Database attribute sensitivity quantification method based on attack probability
A quantitative method and database technology, applied in the field of data security, can solve problems such as inaccuracy, incomplete definition of sensitive information, ignorance of semantic information, etc., to achieve authentic and credible results and retain data availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] Table 1
[0051] ID sex Birthday Nation Salary(50k)
10564 M 0324 China > 12368 M 0930 China <
13851 F 0930 Brazil > 18635 F 0506 China <
20654 M 0825 USA <
25101 F 1114 China >
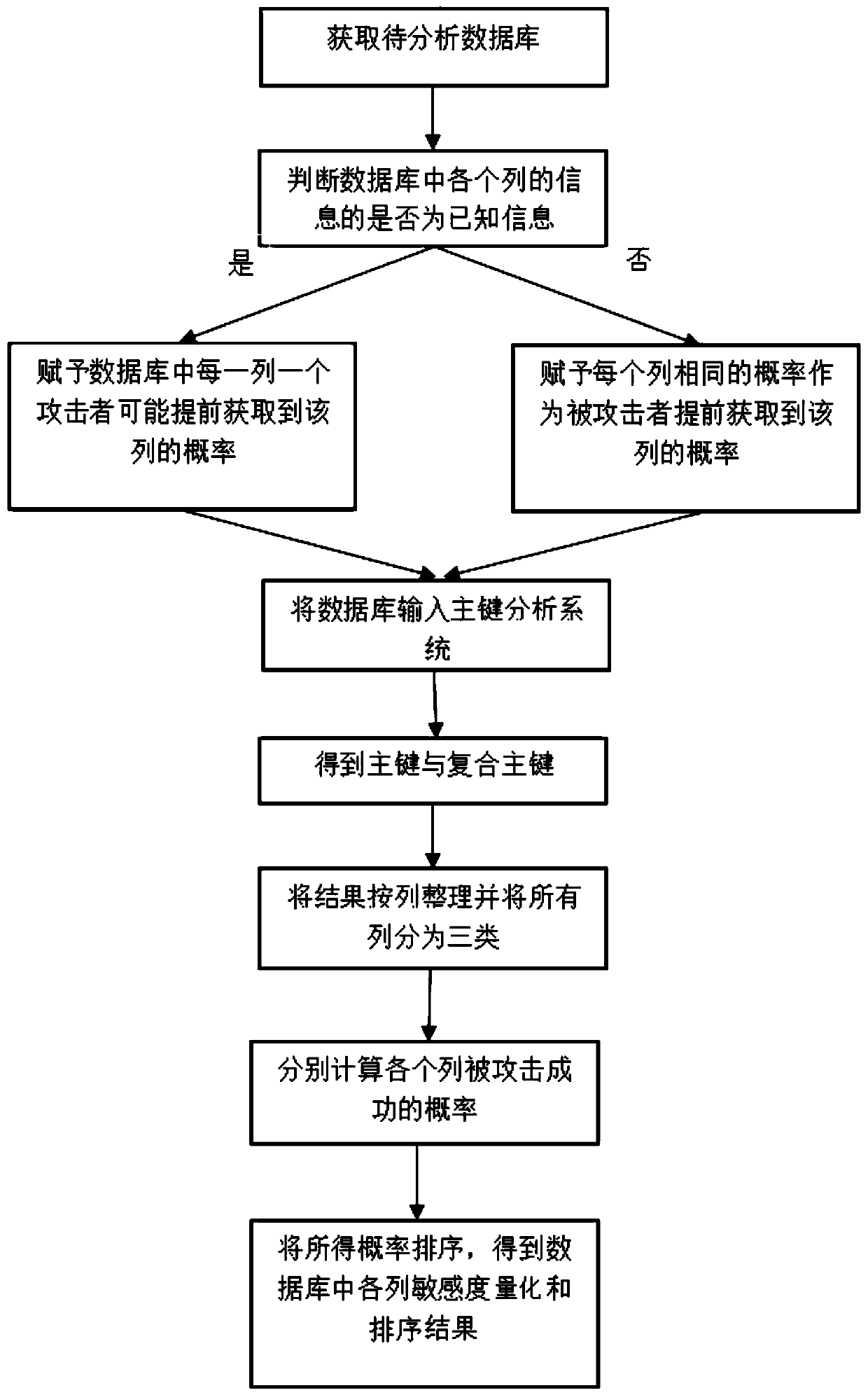
[0052] Table 1 is a personal information database, where each row represents a person’s ID, gender, date of birth, nationality and salary information in Table 1. The sensitivity analysis of this database is now carried out. The specific process is as follows:
[0053] Give each column a probability of being acquired by the attacker in advance. After the experience of the data manager and comprehensive analysis based on the published information, give each column a probability of being acquired by the attacker in advance P={0.1, 0.5, 0.5, 0.8, 0.5 };
[0054] Enter the database into the framework of the primary key search algorithm, analyze its primary key and composite primary key, and the output result is:
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com