Hidden communication message security coding method and system based on block chain, and medium
A covert communication and secure coding technology, applied in the field of secure coding of covert communication messages based on blockchain, can solve problems such as errors, explicit reception, and easy exposure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
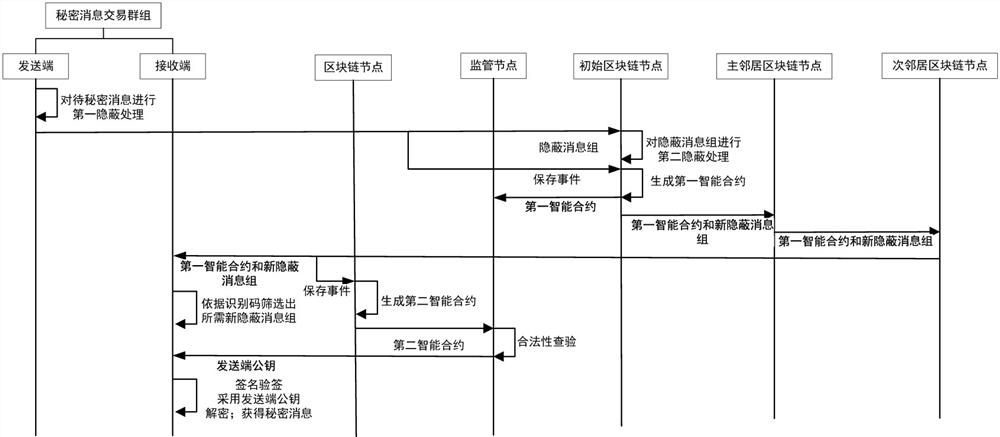
[0034] as attached figure 1 As shown, a block chain-based covert communication message security encoding method, which includes the following steps:
[0035] The sending end performs the first covert processing on the covert data to be transmitted to obtain a covert message group;
[0036] Generate a first smart contract on the initial blockchain node based on the transaction event that the sender transmits the covert message group to the initial blockchain node;
[0037]The initial block chain node broadcasts the covert message group and the first smart contract to the main neighbor block chain node of the block chain, and the main neighbor block chain node broadcasts the covert message group and the The first smart contract is broadcast to the second neighbor blockchain node;
[0038] The receiving end obtains the required covert message group according to the identification code of the covert message group; the second smart contract is generated based on the transaction e...
Embodiment 2
[0079] The difference between this embodiment and Embodiment 1 is that the first concealment process may also include the following steps: perform digest operation on the concealed data to be transmitted to obtain digest information, use the first encryption algorithm to encrypt the digest information, and obtain the verification field; after dividing the concealed data to be transmitted into several sub-concealed data blocks, several identification fields are generated based on the sequence number of each sub-concealed data block and the total number of sub-concealed data blocks; the identification field and the sub-concealed data blocks are spliced to generate a concealed Data grouping: performing random out-of-sequence processing on the concealed data group to obtain a out-of-order message group, adding the verification field before the out-of-order message group, and performing encryption processing to obtain a new concealed message group.
[0080] It should be noted that...
Embodiment 3
[0082] The difference between this embodiment and Embodiment 1 lies in that: the general transaction information broadcast in the blockchain network is obtained, and the general transaction information is used as the carrier of the concealed message group.
[0083] It is understandable that due to the permanent public storage of transaction data, the adversary has enough time to analyze all historical transaction data, so it is necessary to reduce the particularity of transactions carrying concealed data and increase the difficulty for the adversary to distinguish special transactions from ordinary transactions. Through statistical analysis of ordinary transaction data, the characteristics of ordinary transactions are sorted out, and the characteristics of ordinary transactions are simulated when constructing special transactions, so that opponents cannot easily identify special transactions.
[0084] It should be noted that, the initial block chain node extracts the characteri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com