Mailbox-based frequency limiting method and device, computer equipment and storage medium
A frequency limiting and mailbox technology, applied in the computer field, can solve the problems of single judgment method, low accuracy and efficiency of malicious emails, and inability to guarantee the security and reliability of mailboxes, so as to improve security and reliability and save storage space. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
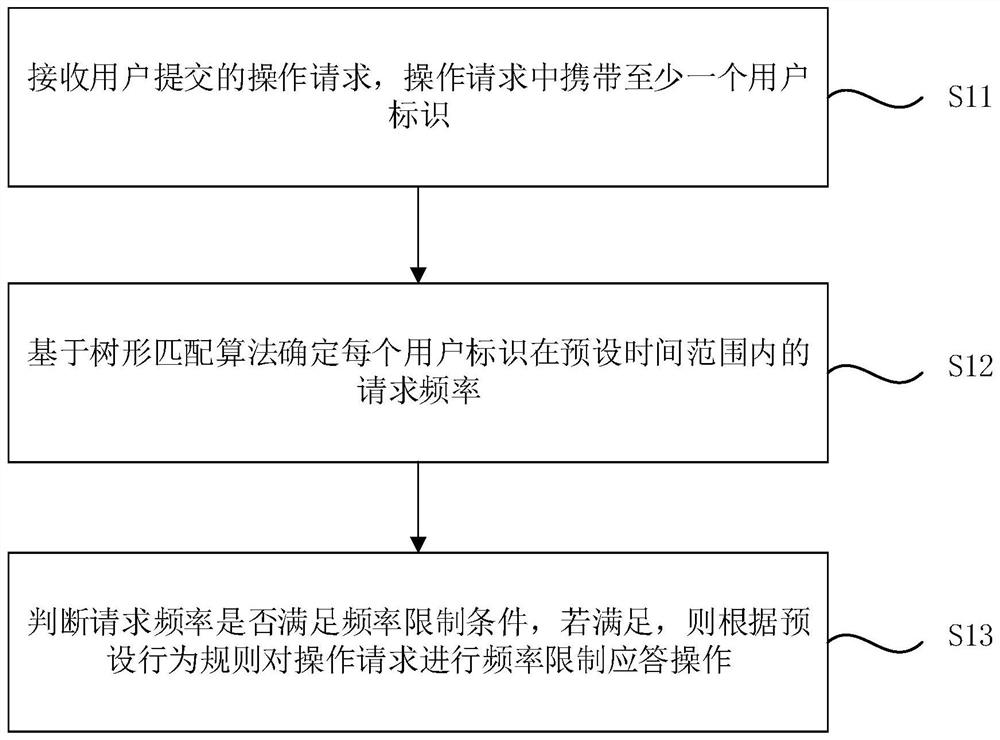
[0027] figure 1 It is a flow chart of the mailbox-based frequency limitation method provided by Embodiment 1 of the present invention. This embodiment is applicable to analyzing and intercepting malicious user operation requests during the use of mailbox services. The method can be performed by the mailbox-based frequency limitation device provided by the embodiment of the present invention. The device can be implemented by hardware and / or software Generally, it can be integrated into computer equipment. Such as figure 1 As shown, it specifically includes the following steps:
[0028] S11. Receive an operation request submitted by a user, where the operation request carries at least one user identifier.
[0029] Wherein, the operation request submitted by the user may be a login request, a request to send a short message, a request to send an email, a log access request, a communication rate access request, and the like. Each submitted operation request carries a correspon...
Embodiment 2
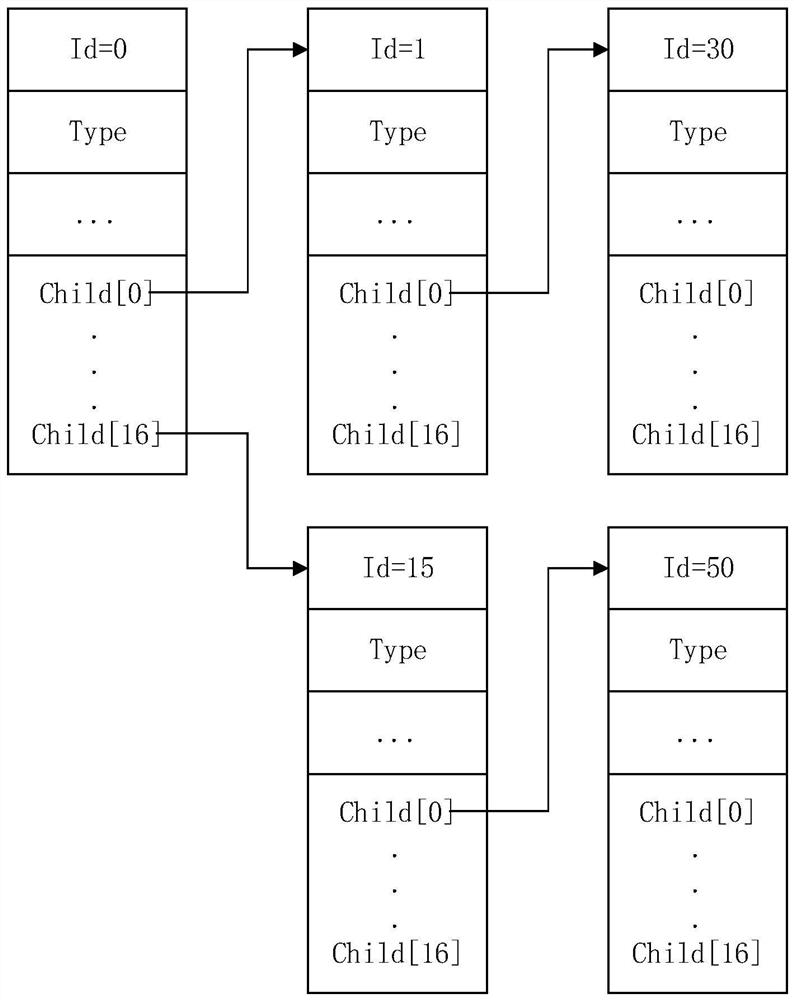
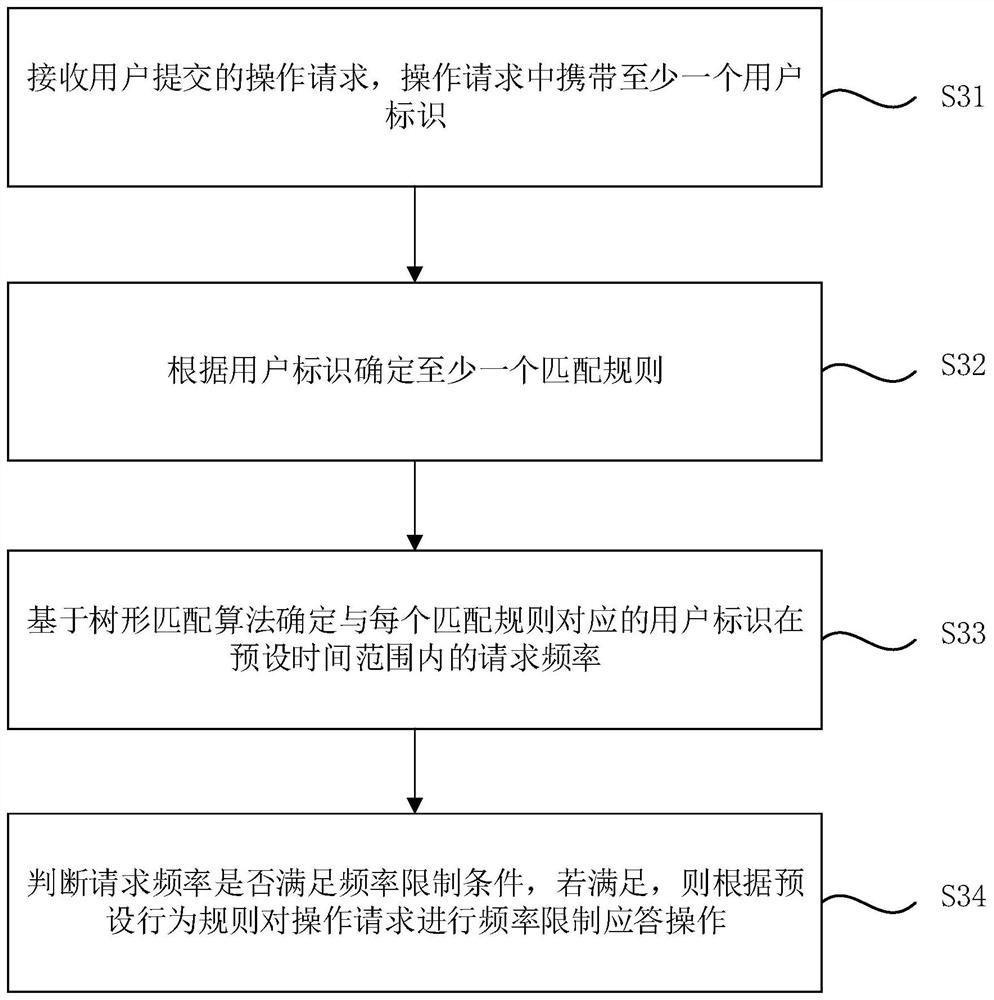
