Key negotiation method and system
A technology of key negotiation and shared key, applied in transmission systems, digital transmission systems, public keys for secure communications, etc., can solve the problem that password authentication key exchange protocols cannot resist password guessing attacks, and achieve resistance to man-in-the-middle attacks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment
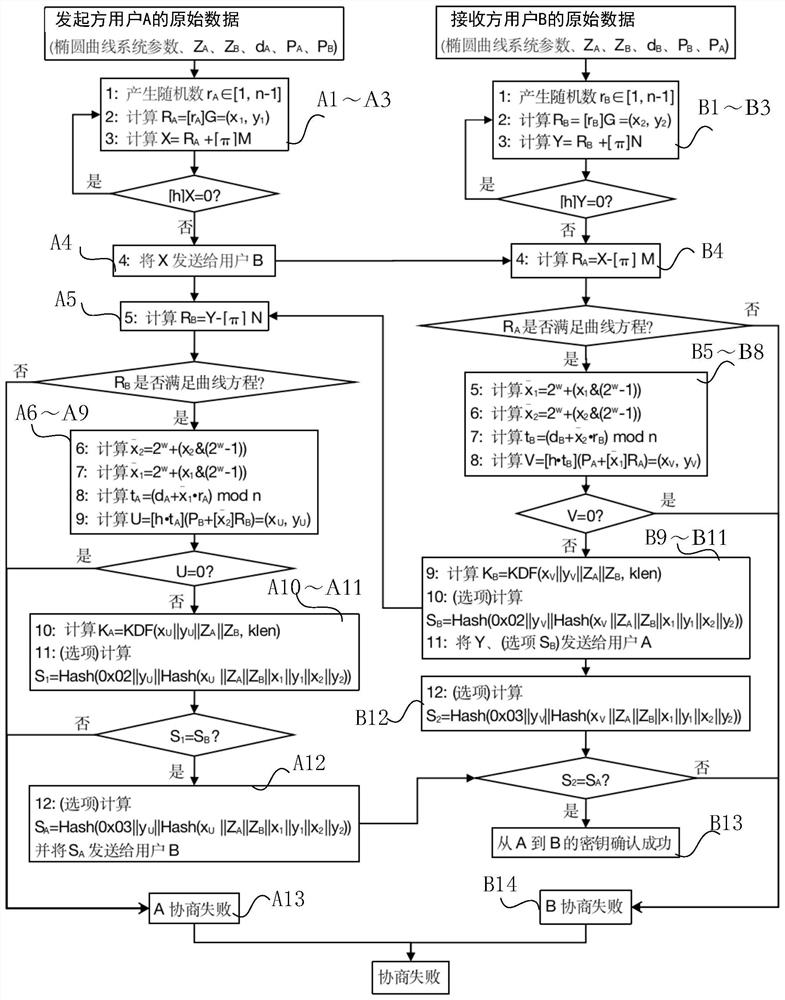
[0094] In the first embodiment, the elliptic curve parameters are system parameters of the SM2 elliptic curve public key cryptographic algorithm: wherein, G is the base point of the elliptic curve, its order is a prime number n, and h is a cofactor. In addition, the points M and N on the two elliptic curves are arbitrarily selected as public parameters. The Hash algorithm, KDF algorithm and the generating function F of the shared secret point are all consistent with the SM2 algorithm key exchange protocol.
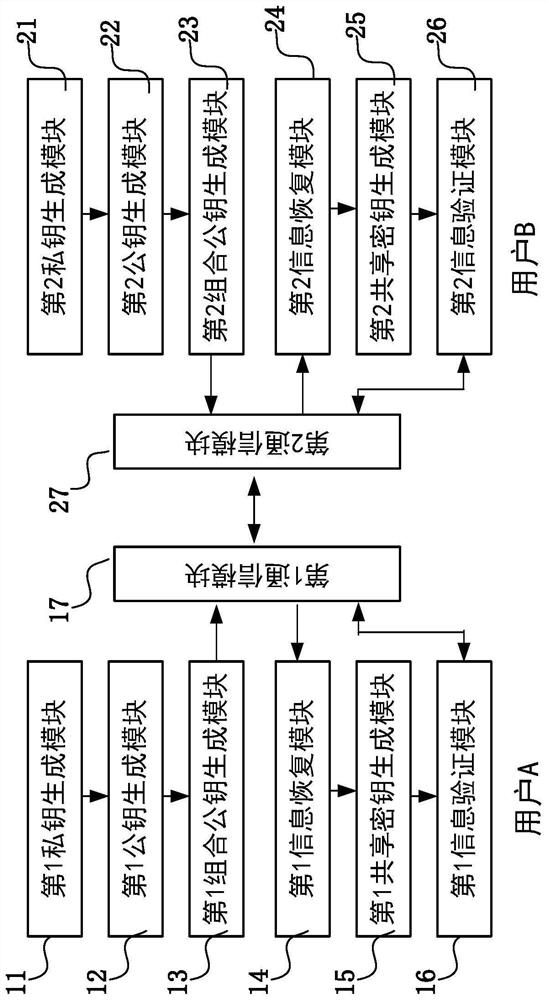
[0095] figure 1 It is a structural block diagram of the key agreement system in the first embodiment 1.
[0096] The communication party A is composed of the following modules: the first private key generation module 11, the first public key generation module 12, the first combined public key generation module 13, the first information recovery module 14, the first shared key generation module 15, the first 1 An information verification module 16 and a first communicatio...
no. 2 Embodiment
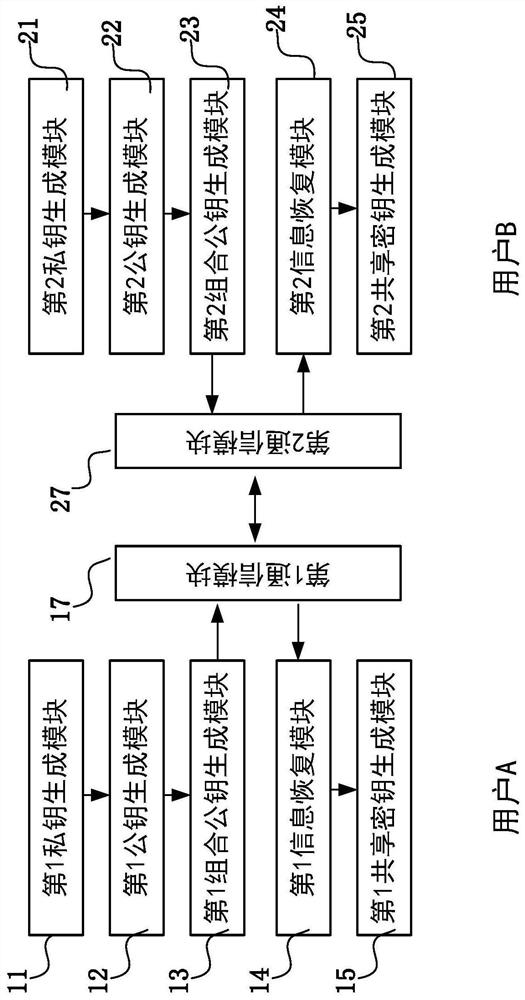
[0159] image 3 is a structural block diagram of the key agreement system of the second embodiment, Figure 4 It is a flowchart of the key exchange protocol in the second embodiment.
[0160] Compared with the first embodiment, the second embodiment omits the first information verification module and the second information verification module and the calculation S 1 , S 2 , S A , S B and verification steps, others are the same as those in the first embodiment. Compared with the first embodiment, the second embodiment can reduce the number of information transfers between the communicating parties A and B.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com