Network system, and semi-isolated network terminal virus searching and killing method and device
A virus detection and network terminal technology, applied in the field of data processing, can solve problems such as restrictions, user terminals cannot achieve cloud detection and killing, and cannot be directly connected to the public network, so as to avoid pressure, ensure real-time performance, and meet data real-time performance. the effect of the request
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
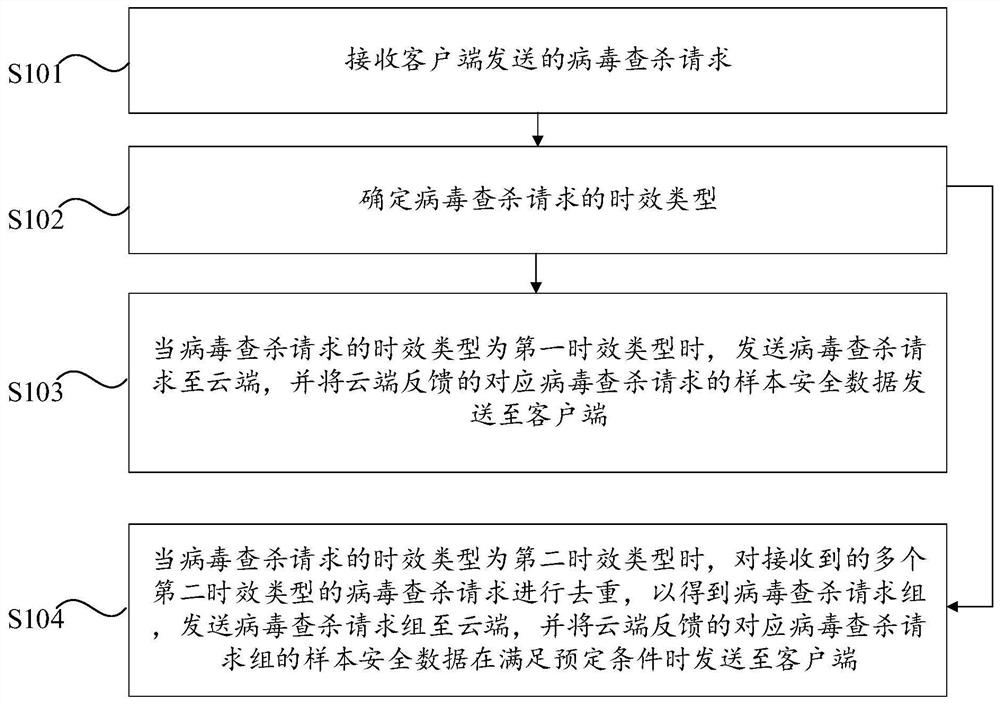
[0035] The embodiment of the present invention provides a half-isolated network terminal virus checking and killing method, the method is applied to the control center in the network system, wherein the network system also includes a number of clients, the clients are set on the semi-isolated network terminal, through this method, It can realize the virus detection and killing of semi-isolated network terminals, and at the same time can ensure the timeliness of the detection and killing results and the special control of the network environment of semi-isolated network terminals. Specifically, figure 1 The flowchart of the semi-isolated network terminal virus scanning and killing method provided by Embodiment 1 of the present invention, such as figure 1 As shown, the semi-isolated network terminal virus scanning and killing method provided in this embodiment includes the following steps S101 to S104.
[0036] Step S101: Receive a virus scanning and killing request sent by a cl...
Embodiment 2
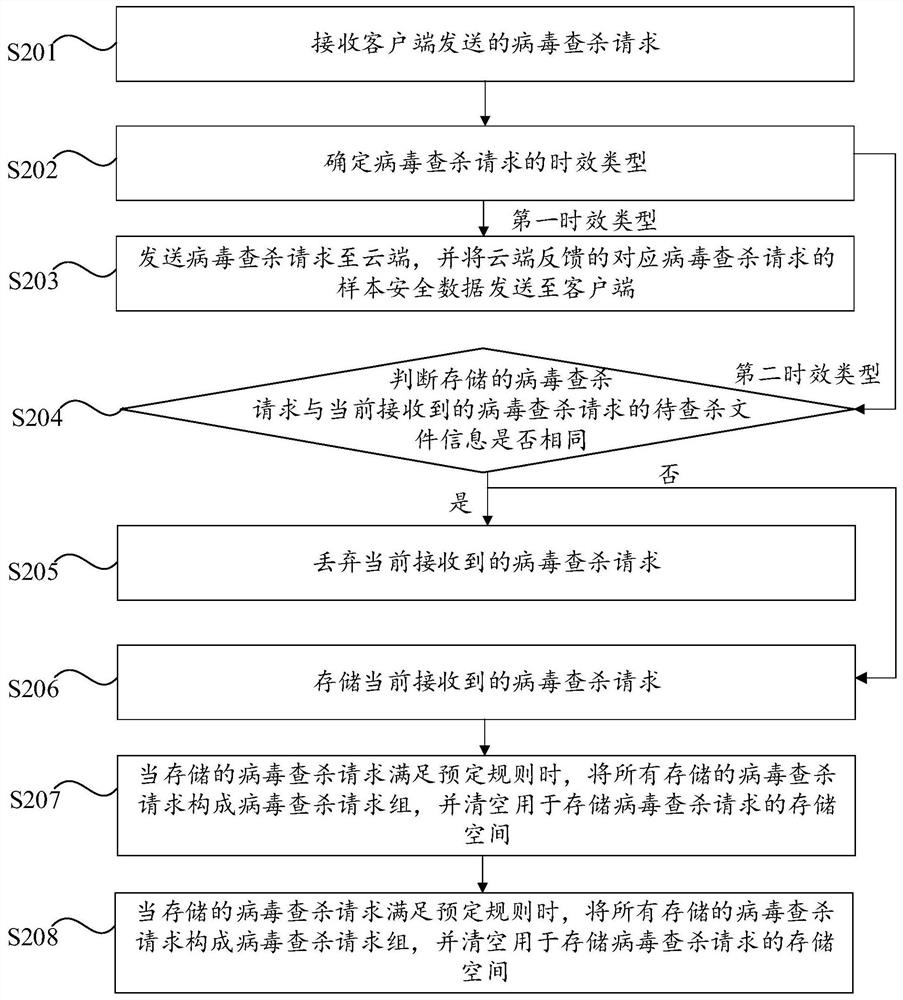
[0057] Embodiment 2 of the present invention provides a preferred semi-isolated network terminal virus scanning and killing method. Part of the features and corresponding technical effects are the same as those in Embodiment 1 above. Reference may be made to Embodiment 1 above, which will not be repeated here. In this embodiment, every time the control center receives a virus scanning and killing request whose aging type is the second aging type, it compares it with the currently stored virus scanning and killing request to ensure that the stored virus scanning and killing requests are not repeated. Specifically, figure 2 The flow chart of the semi-isolated network terminal virus scanning and killing method provided by Embodiment 2 of the present invention, as figure 2 As shown, the semi-isolated network terminal virus scanning and killing method provided in this embodiment includes the following steps S201 to S208.
