A graph-based threat intelligence analysis method for honeypot systems
An analysis method and intelligence technology, applied in the field of network security, can solve problems such as deep mining of inaccessible data, and achieve the effect of improving data processing efficiency, improving trapping efficiency, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
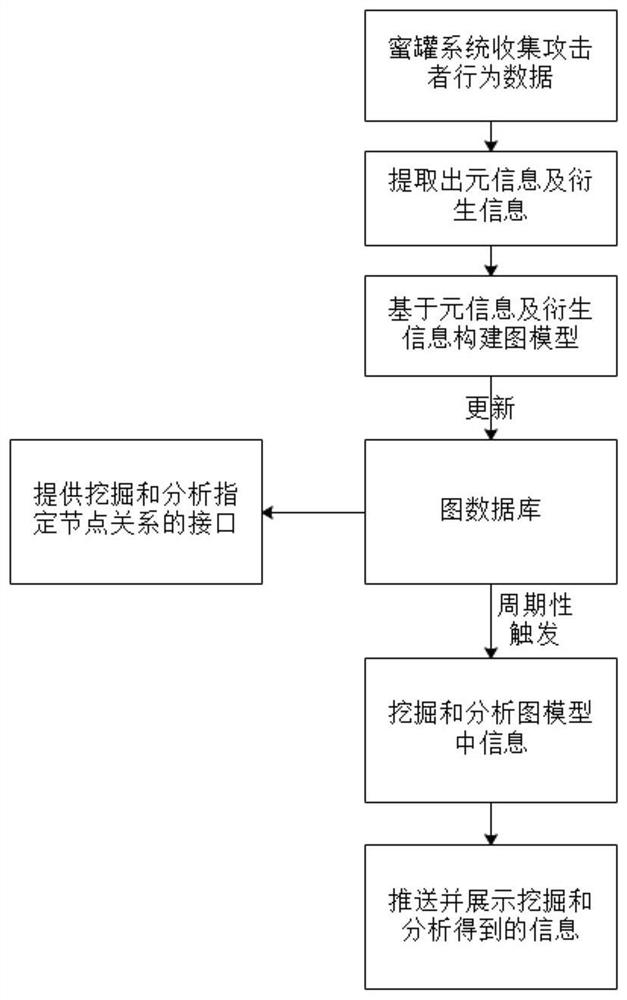
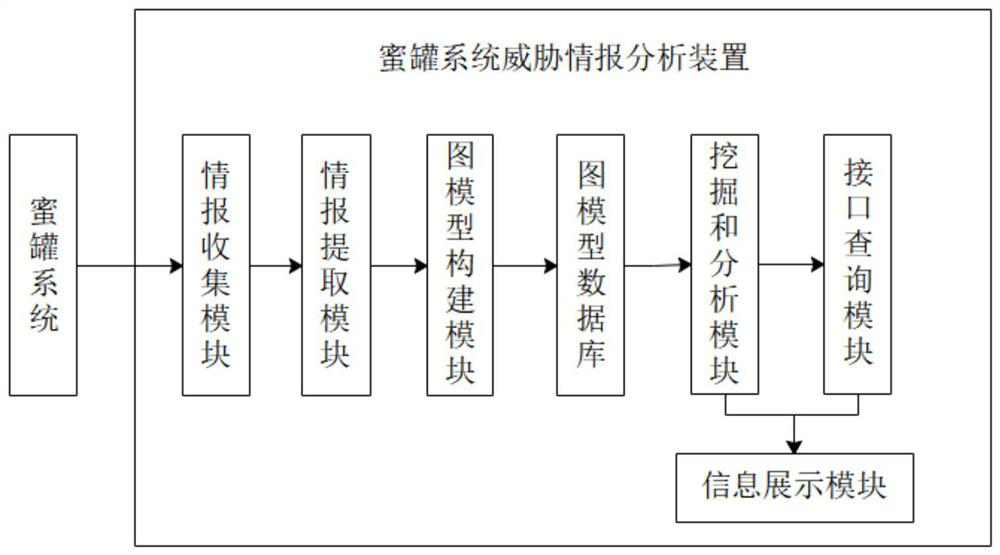
[0088] The process of mining and analyzing the correlation between the attack sources is as follows:
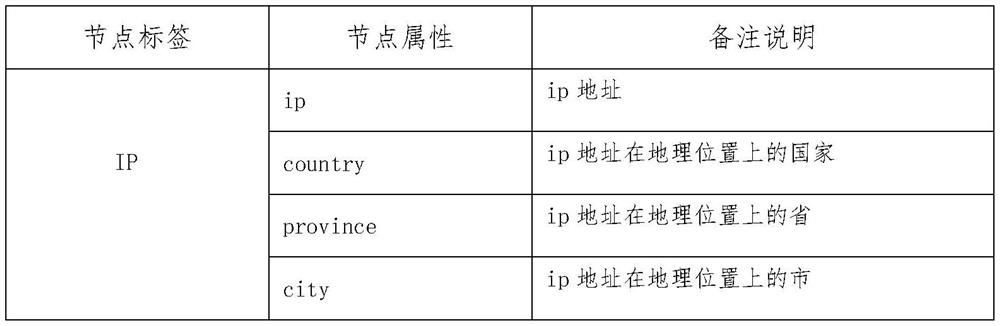
[0089] Select SAMPLE, SAMPLE_FUZZY, SAMPLE_NAME, URL, TOOL_PAYLOAD nodes associated with IP nodes in the graph model;
[0090] Use the community discovery algorithm to mine and analyze the community groups existing in the attack source IP attacking the honeypot system;
[0091] The frequent subgraph mining algorithm is used to dig out attack tools with high frequency of use by attack sources, and analyze the attack habits and attack levels of attack sources.
Embodiment 2
[0093] The fuzzy relationship mining and analysis process between the malicious files is as follows:
[0094] Select all SAMPLE_FUZZY nodes in the graph model;
[0095] Calculate the similarity of fuzzy hash values between SAMPLE_FUZZY, for example, using a string similarity comparison algorithm to determine the similarity between two fuzzy hash values, thereby judging the similarity between two files;
[0096] Associate the SAMPLE_FUZZY nodes whose similarity is greater than the threshold to obtain the relationship between malicious files.
Embodiment 3
[0098] The mining and analysis process of the malicious file family derivative map is as follows:
[0099] Select all SAMPLE, SAMPLE_FUZZY, RELEASE_FIL and REALSE_FILE_FUZZY nodes in the graph model;
[0100] Based on the SAMPLE, SAMPLE_FUZZY, RELEASE_FIL and REALSE_FILE_FUZZY nodes, respectively calculate the node similarity of the hash value or fuzzy hash value between each node;
[0101] Associate the nodes whose node similarity is greater than the threshold to construct a family derivative graph of malicious files;
[0102] Based on the family derivation map of malicious files, the evolution and derivation process of malicious files can be analyzed, and the evolution and derivation process of attack tools and the technical capability level of attackers can be known.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com