Logic encryption defense method based on key gate position selection
A key gate and key technology, applied in encryption devices with shift registers/memory, secure communication devices, digital transmission systems, etc., can solve the problem of shortening the running time and the difficulty of keeping the key bits in the encryption scheme while resisting sensitization. and Gao Hanming distance and other issues, to achieve the effect of shortening running time, saving running time, and short running time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The logical encryption defense method based on key gate position selection provided by the present invention will be described in detail below in conjunction with the accompanying drawings, but it does not constitute a limitation to the present invention.
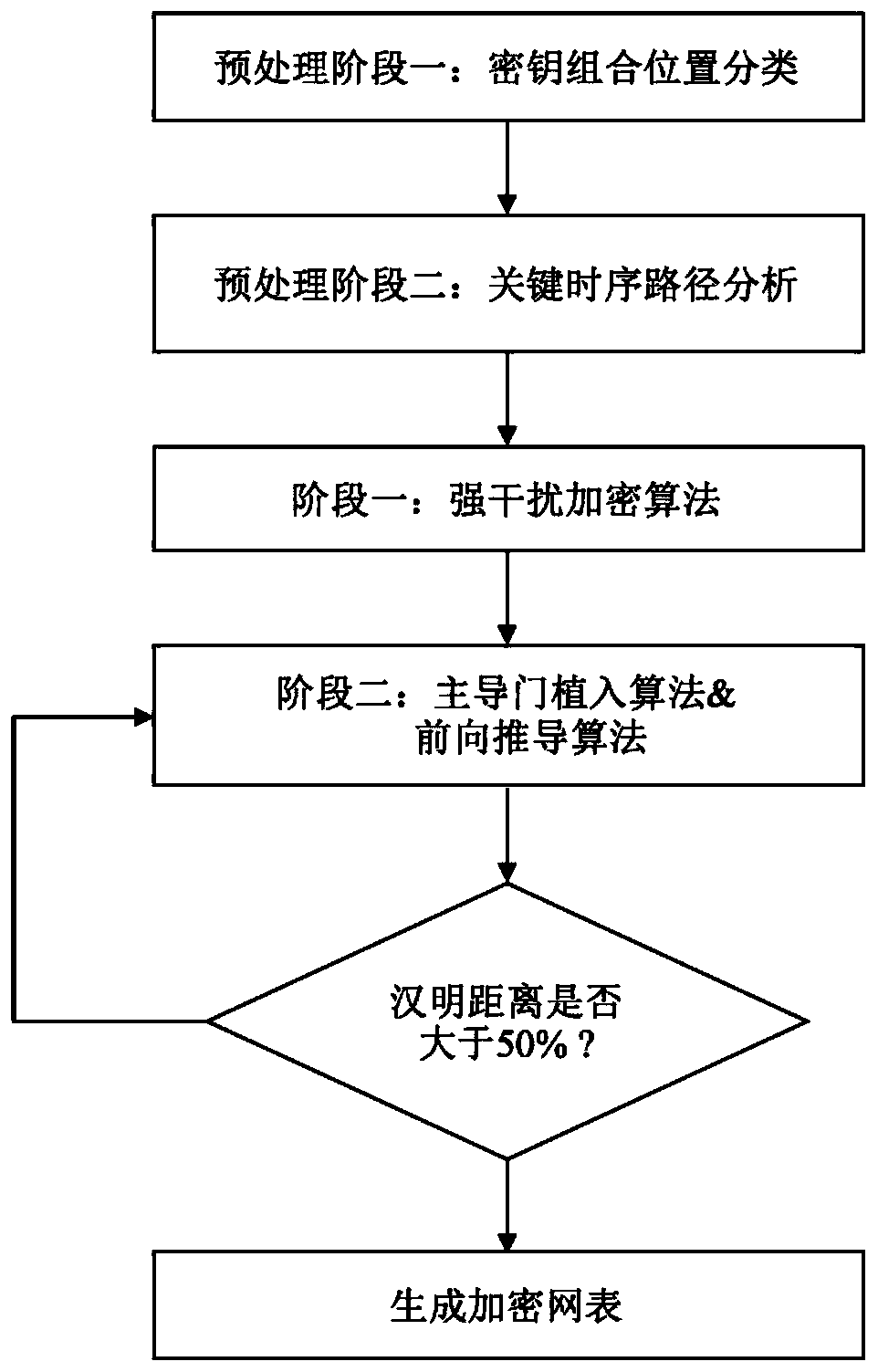
