Cross-security intranet and Internet data security interaction system and method
A data security and interactive system technology, applied in the field of electric power dispatching automation, can solve the problems of incapable of vertical authentication, non-partitioned security, non-dedicated network, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
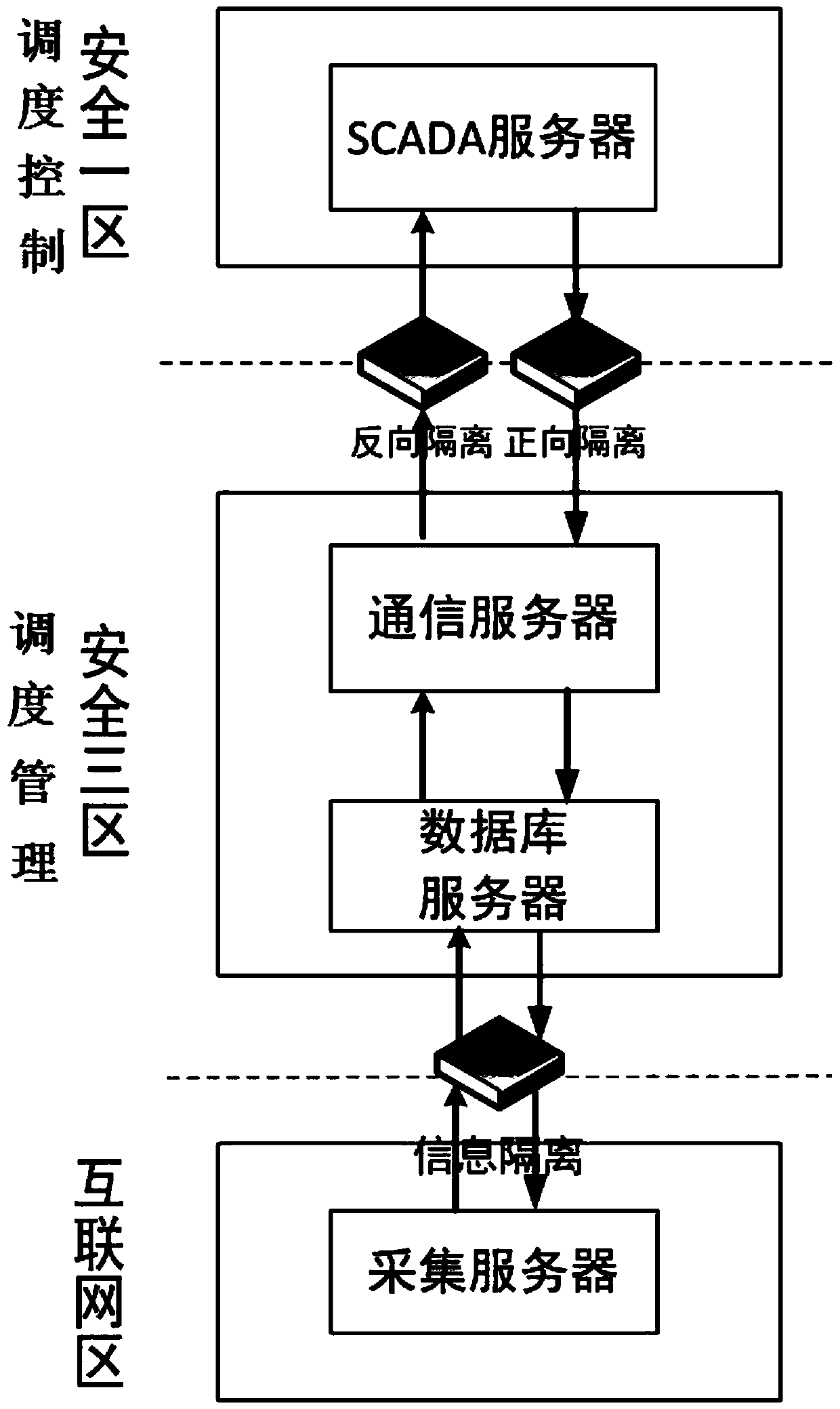
[0021] Embodiment 1: as figure 1 As shown, the present invention proposes a data security interactive system across a secure intranet and the Internet, including at least one SCADA server, forward network security isolation equipment, reverse network security isolation equipment, communication servers, database servers, information security network isolation Device and acquisition server; the SCADA server is located in the dispatching control security zone 1; the communication server and the database server are located in the dispatching management security zone 3; the collection server is located in the Internet zone; both the forward network security isolation device and the reverse network security isolation device are set in the SCADA server and the communication server; the information security network isolation device is set between the database server and the collection server; the data transmission client of the communication server is connected with the data server of ...
Embodiment 2
[0022] Embodiment 2: When the data access system across the secure intranet and the Internet is in the state of uploading data, the acquisition server sends the data to the database server through the information security network isolation device by calling the database security agent service; The wired network of the static IP communicates with the database server; the communication server reads the uploaded data by calling the database service, generates a power system standard E format file, transmits it to the SCADA server through the reverse network security isolation device, and finally analyzes it by the SCADA server. Store, display, all the other are the same as embodiment 1.
Embodiment 3
[0023] Embodiment 3: when the data access system across the secure intranet and the Internet is in the state of sending data, the SCADA server sends the data to the communication server through the forward network security isolation device in the form of a message; the communication server calls the database service Write the issued data into the database server; the acquisition server obtains the issued data from the database server through the information security network isolation device by calling the database security agent service, and the rest is the same as that of embodiment 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com