Thermal power plant safety measure execution closed-loop management method and system
A technology of safety measures and management methods, which is applied in the field of closed-loop management methods and systems for the implementation of safety measures in thermal power plants, can solve the problems of the two-ticket management system Internet processing business data and the inability to realize effective supervision at the technical level, so as to avoid misoperation and avoid Safety accidents and the effect of avoiding missing operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
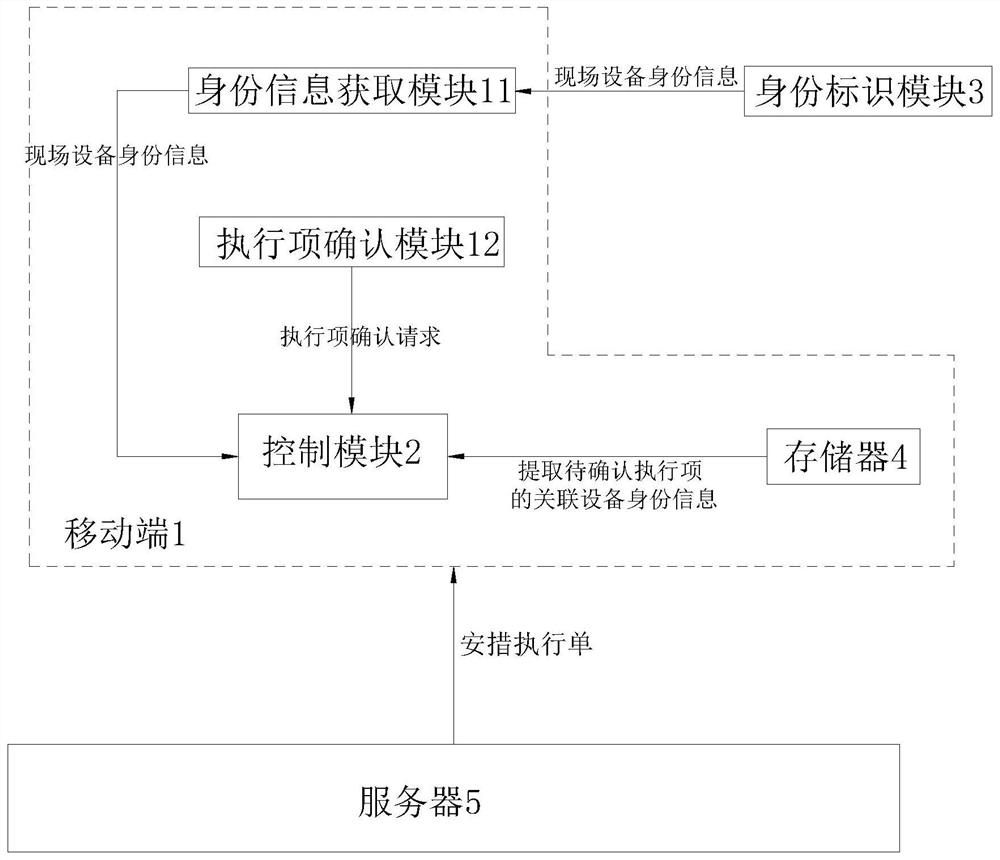
[0047] like figure 1 and figure 2 As shown, the system includes an identity identification module 3 , an identity information acquisition module 11 , an execution item confirmation module 12 , a memory 4 and a control module 2 .
[0048] Specifically, the identity identification module 3 is located at the corresponding field device, and is used for storing the identity information of the field device.
[0049]The identity identification module 3 in this embodiment is an identification code pasted on each field device, such as a two-dimensional code, a bar code, a three-dimensional code or a small program code. The identity information of the corresponding field device is stored in the identification code, and when the identification code is scanned, the scanning party can obtain the identity information of the corresponding field device. The identity information here refers to the code of the corresponding device. A device may need to implement multiple unrelated security m...
Embodiment 2
[0062] This embodiment is similar to Embodiment 1, except that the identity identification module 3 of this embodiment includes a wireless transmission module that stores identity information of corresponding field devices. Correspondingly, the identity information acquiring module 11 includes a wireless receiving module for receiving information sent by the wireless transmitting module, the wireless transmitting module is a Bluetooth beacon or an RFID chip, and the wireless receiving module is a Bluetooth receiving module or an RFID reading module. This solution replaces the identification code with a Bluetooth beacon or RFID chip. Compared with the first embodiment, the cost is higher, but this solution can also be realized, and the identification code solution of the preferred embodiment is preferred.
