Hybrid encryption method for controlling system network security and system thereof
A technology of mixed encryption and encrypted value, which is applied in the field of password protection and information security, can solve the problem of insecure initial value of equipment, and achieve the effect of reducing operation cost and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
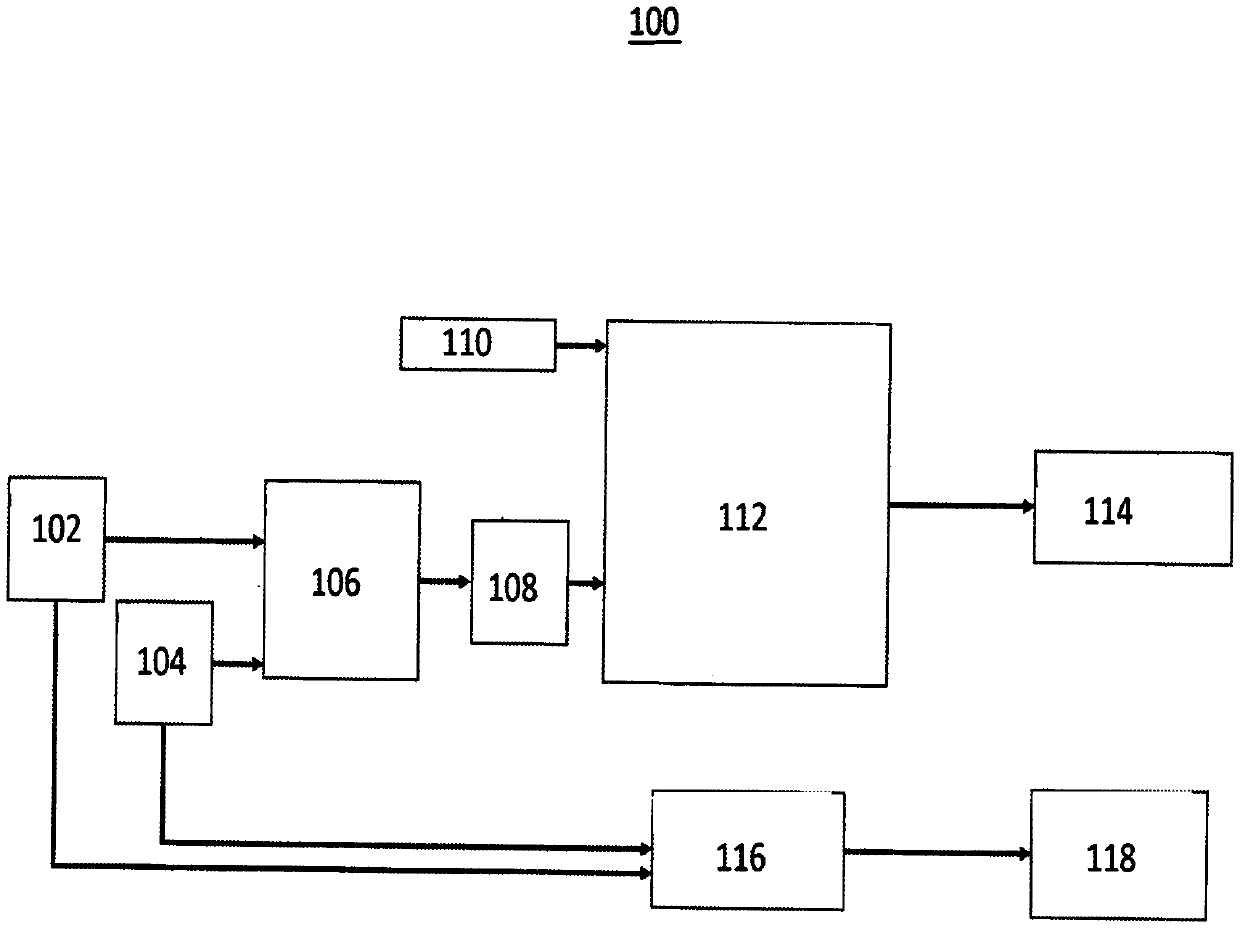
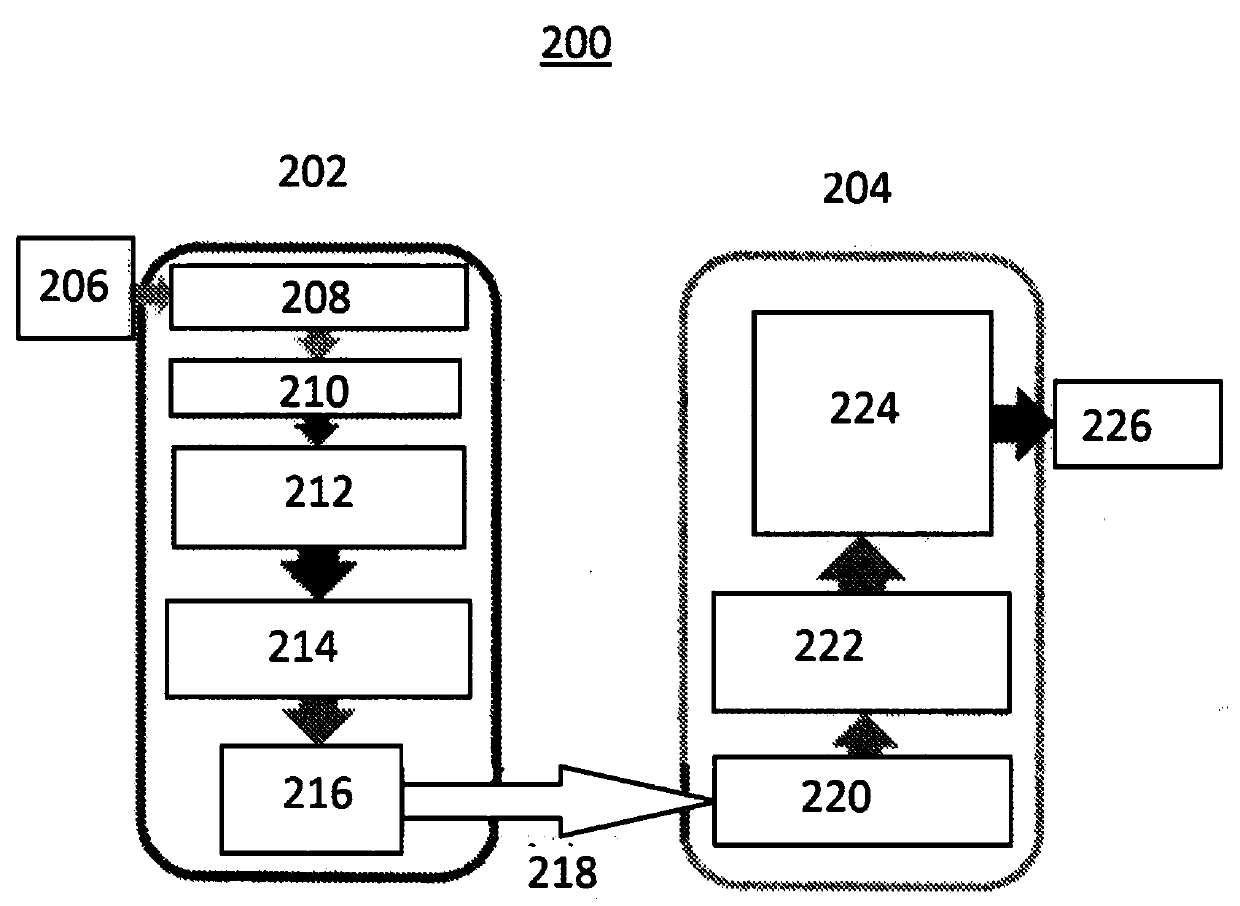
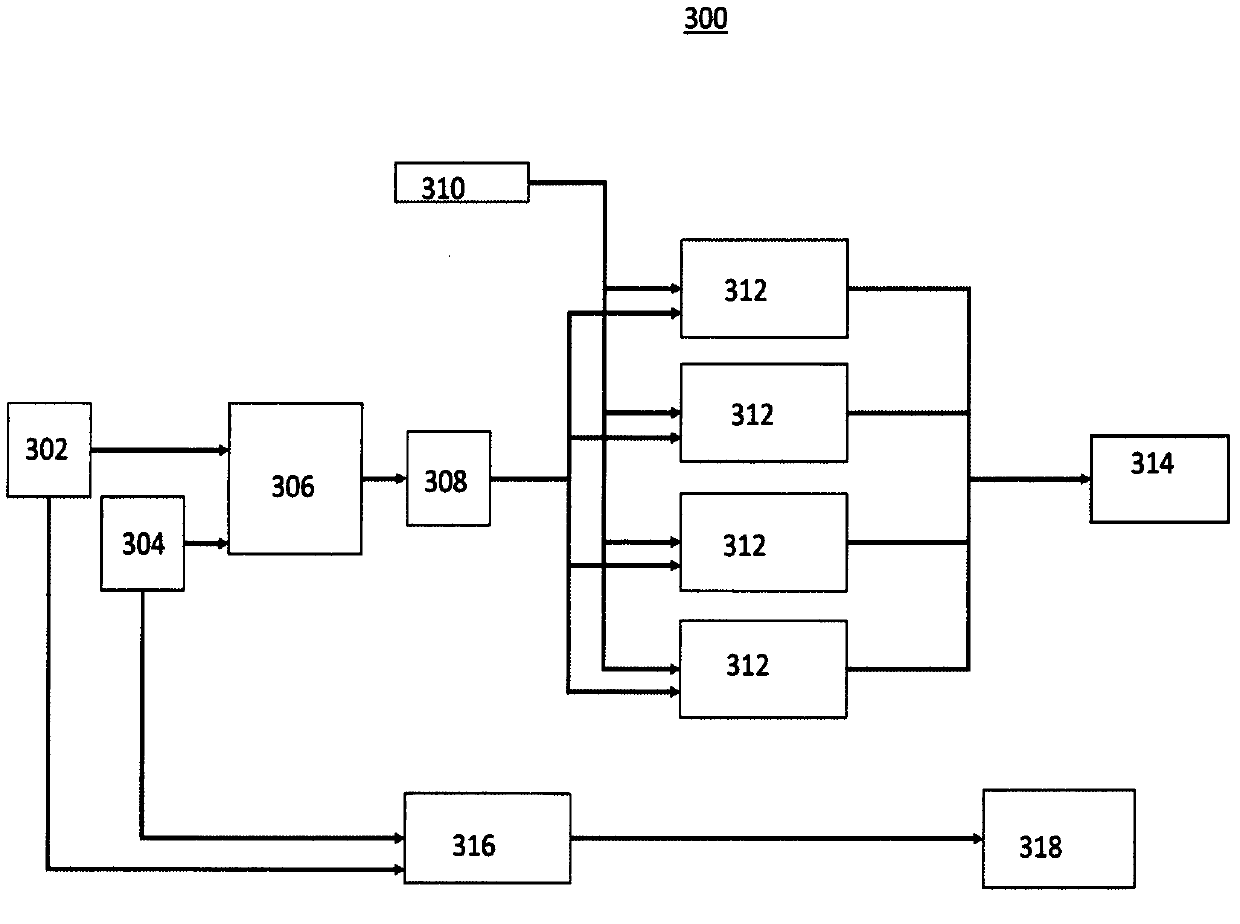
[0059] The present invention will now be described in further detail with reference to the accompanying drawings. These drawings are all simplified schematic diagrams, and only illustrate the basic structure of the present invention in a schematic manner, so they only show the structures related to the present invention.
[0060] Defense-in-depth strategies are driven concepts that combine multiple encryption types, such as the SM2-CNN cipher. Historical experience has proven that no network security password or system architecture is a fatal vulnerability for hackers to break into a system, so the primary goal of protecting information security is to make password cracking take longer than it takes to detect intrusions and initiate manual or automated defense countermeasures.
[0061] A key idea of CNN cryptography is that without the correct initial values and conditions in the CNN, the result cannot be decrypted into something valuable to an adversary actor. Due to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com