High-expansibility password encrypted storage method
A high scalability, encrypted storage technology, applied in the field of computer information technology security, can solve problems such as restricting the use of new encryption algorithms in new systems, and achieve the goal of improving scalability and maintainability, increasing difficulty, and ensuring security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
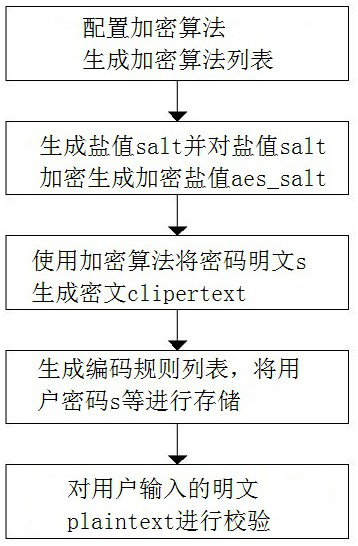
[0051] This embodiment proposes a highly scalable password encryption storage method, such as figure 1 shown, including the following steps:
[0052] Step 1: first obtain the list of encryption algorithms generated by the encryption algorithm configuration module; the list of encryption algorithms includes a plurality of encryption algorithms, and each of the encryption algorithms has a unique encoding code and corresponding name and type; the type includes system built-in and user-added;
[0053] Step 2: Generate a 32-bit random string in the encrypted salt value generation module, and the random string is the salt value salt of the encryption algorithm; then perform symmetrical encryption on the salt value salt by the AES algorithm to obtain the encrypted salt value aes_salt;
[0054] Step 3: Obtain the encryption algorithm set by the user in the password encryption module, and judge whether it is necessary to use the salt value salt to encrypt the user password s through ...
Embodiment 2
[0061] In this embodiment, on the basis of the above-mentioned embodiment 1, in step 1, the specific steps are:
[0062] Step 1.1: The user obtains a list of password encryption algorithms. Each encryption algorithm has a unique code and corresponding name and type, including system built-in and user added; system built-in encryption algorithms such as md5, sha, hamc, pkddf2, crc, etc.:
[0063] Step 1.2: The user selects the password encryption algorithm that the user wants to set. If there is an encryption algorithm that the user wants to set in the current encryption algorithm list, directly select the algorithm and set it; otherwise, add and set it through step s1.3;
[0064] Step 1.3: The user adds the implementation of the encryption algorithm, and names the encryption algorithm. After the addition is successful, the system will generate a unique code for the newly added encryption algorithm; then obtain the list of encryption algorithms, and set the newly added encryptio...
Embodiment 3
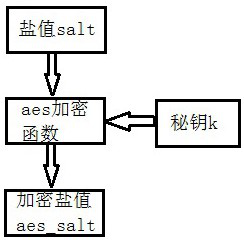
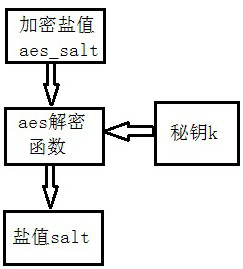
[0079] This embodiment is based on any one of the above-mentioned embodiments 1-2, such as figure 2 , image 3 As shown, encrypt the salt value salt to generate the encrypted salt value aes_salt and decrypt the encrypted salt value back to the salt value salt;
[0080] The following briefly introduces the function and significance of each part:
[0081] Salt value salt: unencrypted data, in this system is the unencrypted salt value salt
[0082] Key K: the salt value salt used to encrypt the plaintext. In the symmetric encryption algorithm, the key k for encryption and decryption is the same. The key k is generated through negotiation between the receiver and the sender, but it cannot be directly transmitted on the network, otherwise the key k will be leaked. Usually, the key k is encrypted by an asymmetric encryption algorithm, and then transmitted to the other party through the network, or Negotiate the key k directly face to face. The key k must never be leaked, otherw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com