Vertical malicious crawler traffic identification method based on deep learning
A technology of deep learning and traffic identification, applied in the field of traffic identification of malicious crawlers based on deep learning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] specific implementation
[0022] Describe the present invention in detail below in conjunction with accompanying drawing:
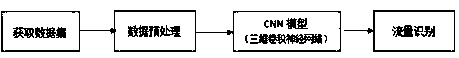
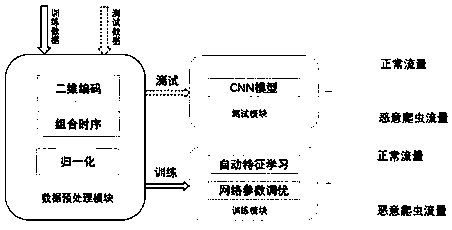
[0023] Such as figure 1 The overall process mainly consists of the following four steps:
[0024] Step1: Build a training data set;
[0025] Step2: Use the three-dimensional convolutional neural network to train the model;
[0026] Step3: Adjust the optimal recognition model;
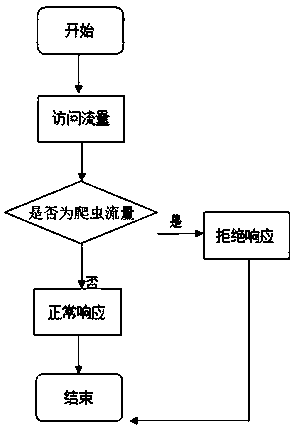
[0027] Step4: Test data and complete traffic identification.
[0028] The specific implementation of Step1 is as follows:
[0029] (1) Set up a target machine in the experimental network, and deploy a target website with a certain amount of information without any defense measures on its equipment;
[0030] (2) In order to improve the speed of sample collection, the target website is completely statically processed. In order to ensure sufficient sample data and collection efficiency, the crawler program is deployed in high-performance collection nodes and general perfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com