Private protocol fuzzy test case generation method based on byte length classification
A proprietary protocol, byte-length technology, applied in electrical components, transmission systems, etc., can solve the problems of low test efficiency and low positioning accuracy, and achieve the effect of high real-time performance and low technical level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
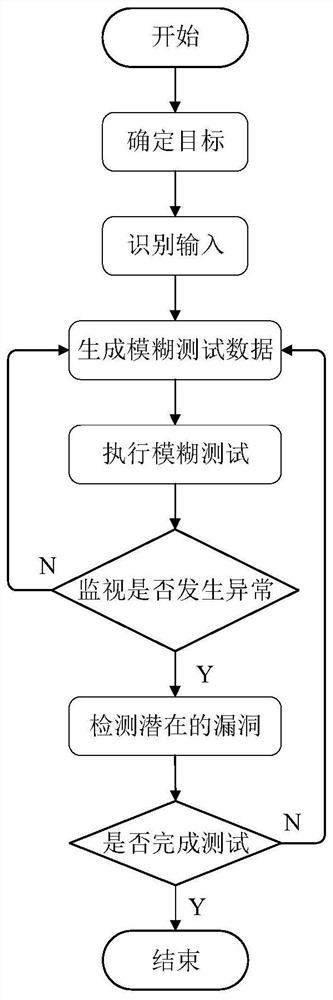
[0031] For the public industrial control system communication protocol, we can clearly know the content of the protocol according to the protocol specification, and then specify the test strategy, but for the private protocol, we cannot know the content of the protocol specification, and we need to conduct a preliminary analysis of the protocol. The current method of fuzzy testing for industrial control systems has shortcomings such as too simple and random fuzzy data, low accuracy for abnormal positioning, and low test efficiency. In addition, testers need to be very familiar with the protocol. The requirements of high standards, high coverage and high efficiency cannot be met.
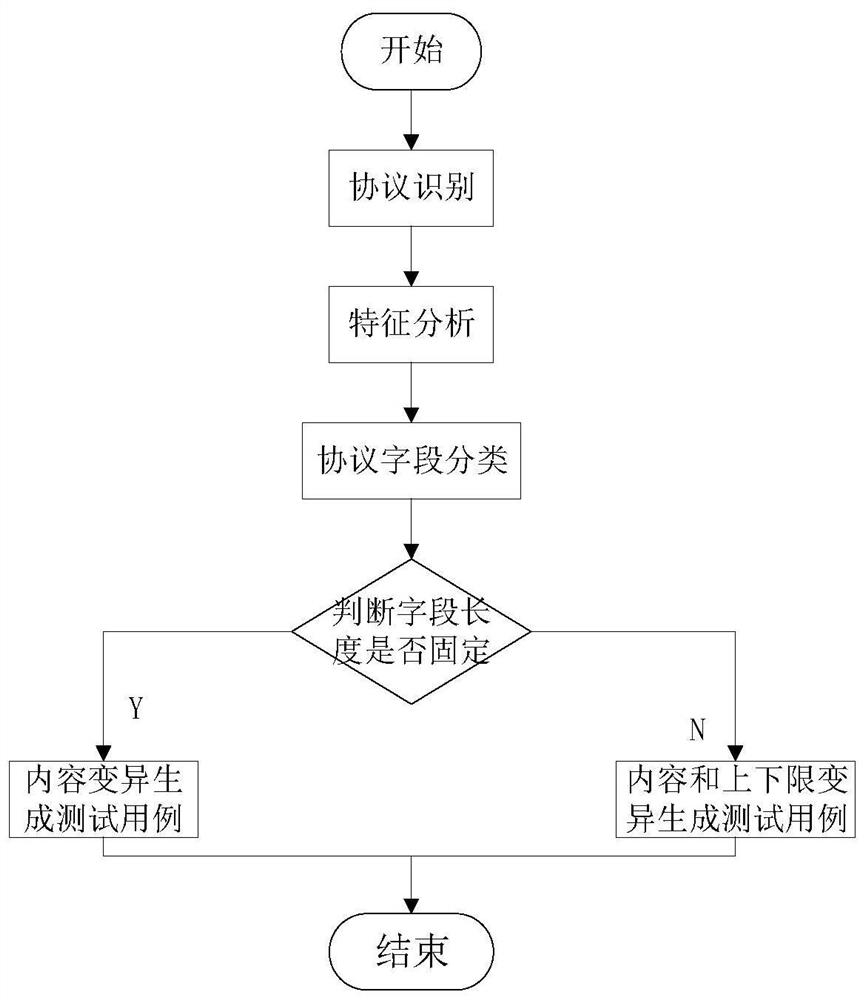
[0032] refer to Figure 1~3 , is an embodiment of the present invention, provides a kind of private protocol fuzzy test case generation method based on byte length classification, comprising:
[0033] S1: Use the MSA data flow to compare and analyze the characteristics of the private protocol to det...
