Multi-core security chip processor based on logic expansion and processing method thereof
A security chip and processing method technology, applied in the direction of electrical digital data processing, instruments, multi-programming devices, etc., can solve problems such as nuclear idleness, low efficiency of information security operations, and poor accuracy of operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
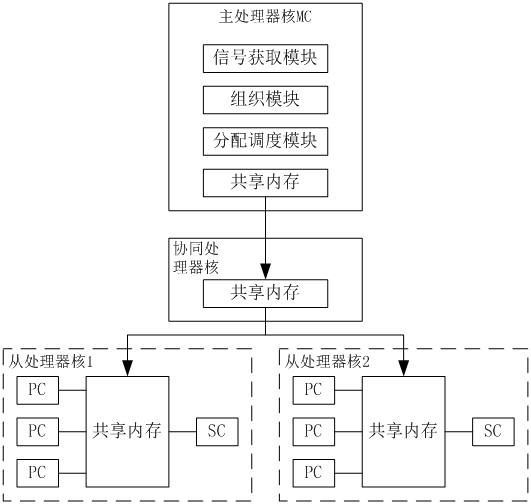
[0047] refer to figure 1 , a multi-core security chip processor based on logic expansion, including a main processor core and multiple heterogeneous slave processor cores, the main processor core includes a signal acquisition module, an organization module and an allocation scheduling module; the signal acquisition module uses To obtain externally transmitted control signals in real time, the organization module is used to dynamically organize multiple slave processor cores according to the operation logic of the safety operation to form a dynamic execution architecture that matches the operation logic of the safety operation; The operation logic of the safety operation decomposes the safety operation into multiple operation tasks, and assigns the operation tasks to the corresponding slave processor cores under the above dynamic execution architecture, and coordinates the operation tasks among multiple slave processor cores; The slave processor cores are respectively used to r...
Embodiment 2
[0056] refer to Figure 4 , a method for processing a multi-core security chip based on logic expansion, comprising the following steps:
[0057] S101: Obtain externally transmitted control signals in real time; specifically, the main processor checks that the logical organization of multiple slave processor cores is dynamic, and each externally transmitted control signal can include different safety operation logics, which can be executed according to each The security operation logic is used to reorganize the execution architecture of multiple slave processor cores to realize dynamic organization.
[0058] S102: Dynamically organize multiple slave processor cores according to the operation logic of the safety operation to form a dynamic execution architecture matching the operation logic of the safety operation; specifically, the main processor core and the plurality of slave processor cores are used for Undertake the computing tasks of the security chip processor, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com