Protection method and system for preventing stack overflow attack
A stack overflow and system protection technology, applied in platform integrity maintenance, program control design, instruments, etc., can solve problems such as high consumption, segmentation fault, and large amount of computation, and achieve the effect of preventing overflow attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
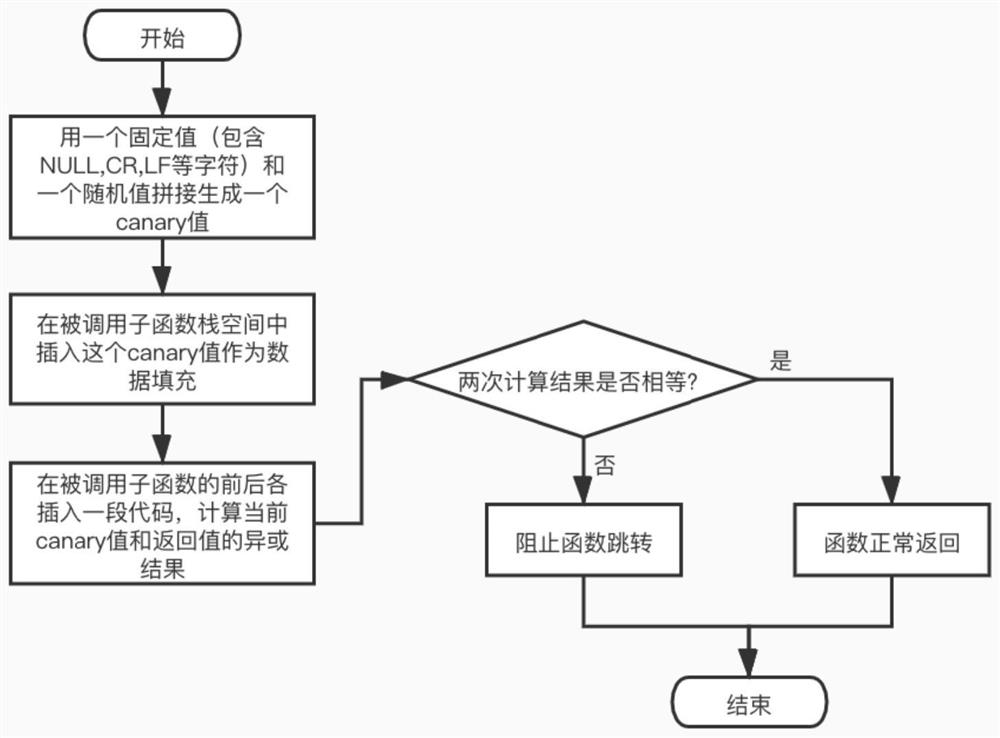
[0060] In order to overcome the defects in the existing technical solutions, the present invention provides a protection method for preventing stack overflow attacks, combining the advantages of the three canary value generation methods, and solving the problem of attackers bypassing the canaryword to modify the return value under the condition of reducing the amount of calculation The problem. This enhances stack protection.
[0061] In order to solve the problem that the attacker bypasses the canary word and directly modifies the return value, a protection method against stack overflow attacks is proposed. The main idea of this method is: combining the advantages of the three canary value generation methods in the prior art, the canary word is generated by concatenating fixed values including NULL, CR, LF and other characters plus random values, and at the same time, before and after the function that needs to be protected Add a piece of code each. The code at the begin...
