Method and device for detecting account stealing behavior
A behavior and account technology, applied in the field of information security, can solve the problem of low accuracy of detection results, achieve the effect of good detection rate, reduced missed detection rate, and strong pertinence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
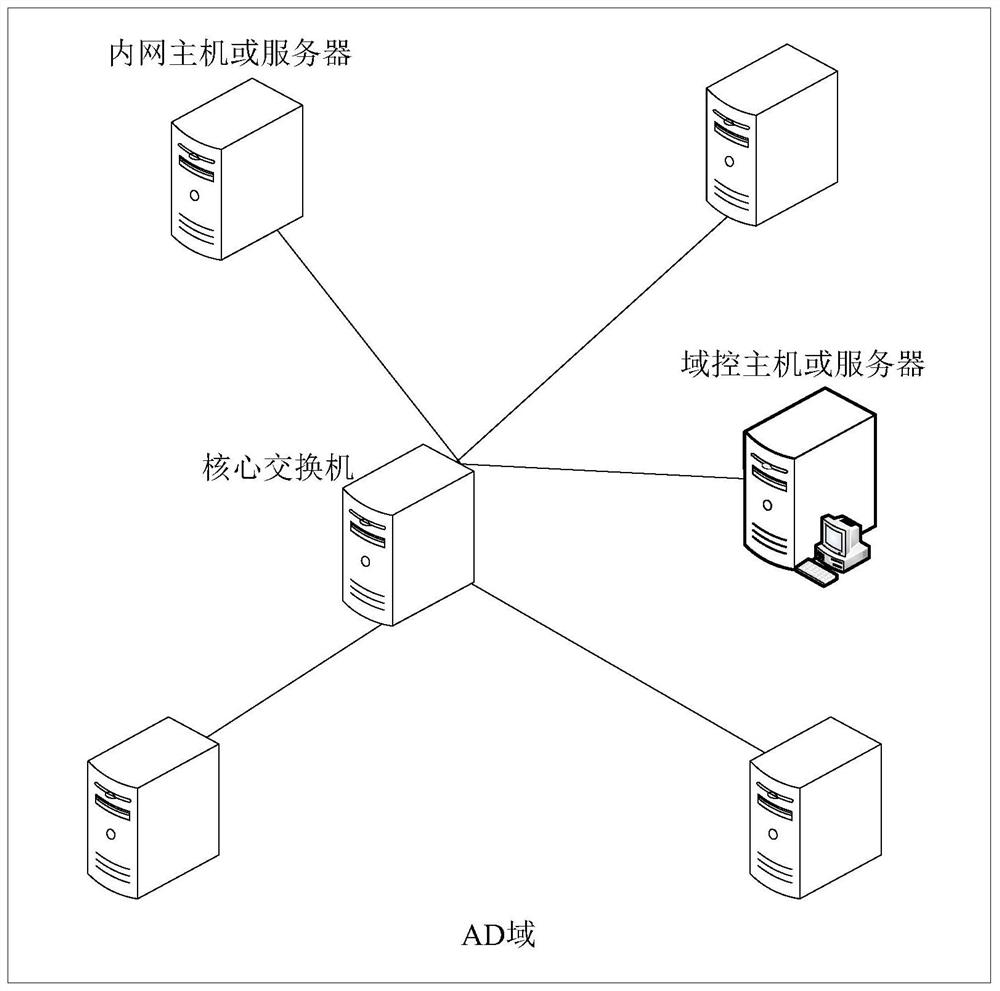
[0061] After the hacker compromises the intranet device in the AD domain, the compromised intranet device becomes a "broiler", and the hacker can manipulate the "broiler" to obtain an account with a higher authority level.