Embodiment 2
[0061] The technical effects adopted in this method are verified and explained. In this embodiment, OpenVAS (Open Vulnerability Assessment System) is selected for comparative testing with the method of the present invention, and the test results are compared by means of scientific demonstration to verify the real effect of this method.
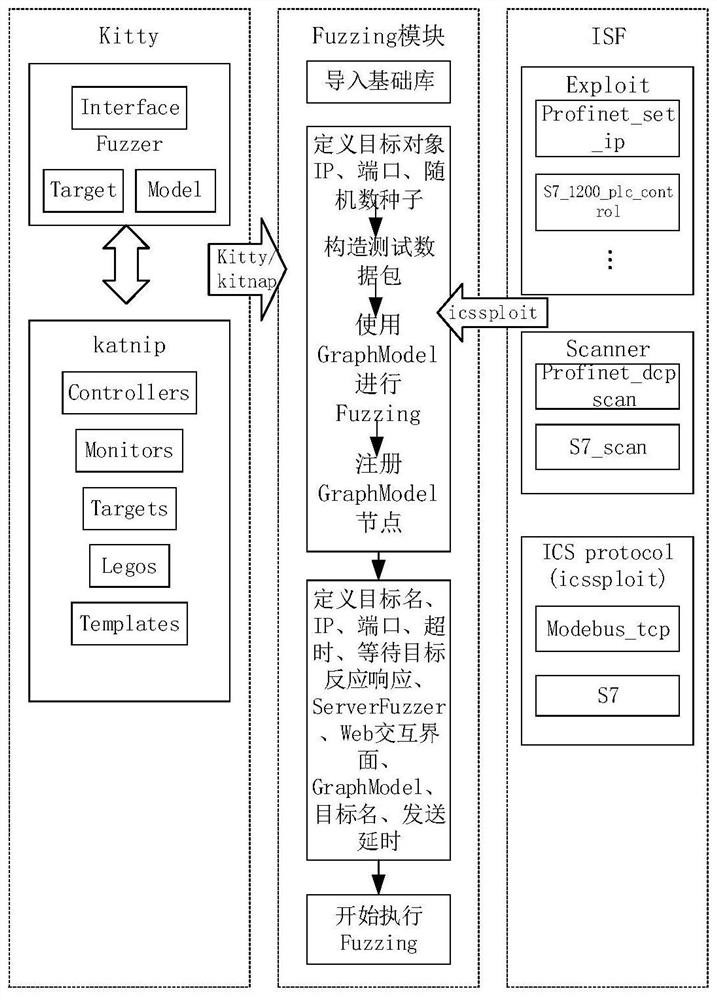
[0062] Among them, OpenVAS (Open Vulnerability Assessment System) is a network scanner that includes related tools, and its core component is a server, including a set of network vulnerability testing programs, which can detect security problems in remote systems and applications. Such as figure 1 As shown, using the Kitty fuzz testing framework combined with the industrial control protocol components in the ISF and traditional technical solutions to execute the fuzz test protocol on the Siemens S7comm protocol to perform fuzz testing to find vulnerabilities. Firstly, Kitty sets the interface and target, and can connect with the target three t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com