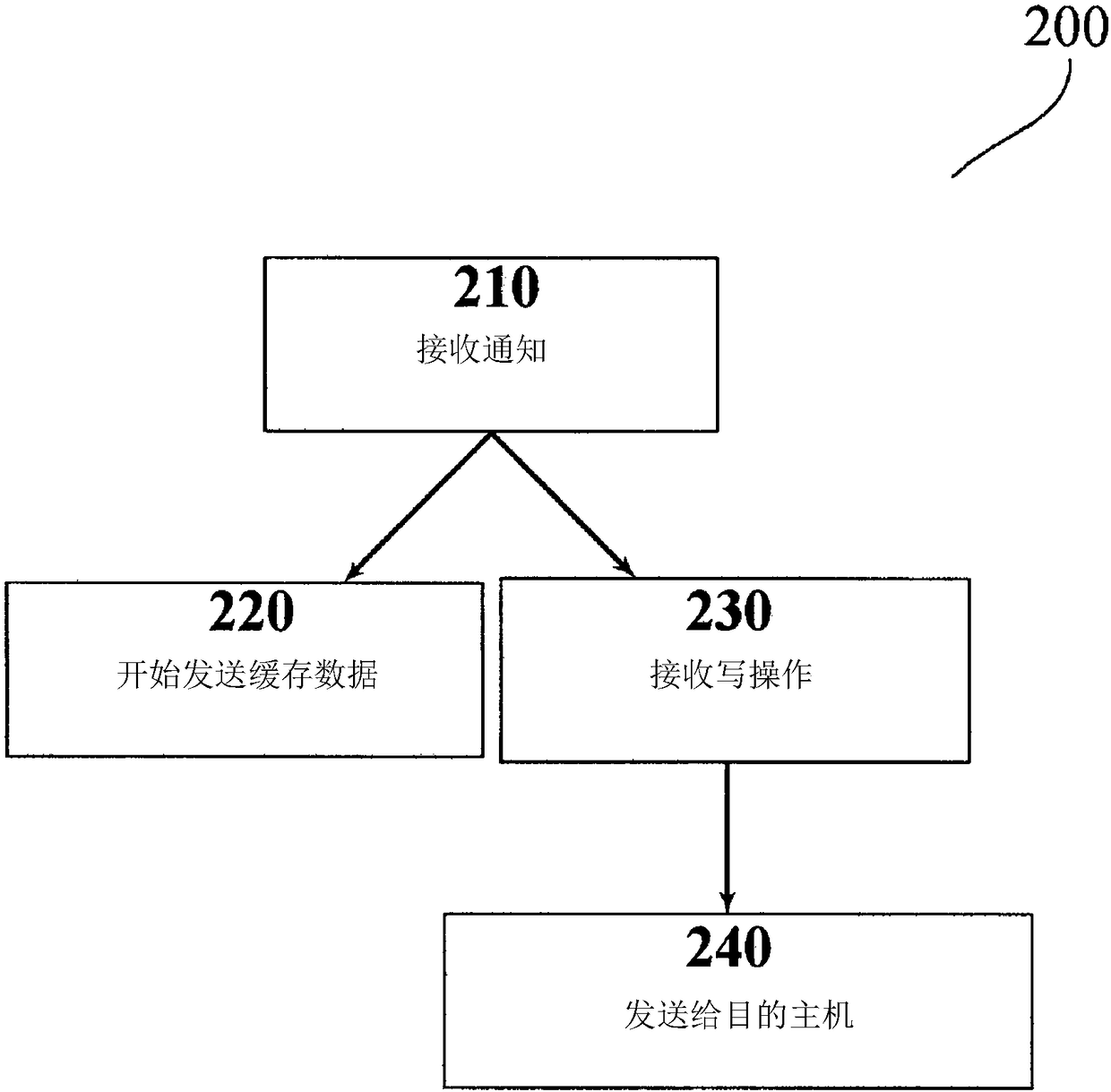
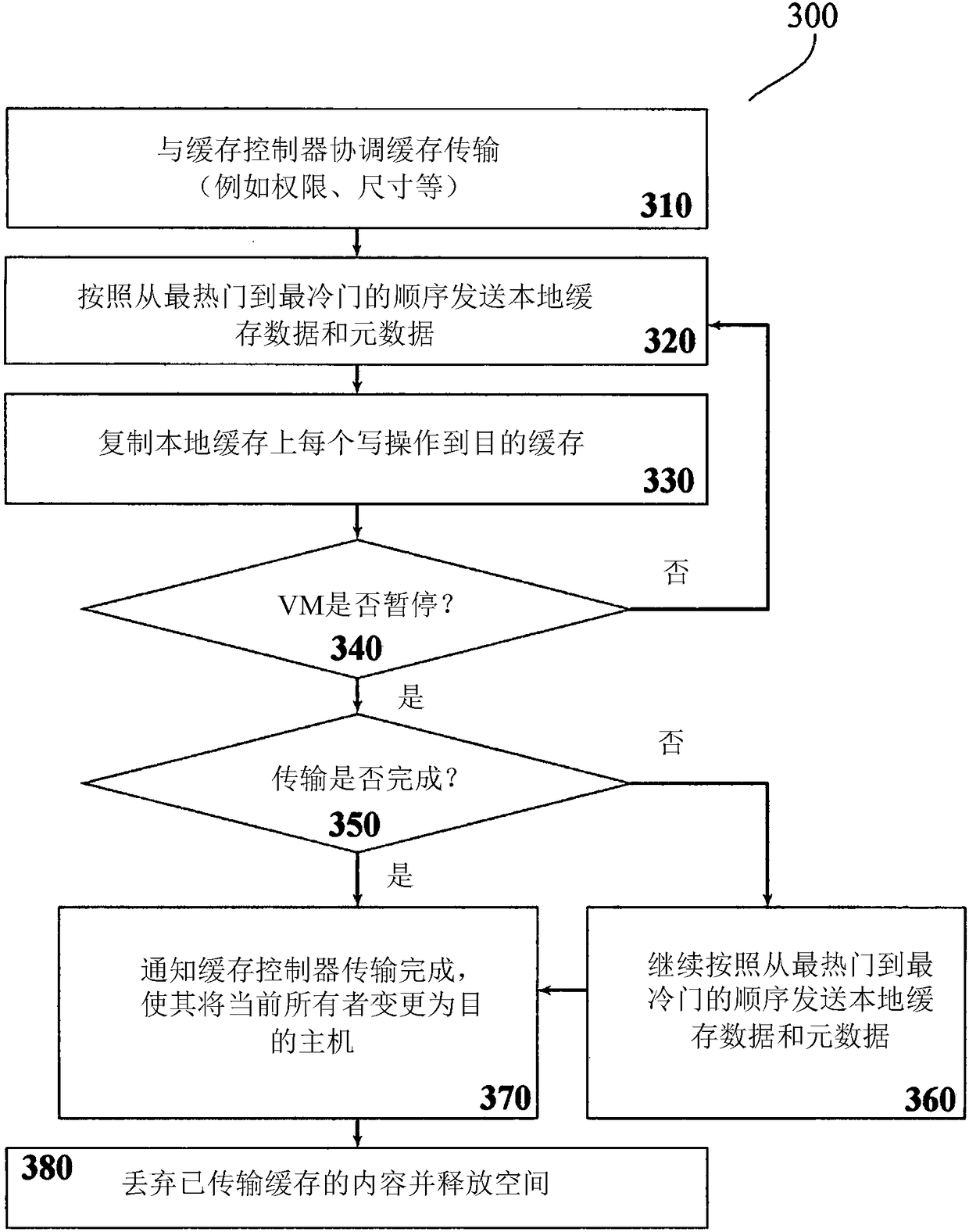
Distributed cache live migration
ActiveCN108139974AMake Migration SeamlessReduce in quantityMemory architecture accessing/allocationTransmissionDistributed cacheParallel computing
A system, comprising: a first host comprising a first cache and associated with a virtual machine, VM; and a second host comprising a second cache; wherein the first host is adapted to send cache dataof the first cache to the second host in response to a notification, said cache data associated with the VM and said notification indicating that the VM is to be migrated from the first host to the second host, and wherein the first host is adapted to send write operations associated with the VM to the second host in response to receiving the notification; and wherein the second host is adapted to apply, in response to receiving the notification, read operations associated with cache data of the VM to the first cache if said cache data is not present in the second cache, and to apply write operations associated with cache data of the VM to the second cache.
