End-to-end verification method and system for telecommunication service unauthorized access prevention
A telecommunications service and unauthorized access technology, applied in digital data authentication, data processing applications, electronic digital data processing, etc., can solve the problems of complex interaction process, user information leakage, etc., to improve access efficiency, increase authentication capabilities, Improve the effect of security authentication access capability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The principles and features of the present invention will be described below with reference to the accompanying drawings. The examples cited are only used to explain the present invention and are not used to limit the scope of the present invention.
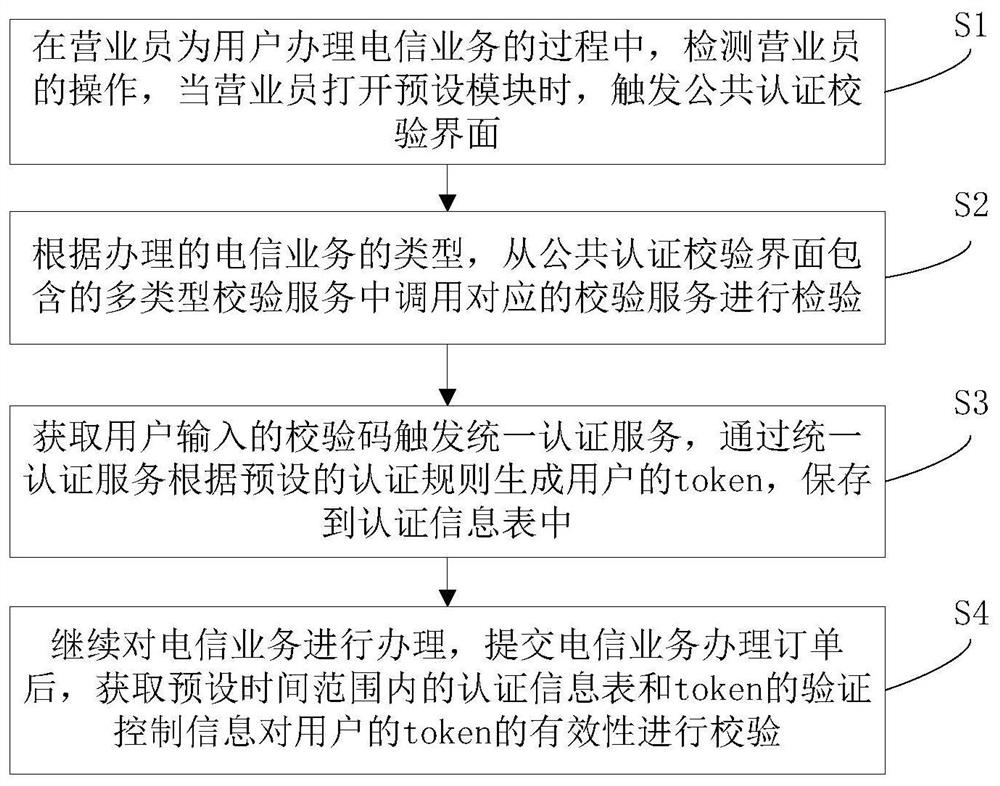
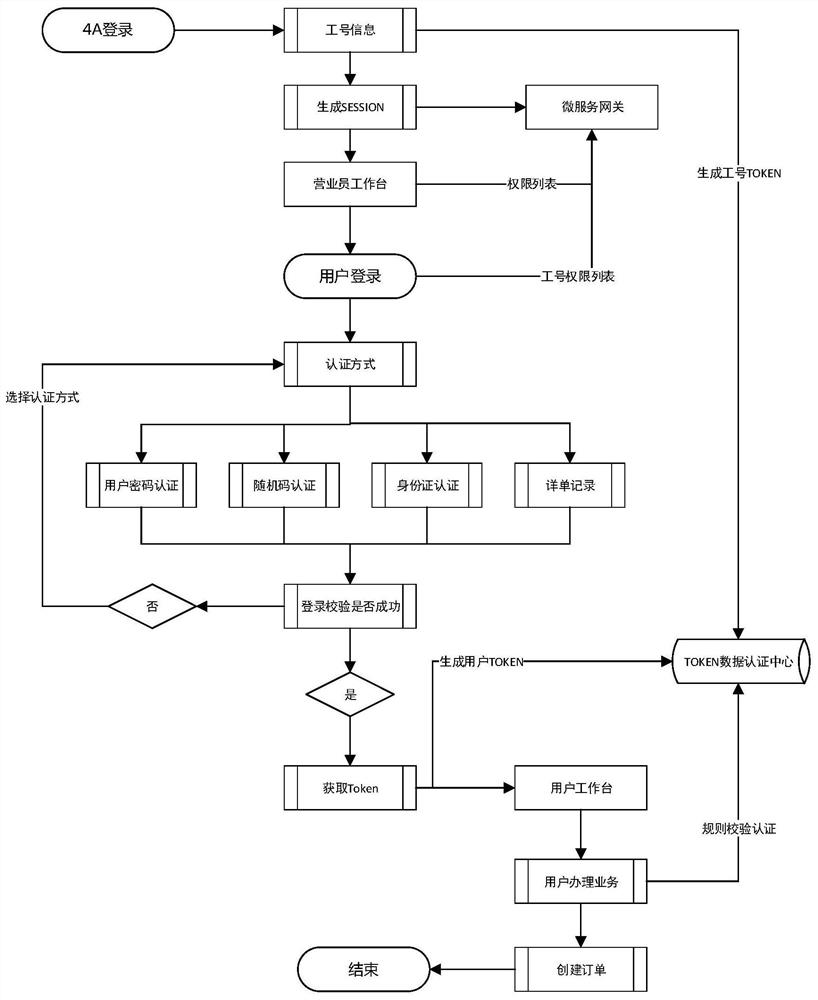
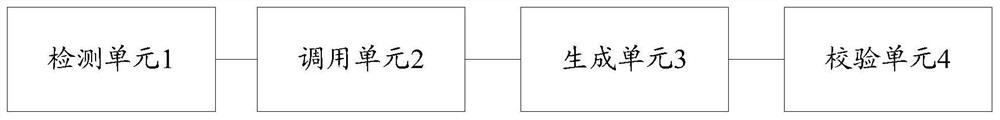
[0023] Such as figure 1 Shown is a schematic flow diagram provided by an embodiment of the end-to-end verification method of the present invention. The end-to-end verification method is used to prevent unauthorized access to telecommunication services, and includes:
[0024] S1: Detect the operation of the salesperson when the salesperson handles telecommunications services for the user, and trigger the public authentication verification interface when the salesperson opens the preset module;
[0025] For example, the public authentication verification interface can be triggered when a salesperson logs on to the OP homepage of the operator and opens the secondary module for the user to handle business.
[0026] It should be underst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com