Online fountain code limited feedback method
A fountain code and feedback point technology, which is applied in the limited feedback field of online fountain codes, can solve the problems of inaccurate overhead calculation and low utilization rate of feedback points, and achieve the effect of flexible adaptation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
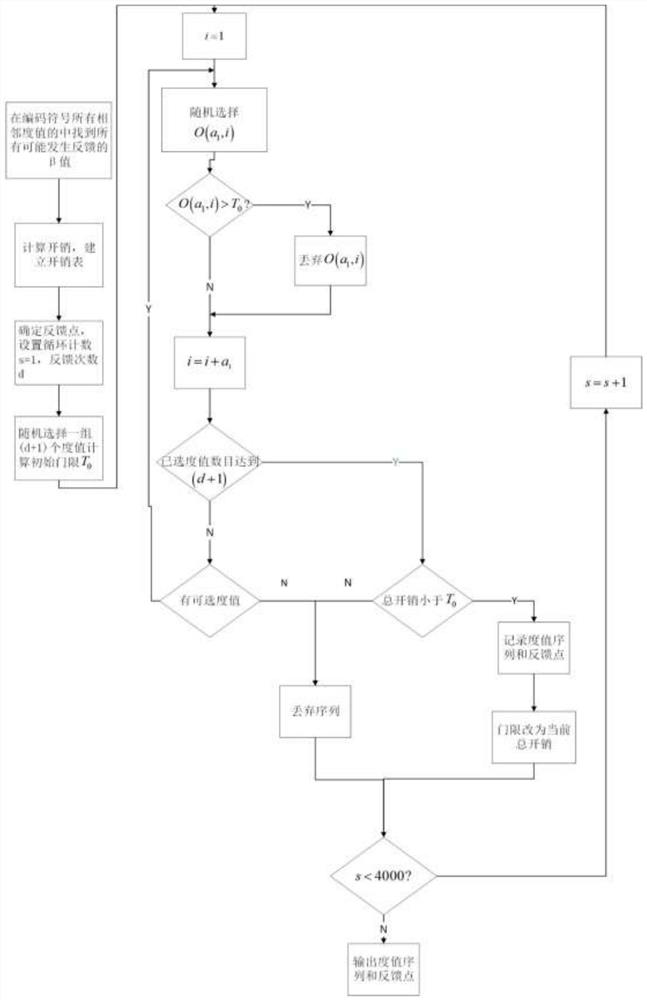
[0037] Suppose there are two satellites A and B, each carrying a mobile terminal T A and T B . Now T A Need to confirm T B Whether it is within the communication distance, that is, T A to T B Send a message of length K=10, T B After receiving the TA to reply. Considering the space communication scenario, the online fountain code with strong anti-interference ability is used as the channel coding method between satellites. And because of T B The state is unknown, considering T B to T A In cases where the uplink may be severely blocked, an online fountain code with limited feedback is used.
[0038] During specific implementation, in step 1, the encoding symbol degree is m i When , the sum of the probabilities of "contains only 1 unrecovered coding symbol" and "contains only 2 unrecovered coding symbols" is:
[0039]
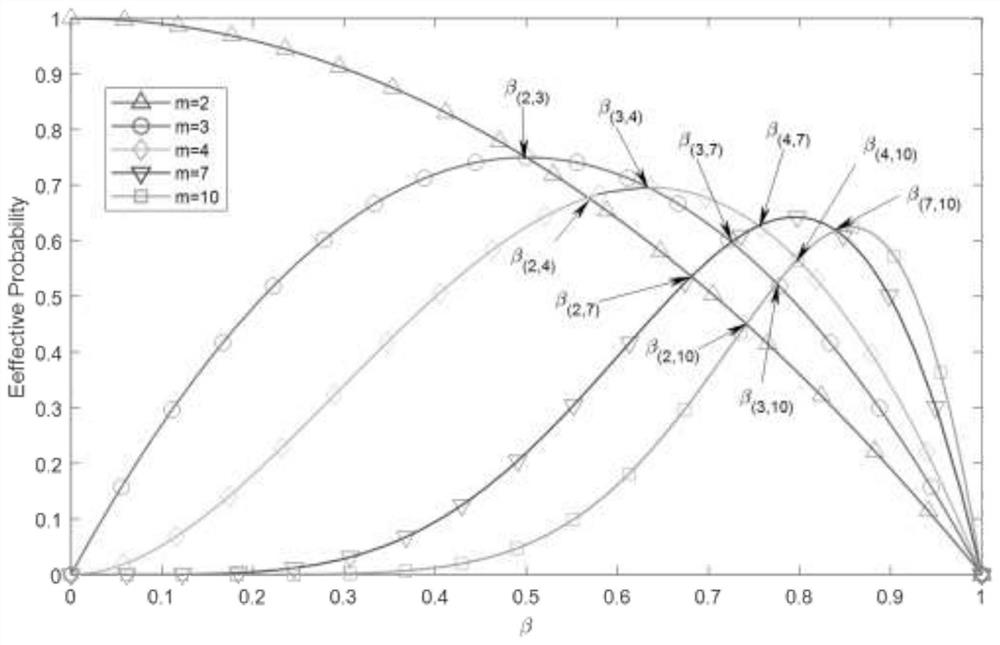