Owner:HUAWEI TECH CO LTD
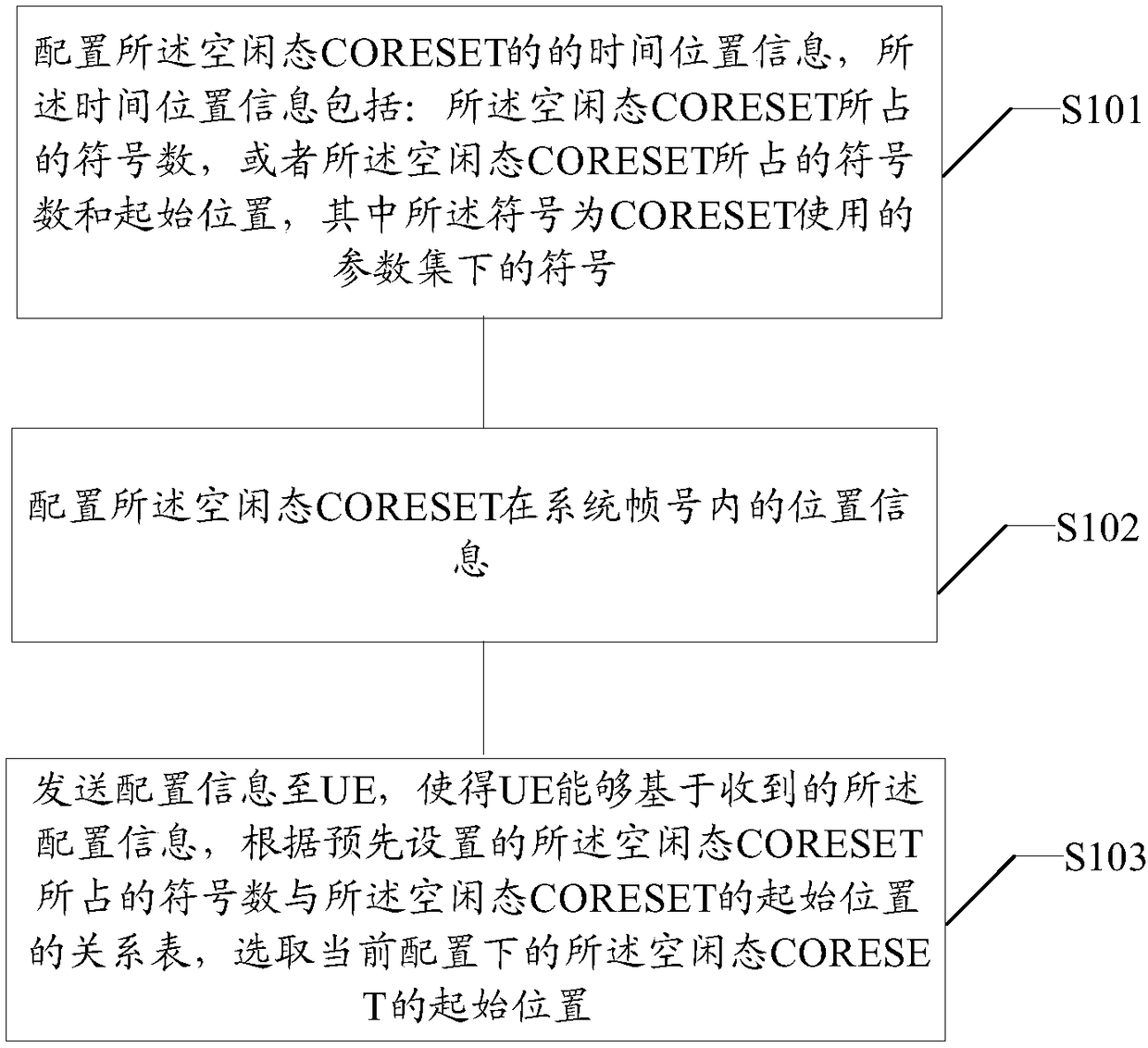
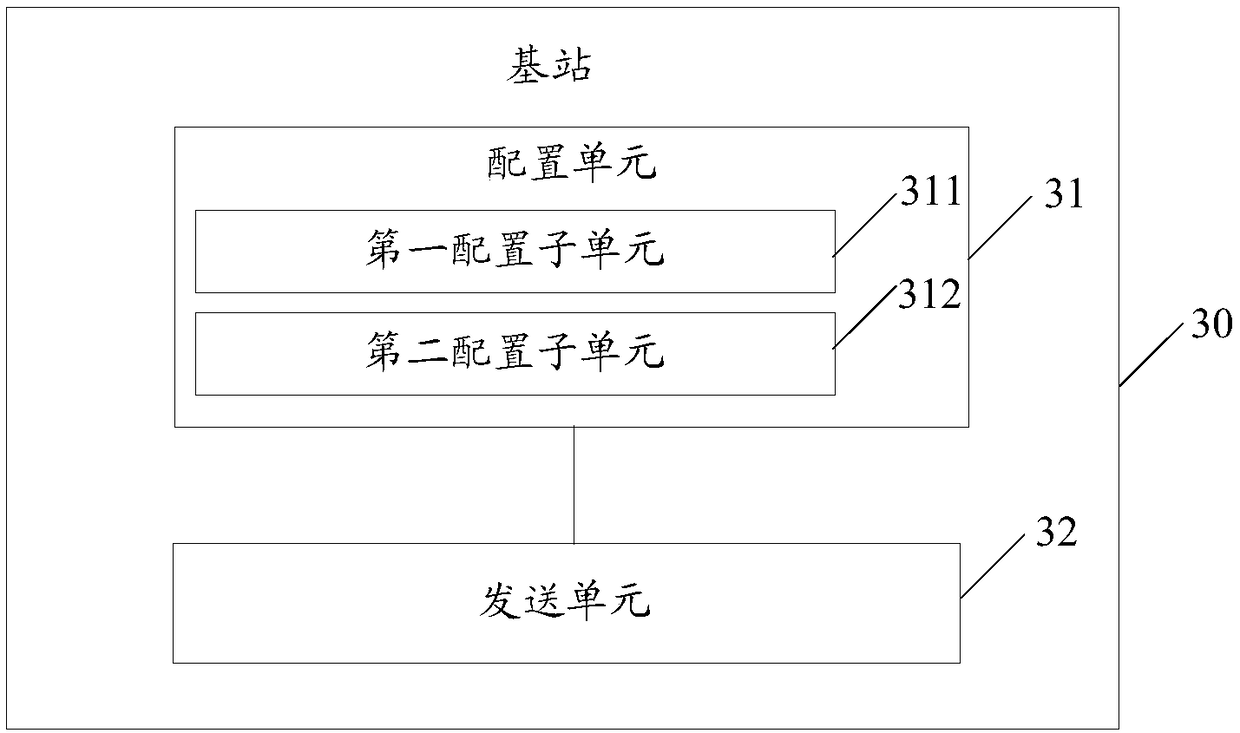
Method for distributing and obtaining CORESET in idle state, base station, user equipment, and readable medium
ActiveCN109391452AReduce bandwidth overheadImprove time-frequency tracking performanceSynchronisation arrangementModulated-carrier systemsComputer hardwareUser equipment
The invention discloses a method for distributing and obtaining a CORESET in an idle state, a base station, user equipment, and a readable medium. The method comprises the steps: configuring time andposition information of the CORESET in the idle state, wherein the time and position information includes a number of symbols occupied by the CORESET in the idle state, or a number of symbols occupiedby the CORESET in the idle state and a start position of the CORESET in the idle state, and the symbol is a symbol in a parameter set used by the CORESET; configuring the location information of theidle state CORESET in the idle state in the system frame number; transmitting the configuration information to the UE, so that the UE can select the start position of the CORESET in the idle state inthe current configuration based on the received configuration information according to a preset relation table between the number of symbols occupied by the CORESET in the idle state and the start position of the CORESET in the idle state. According to the above scheme, the method does not need to directly indicate the CORESET in the idle state, so the bandwidth overhead of signaling indicating the CORESET in the idle state can be effectively reduced.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
