Linux ransomware virus prevention method and system
A virus and honeypot technology, applied in the field of Linux ransomware prevention and Linux ransomware prevention software, can solve the problems of undetectable ransomware, limited effect, and difficult acquisition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
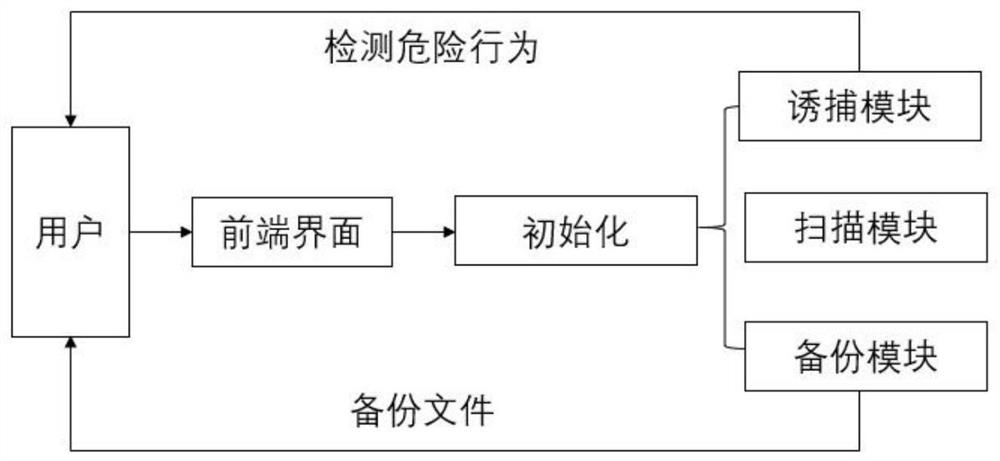
[0064] A kind of Linux ransomware virus prevention system provided according to the present invention comprises:
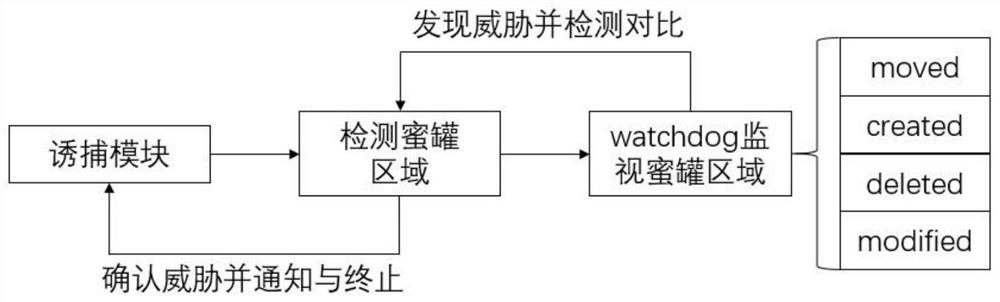
[0065] Trapping module: Use the trapping module to monitor the honeypot area file, and when it is found that there is a Linux ransomware virus or other non-virus processes that perform corresponding operations on the current honeypot area file, it will detect and compare the file characteristics of the current honeypot area file , to determine whether the current process is threatened, and when it is confirmed that the current process is threatened, the relevant process is terminated, and the alarm information is fed back to the front-end platform in time;
[0066] Specifically, it also includes a backup module: back up and protect the modified files in the area selected by the user (the area expected to be protected), and realize file recovery after being attacked by the Linux ransomware virus; the size of the area selected by the user can be expected by the user ...
Embodiment 2
[0117] Embodiment 2 is a modification of embodiment 1
[0118] The present invention mainly solves the problem that the current Linux operating system has no effective means of protection against ransomware, and at the same time seeks a method that can prevent unknown types of ransomware, and improves the current backup that requires manual operation or online backup in order to prevent ransomware Trouble.
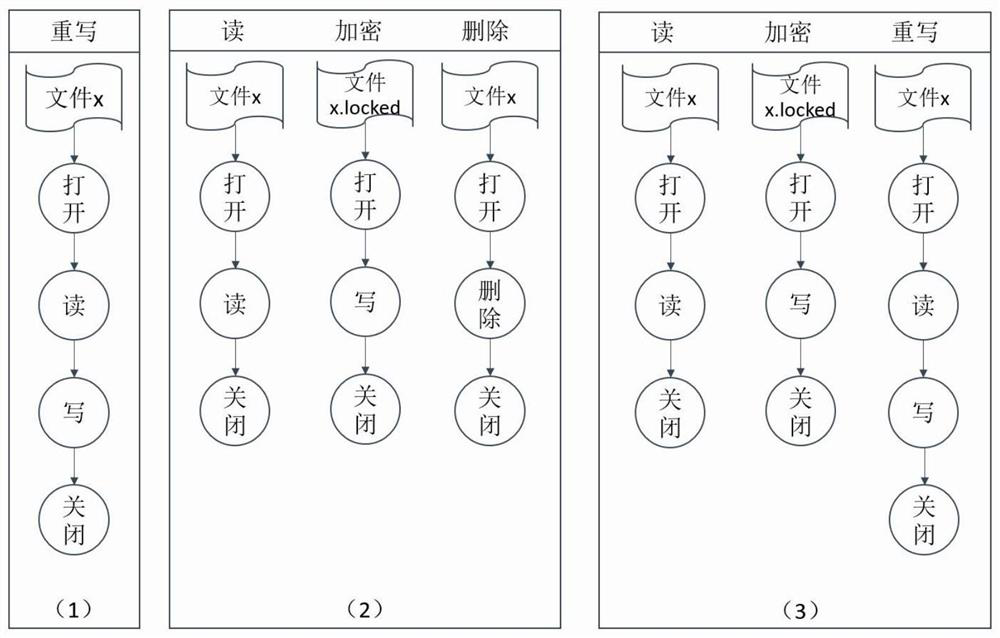
[0119] The present invention adopts setting honeypot file, and judges the change of its file information entropy to judge whether there is known or unknown ransomware;
[0120] Real-time backup is used to back up any files suspected of being encrypted by ransomware in real time, and save the contents of the files before modification or deletion for subsequent recovery.
[0121] After testing, the software realized by the invention can prevent any encrypted file-type malicious software, and can also back up and restore files before being encrypted.
[0122] The front-end ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com