[0058] Step S201: Receive a virus scanning and killing re...
Embodiment 3
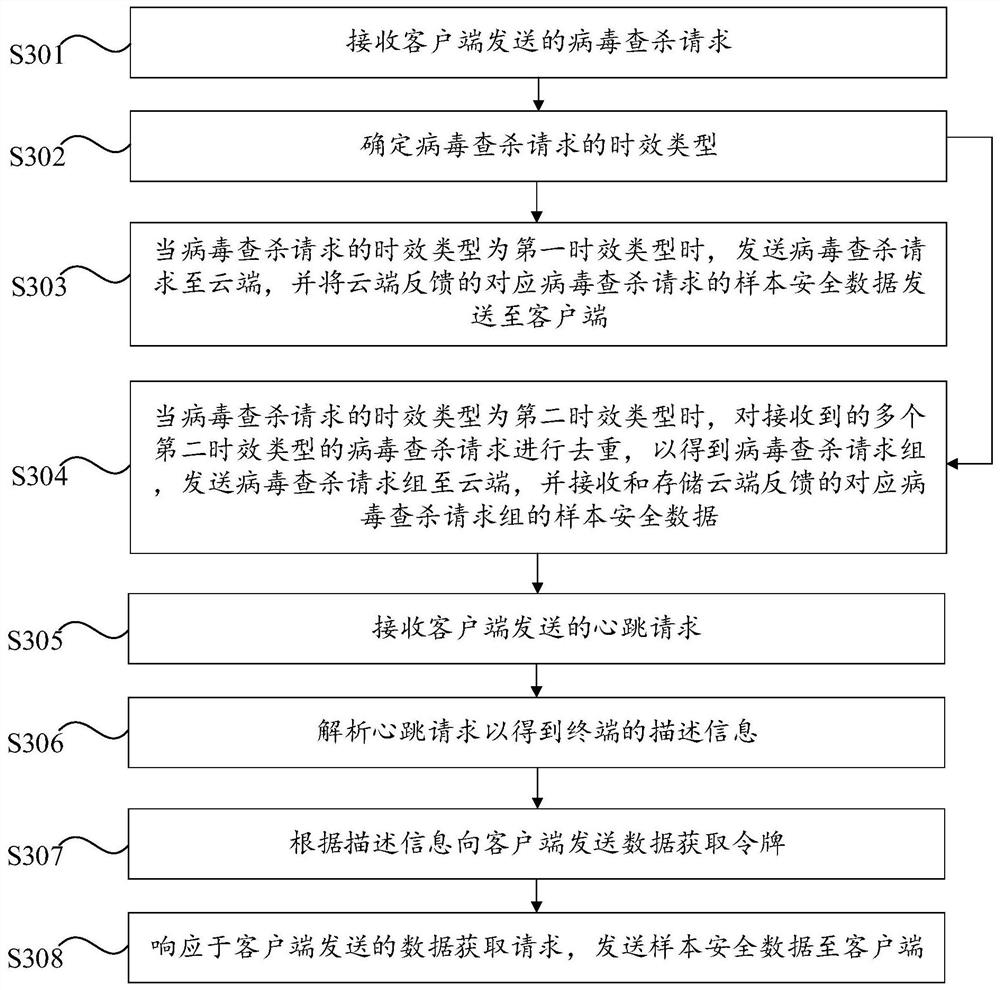
[0068] Embodiment 3 of the present invention provides a preferred semi-isolated network terminal virus scanning and killing method. Part of the features and corresponding technical effects are the same as those of Embodiment 1 above. Reference may be made to Embodiment 1 above, which will not be repeated here. In this embodiment, when the control center sends the sample security data corresponding to the virus scanning and killing request group to the terminal, it sends it based on the information of the terminal. On the one hand, compared with centrally delivering all sample security data to all clients, it can further reduce the pressure on the control center. specifically, image 3 The flow chart of the semi-isolated network terminal virus checking and killing method provided by Embodiment 3 of the present invention, such as image 3 As shown, the semi-isolated network terminal virus scanning and killing method provided by this embodiment includes the following steps S301 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com