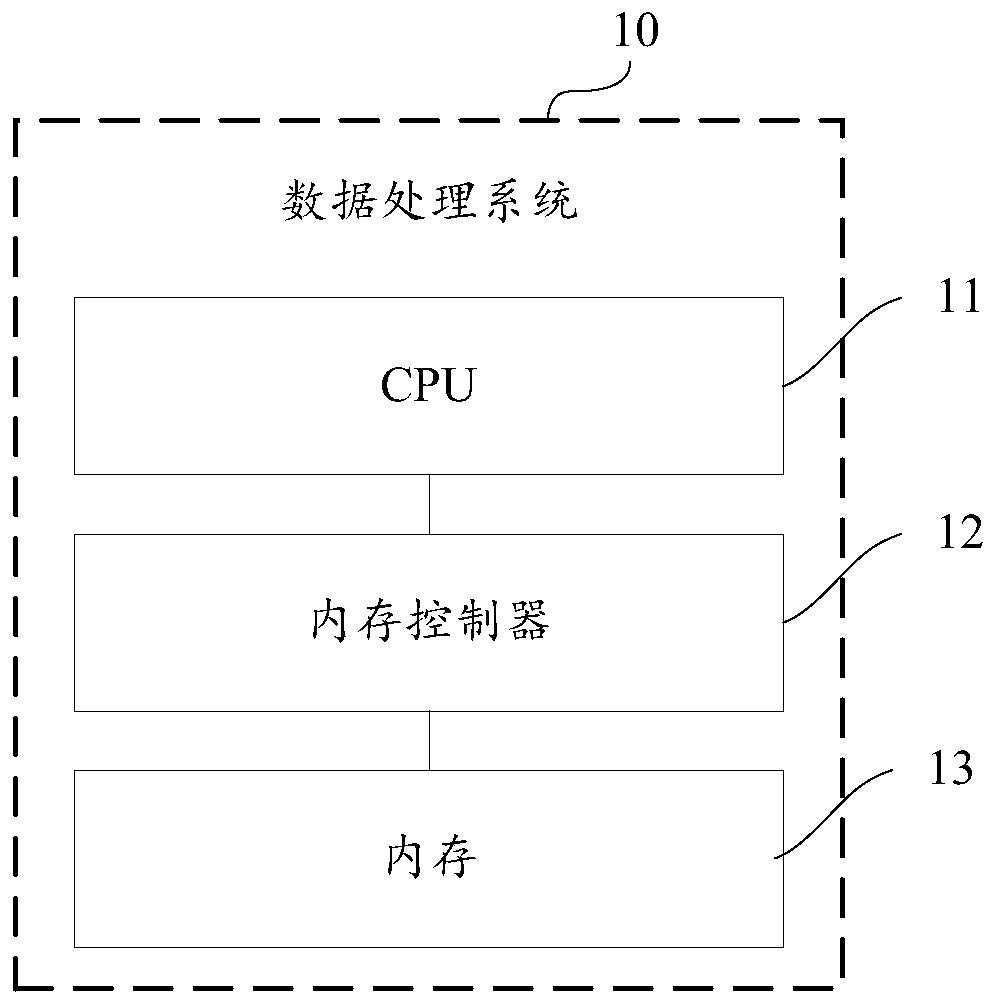
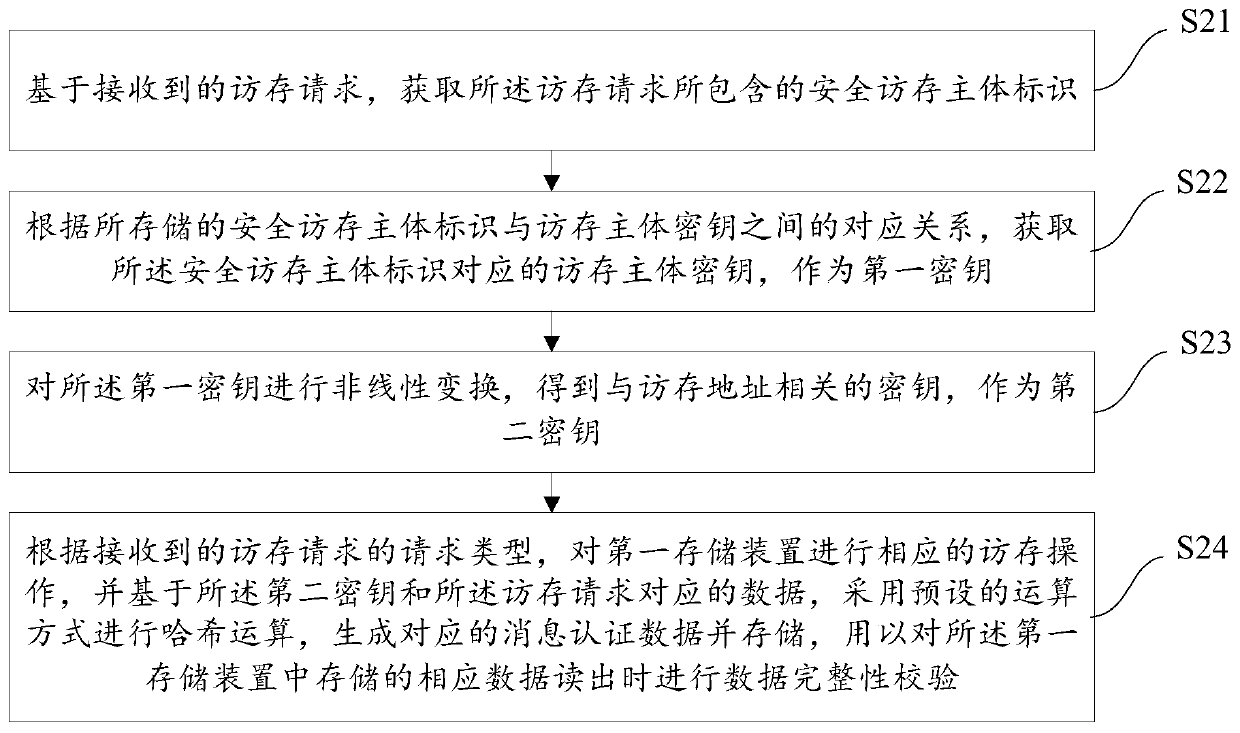
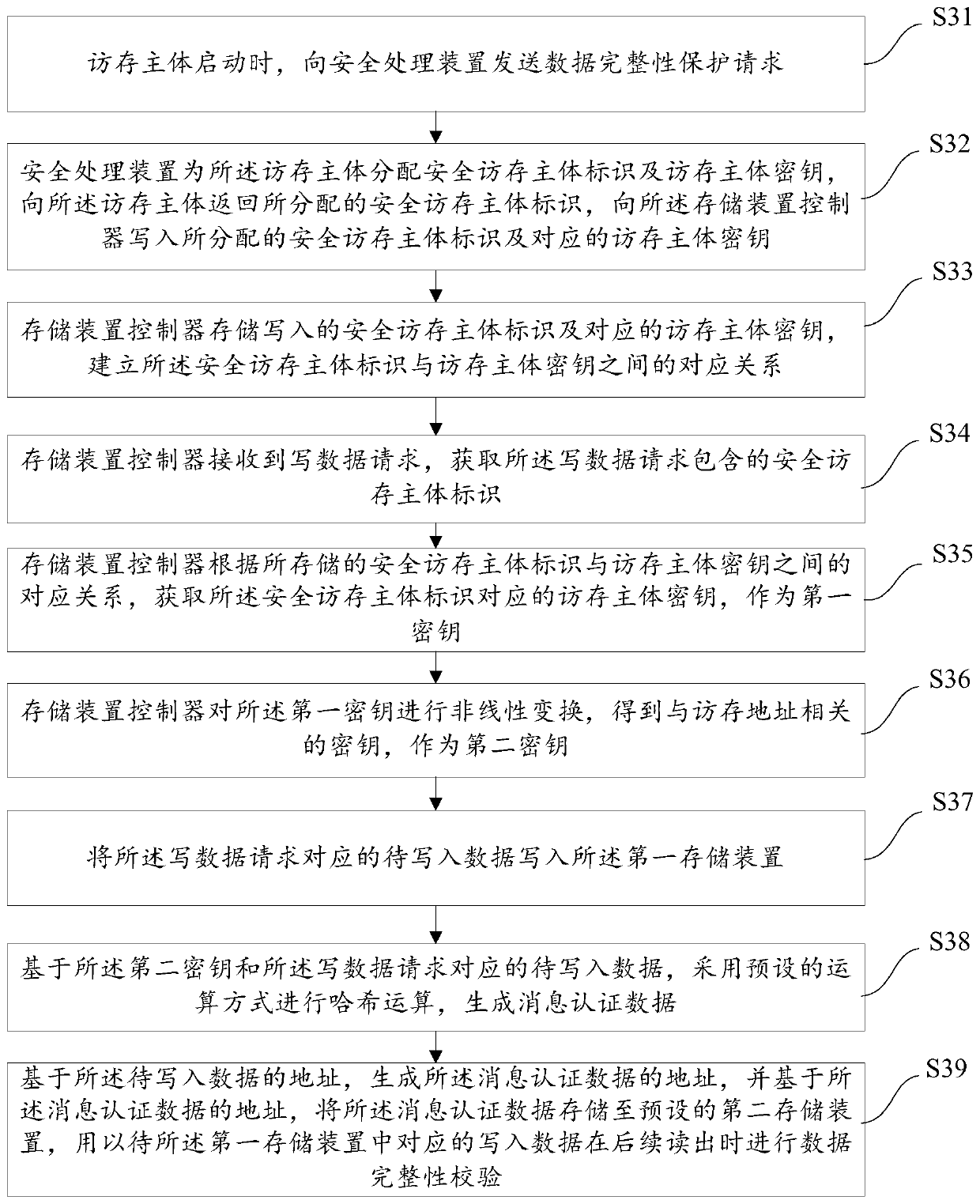
Storage device data integrity protection method, controller thereof and system on chip
PendingCN111143247AImprove integrityPrevent tamperingUnauthorized memory use protectionInternal/peripheral component protectionComputer hardwareData integrity
The invention discloses a storage device data integrity protection method, a controller thereof and a system on chip, and the method comprises the steps: obtaining a safety memory access main body identifier contained in a memory access request based on the received memory access request; acquiring a memory access main body key corresponding to the security memory access main body identifier as afirst key according to a corresponding relationship between the stored security memory access main body identifier and the memory access main body key; carrying out nonlinear transformation on the first secret key to obtain a secret key related to a memory access address; the method comprises the steps of receiving a request type of a memory access request; and performing corresponding memory access operation on a first storage device, performing hash operation by adopting a preset operation mode on the basis of the second key and data corresponding to the memory access request, generating corresponding message authentication data, and storing the message authentication data for performing data integrity verification when the corresponding data stored in the first storage device is read. According to the scheme, integrity protection can be provided for the data in the first storage device.
