Executor construction method of mimicry WAF
A construction method and executive technology, applied in the field of network security, can solve problems such as inability to perceive uncertainty in advance, achieve diversity and redundancy, reduce manslaughter rate and missed kill rate, and balance isomorphic and heterogeneous structures Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
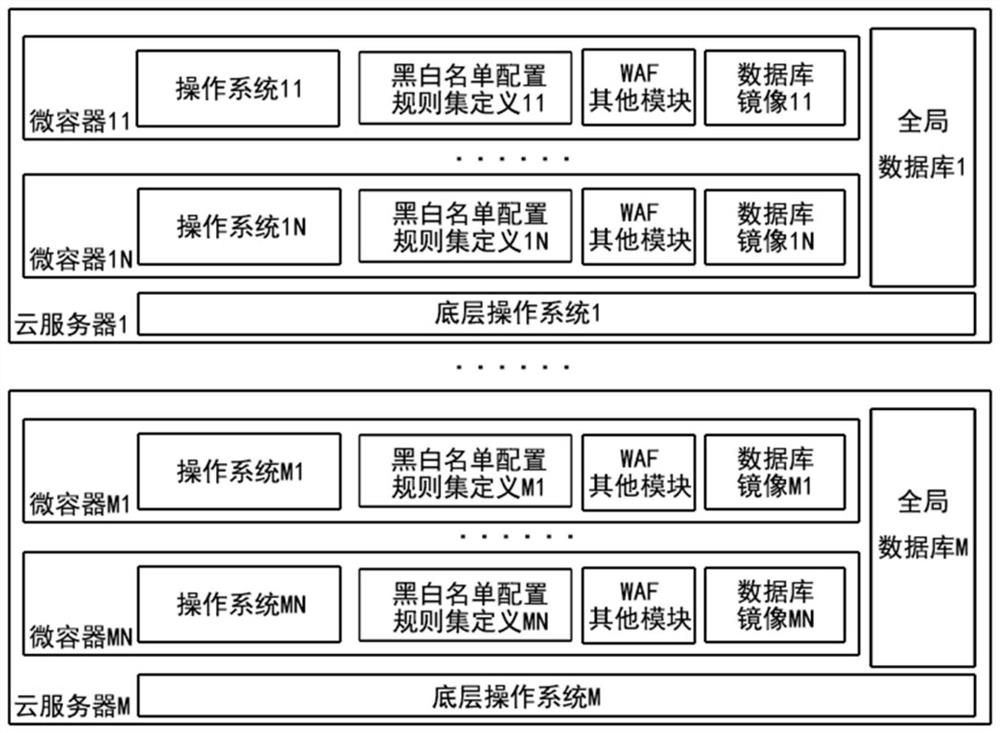
[0027] The present invention focuses on the execution body construction in the mimic WAF, realizes the execution body construction of the mimic WAF through micro-container heterogeneity, database heterogeneity, and WAF interception rule heterogeneity, etc., by setting multiple candidate execution body sets and later dynamic The selection module satisfies the dynamics, majority and redundancy of mimic defense, making WAF have active defense capabilities. In the past, the ruling results of the single executive body structure will directly affect the action execution behavior of WAF, and there will be a large probability of false positives and manslaughter.
[0028] Such as figure 1 As shown, a method for constructing a mimetic WAF executive in the present invention includes operating system heterogeneity, database heterogeneity, WAF platform heterogeneity, and rule set heterogeneity, specifically including the following steps:
[0029] (1) Deploy M cloud servers E={e i |i=1,2,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com