Cache hit state-based processor chip false security dependency conflict identification method
A cache hit and processor technology, applied in electrical digital data processing, computer security devices, instruments, etc., can solve problems such as static analysis is difficult to ensure coverage, dynamic analysis consumes a lot of time, performance degradation and other problems, to ensure performance and safety The balance between performance and performance, and the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
[0015] The method for identifying false security dependency conflicts of a processor chip based on a cache hit state proposed by the present invention mainly includes the following technical solutions:
[0016] 1) Dynamically judge false security dependencies
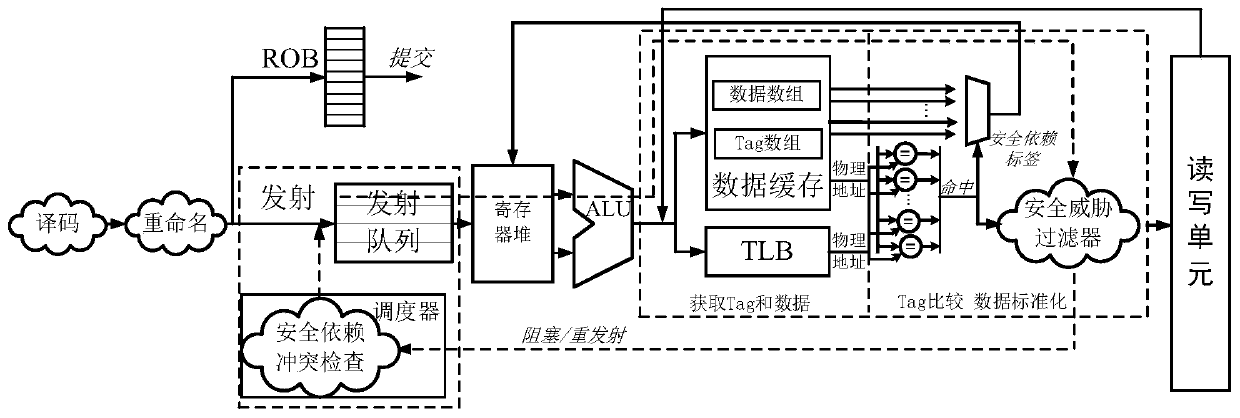
[0017] When accessing the cache unit, according to the security dependency flag of the current memory access operation request, and according to whether the current memory access operation hits the tag (Tag) in the cache at this level, that is, whether the content of the current memory access operation request has been recorded in the Tag array, To judge whether the security dependency of the current memory access operation is true or false:
[0018] If the current memory access operation misses in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com