Risk model training method and device, computer equipment and readable storage medium
A training method and risk model technology, applied in computer parts, calculation, character and pattern recognition, etc., can solve problems such as poor accuracy, illegal user utilization, and strict risk rule formulation, to avoid hysteresis and risk identification. Efficient and accurate results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
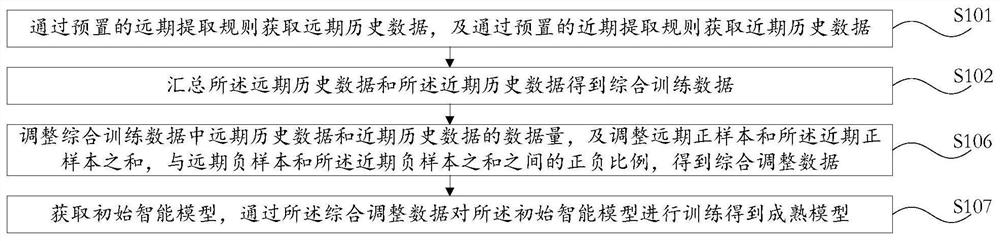
[0058] see figure 1 , a risk model training method of this embodiment, comprising:
[0059] S101: Obtain long-term historical data through preset long-term extraction rules, and obtain recent historical data through preset recent extraction rules.
[0060] S102: Summarize the long-term historical data and the recent historical data to obtain comprehensive training data.
[0061] S106: Adjust the data volume of the long-term historical data and the recent historical data in the comprehensive training data, and adjust the sum of the long-term positive samples and the recent positive samples in the comprehensive training data, and the long-term negative samples in the comprehensive training data. The positive and negative ratio between the sample and the sum of recent negative samples to obtain comprehensive adjusted data.
[0062] S107: Obtain an initial intelligent model, and train the initial intelligent model through the comprehensive adjustment data to obtain a mature mode...
Embodiment 2
[0071] This embodiment is a specific application scenario of the first embodiment above. Through this embodiment, the method provided by the present invention can be described more clearly and specifically.
[0072] Next, in the server running the risky model training method, the comprehensive adjustment data is obtained by obtaining the long-term historical data and the recent historical data and adjusting them, and then the mature model is obtained by training the initial intelligent model through the comprehensive adjustment data. An example is used to describe the method provided in this embodiment in detail. It should be noted that this embodiment is only exemplary, and does not limit the protection scope of the embodiment of the present invention.
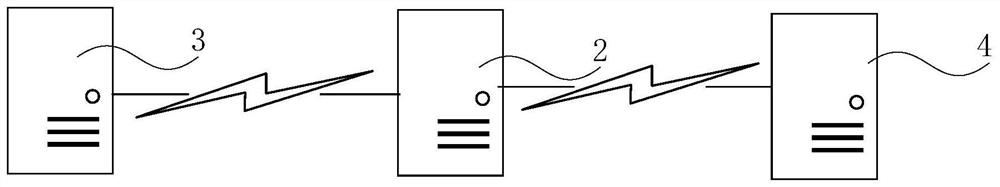
[0073] figure 2 A schematic diagram of an environment application of the risk model training method according to Embodiment 2 of the present application is schematically shown.
[0074] In an exemplary embodiment, the serv...
Embodiment 3
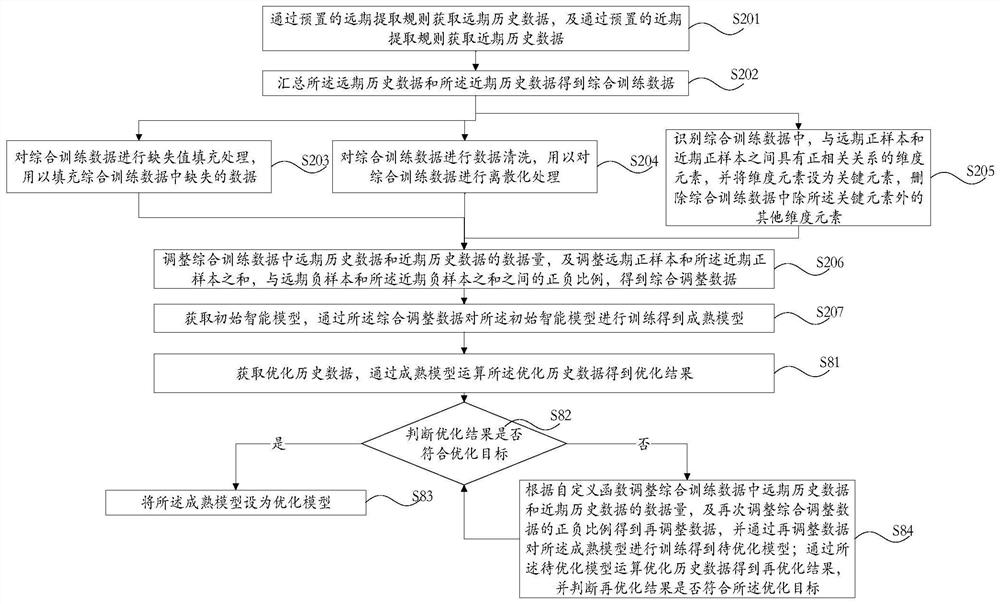
[0252] see Figure 4 , a risk model training device 1 of this embodiment, comprising:
[0253] The data extraction module 11 is used to obtain long-term historical data through preset long-term extraction rules, and obtain recent historical data through preset recent extraction rules;
[0254] Data summary module 12, is used for collecting described long-term historical data and described short-term historical data to obtain comprehensive training data;
[0255]The data adjustment module 16 is used to adjust the data volume of the long-term historical data and the recent historical data in the comprehensive training data, and adjust the sum of the long-term positive samples and the recent positive samples in the comprehensive training data, which is consistent with the comprehensive training data. The positive and negative ratio between the sum of the long-term negative samples and the recent negative samples in the data, to obtain the comprehensive adjusted data;
[0256] T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com