Anti-vulnerability mining method and device based on code injection
A vulnerability mining and code injection technology, which is applied in program code conversion, computer security devices, decompilation/disassembly, etc., can solve the problems of third-party dll library call failure, inability to achieve cross-platform protection, etc., to prevent and block exceptions Effects of monitoring, reducing efficiency, hindering execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
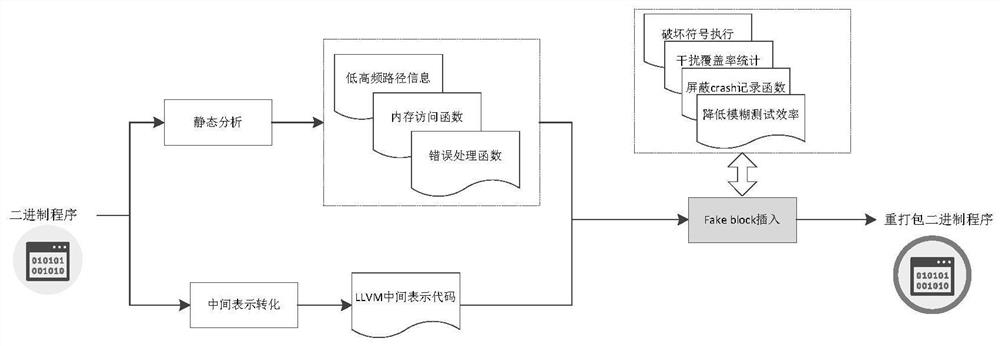
[0045] Such as figure 1 As shown, an anti-vulnerability mining method based on code injection includes:
[0046] Step S101: Based on the built common function library, perform static analysis on the target binary program;
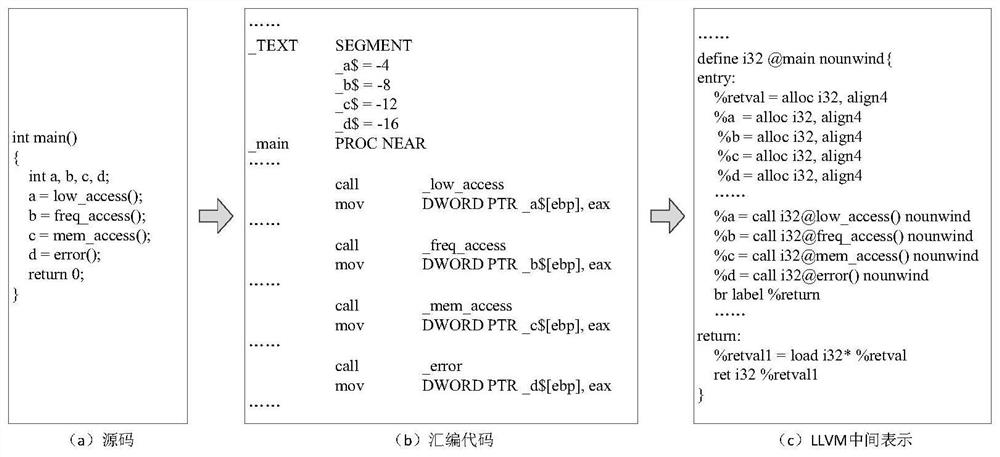
[0047] Step S102: converting binary programs from different sources into a unified LLVM (Low Level Virtual Machine) intermediate representation;
[0048] Step S103: Perform pseudo-code block injection on the basis of obtaining the LLVM intermediate representation.
[0049] Further, the step S101 includes:
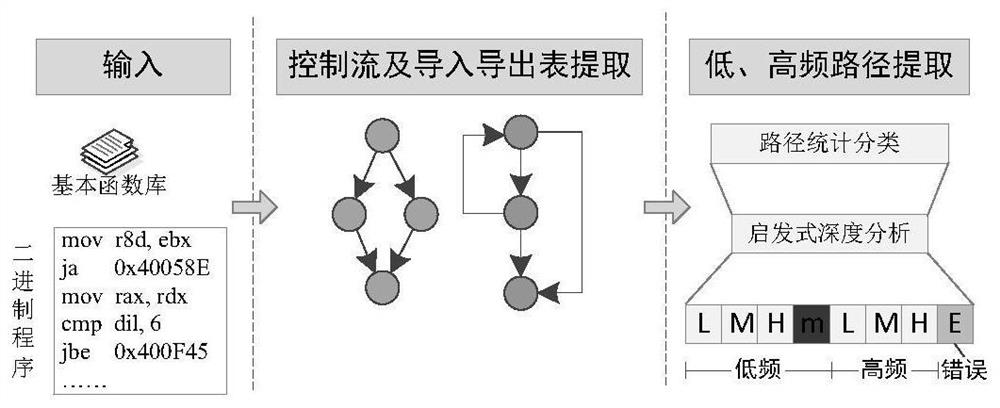
[0050] Step S101.1: Decompile all binary programs by using the existing network test set, identify memory access functions and error handling functions, and build a function library;
[0051] Step S101.2: Perform IDA reverse analysis on the library function in step S101.1, extract the control flow graph, identify the import a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com