Smart city-oriented blockchain identity authentication and access control method and system
An access control and identity authentication technology, applied in digital data authentication, digital data protection, etc., can solve problems such as single faults, and achieve the effect of reducing storage pressure, good supervision and standardization of user access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059]This embodiment proposes a block chain identity authentication and access control method for smart cities, and applies IPFS systems in the government work of smart cities. The implementation of the method includes the block chain identity authentication section and the block chain access control section.
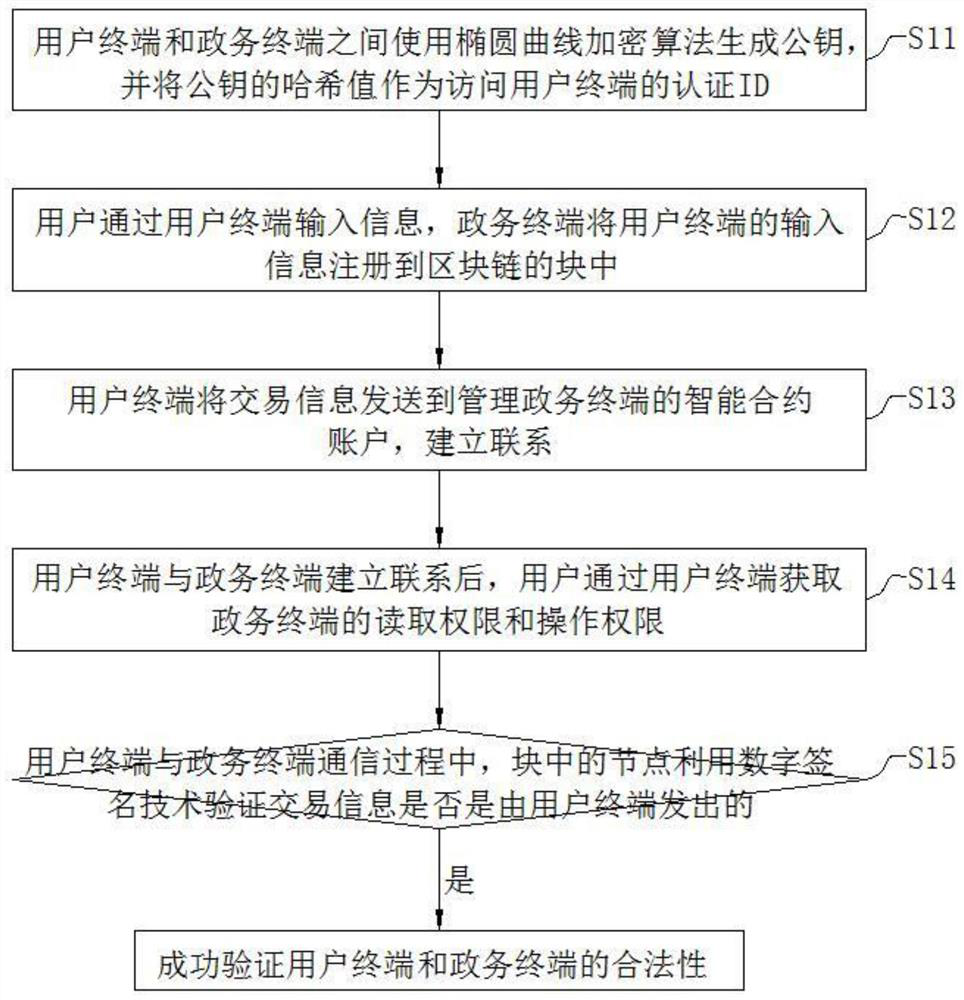
[0060](1) Combined withfigure 1 , In the block chain identity authentication section:
[0061]S11, the user terminal and the government terminal use the elliptic curve encryption algorithm to generate private key K, based on a given elliptic curve E and known base point g, the private key k and the base point G is a public key, and the public key is The value is an authentication ID that accesses the user terminal.
[0062]S12, the user enters information through the user terminal, and the government terminal registers the input information of the user terminal to the block of the block chain.
[0063]S13, the user terminal sends transaction information to the intelligent contract accou...
