Identity authentication method and protection method for ensuring security of encryption device
An encryption device and identity authentication technology, applied in digital data authentication, internal/peripheral computer component protection, etc., can solve the problems of high failure rate of encryption device and low safety factor, achieve low power consumption, low equipment failure rate, easy The effect of installation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
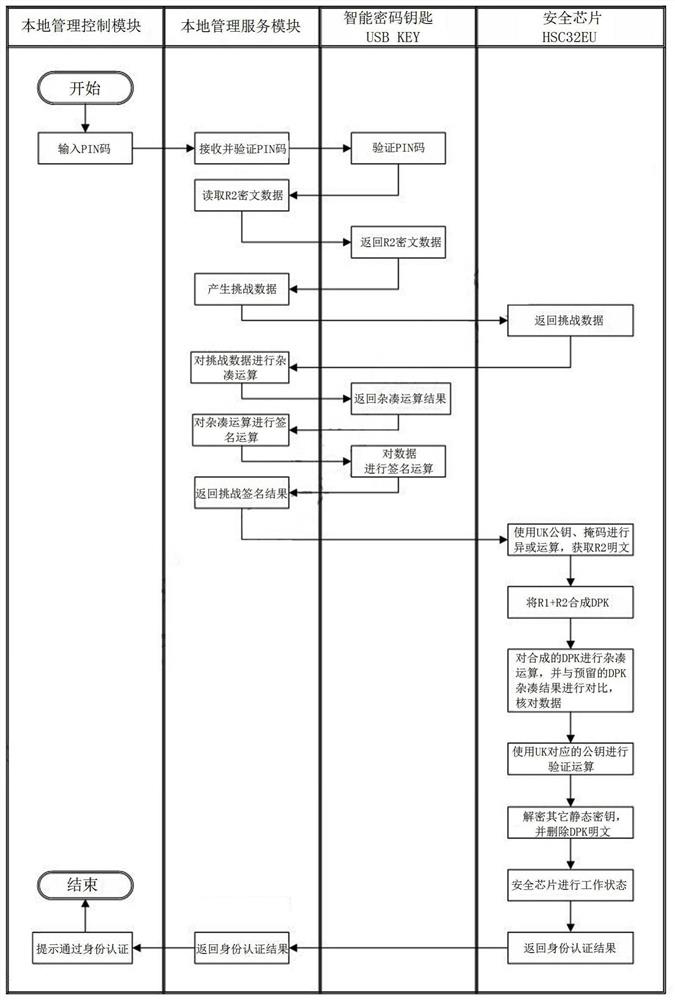
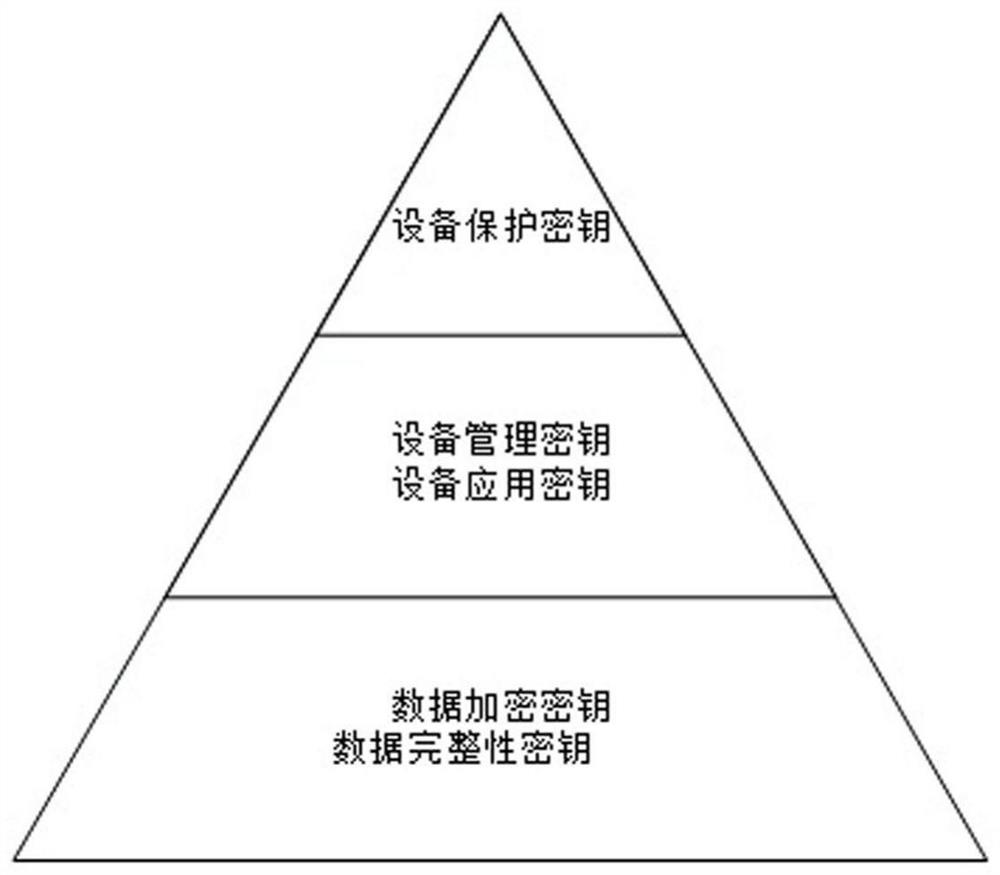
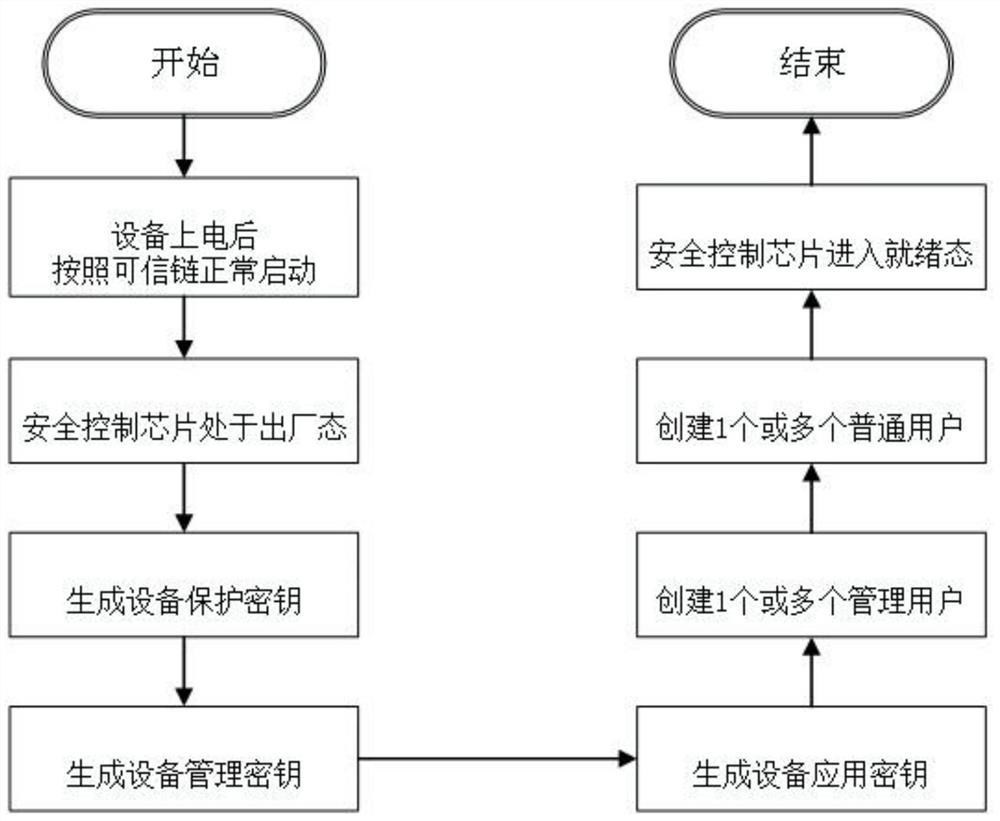
[0066] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0067] A miniature transmission encryption device based on embedded technology, combined with Figure 5 to Figure 8 Shown, including Encryption Guard hardware part and Encryption Guard software part.
[0068] Encryption Guard is developed on a low-power ARM platform. It uses a hardware security chip as a module for key management and cryptographic operations. It supports dual gigabit network interfaces and has functions such as temperature and humidity sensors, local management, and remote management.
[0069] The encryption guard hardware part includes: business control chip, security control chip, noise source, algorithm coordination processor, multi-mode positioning module, temperature and humidity sensor, smart password key, DDR3 memory, eMMC Flash, reset button, indicator light and SPI Flash.
[0070] Business control chip, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com