[0062] The inventor of the present application found in the research that when hackers steal accounts with higher authority levels by manipulating "broilers", the stealing methods usually used can be summarized into the following three types:
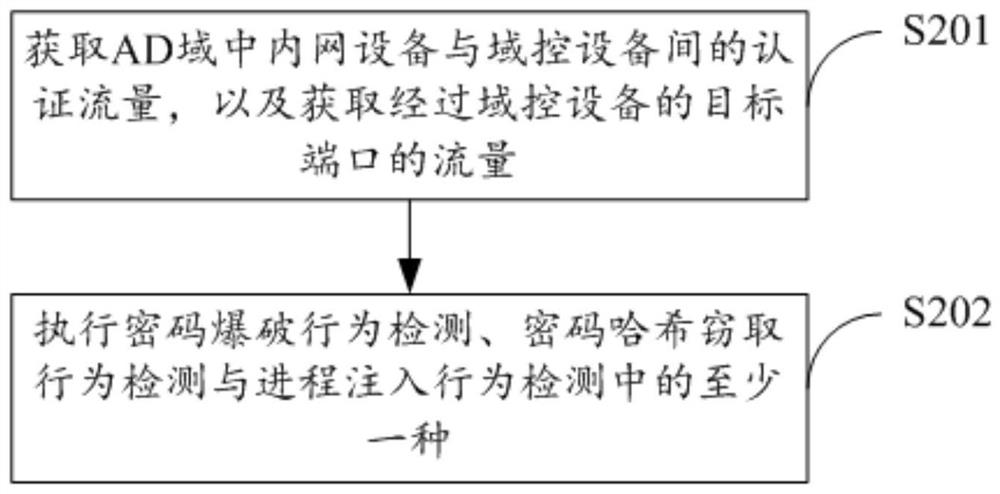
[0063] The first one is password blasting.
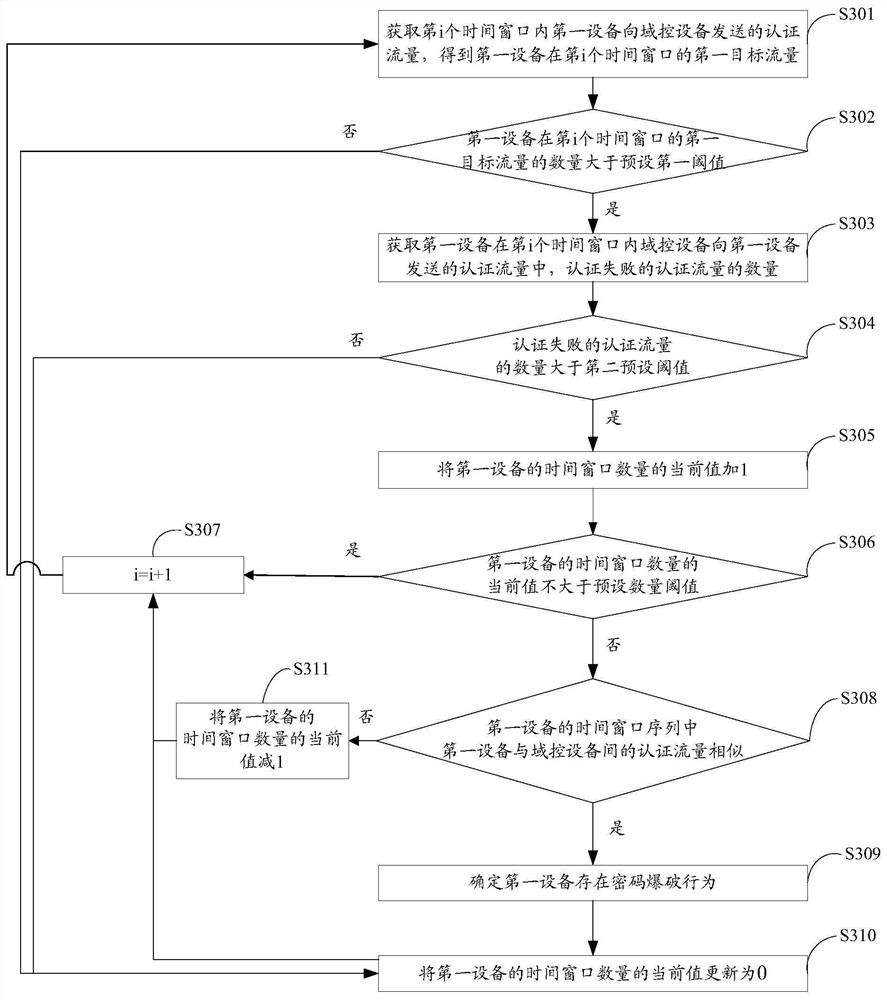
[0064] Password blasting refers to the brute force cracking of the password of the account to be stolen. Specifically, when the hacker manipulates the "broiler" to log in to the account to be stolen, the program can be used to enter different passwords by enumerating different strings in a short period of time until the domain control device successfully authenticates the entered account. Stealing accounts in this way is the least difficult and is the easiest way for hac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com