A data processing method and device for a trusted security terminal
A technology for data processing devices and security terminals, which is applied in the fields of electrical digital data processing, computer security devices, digital data protection, etc., and can solve problems such as potential safety hazards, information theft of USB peripherals, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
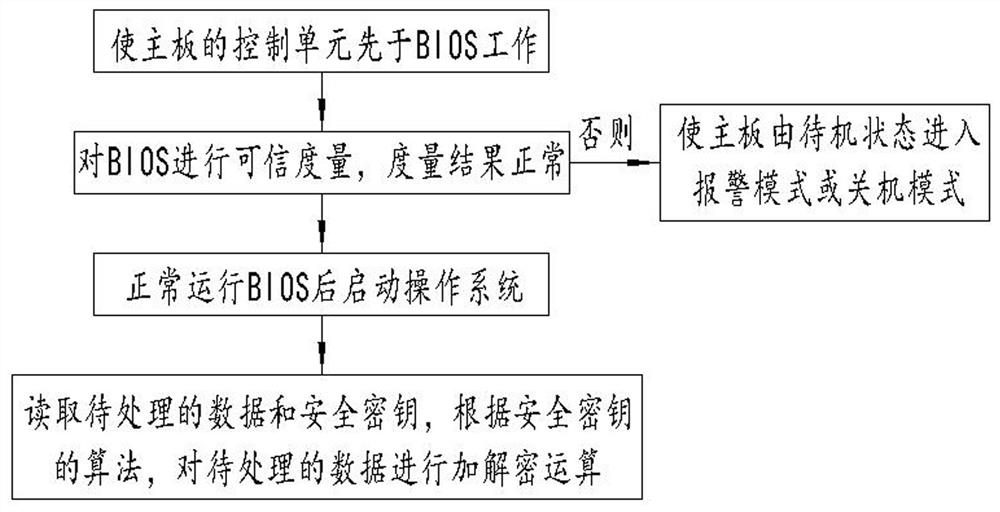
[0038] figure 1 A schematic flowchart of a data processing method for a trusted security terminal provided in Embodiment 1 of the present invention; such as figure 1 As shown, a data processing method for a trusted security terminal provided by this embodiment may include:
[0039] Make the control unit of the mainboard work before the BIOS; perform credible measurement on the BIOS, when the measurement result is normal, run the BIOS normally and start the operating system; otherwise, make the mainboard enter the alarm mode or shutdown mode from the standby state; read the data to be processed And the security key, according to the algorithm of the security key, the data to be processed is encrypted and decrypted.
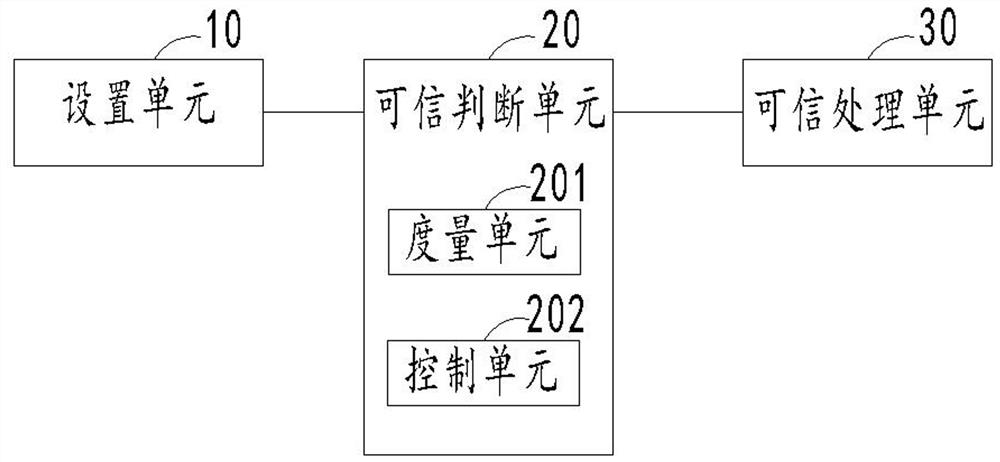
[0040] figure 2 A schematic structural diagram of a data processing device for a trusted security terminal provided in Embodiment 1 of the present invention; such as figure 2 As shown, a data processing device for a trusted security terminal provided by this e...
Embodiment 2
[0044]On the basis of Embodiment 1, this embodiment provides a data processing method for a trusted security terminal. The BIOS is credible measurement. When the measurement result is normal, the operating system is started after running the BIOS normally. Otherwise, the motherboard Entering the alarm mode or shutdown mode from the standby state specifically includes: performing credible measurement on the BIOS; receiving the measurement result, and converting the measurement result into a signal for controlling the state of the mainboard; the signal for controlling the state of the mainboard includes: causing the mainboard to enter from the standby state BIOS system, or make the main board enter the shutdown mode from the standby state; or make the main board enter the alarm mode from the standby state.
[0045] image 3 A schematic structural diagram of a data processing device for a trusted security terminal provided in Embodiment 2 of the present invention, such as image...
Embodiment 3
[0053] On the basis of the first embodiment, this embodiment provides a data processing method for a trusted security terminal, wherein the data to be processed and the security key are read, and the data to be processed is added according to the algorithm of the security key. Decryption operations, which may include:
[0054] Acquire the data to be processed; perform protocol conversion on the data to be processed, cache and store it; read the security key; perform encryption and decryption operations on the data to be processed according to the encryption and decryption algorithm in the security key.
[0055] Image 6 A schematic structural diagram of a data processing device for a trusted security terminal provided in Embodiment 3 of the present invention, such as Image 6 As shown, this embodiment provides a data processing device for a trusted security terminal. On the basis of Embodiment 1, the trusted processing unit 30 may include: an obtaining unit 301 for obtaining ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com