Embodiment 3
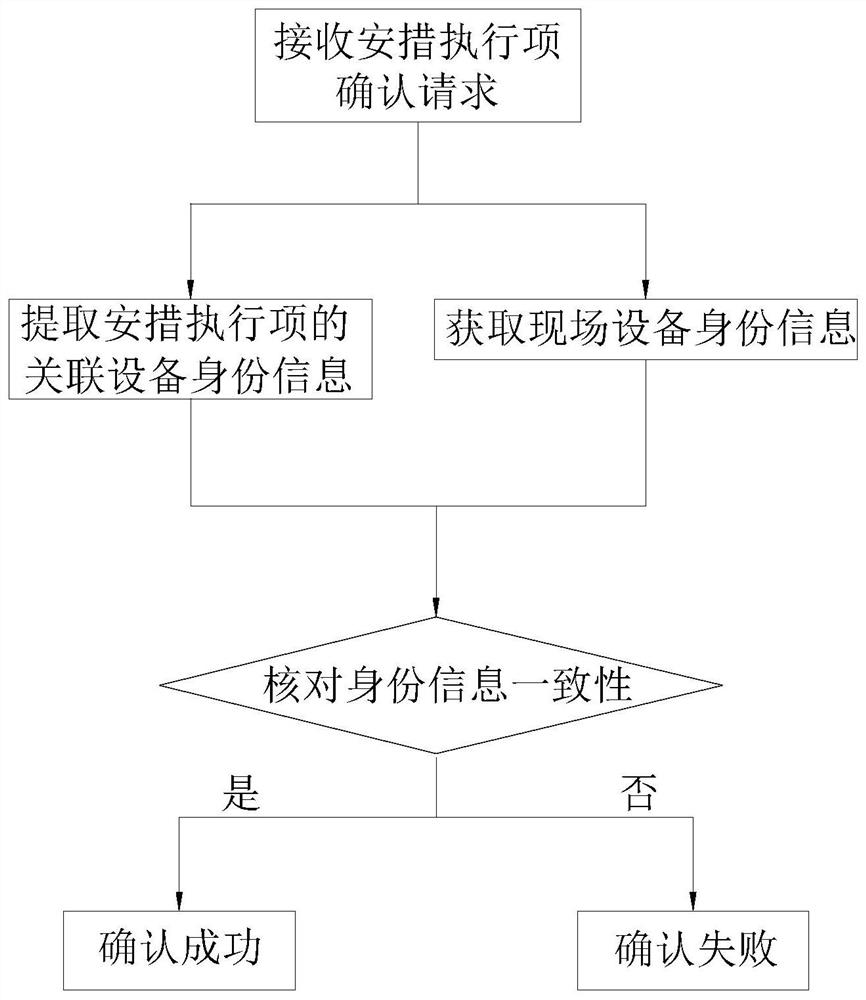
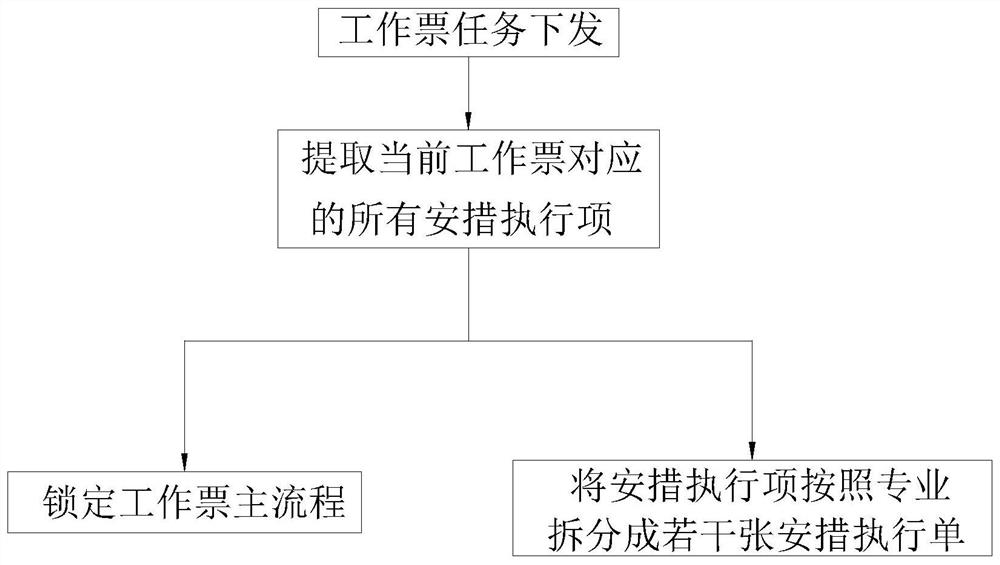
[0064] like Figure 5 As shown, this embodiment is similar to Embodiment 1, the difference is that the identity information acquisition module 11 and the execution item confirmation module 12 of this embodiment are located in the mobile terminal 1, and the memory 4 and the control module 2 are located in the server 5; The real-time identity information acquisition module 11 and the execution item confirmation module 12 are connected to the control module 2 at the server 5 through the processor of the mobile terminal 1 . The mobile terminal 1 of this solution is responsible for receiving the user's operation information on the touch screen, such as the click information on the security measure execution confirmation button, as well as the obtained field device identity information, and confirming the field device identity information and security measure execution items The information is sent to the server 5, and the server 5 checks the consistency between the associated devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com