A Safe and Reversible Relational Database Copyright Protection Method
A copyright protection and database technology, applied in the computer field, can solve problems such as lack of error correction ability of binary strings, data copyright disputes, damage to interests, etc., to achieve the effect of resisting common attacks, avoiding LBS pathological phenomena, and improving the detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
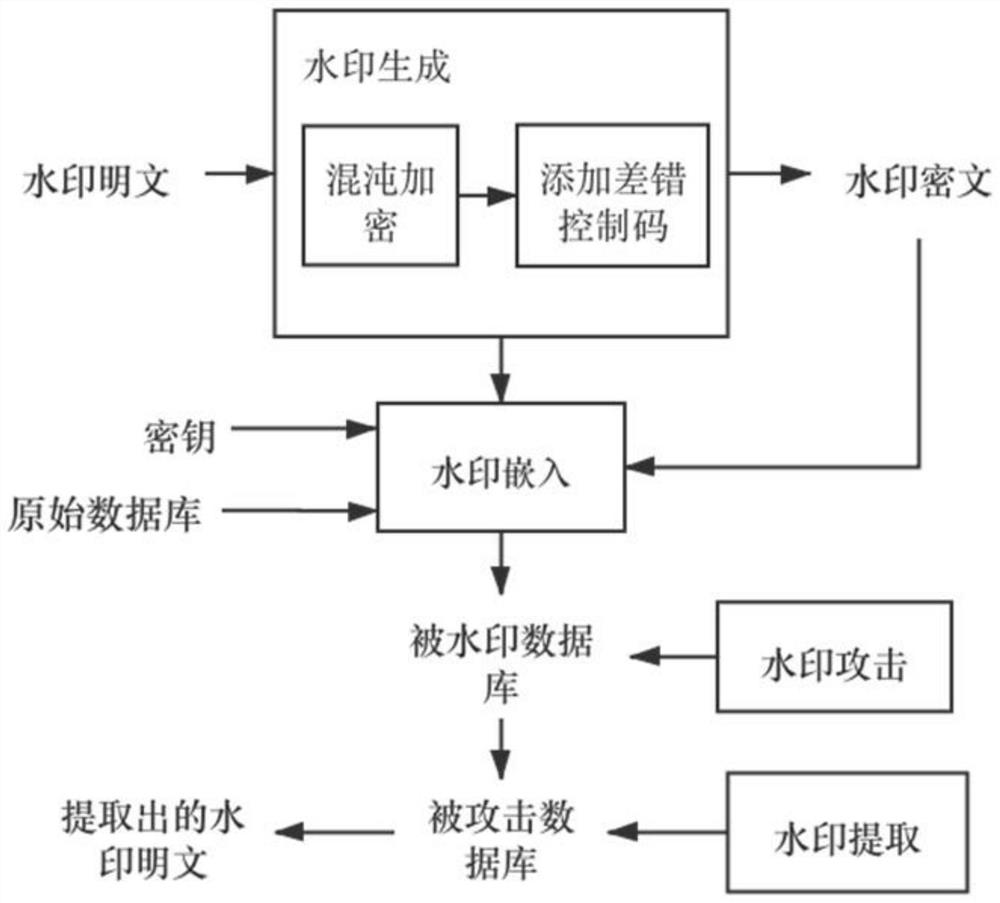
[0036] Embodiment 1: as figure 1 As shown, it is a schematic diagram of the overall functional structure implemented by the present invention. The present invention provides a digital watermarking algorithm for numerical attributes of relational databases. Specifically include the following steps:
[0037] A. Convert watermark plaintext to binary sequence;
[0038] B. Use chaotic encryption to scramble the watermark binary sequence, and add BCH (31,16,7) error control codes to the scrambled sequence;
[0039] C. Execute the watermark embedding program with each redundant numerical attribute column as a unit; determine the embedded watermark tuple according to the database owner's personal private key and embedding ratio, and determine the watermark selected for this embedding process according to the watermark length The watermark bit value in the information binary sequence, and the value bit to be modified is randomly selected;
[0040] D. Publish the database table embe...
Embodiment 2
[0066] Embodiment 2: In this embodiment, the geographic location database is used as an example to carry out this instance. An example of part of the data in the database is shown in Table 2.
[0067] Table 2 Partial data example of the database
[0068] user id longitude 2011024425454226447 122.102229 2226391011334799248 123.344526 3243242432444454345 121.2313343 3232432444445544334 123.323223 3242224344552231324 122.233323
[0069] Step 1: The watermark information to be embedded is a binary image, such as figure 2 As shown, converted to binary "0000000000000000000000000...00111100000011000000000000000000
[0070] 0000111011001111111110000001100011111111110...00001110011100
[0071] 00…0000000000000000000000” with a total of 2304 digits;
[0072] Step 2: Group each 16-bit group. Let μ=3.8, X0=0.5, then have
[0073] X(k+1)=3.8Xk(1-Xk)
[0074] Scramble each group according to the above function. For example, if a sequence is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com