Owner:HYGON INFORMATION TECH CO LTD
Link layer and network layer combined control multi-satellite networking method
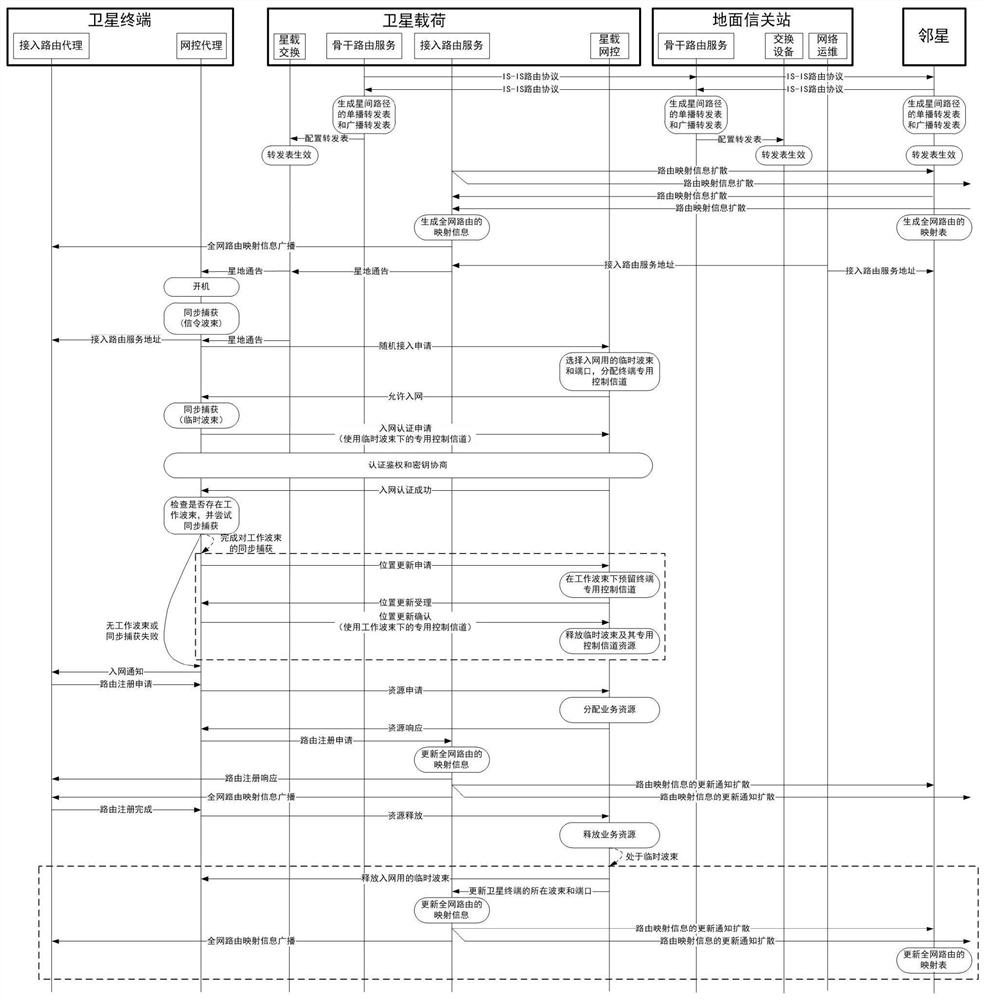
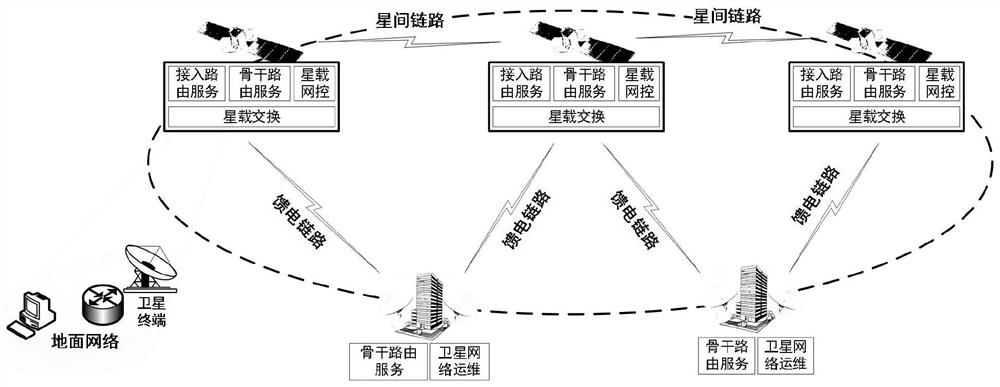
PendingCN113965252AReduce the number of interactionsReduce bandwidth overheadRadio transmissionTelecommunicationsNetworking protocol
The invention discloses a link layer and network layer combined control multi-satellite networking method, and relates to the field of satellite communication. According to the method, when a satellite terminal applies for accessing a satellite network, a link layer dynamically selects a network access beam and a port, and triggers a network layer to execute user route registration and whole network diffusion, so that the interaction times and bandwidth overhead of a networking protocol are reduced, and rapid convergence of the route and rapid network access of the terminal are realized. According to the invention, the network access time and the routing convergence time of the multi-satellite networking system can be reduced, and the random network access capability is improved.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Method and system for locality non-cluster index based on streaming data
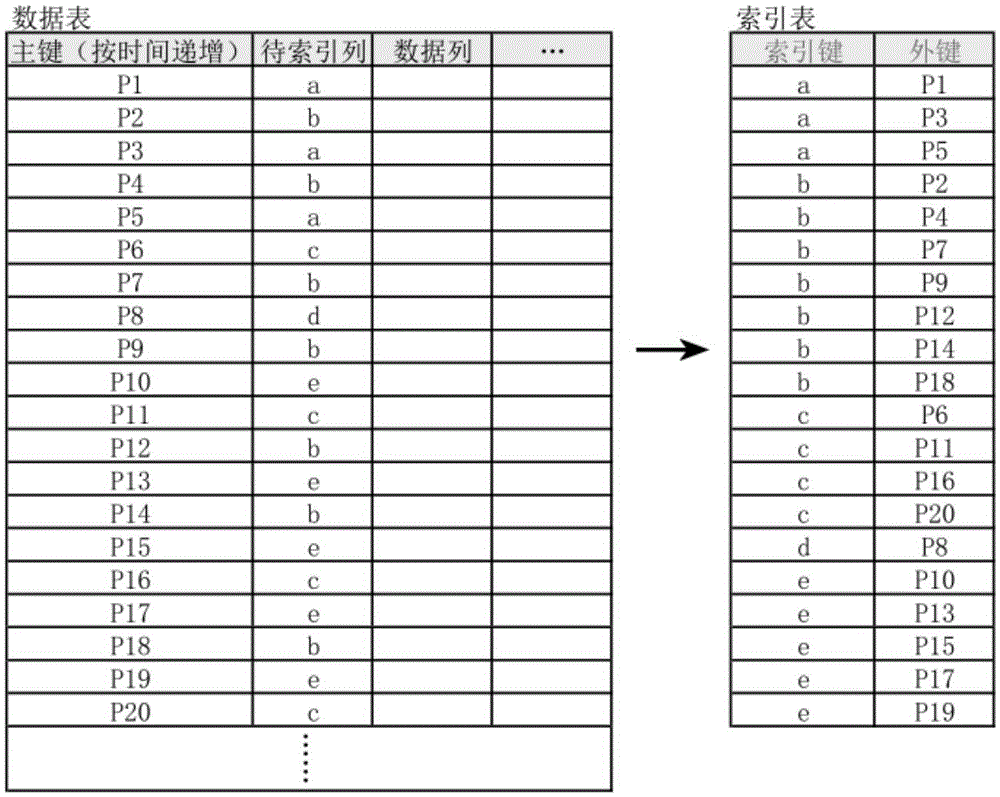
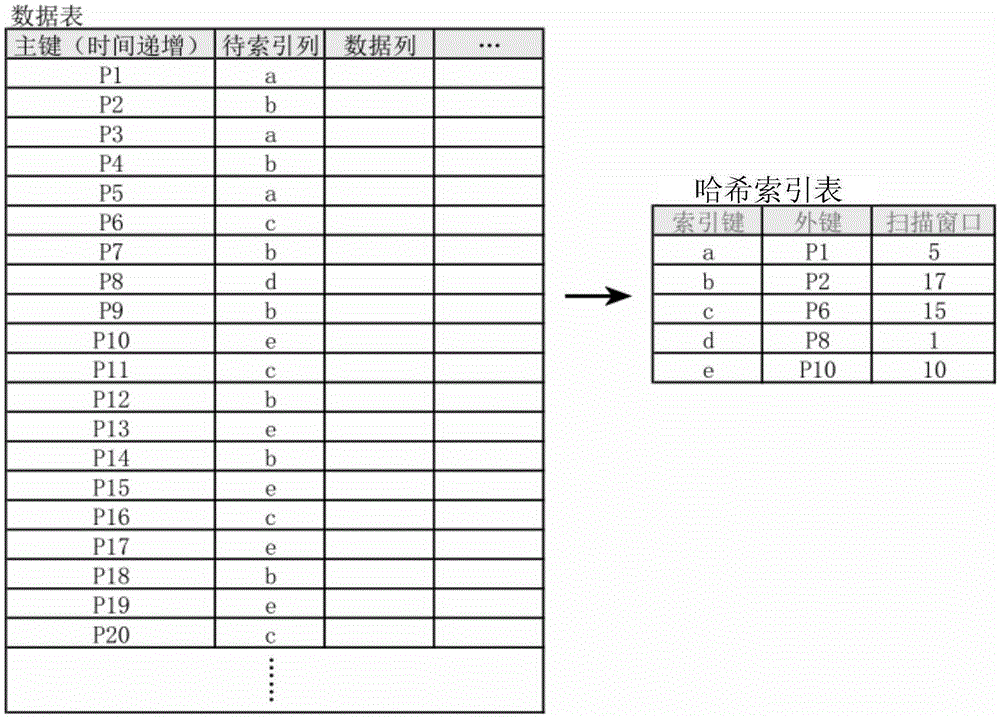
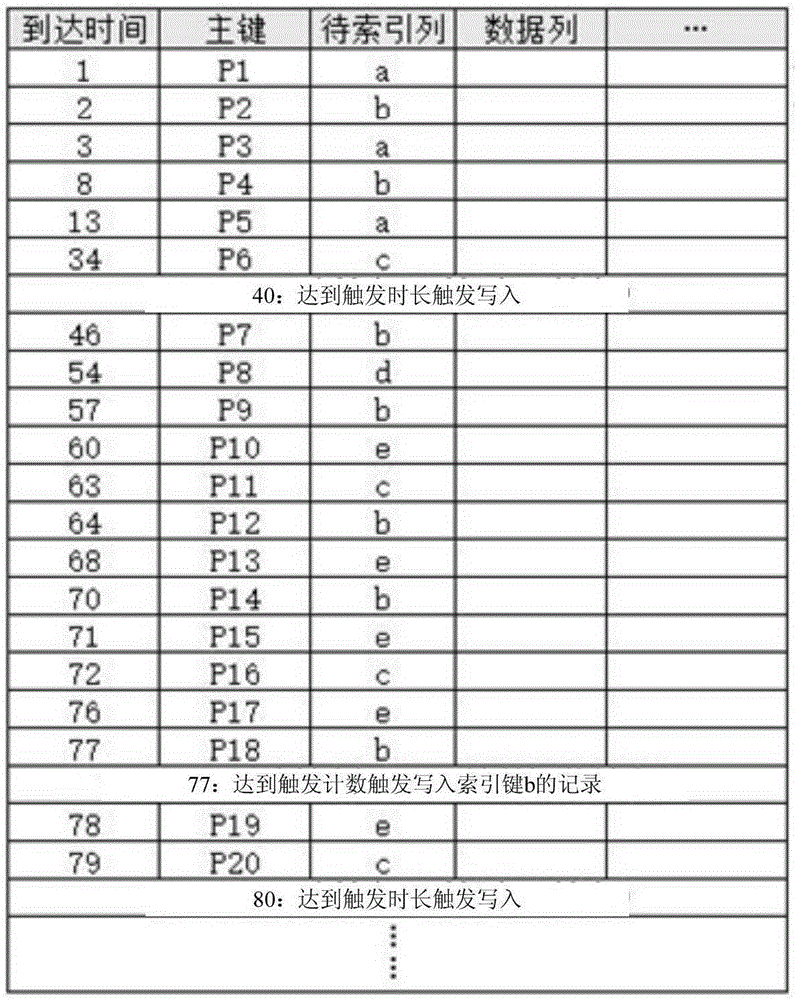
ActiveCN105335475ASave spaceReduce bandwidth overheadSpecial data processing applicationsStream dataIndex method
The invention discloses a method and a system for locality non-cluster index based on streaming data. The method comprises: a real-time update step: updating index records generated aimed at each received piece of streaming data in a Hash index table in real time, the index record recording an index key in the