Malicious behavior recognition method, system and storage medium for weighted heterogeneous graph
An identification method and heterogeneous technology, applied in the field of network security, can solve problems such as poor generalization ability, slow model update speed, and insufficient use of relational attributes, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
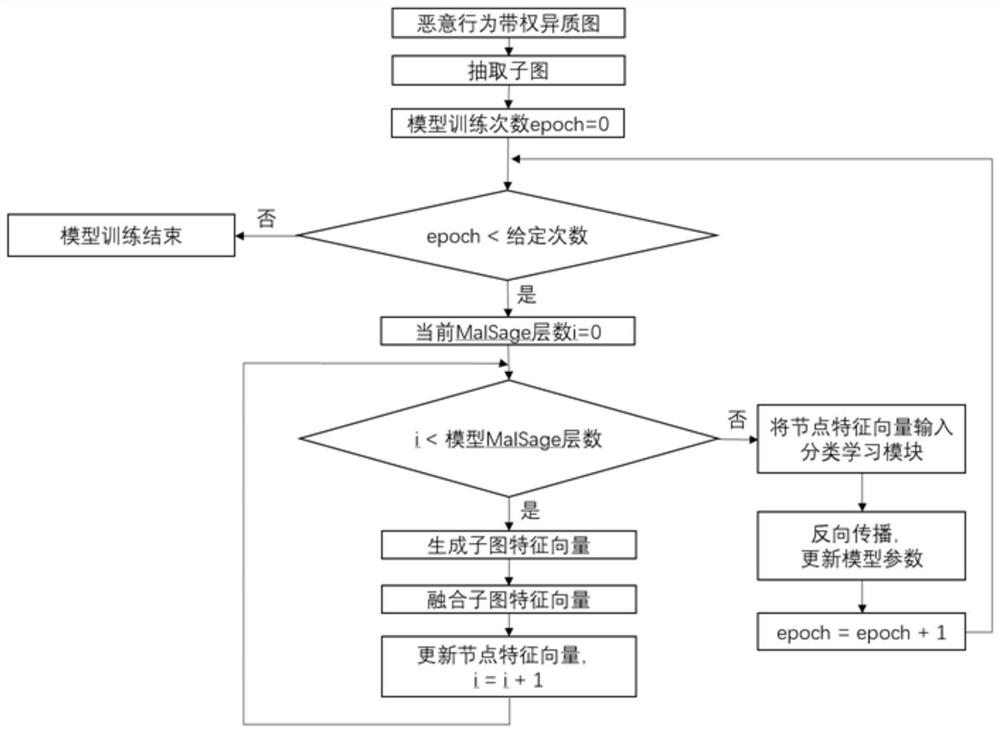
[0057] Such as figure 1 , figure 2 As shown, in the present invention, a malicious behavior recognition method for a weighted heterogeneous graph includes the following steps:
[0058] S1. Construct an inductive graph neural network model, specifically:
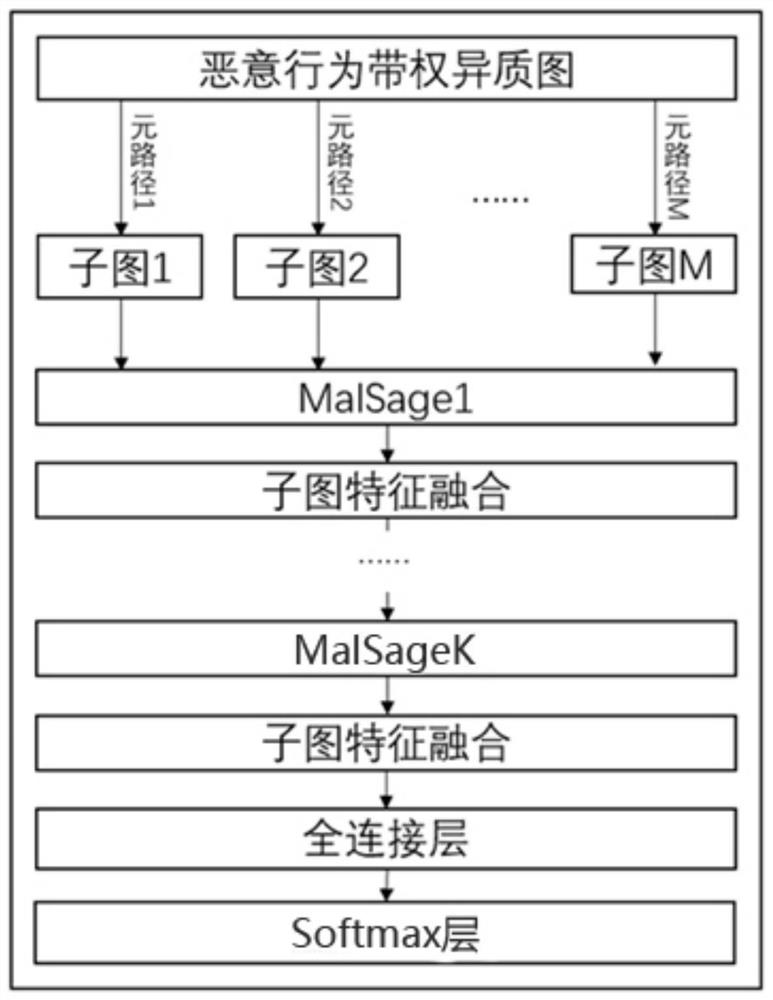
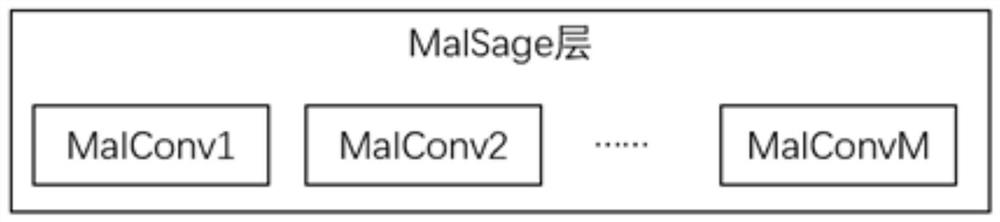
[0059] In this embodiment, the inductive graph neural network model includes a subgraph extraction module, a plurality of feature vector generation fusion modules, and a classification learning module; the feature vector generation fusion module includes a MalSage layer and a subgraph feature fusion layer; the The MalSage layer includes M MalConv layers, which act on M subgraphs respectively. For details, see image 3 ; The classification learning module includes a fully connected layer and a Softmax layer.
[0060] In this embodiment, the input of the inductive graph neural network model is a weighted heterogeneous graph constructed based on the malicious behavior data set, the original feature vector of the node, and mu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com