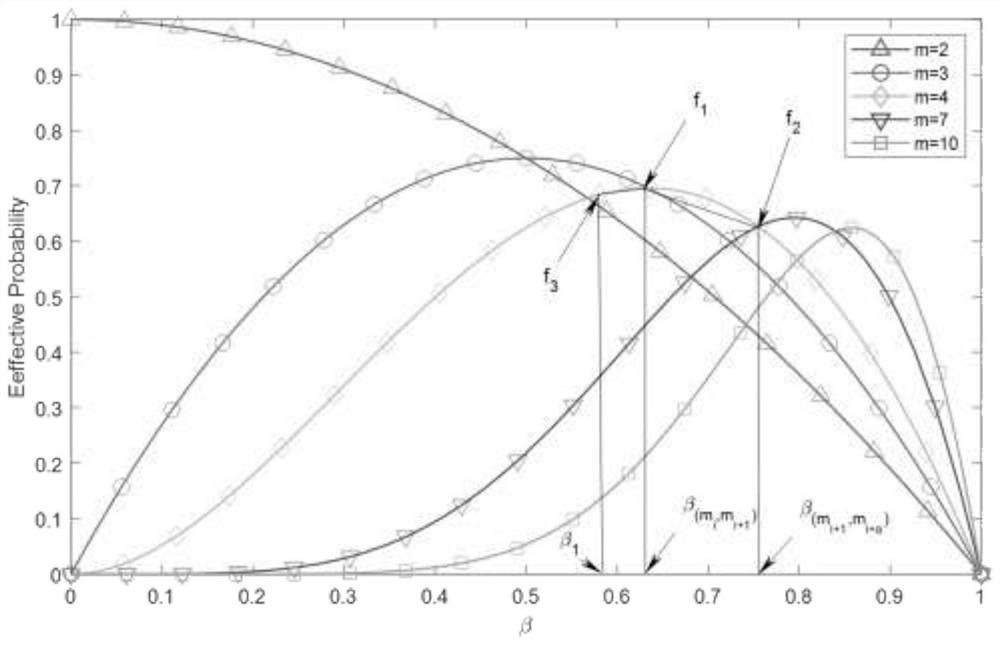
[0040] Defined as the effective probability;
[0041] Points at which all contiguity values are valid with equal probability Find all possible...
Embodiment 2
[0077] Assume that there are master A and slave B in the UAV group, each carrying terminal T A and T B . Now A needs to send an attack command to B, that is, T A to T B Send a piece of information with length K=1000. Due to the complex electromagnetic environment of the battlefield, the online fountain code with strong anti-interference ability is used as the channel coding method. Considering that the computing power of the slave machine is relatively limited, and the decoding process cannot occupy too much computing power for combat, an online fountain code with limited feedback is adopted.
[0078] Let K=1000, d=2, β 0 = 0.45. In step 1, since K=1000, there is no β>β at the end of the establishment phase 0 problem, so for β 0 = 0.45 using m 1 =2 as the first degree value. Other steps are similar to Embodiment 1 and will not be repeated here. Finally, using IO-FSS-HTLO, the average overhead is 1277. Much closer to the Online Fountain Code result 1200 than the HTL...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com