Test case design method for discovering memory leak bug
A technology for test cases and memory leaks, applied in software testing/debugging, computing, error detection/correction, etc., can solve problems such as memory leaks, one-time memory leaks, implicit memory leaks, etc., to reduce negative effects and ensure comprehensive performance and accuracy, transaction stock data and incremental data are accurate and real-time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
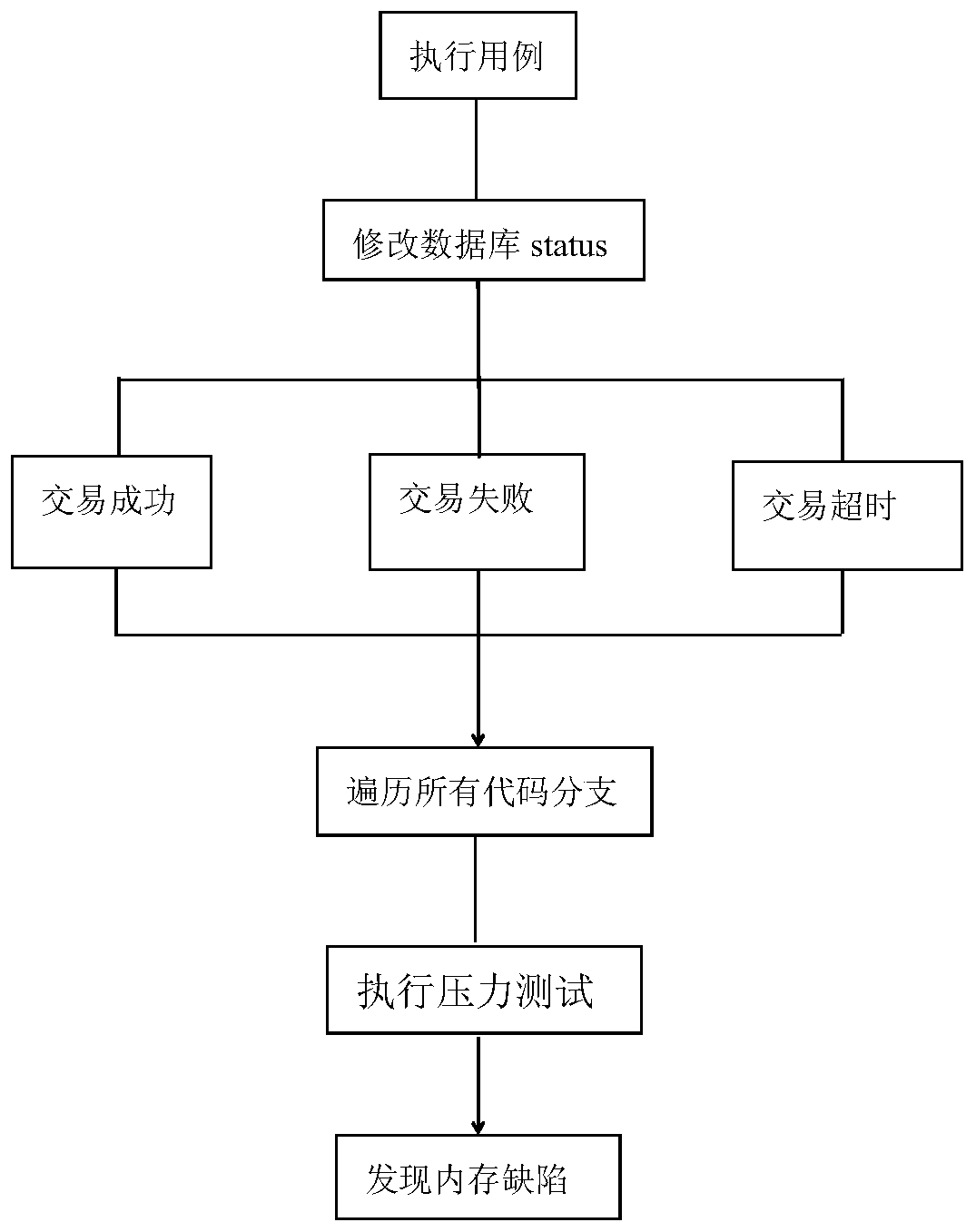
[0030] Embodiment 1, find the test case design method of memory leak bug, as figure 1 shown;
[0031] 1. The usage scenarios of the present invention are:
[0032] The present invention is suitable for the business system of the cluster structure, and the transaction data volume of the tested system is large, and the number of concurrency is high;
[0033] Two, the system architecture description of the present invention:
[0034] The tested system is a clustered system, and the system services are installed on multiple hosts, and through the load balancing component, transactions are sent to different hosts through certain rules. The database recording method of the system application is a traditional relational database + redis cache;
test Embodiment 8
[0035] Eight elements of a test case: serial number, use case title, preset conditions, priority, test input, operation steps, expected results, and actual results.
[0036] The priority is based on the specific test situation. If the company pays attention to the problem of memory leaks and has specific standards during the test, the priority can be rated as medium or high, and the serial number can be incremented.
[0037] 3. Test case design:
[0038] 3.1. Test tool: jmeter / loadrunner. Use stress testing tools to cover all business interfaces of the system under test, simulating real concurrency as much as possible.
[0039] For example, from the design of business functions to subsequent transactions, the combination and execution sequence of the original transaction and subsequent transactions should be close to the real business scenario.
[0040] 3.2. For the scene of finding the bug of memory leak, the present invention can use boundary value method and scene method:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com