Security processor and operation method thereof, and method for encrypting or decrypting data
The technology of a security processor and operation method, which is applied in the field of security processors, can solve problems such as increase of circuit area or average power consumption of security processors, inability of SCA to provide sufficient protection, and influence on performance of security processors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
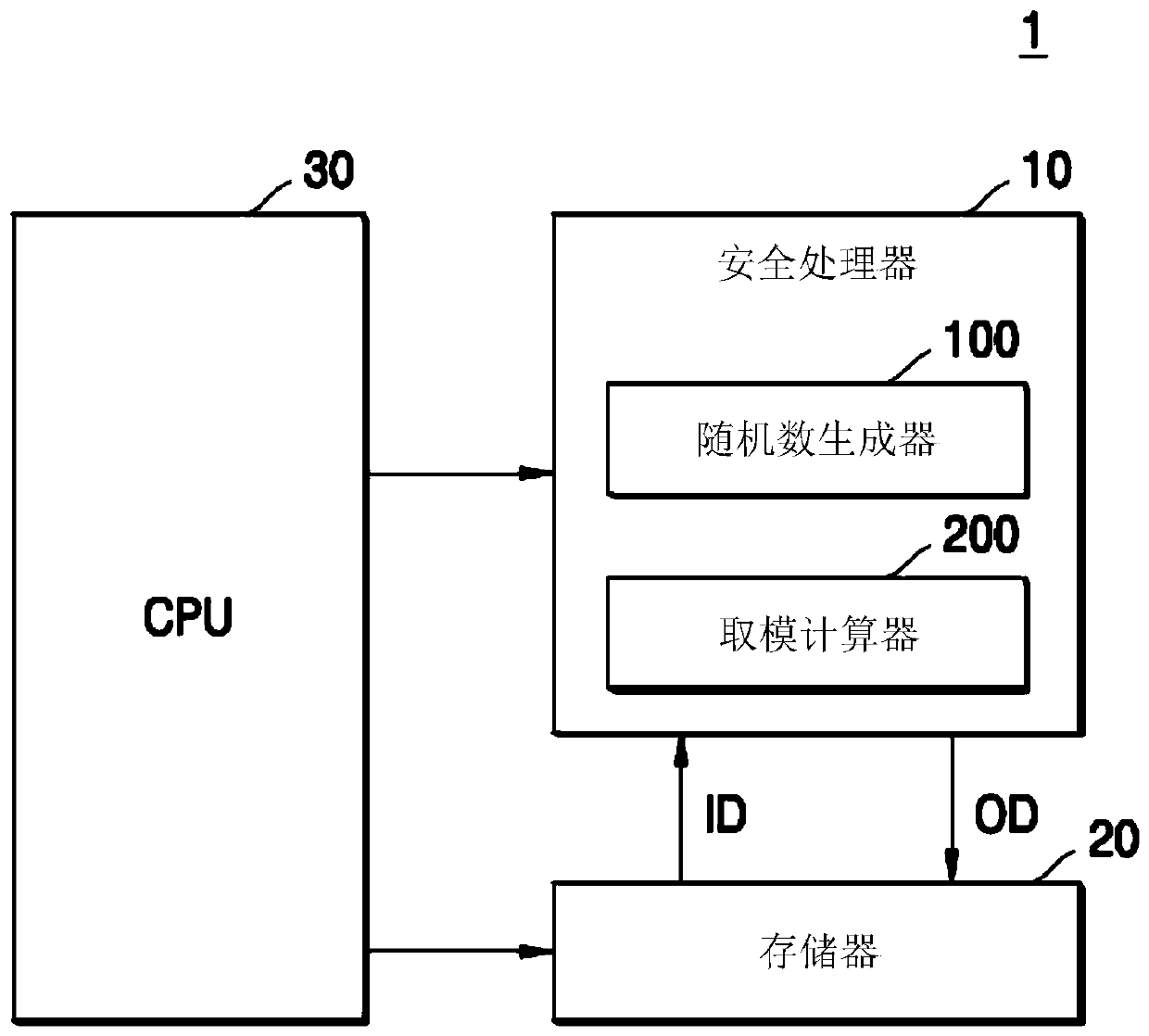
[0027] figure 1 is a block diagram illustrating an electronic system 1 according to an example embodiment.
[0028] refer to figure 1 , the electronic system 1 may include a security processor 10 , a memory 20 and a central processing unit (CPU) 30 . The electronic system 1 may correspond to various types of systems including, for example, a laptop computer, a mobile phone, a smart phone, a tablet personal computer (PC), and a personal digital assistant (PDA).
[0029] The CPU 30 can output various control signals for controlling the security processor 10 and the memory 20 . In another embodiment, an application processor (AP) may perform the functions of the CPU 30 .
[0030] The memory 20 may store data under the control of the CPU 30 or the security processor 10 . In an embodiment of the present inventive concept, the memory 20 may record the input data ID received from an external source, provide the input data ID to the security processor 10 under the control of the C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com