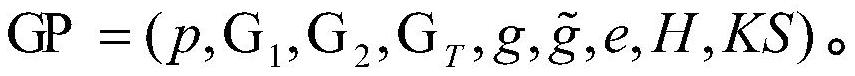Security-enhanced keyword search method based on public key encryption
A keyword search and public key encryption technology, which is applied in the field of keyword search based on public key encryption, can solve problems such as security doubts and security that need further verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the purpose, content and advantages of the present invention clearer, the specific embodiments of the present invention will be described in further detail below with reference to the accompanying drawings.
[0037] The core idea of the specific structure of the SCF-PEKS scheme of the present invention comes from the IBE scheme proposed by Water. In order to realize the receiver anonymity of the scheme, the present invention uses the characteristics of asymmetric bidirectional groups to improve the scheme, and based on anonymity The IBE scheme further constructs an SCF-PEKS scheme, which achieves better results in terms of functionality, performance and security.
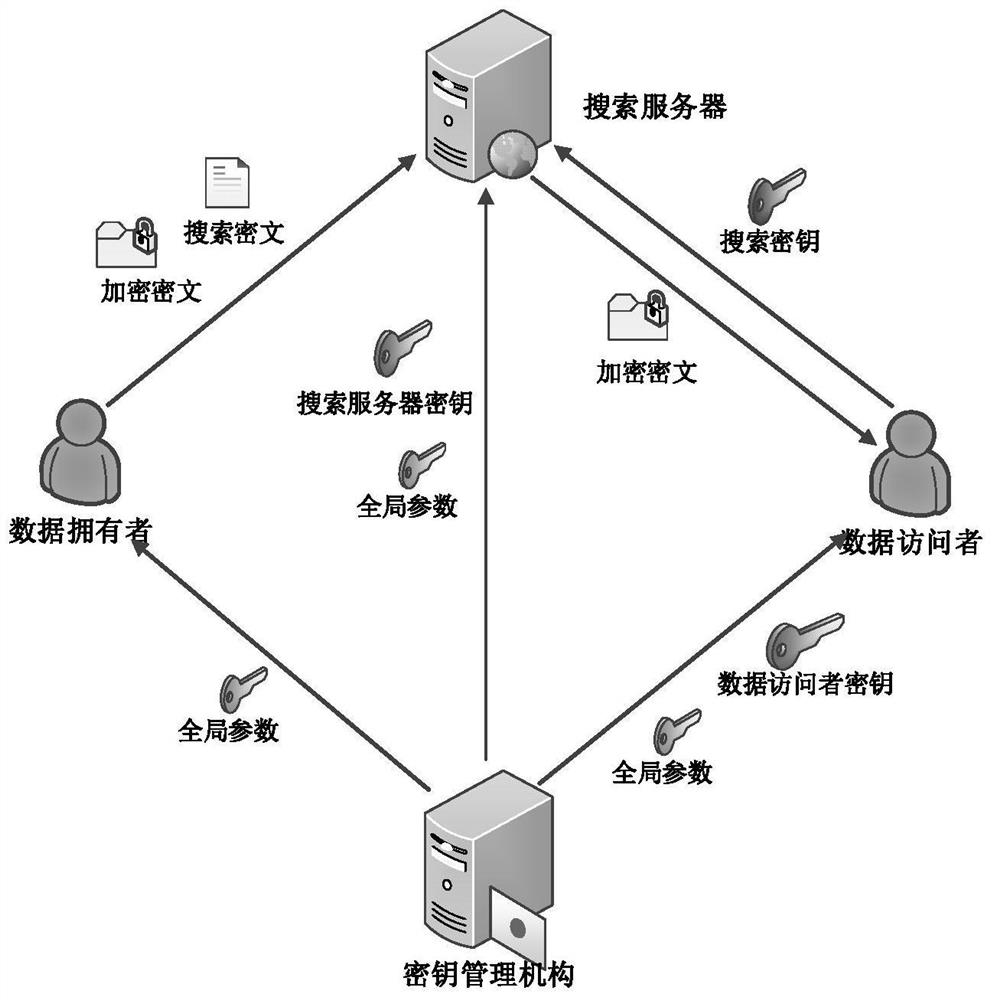
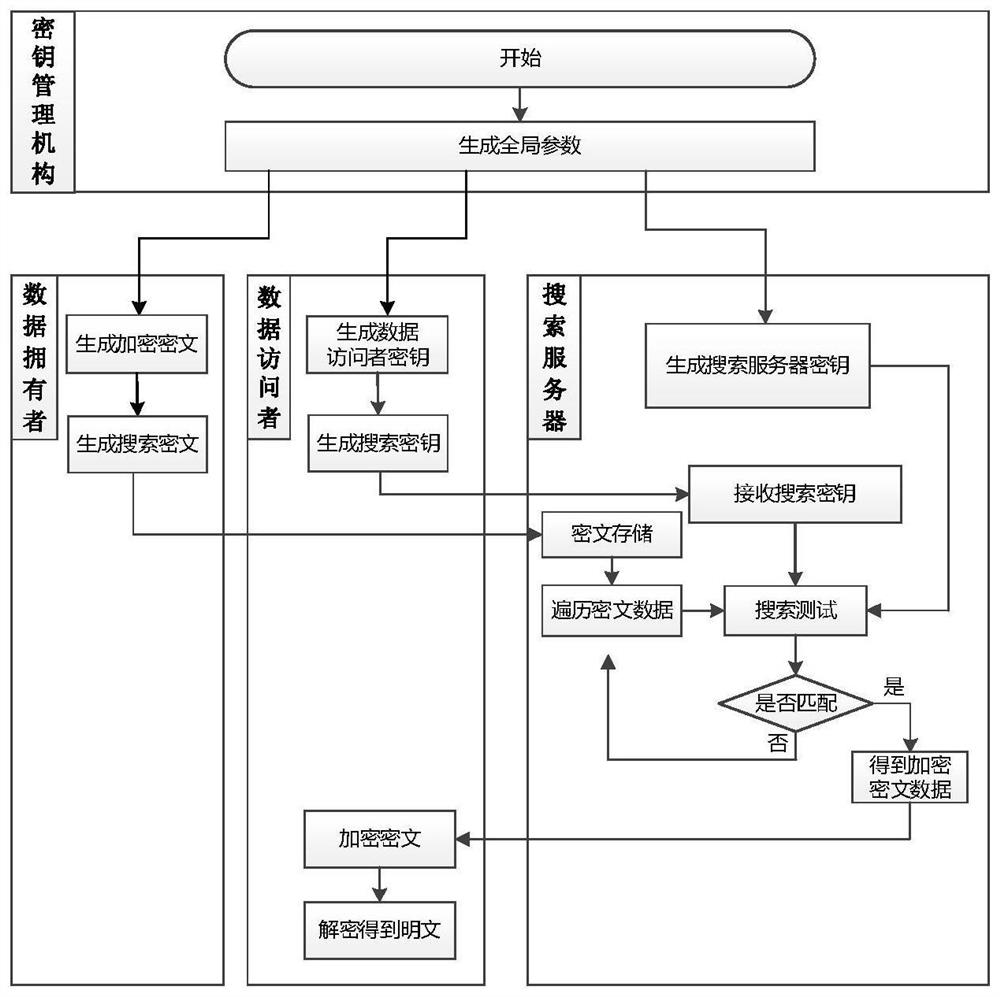
[0038] as attached figure 1 and figure 2 As shown, the scheme mainly includes four components: key management authority, data owner, data visitor and search server, wherein the key management authority is responsible for generating global parameters, search server key and data visitor key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com