Computer implemented system and method for distributing shares of digitally signed data
A computer, share technology, applied in the field of secret sharing, that can solve problems that do not scale well, have no sorting or organization, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
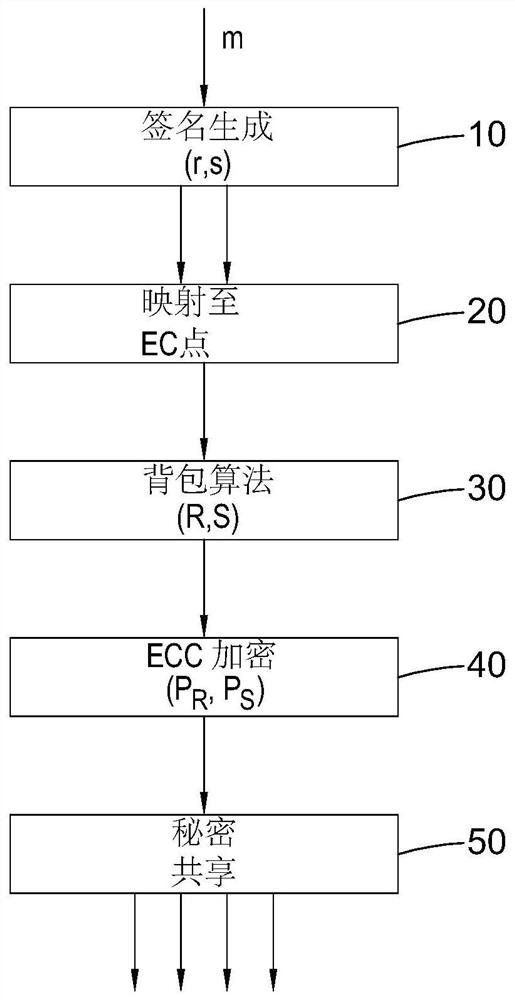
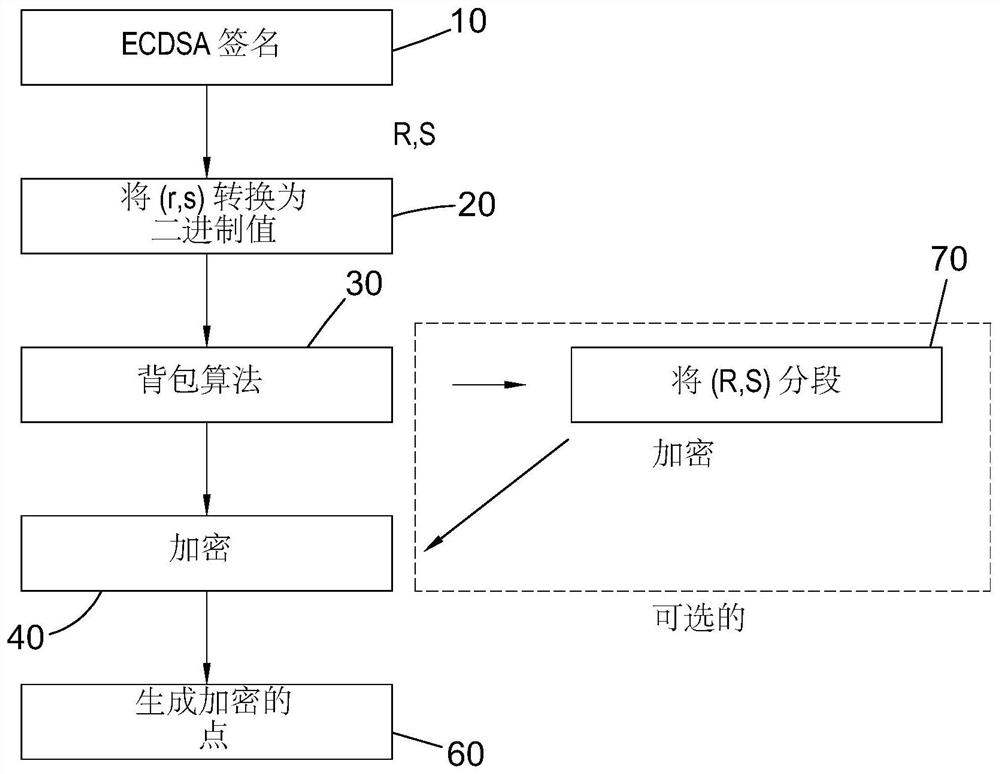
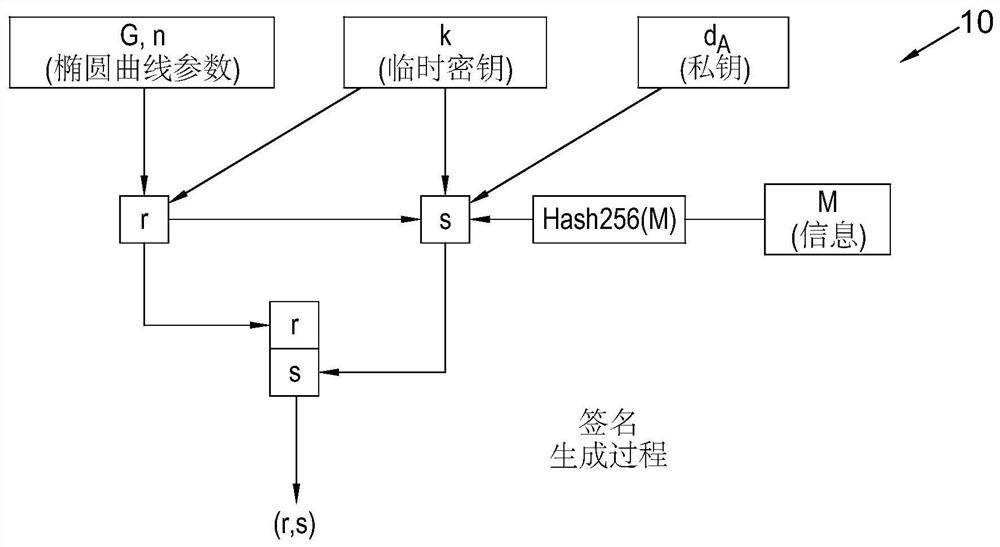
[0058] refer to figure 1 , which describes the process of distributing shares of a digitally signed message among multiple participants. Initially, digital information m (where m is the hash of information M such as a blockchain transaction) is input to the Elliptic Curve Digital Signature Algorithm (ECDSA) in step 10 . Those skilled in the art will appreciate that ECDSA generates public and private key pairs and ephemeral keys as random integers and provides digital signatures (r, s) in a manner described in more detail below. In a mapping step 20, the digital signature (r, s) is mapped to elliptic curve points of the elliptic curve cryptosystem shared by the participants. Then, a first encryption step 30 in the form of the knapsack algorithm is applied to the elliptic curve points generated in step 20 to generate an encrypted version (R,S) of the digital signature (r,s); using elliptic curve cryptography ( A second encryption step 40 in the form of ECC) encryption is appli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com