streaming data, a major key corresponding to the index key when the index key appears for the first time, and the number of data covered from first appearance to last appearance at present; a writing-in step: when a trigger condition is achieved, writing the index records in the Hash index table in an index table, and continuing to execute the real-time update step. The method greatly reduces space of the index table and bandwidth cost generated by establishing the index table. The index method combines random access and sequential scanning, effectively uses time locality characteristic of the streaming data, and is more aligned with an access model of a storage medium, and improves inquiry efficiency of index data.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
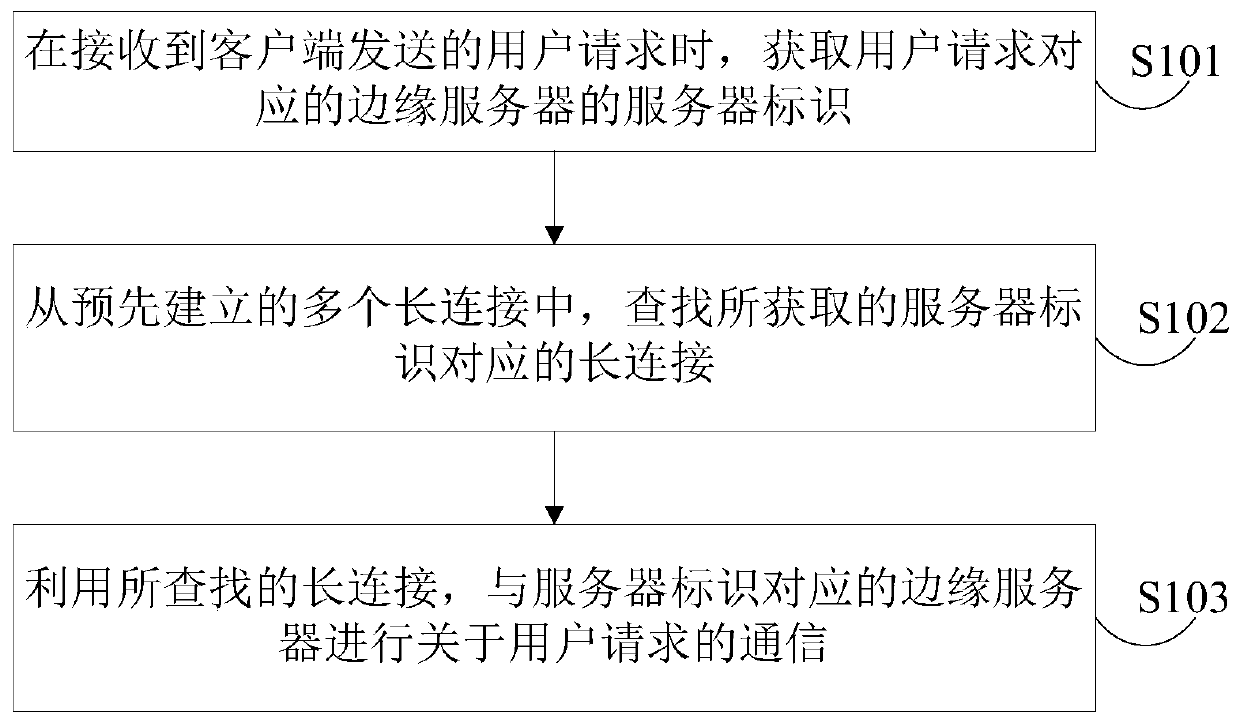
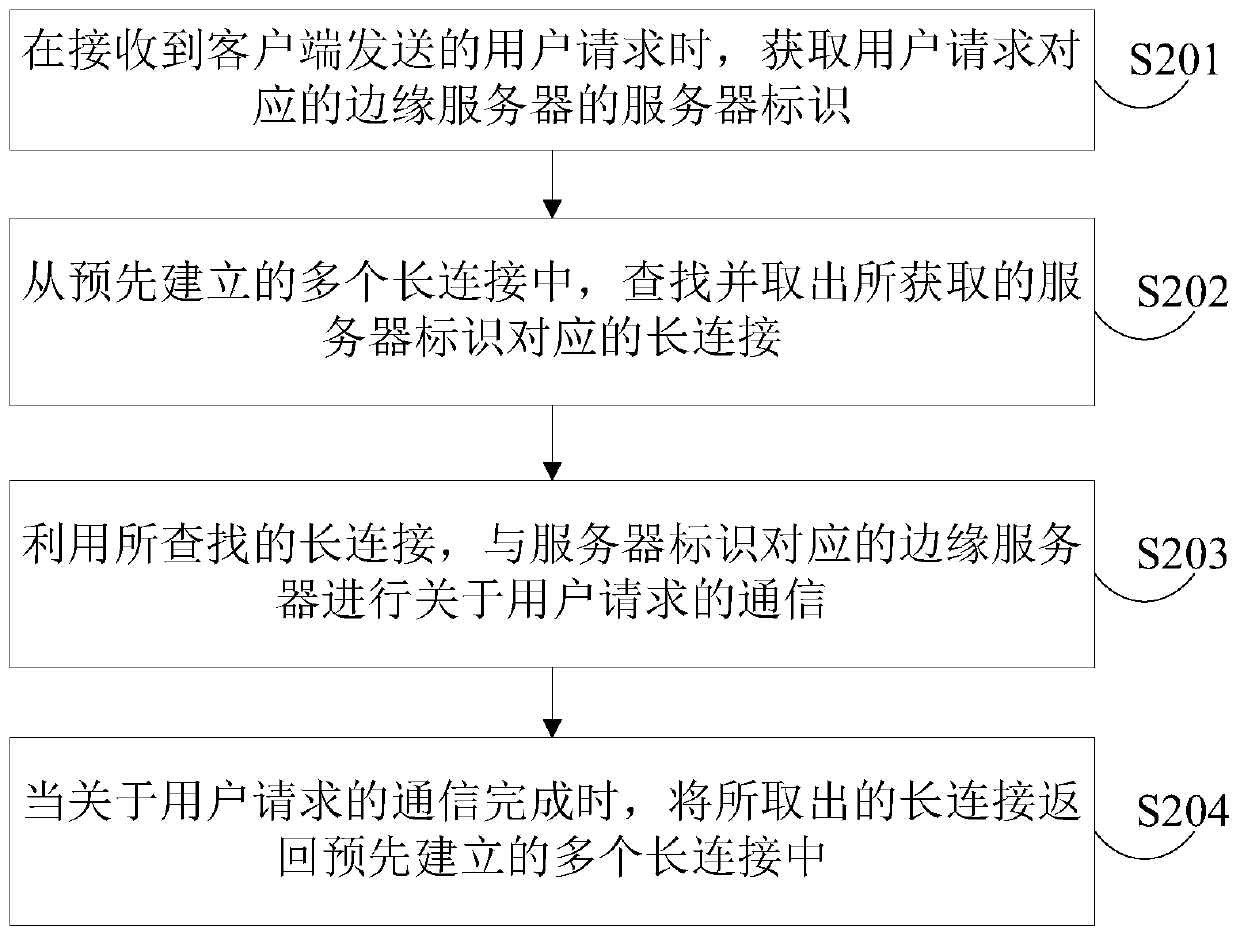
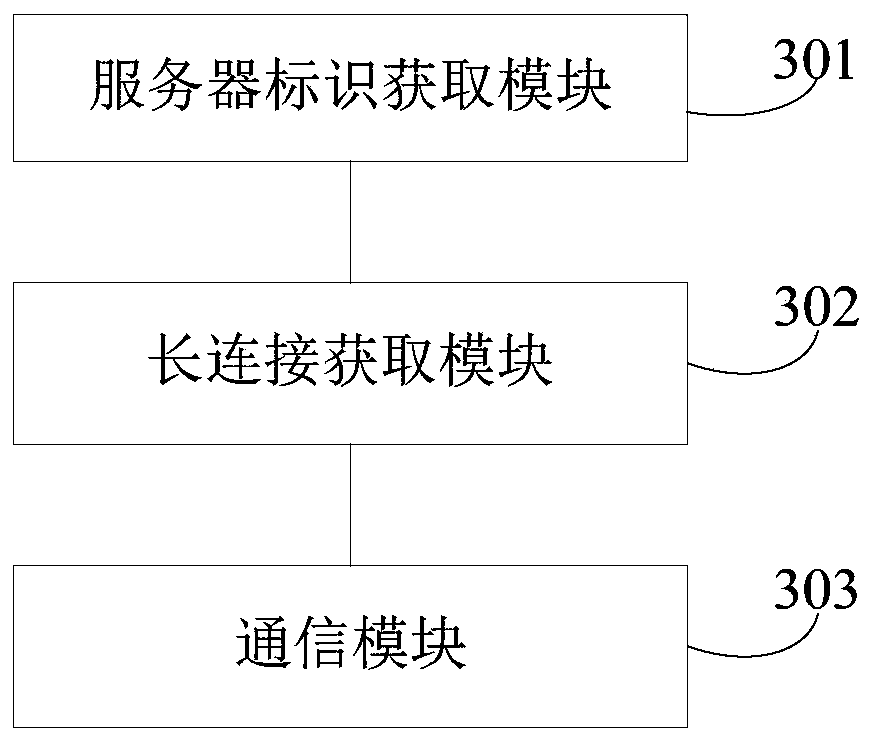
Communication method, device and server
The embodiment of the invention provides a communication method, a communication device and a server. The communication method is applied to a management server. When a user request sent by a client is received, a server identifier of an edge server corresponding to the user request is acquired. A long connection corresponding to the server identifier is searched from a plurality of pre-established long connections. The plurality of pre-established long connections are respectively pre-established long connections with each edge server before the management server receives a user request sentby a client. The communication about the user request is performed with an edge server corresponding to the server identifier by using the searched long connection. According to the scheme, the time cost and bandwidth overhead of communication can be reduced.