[0043] image 3 It is a flow chart of the mailbox-based frequency limitation method provided by Embodiment 2 of the present invention. The technical solution of this embodiment is further refined on the basis of the above technical solution. Optionally, different matching rules may be determined for different types of user identifiers. Specifically, in this embodiment, before determining the request frequency of each user ID within a preset time range based on the tree matching algorithm, it also includes: determining at least one matching rule according to the user ID; correspondingly, based on the tree matching algorithm Determining the request frequency of each user ID within the preset time range includes: determining the request frequency of the user ID corresponding to each matching rule within the preset time range based on a tree matching algorithm. Correspondingly, such as image 3 As shown, it specifically includes the following steps:
[0044] S31. Receive an ope...
Embodiment 3
[0056] Figure 4 It is a schematic structural diagram of a mailbox-based frequency limitation device provided in Embodiment 3 of the present invention. The device can be implemented by hardware and / or software, and can generally be integrated into computer equipment. Such as Figure 4 As shown, the device includes:
[0057] The request receiving module 41 is configured to receive an operation request submitted by a user, and the operation request carries at least one user identifier;
[0058] A frequency determination module 42, configured to determine the request frequency of each user identifier within a preset time range based on a tree matching algorithm;
[0059] The restriction response module 43 is configured to judge whether the requested frequency satisfies the frequency restriction condition, and if so, perform a frequency restriction response operation to the operation request according to preset behavior rules.
[0060] The technical solution provided by the emb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com