Code parallel verification method and device based on shared infeasible path pool
A feasible and path-based technology, applied in code compilation, program code conversion, instrumentation, etc., can solve the problems of large number of program paths, long time-consuming, huge resources, etc., and achieve the effect of improving efficiency and path traversal efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in further detail below in conjunction with the accompanying drawings.
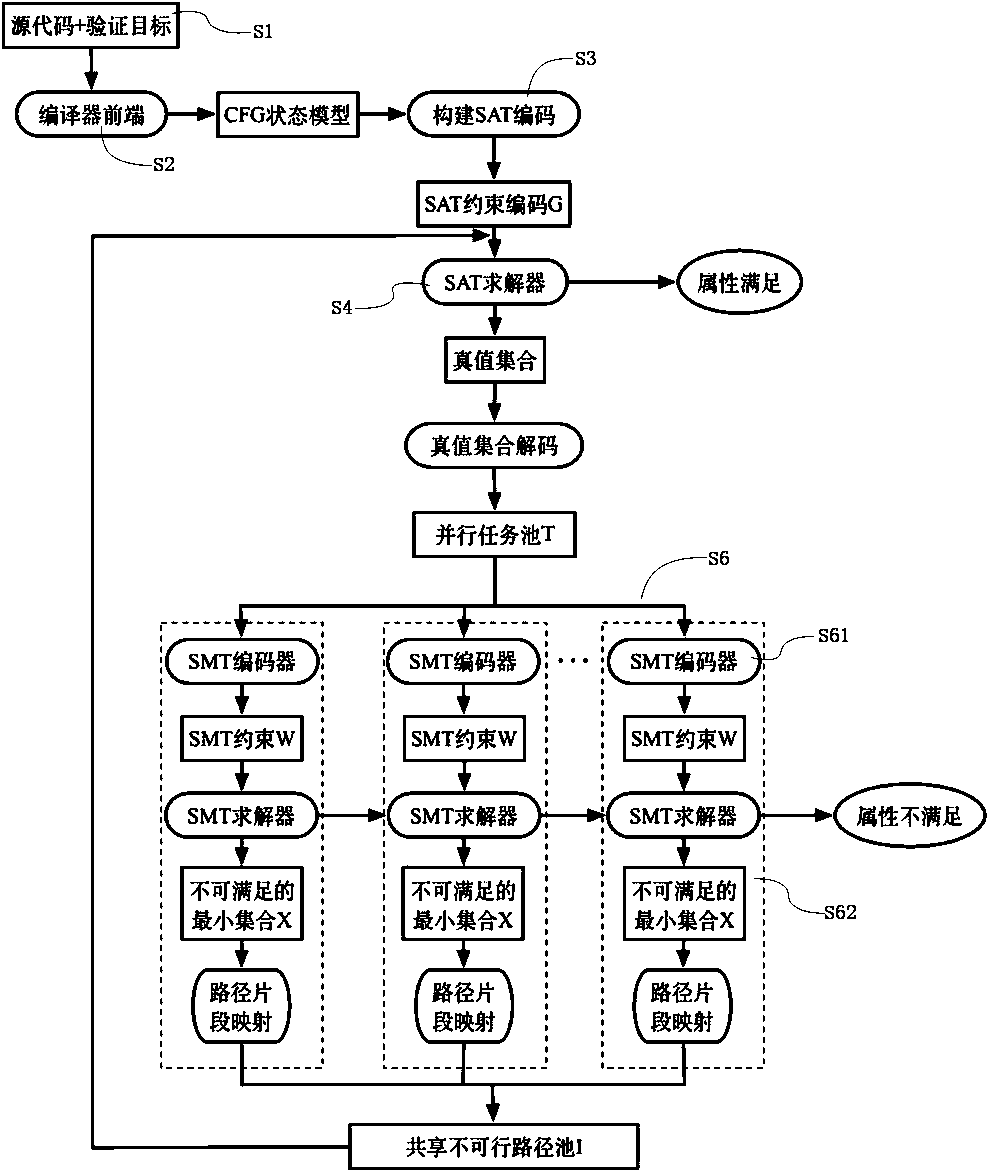
[0045] refer to figure 1 , a parallelized code verification method for sharing an infeasible path pool in the present invention can be roughly divided into four processes: the first is the initialization process, the second is the process of finding potential paths, and the third is the process of analyzing potential paths. Among them, the process of finding out the potential path and analyzing the potential path is a process in an iterative process.
[0046] The initialization process is to initialize the SAT constraint code G, the parallel task pool T and the shared infeasible path pool I, namely the aforementioned steps S1 to S3. SAT Constrained Coding G is constructed from user-input source code and verification targets. The source code input by the user is first converted into a CFG state model, and then the SAT constraint encoding G is constructed wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com