Owner:JOYME PTE LTD
A stream text transmission method
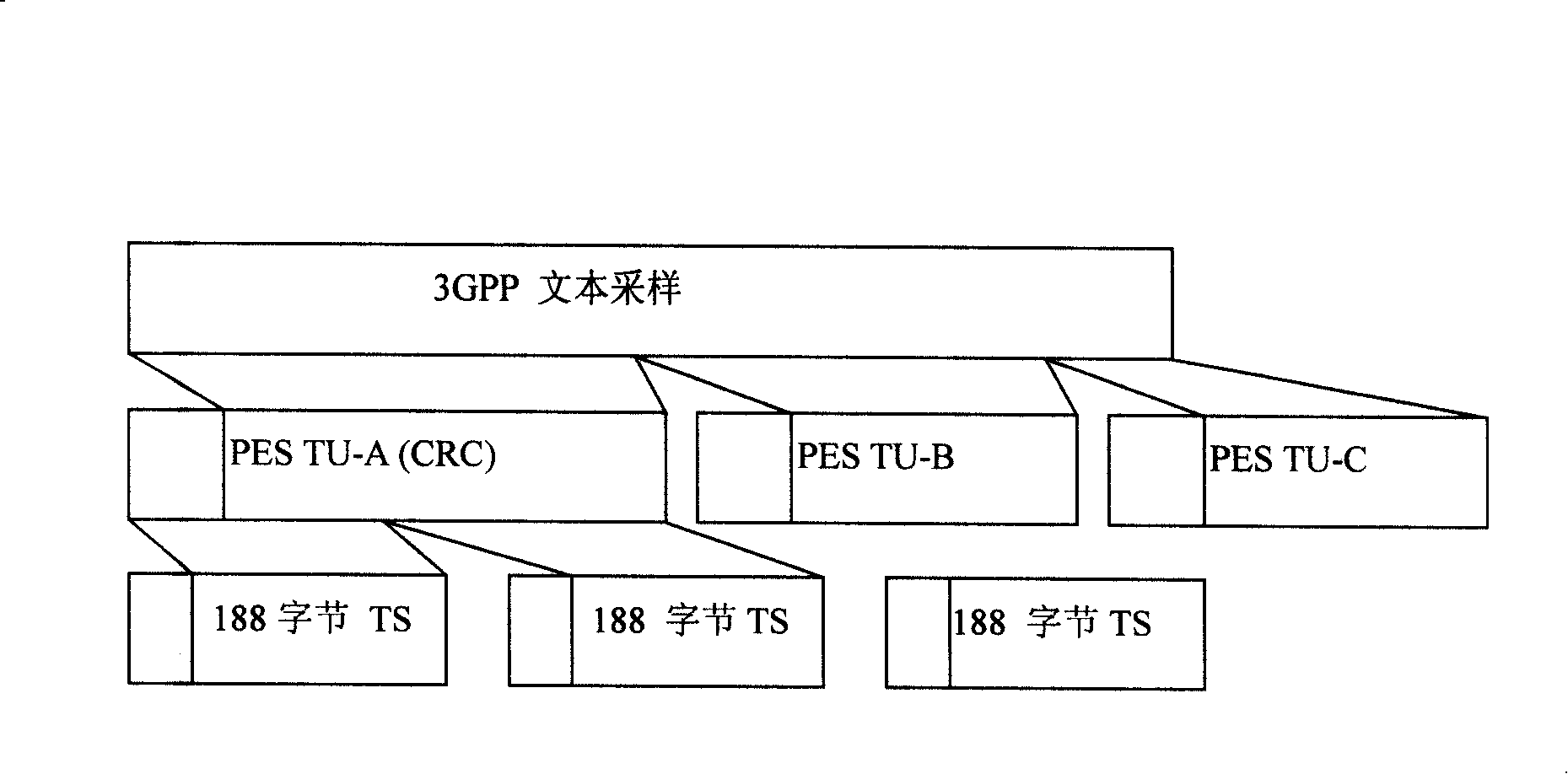
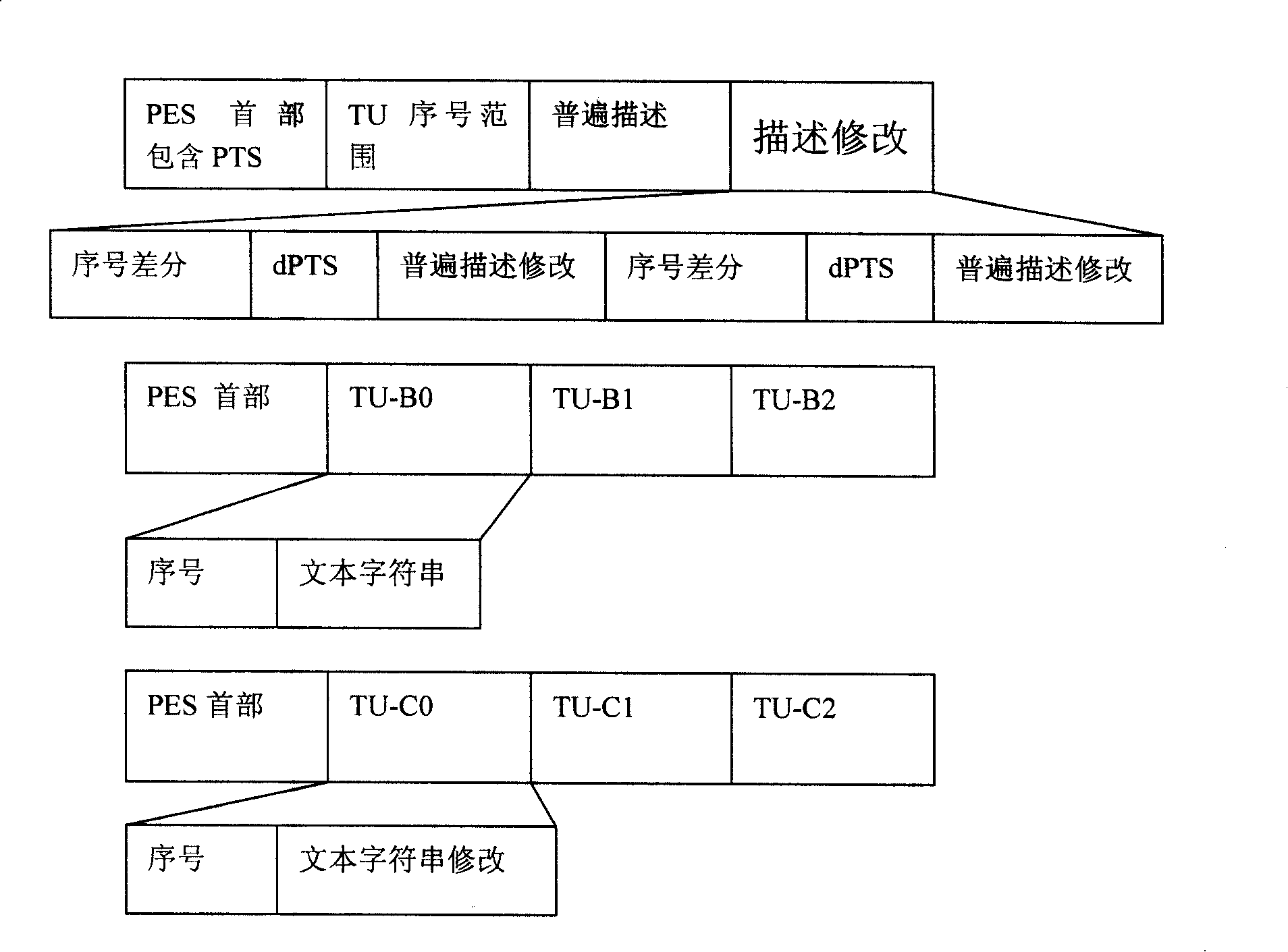
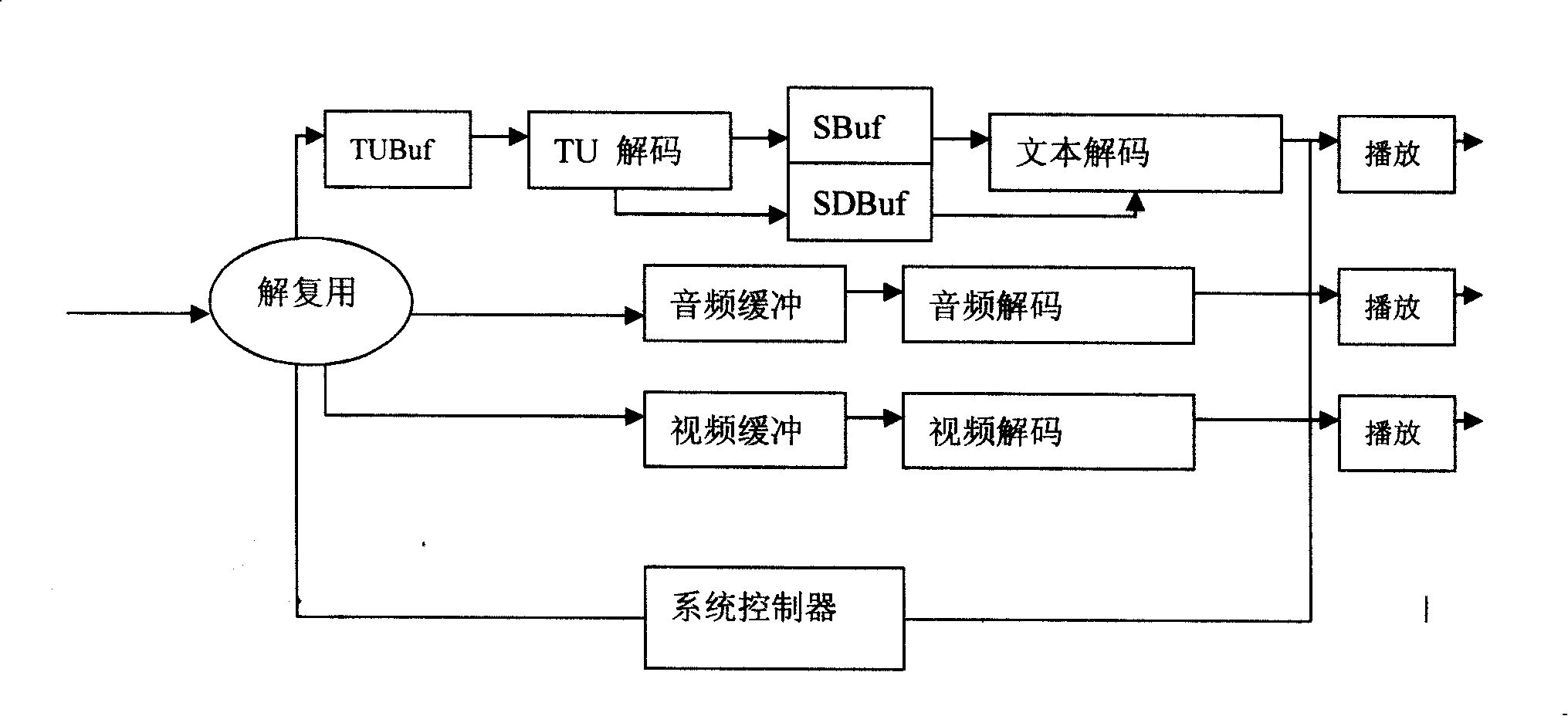
ActiveCN101237446AReduce overheadGuaranteed reception qualityData switching networksTimestampTransport layer
The invention relates to a method for transmitting a streaming text. The method of the invention provides a method for directly mapping a 3GPP streaming text to a transport layer in order to realize the streaming text transmission with high efficiency and low broadband expenditure. The invention provides a method for bearing the difference text timestamp and the synchronization by a PES, which can save the expenditure of the broadband. The invention provides a method for detecting and packing a TU with different importance and different error codes CRC, which guarantees the receiving quality.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
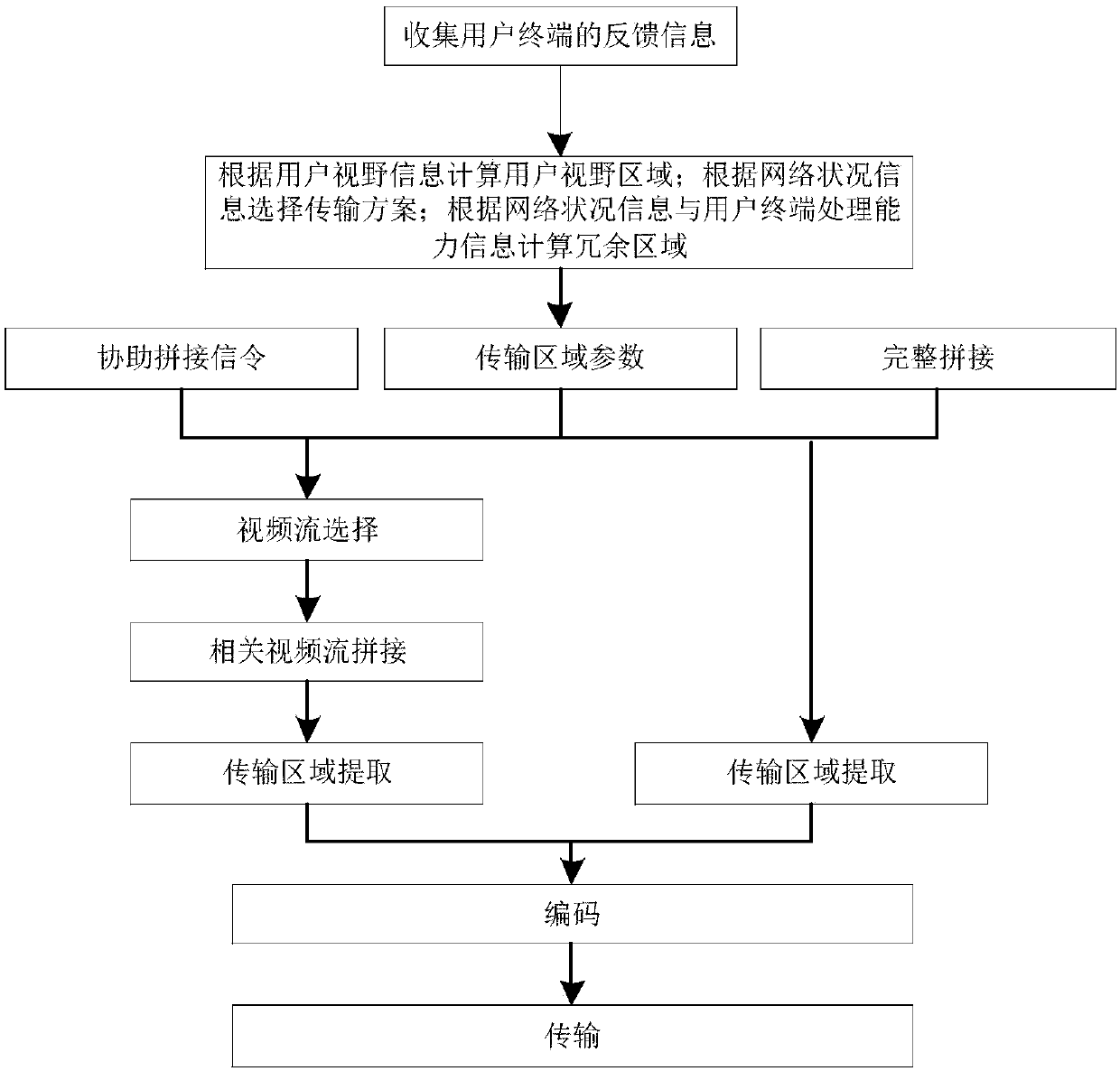
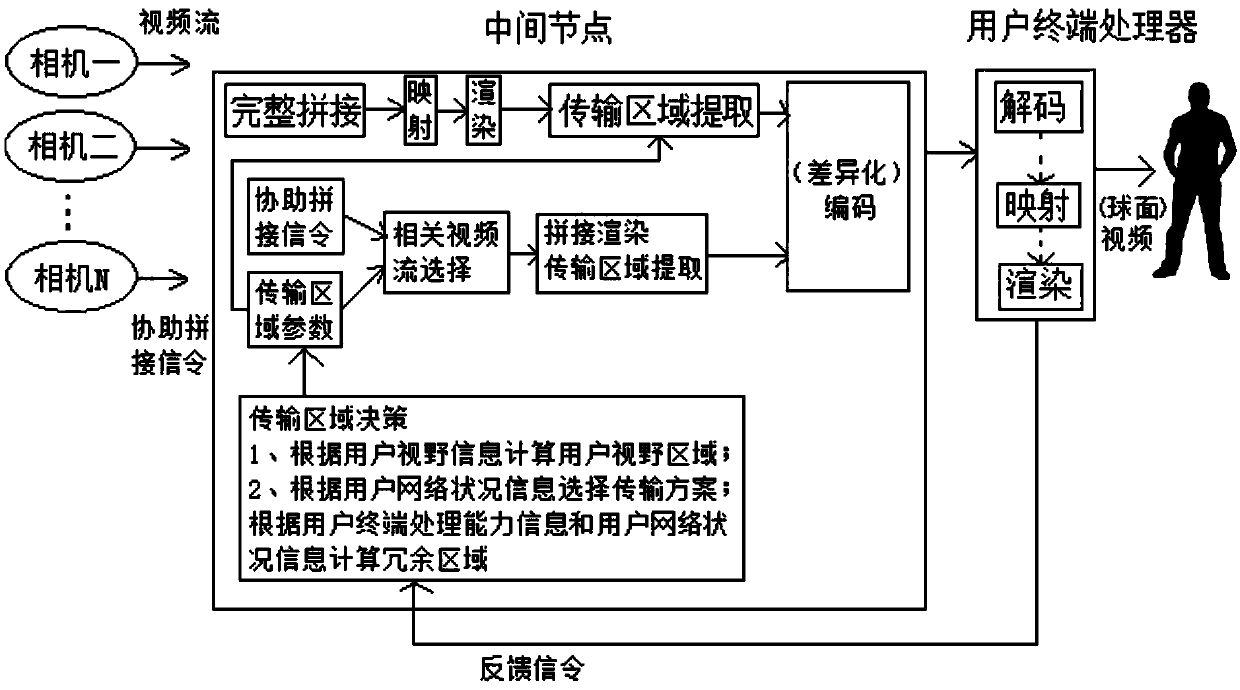
Panoramic video transmission method and system based on node calculation
InactiveCN110708562AReduce processing delayReduce bandwidth overheadTelevision system detailsColor television detailsTelecommunicationsVideo streaming
The invention provides a panoramic video transmission method and system based on node calculation. The method comprises the following steps: obtaining feedback information of a user terminal in real time through an intermediate node, calculating a user visual field region according to the user visual field information, selecting a video stream accommodating the user visual field region for splicing, and obtaining a processed video stream; selecting a transmission scheme according to the user network condition information, extracting a transmission area for the processed video stream, and transmitting the transmission area code to a corresponding user terminal; wherein the transmission scheme comprises non-redundancy transmission and redundancy transmission, in the non-redundancy transmission, the transmission area is a user view area, in the redundancy transmission, the transmission area is a user view area plus a redundancy area, and the redundancy area is calculated according to usernetwork condition information and user terminal processing capability information. By combining the feedback information of the user terminal, the processing time delay can be effectively reduced, and the bandwidth overhead is reduced, so that the consumption experience of the user is integrally improved.