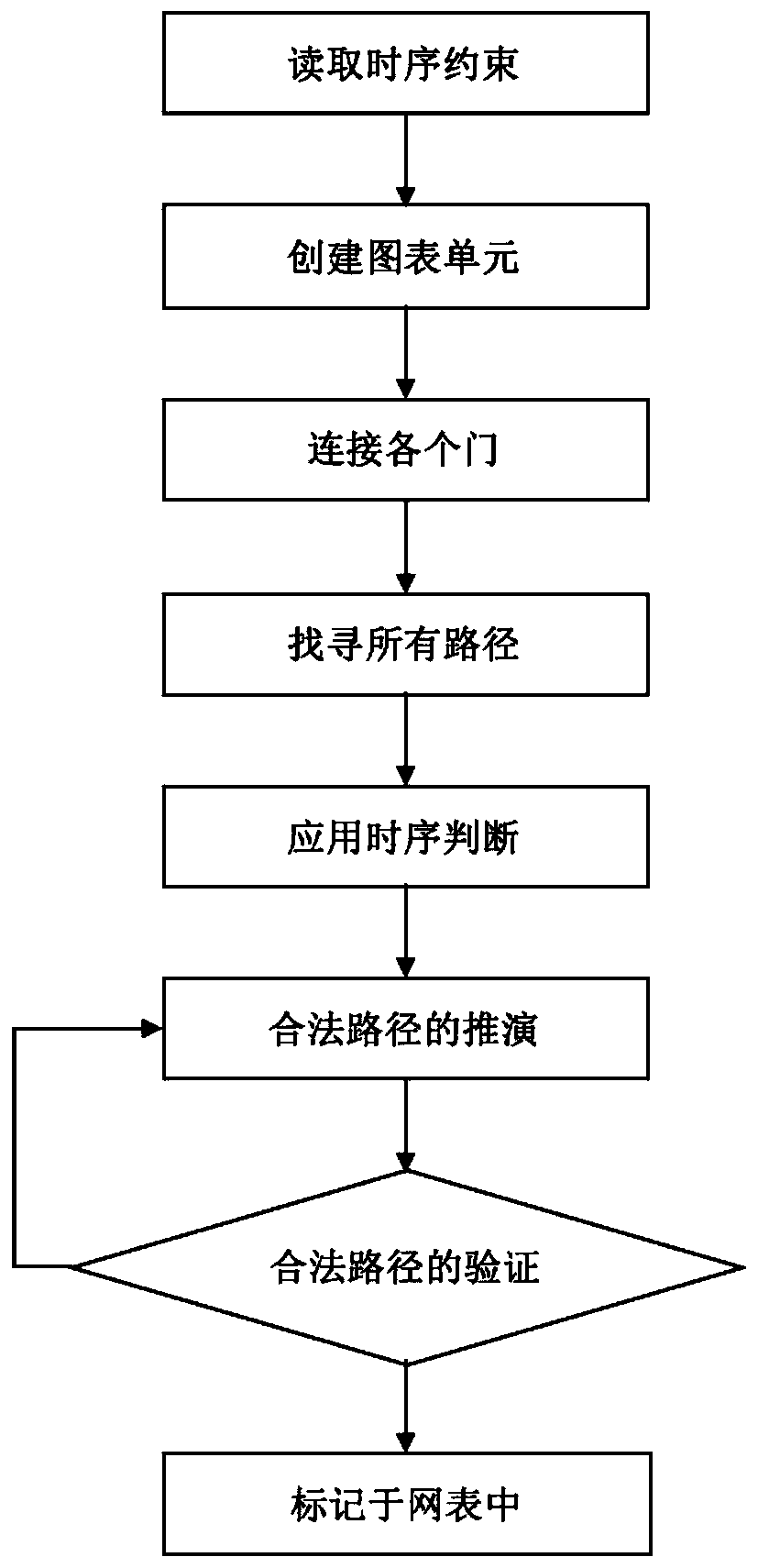
[0020] This method mainly covers two parts, data preprocessing to facilitate the generation of encrypted netlist, and the actual execution of encryption algorithm to generate its encrypted netlist. The specific implementation steps are as follows:
[0021] first part:
[0022] Data preprocessing (1)
[0023] Step 1: Since the attacker can formulate different attack strategies to determine the value of the key bit according to the implanted position, firstly, the convergent key gate needs to be marked according to the pairwise security.
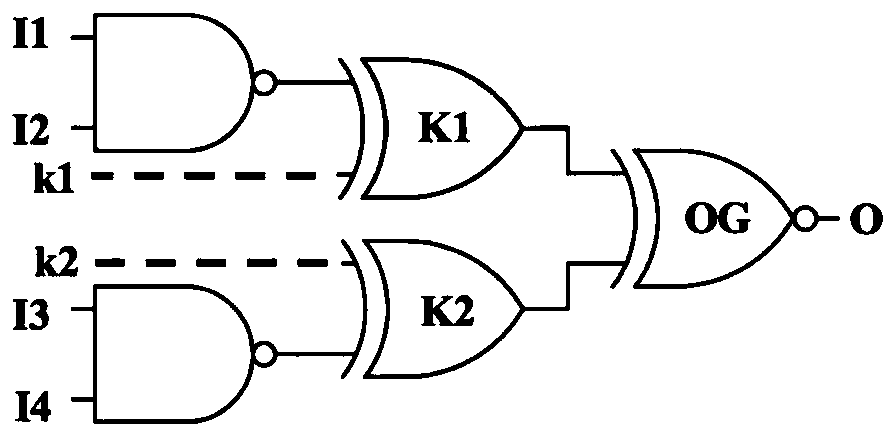
[0024] figure 2 An example of pairwise security convergent key gate. Assuming that the attacker wants to sensitize any key bit, the attacker must set any input bit of the OG log...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com