Embodiment 2
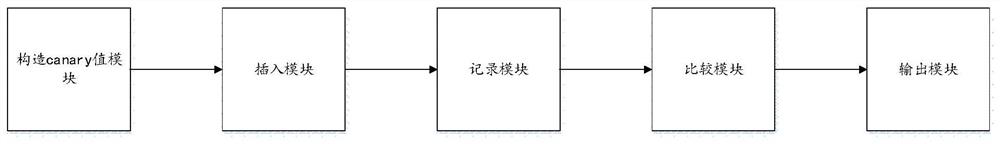
[0070] Please refer to image 3 , image 3 It is a schematic structural diagram of the protection system for preventing stack overflow attacks of the present invention. Such as image 3 Shown is a protection system for preventing stack overflow attacks of the present invention, including:
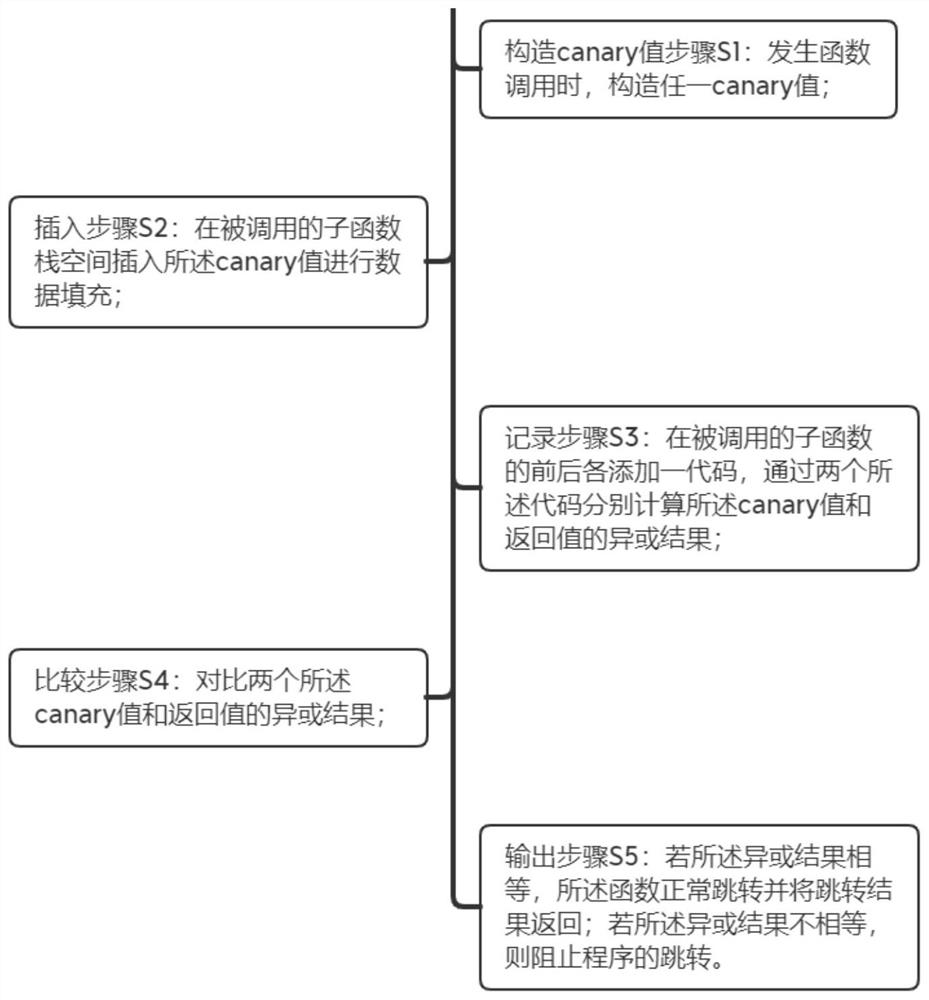
[0071] Constructing a canary value module, the constructing canary value module constructs any canary value when a function call occurs;
[0072] Inserting a module, the inserting module inserts the canary value into the called sub-function stack space for data filling;
[0073] A recording module, the recording module adds a code before and after the called sub-function, respectively calculates the XOR result of the canary value and the return value by two described codes;
[0074] A comparison module, the comparison module compares the XOR results of the two canary values and the return value;
[0075] In the output module, if the XOR results are equal, the function jumps normally ...
Embodiment 3
[0081] combine Figure 4 As shown, this embodiment discloses a specific implementation manner of a computer device. The computer device may comprise a processor 81 and a memory 82 storing computer program instructions.
[0082] Specifically, the processor 81 may include a central processing unit (CPU), or an Application Specific Integrated Circuit (ASIC for short), or may be configured to implement one or more integrated circuits in the embodiments of the present application.
[0083]Among them, the memory 82 may include mass storage for data or instructions. For example without limitation, the memory 82 may include a hard disk drive (Hard Disk Drive, referred to as HDD), a floppy disk drive, a solid state drive (SolidState Drive, referred to as SSD), flash memory, optical disk, magneto-optical disk, magnetic tape or universal serial bus (Universal Serial Bus, referred to as USB) drive or a combination of two or more of the above. Storage 82 may comprise removable or non-re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com