Anonymous identity authentication and key agreement protocol in wsn
A technology of identity authentication and key agreement, applied in network topology, electrical components, security devices, etc., can solve problems such as difficult calculations and unsolvable polynomial time, and achieve the effect of low calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
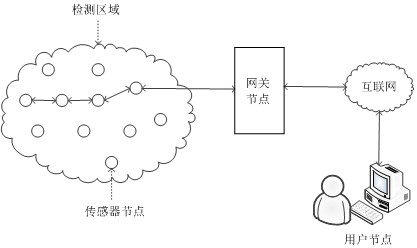
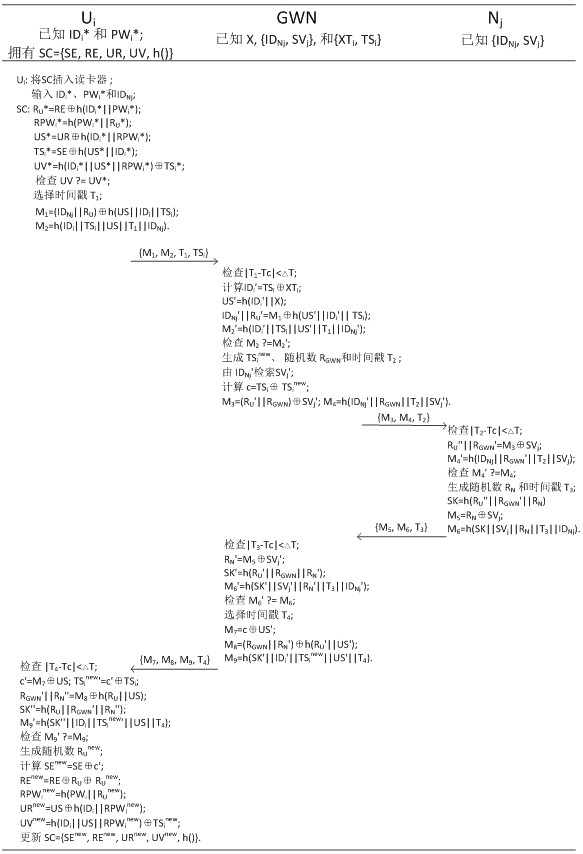
[0027] (1) Network initialization stage: Before the wireless sensor network is deployed to the monitoring area, the gateway GWN, sensor node N j and the smart card SC need to perform the following initialization operations, and the symbols and meanings in the protocol are shown in Table 1:
[0028]Table 1 Symbol description
[0029]
[0030] (1.1) The administrator is on the smart card SC, the gateway GWN and the sensor node N j One-way hash function, XOR operation function, connection operation function, random number generator and other basic operation functions are stored in the internal memory; the identity ID selected by the administrator for the smart card SC SC and a random number R SC , and put {ID SC , R SC} stored in the user authentication table UT of the gateway GWN (as shown in Table 2, the initial user identity information XT and serial number TS are empty) and the memory of the smart card SC to make it a legal smart card; The smart card SC is distributed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com