Detection method, device, computer equipment and storage medium for network security
A detection method and security technology, applied in neural learning methods, biological neural network models, electrical components, etc., can solve problems such as low accuracy, low detection accuracy, and low search efficiency, and achieve rapid detection and detection accuracy. High and effective effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
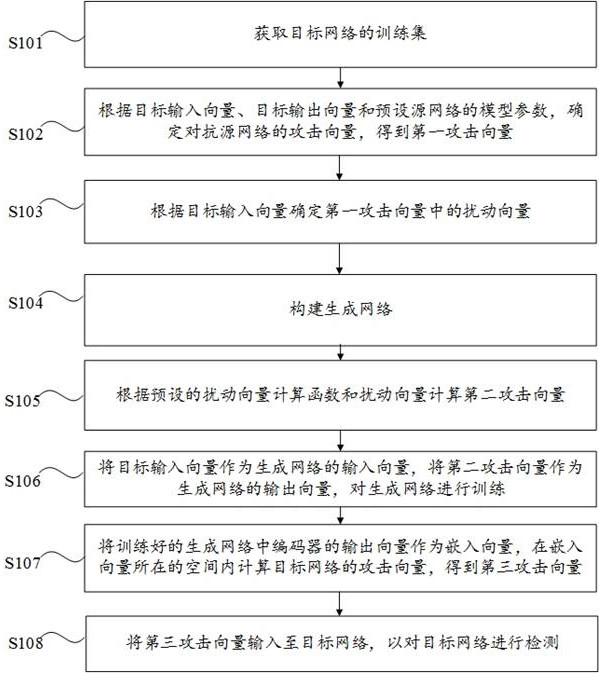
[0039] Embodiment 1 of the present invention provides a detection method for network security, the method is aimed at a target network that performs computer vision tasks, and the target network can perform computer vision tasks such as image classification, image recognition, image segmentation, or image generation. When enhancing the ability of the target network to defend against attacks, the method is used to detect the security of the target network, and then based on the detection results to enhance the ability of the target network to defend against attacks. Through this method, the detection of the target network security can be improved accuracy and efficiency. specifically, figure 1 It is a flow chart of the detection method for network security provided by Embodiment 1 of the present invention, such as figure 1 As shown, the detection method of the network security includes the following steps S101 to S108:
[0040] Step S101: Obtain the training set of the target...
Embodiment 2
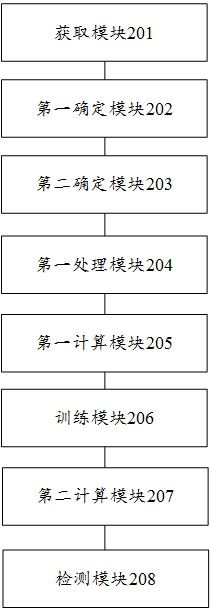
[0086] Corresponding to Embodiment 1 above, Embodiment 2 of the present invention provides a device for detecting network security. For corresponding technical features and corresponding technical effects, reference may be made to Embodiment 1 above, which will not be repeated here. image 3 A block diagram of a detection device for network security provided in Embodiment 2 of the present invention, such as image 3 As shown, the device includes: an acquisition module 201 , a first determination module 202 , a second determination module 203 , a first processing module 204 , a first calculation module 205 , a training module 206 , a second calculation module 207 and a detection module 208 .
[0087] Wherein, the obtaining module 201 is used to obtain the training set of the target network, wherein the training set corresponds to a plurality of images, the training set includes a target input vector and a target output vector, and the target input vector includes a feature vecto...
Embodiment 3
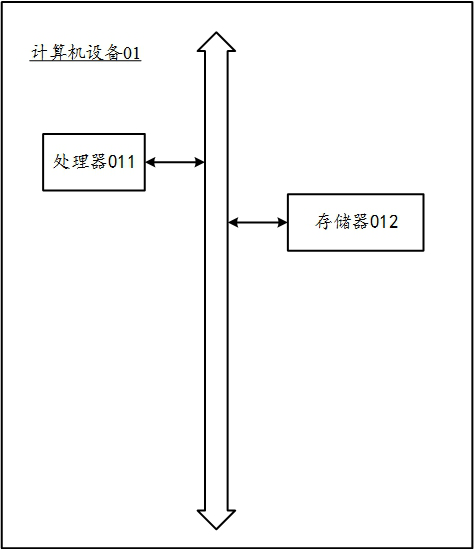
[0105] Embodiment 3 also provides a computer device, such as a smart phone, a tablet computer, a notebook computer, a desktop computer, a rack server, a blade server, a tower server, or a cabinet server (including an independent server, Or a server cluster composed of multiple servers), etc. Such as image 3 As shown, the computer device 01 in this embodiment at least includes but is not limited to: a memory 011 and a processor 012 that can communicate with each other through a system bus, such as image 3 shown. It should be pointed out that, image 3 Only the computer device 01 is shown with components memory 011 and processor 012, but it should be understood that implementing all of the illustrated components is not a requirement and that more or fewer components may instead be implemented.
[0106]In this embodiment, the memory 011 (that is, the readable storage medium) includes flash memory, hard disk, multimedia card, card-type memory (for example, SD or DX memory, et...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com