Voice spoofing attack detection method based on sound field and field pattern
A technology of deception attack and detection method, applied in speech analysis, instruments, etc., can solve the problems of low detection accuracy, difficult application and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
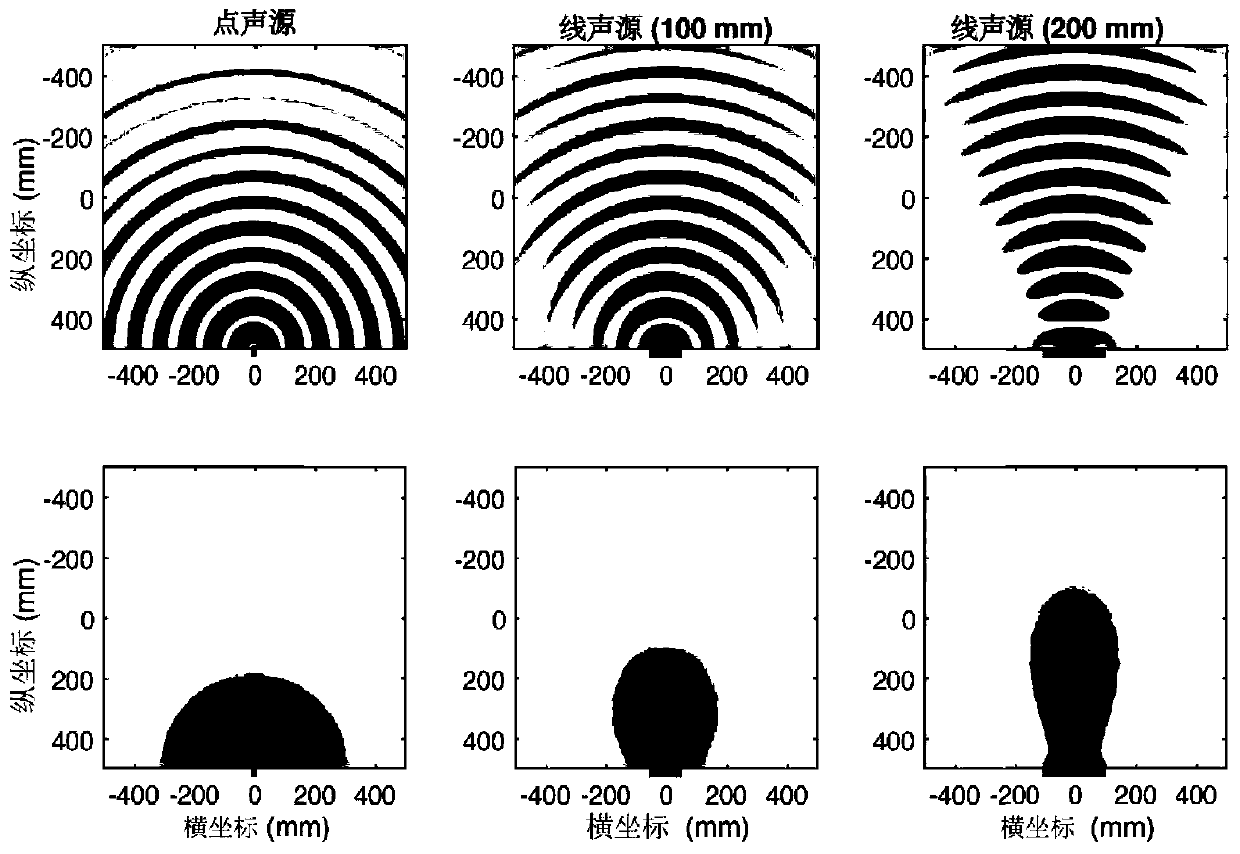
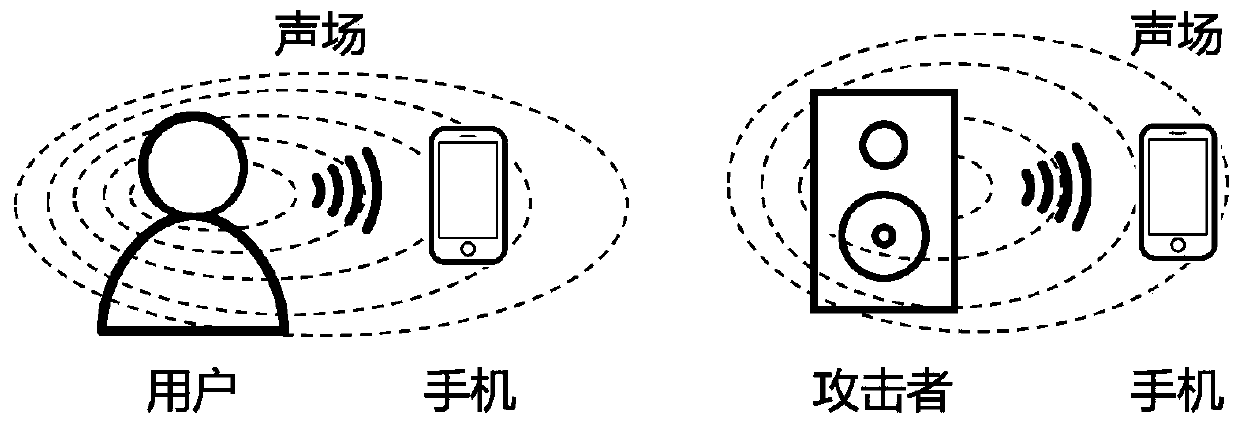
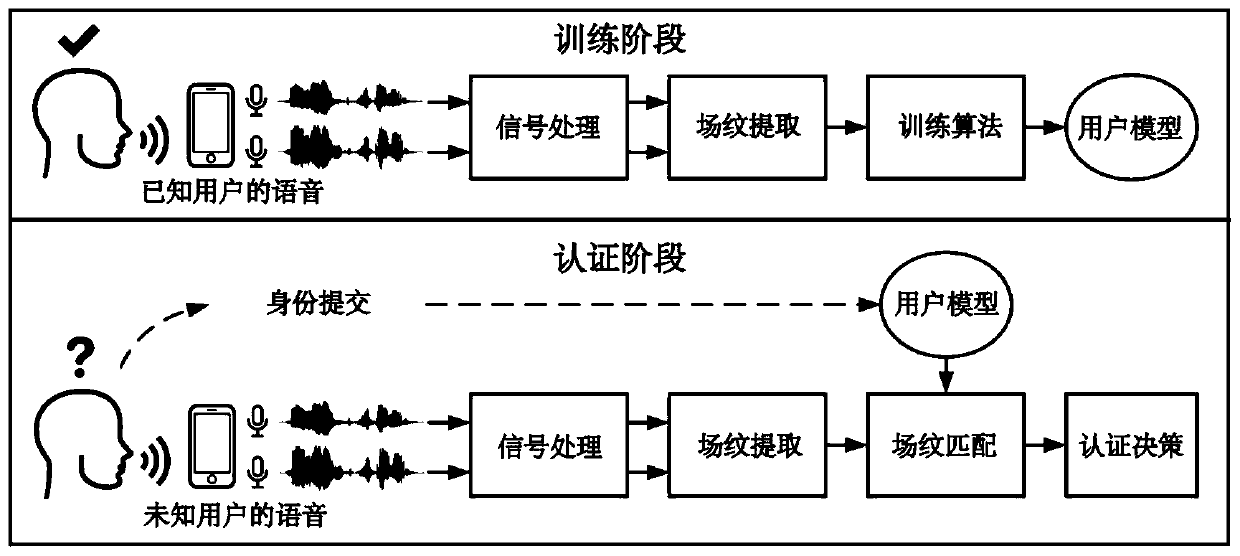
[0095] Such as figure 2 As shown, in the embodiment, the sound emitted by the speaker is used as the counterfeit object for detection and authentication, and the voice signal is collected by using the actual vocal cords of the individual's human vocalizing body to emit sound, and the sound emitted by the actual vocal cords of the individual's human vocalizing body recorded by the speaker is played as the sounding body collection The voice signal is then detected and judged and compared according to the method of the present invention.
[0096] Figure 4 Shows the field pattern comparison between the real person and the speaker, and the original field pattern before dimensionality reduction is shown in the figure. The sound played by the speakers is the replay of the voice of individual 1, and the voice content of the five individuals is also the same.
[0097] Depend on Figure 4 It can be seen from the figure above that there is a significant difference between the field ...
Embodiment 2
[0099] In this embodiment, the living body authentication voices of a total of 20 people (14 men and 6 women) were collected, and voice spoofing attacks were carried out with 8 different types and grades of loudspeakers. Setting the field pattern feature dimension to 9 and selecting the frequency range of 0-4kHz, the detection accuracy rate for real individuals is 99.03%, and the detection accuracy rate for spoofing attacks is 99.18%.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com