Network request log chained tracking method, full-link call monitoring system and medium
A network request and monitoring system technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as analysis, benchmark data support, segmented performance, etc., to achieve efficient dumping, performance improvement, and work. The effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
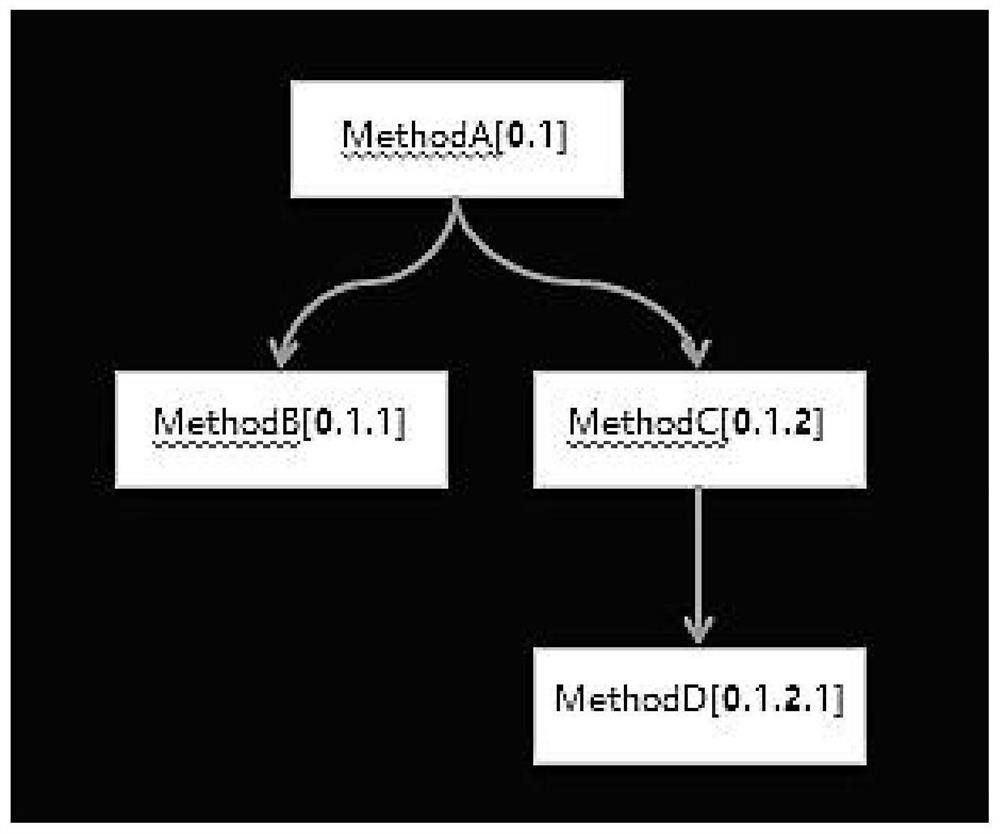
[0046] A network request log chain tracking method, comprising
[0047] Dot and mark call chain units to form tree nodes;
[0048] Through the data information collected by the call chain unit, the tree nodes of the upper-lower call relationship on the call track of the call chain unit are constructed into a tracking tree;
[0049] When a problem occurs at a certain node in the tracking tree, the information corresponding to the calling chain unit is provided.
[0050] The "dot marking" adopts interceptors or embedding points at the frame level.
[0051] The implantation is done by marking each call inside and outside the application (RPC level, after we use the interceptor based on the AOP mechanism, we don’t even need to change to the existing PRC framework) The current call chain unit.
Embodiment 2
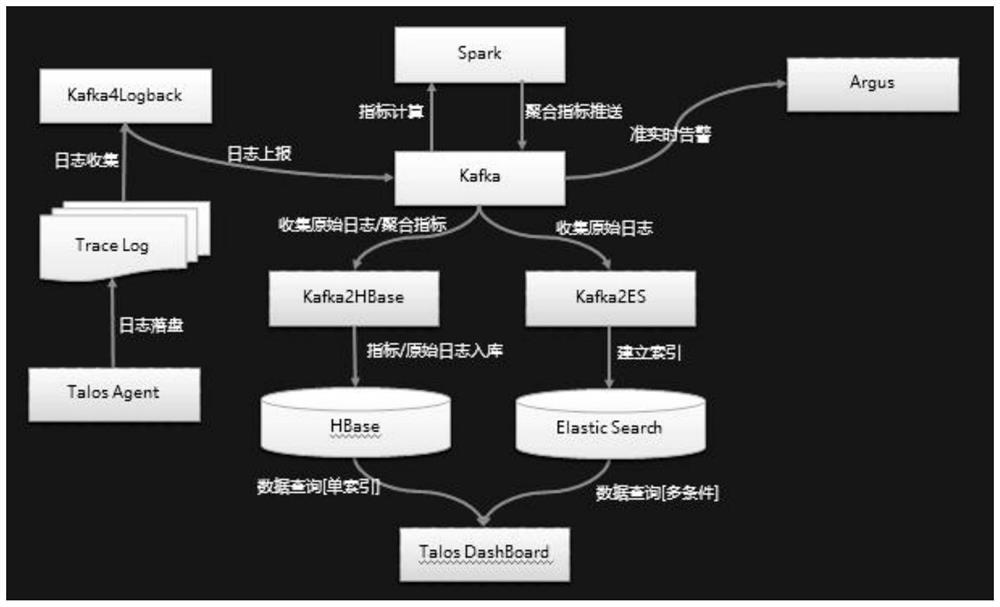
[0053] refer to figure 1 and figure 2 , a full link call monitoring system, including
[0054] The data collection client uses the method described in the first embodiment of the claim to mark the call relationship of the log of the application component, provides the call chain data collection service, and lands the track data to the local file system;
[0055] The data transmission end receives, normalizes, and stores the trajectory data into the database and retrieval server; and
[0056] The display terminal provides call chain retrieval, call chain display and storage service monitoring functions.
[0057] in
[0058] The data collection client (TalosAgent) is based on AOP technology, and the host application only needs simple configuration and annotation to complete the data collection and management work, and the learning cost and implementation cost are extremely low;
[0059] The trajectory data is finally landed to the local file system based on Logback (open sour...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com