Identity authentication method and device based on fusion features, equipment and storage medium
A technology of identity authentication and feature fusion, applied in the field of biometric authentication, can solve the problems of unfavorable protection of information security, low security of information system, and low face recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
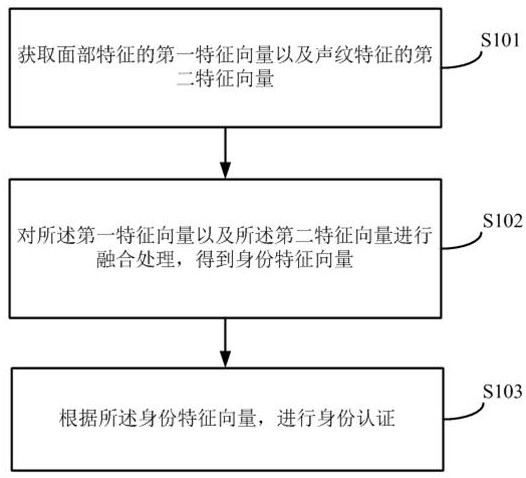
[0072] figure 1 It shows a schematic flowchart of an identity authentication method based on fusion features provided by the embodiment of the present application, the method includes steps S101-S103; specifically:
[0073] S101. Acquire a first feature vector of facial features and a second feature vector of voiceprint features.
[0074] Specifically, when obtaining the feature vector corresponding to the biological feature, the feature information that can represent the biological identity can be extracted from the collected biological data through the biometric feature recognition technology according to the type of biological feature, and according to the extracted feature information, Get the feature vector corresponding to the type of biological feature.
[0075] Illustratively, for the acquisition of the first feature vector, the facial feature vector can be extracted from the collected facial image of the creature as the first feature vector; for the acquisition of th...
Embodiment 2
[0170] Figure 6 A schematic structural diagram of an identity authentication device based on fusion features provided by an embodiment of the present invention is shown, and the identity authentication device includes:
[0171] A data collection module 601, configured to obtain a first feature vector of facial features and a second feature vector of voiceprint features;
[0172] A data processing module 602, configured to perform fusion processing on the first feature vector and the second feature vector to obtain an identity feature vector;
[0173] The identity authentication module 603 is configured to perform identity authentication according to the identity feature vector.
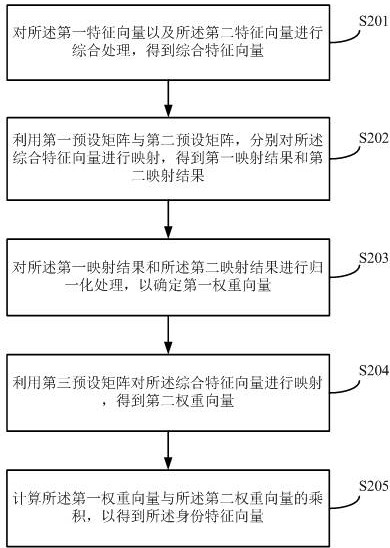
[0174] Optionally, the data processing module 602 includes:
[0175] an integrated processing unit (not shown in the figure), configured to perform integrated processing on the first feature vector and the second feature vector to obtain an integrated feature vector;
[0176] The first mapping uni...
Embodiment 3
[0197] Such as Figure 7 As shown, an embodiment of the present application provides a computer device 700 for executing the identity authentication method based on fusion features in the present application, the device includes a memory 701, a processor 702 and stored in the memory 701 and can be used in The computer program running on the processor 702, wherein, when the processor 702 executes the computer program, the above-mentioned steps of the identity authentication method based on fusion features are realized.
[0198] Specifically, the above-mentioned memory 701 and processor 702 may be general-purpose memory and processor, which are not specifically limited here. When the processor 702 runs the computer program stored in the memory 701, it can execute the above-mentioned fusion feature-based identity authentication method.
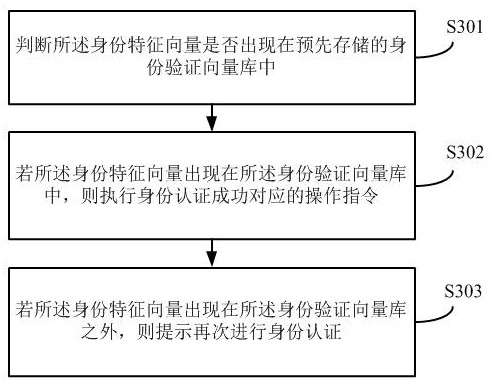
[0199] Corresponding to the fusion feature-based identity authentication method in this application, the embodiment of this application also pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com