Mining method of normal Server IP white list based on K-Means
A white list, normal technology, applied in the direction of instruments, character and pattern recognition, electrical components, etc., can solve the problems of too much manpower, the inability to fully consider the characteristics of traffic, and difficulty in updating, so as to reduce the detection pressure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
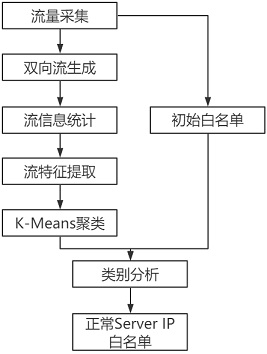
[0015] like figure 1 As shown, the overall process of the present invention includes traffic collection, bidirectional flow generation, establishment of an initial whitelist, flow information statistics, flow feature extraction, K-Means clustering, category analysis, and finally obtains a normal Server IP whitelist, as follows These steps are described in detail.
[0016] 1. Traffic collection
[0017] The present invention needs to pre-collect the network traffic generated by normal users operating computers for a period of time, and save the collected traffic as a pcap file (a datagram storage format) for subsequent processing by using technologies such as Wireshark and Streamdump.
[0018] 2. Initial white list
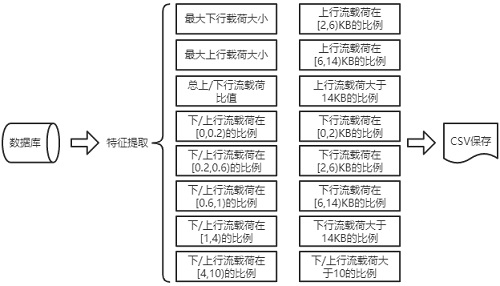
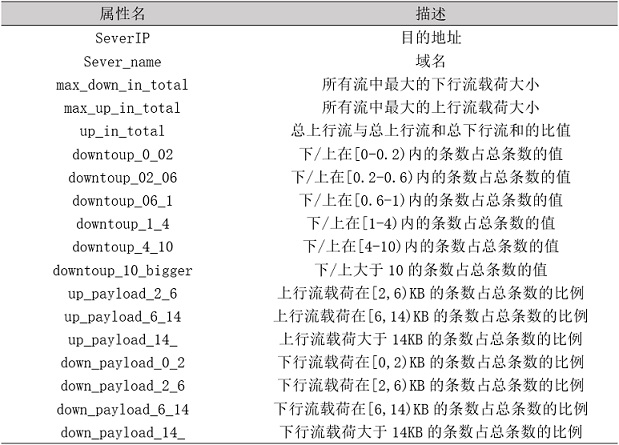
[0019] Use Wireshark to analyze the pcap file obtained in step 1, analyze all the communication records in it, and then extract the relevant Server Name and Server IP of 27 well-known Internet companies and save it as a csv file. The saved content is like "git***...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com