LDoS attack detection and mitigation method based on ET-EDR in SDN
A technology of ET-EDR and attack detection, which is applied to electrical components, transmission systems, etc., and can solve problems such as lack of LDoS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings.
[0038] like image 3 As shown, the ET-EDR-based LDoS attack detection and mitigation method in this SDN mainly includes four steps: information collection, feature calculation, attack detection and attack mitigation.
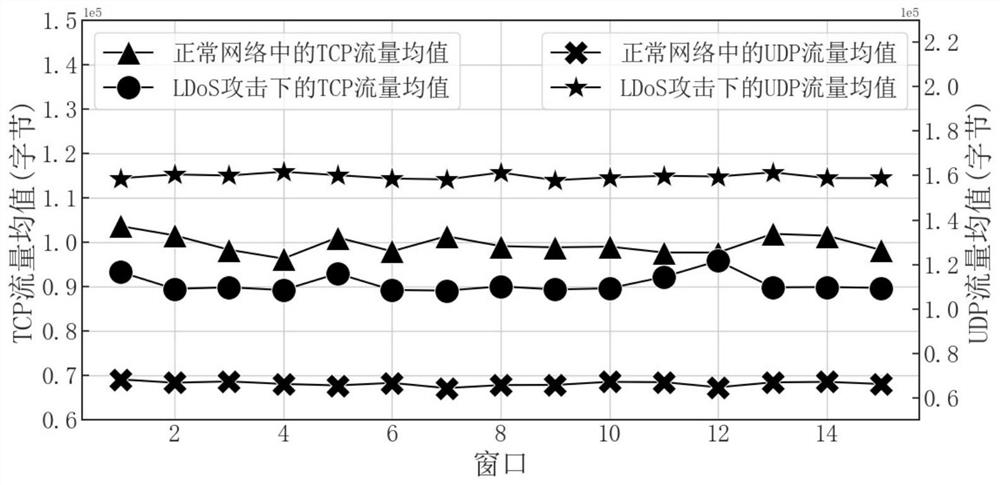
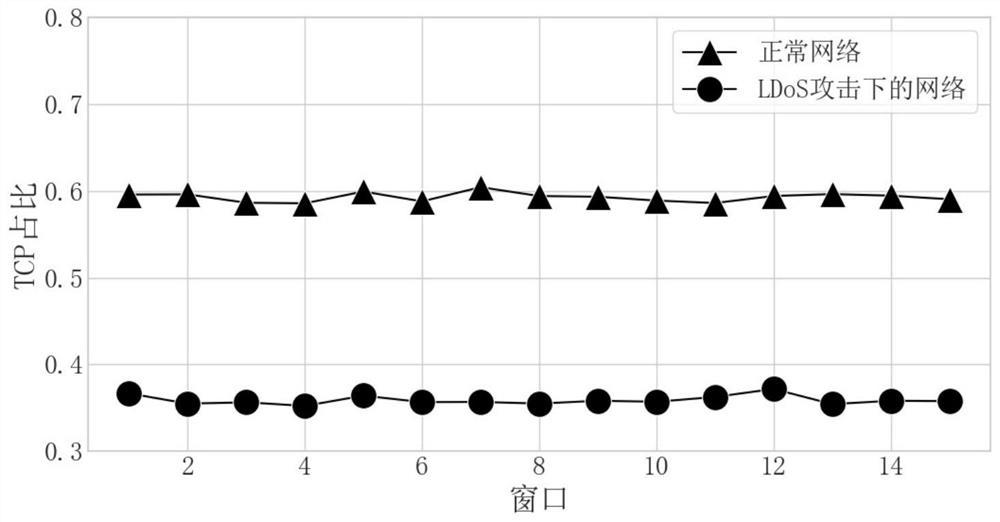
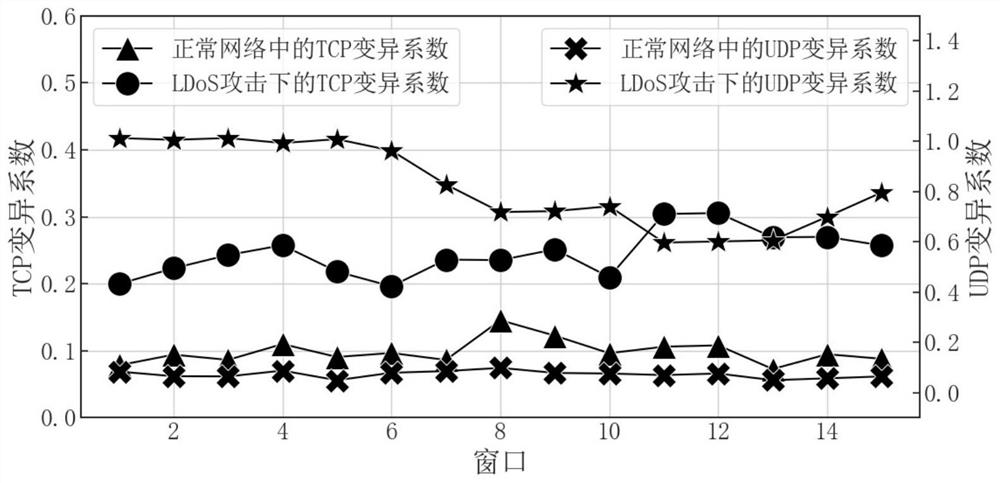
[0039] Figure 1 is a comparison diagram of network traffic characteristic values in two network states. Under normal network conditions: the average value of TCP traffic is high, accounting for most of the total traffic, and the coefficient of variation is low. At the same time, the Spearman rank correlation coefficient between TCP traffic and total traffic is high, close to 1; UDP traffic The mean is lower and the coefficient of variation is also lower. In the state of LDoS attack: the average value of TCP traffic is low, while TCP traffic occupies a small part of the total traffic, the coefficient of variation is higher than that under normal netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com