Internet-based company security network implementation system
A secure network and system implementation technology, applied in the field of secure network implementation, can solve problems such as unguaranteed information security, failure to discover system loopholes and insecure factors in time, and poor encryption and transmission of system information, so as to achieve protection security, The effect of convenient encrypted transmission and viewing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
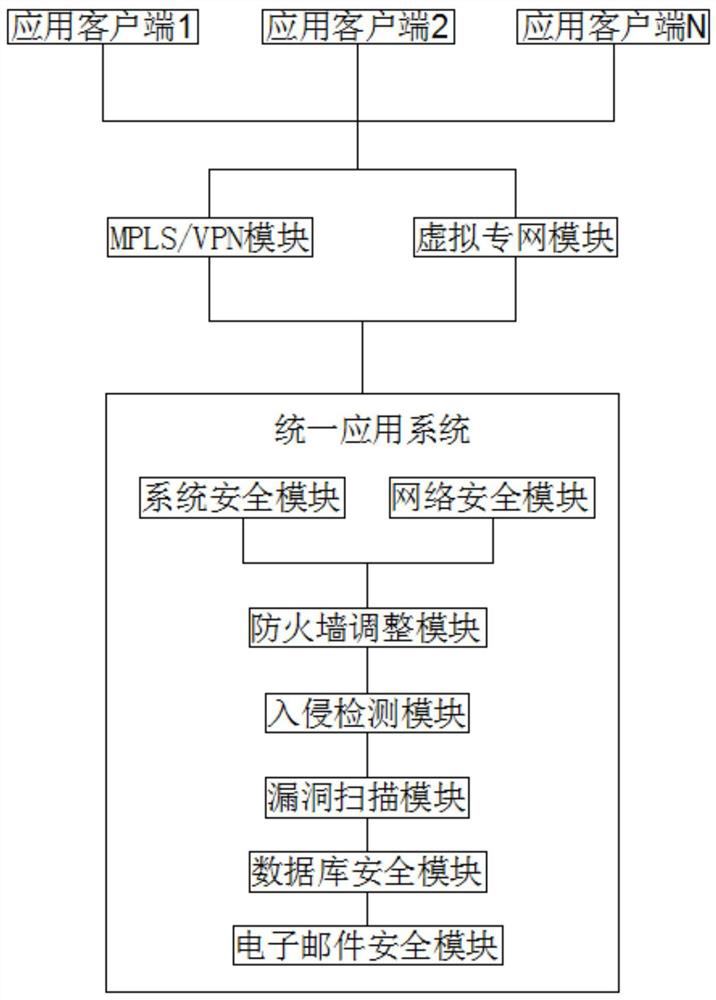
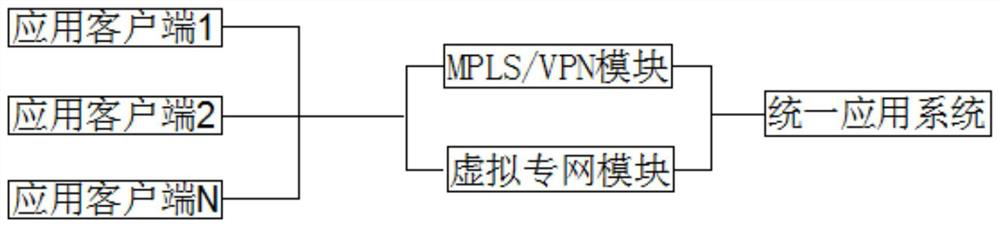
[0029] see figure 1 , 2 , 3, 4, an implementation system of an Internet-based company security network, including application client 1, application client 2, application client N, MPLS / VPN module, virtual private network module and unified application system, unified application system Including system security module, network security module, application client 1, application client 2, and application client N connected to MPLS / VPN module and virtual private network module through the network and connected in series in the system security module and network in the unified application system on the security module;
[0030] The MPLS / VPN module is used to realize the safe interconnection of multi-service systems. The company's unified planning of the MPLS / VPN network transformation is implemented, and the original WAN access method is transformed by using MPLS technology. The business system is divided into VPNs for security isolation and provides safe and effective informati...
Embodiment 2
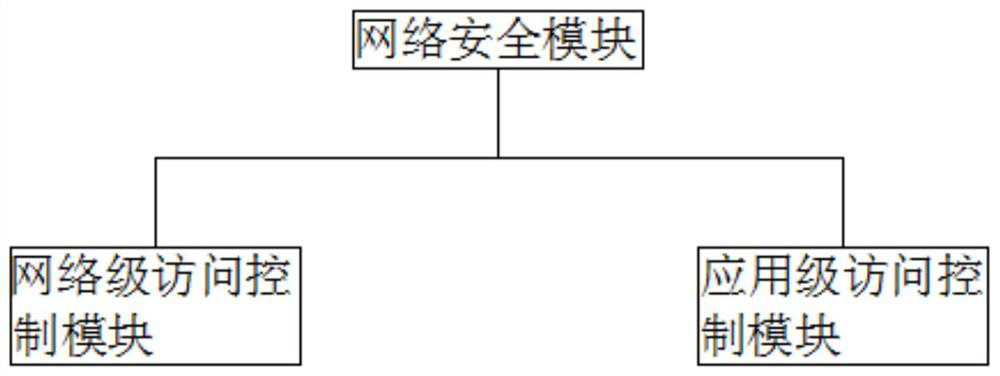
[0036] see figure 1 , an Internet-based implementation system for a company's security network, including a unified application system, the unified application system includes a firewall adjustment module, an intrusion detection module, a vulnerability scanning module, a database security module, and an e-mail security module, and the unified application system is connected through the network. System security module, network security module, firewall adjustment module, intrusion detection module, vulnerability scanning module, database security module and email security module;
[0037] The firewall adjustment module is a security protection measure for the network. It analyzes and monitors traffic, and adjusts the firewall deployment to block illegal data transmission. At the same time, it can independently place servers that provide external services and are relatively easy to attack in a specific protected area;
[0038] The intrusion detection module is a technology desig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com