Embodiment 2
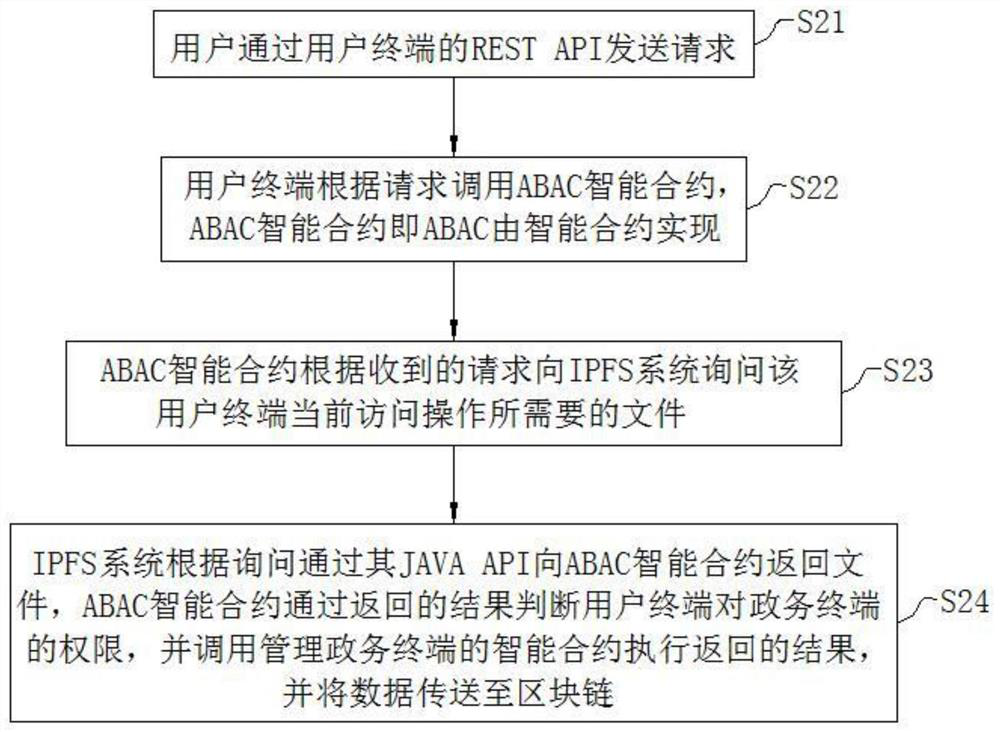
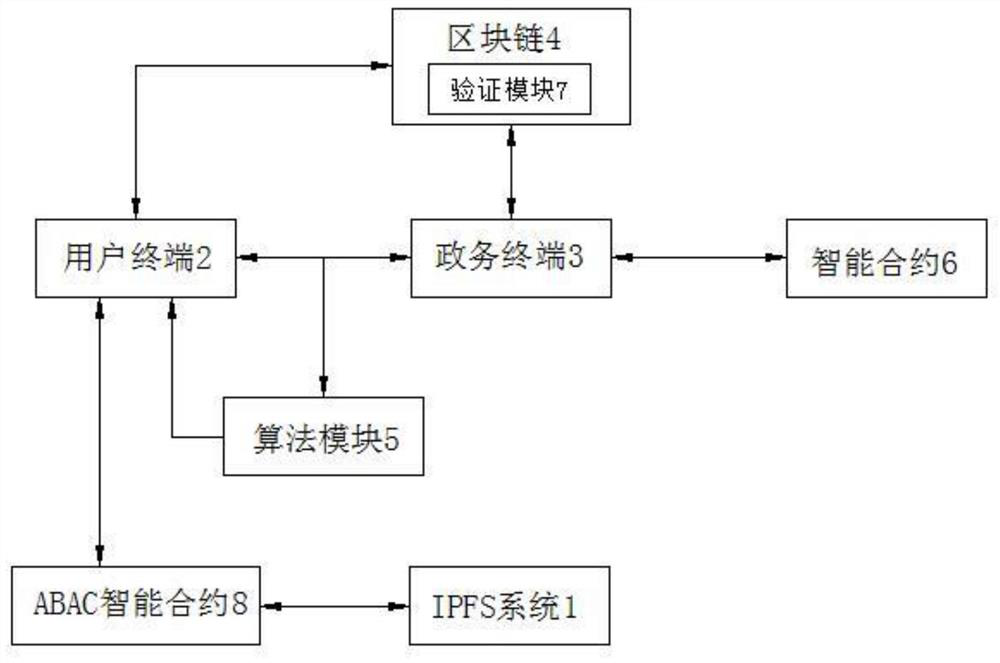
[0073]Joinimage 3This embodiment proposes a block chain identity authentication and access control system for smart cities, which involves the IPFS system, user terminal, government terminal, and multiple government terminals in smart urban government work. The block chain established by multiple government terminals. The system also relates to algorithm modules, intelligent contracts, verification modules, and ABAC intelligent contracts, where
[0074]The user terminal and the government terminal use the algorithm module to generate a public key, and the algorithm module uses the hash value of the public key as the authentication ID of the access user terminal.
[0075]Intelligent contracts are used to manage government terminals,
[0076]The verification module is deployed in the block chain, and the digital signature technology verifies whether the transaction information is issued by the user terminal.
[0077]ABAC intelligent contract, that is, ABAC is implemented by intelligent contract f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com