Owner:SHANGHAI JIAO TONG UNIV
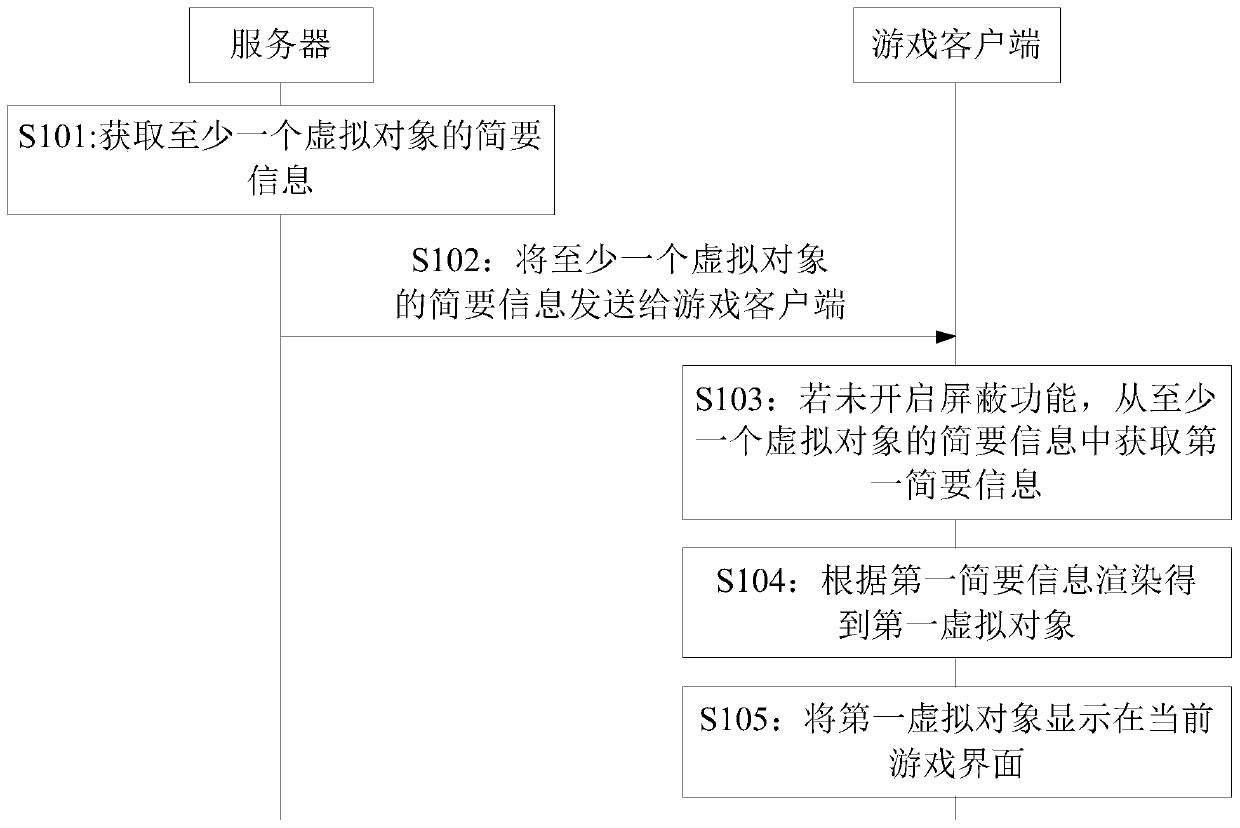
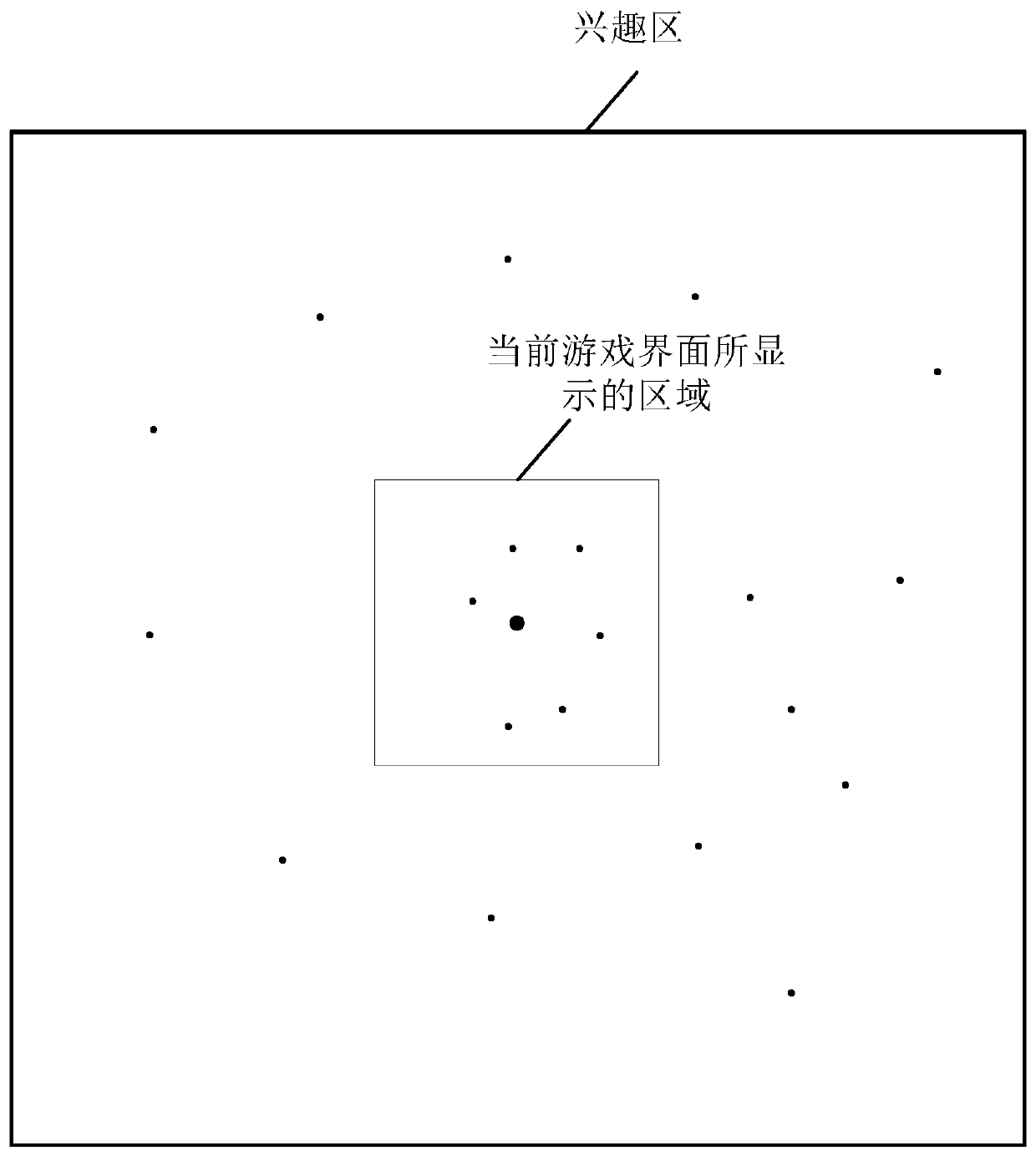
Virtual object display method and device and storage medium
PendingCN111282273AReduce bandwidth overheadReduce the amount of synchronizationVideo gamesComputer networkEngineering
The embodiment of the invention provides a virtual object display method and device and a storage medium. According to the scheme, the method comprises the steps that: the server acquires brief information of at least one virtual object, wherein at least one virtual object is located in an interest area of the virtual object corresponding to the game client; the server sends the brief informationof the at least one virtual object to the game client; and if the game client does not start the shielding function, the game client acquires first brief information from the brief information of theat least one virtual object, carries out rendering according to the first brief information to obtain a first virtual object, and displays the first virtual object on the current game interface. In the embodiment of the invention, the server sends the first brief information to the game client, so that the synchronization amount of the downlink data is reduced, the bandwidth overhead of the serveris saved, and the network performance is improved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com