Network intrusion detection method for large flow
A network intrusion detection and large-traffic technology, applied in the field of large-traffic network intrusion detection, can solve problems such as inapplicability to large-traffic application scenarios, and achieve the effects of optimizing processing time, simplifying data processing, and speeding up the data processing process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
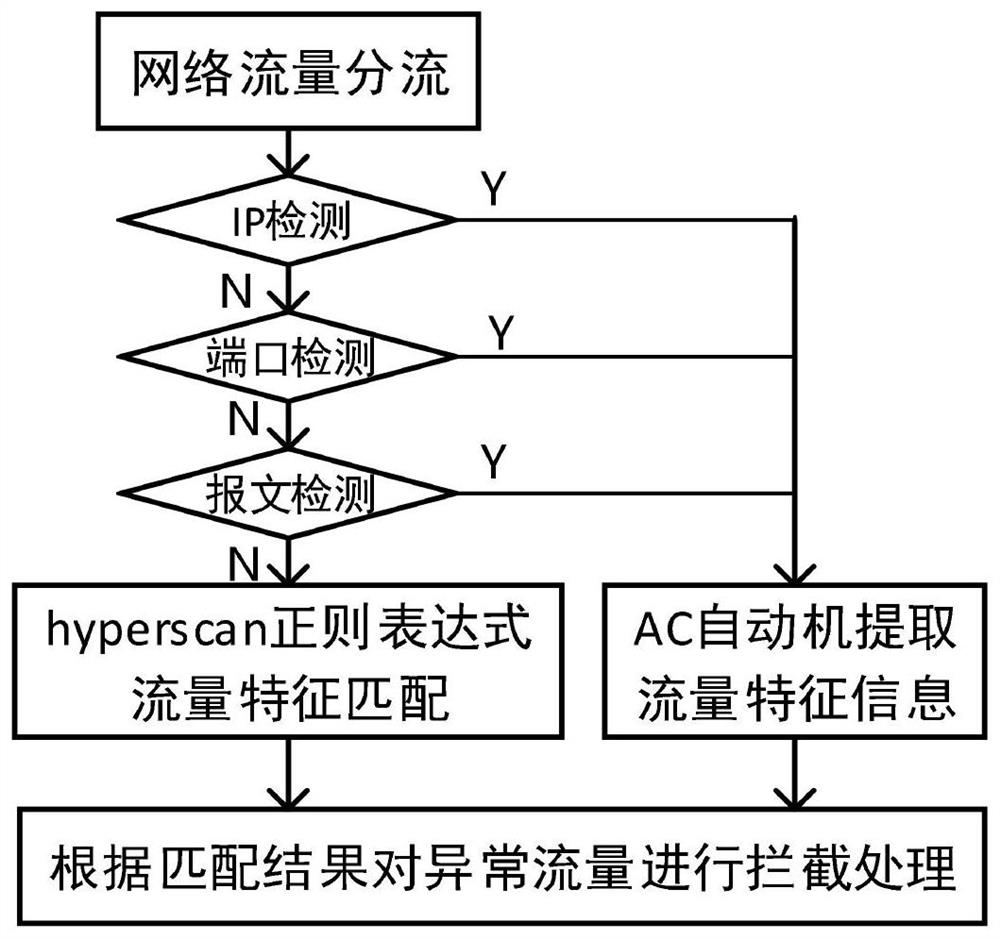
[0021] A network intrusion detection method for large traffic, such as figure 1 shown, including the following steps:
[0022] 1. Obtain and divert network traffic.
[0023] 2. Perform IP detection on the diverted traffic, and the traffic whose protocol type can be determined through IP detection, skip to step 6.
[0024] IP detection is aimed at the network layer of the data packet. The IP address of some Internet services is fixed, and the communication protocol adopted by the service is fixed, so the corresponding relationship between the IP address and the communication protocol is formed. The BM algorithm matching library is established through the IP address and the communication protocol adopted by the service. The corresponding relationship between the IP address and the communication protocol is stored in the matching library. Part of the traffic can be directly detected by the IP to complete the protocol analysis and handed over to the distribution device for proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com