Communication method and device
A communication method and user equipment technology, applied in wireless communication, network data management, security devices, etc., can solve problems such as inability to meet the data security requirements of users and businesses, and achieve the effect of reducing signaling interaction and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0232] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
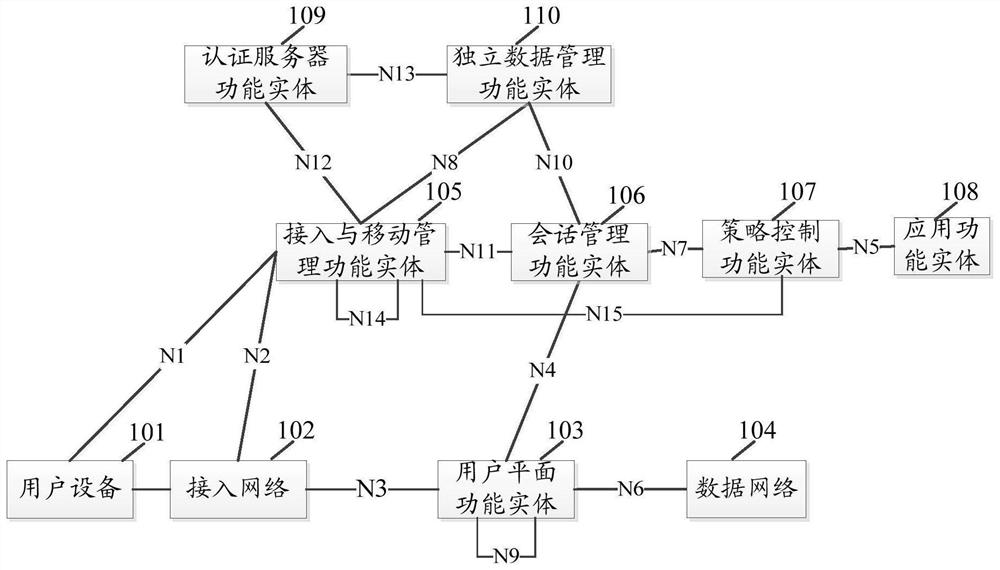
[0233] see figure 1 , figure 1 It is a schematic diagram of a network architecture. A communication method provided by an embodiment of the present invention is implemented based on the network architecture.
[0234] Such as figure 1 As shown, the network architecture includes: user equipment (User Equipment, UE) 101, access network (AccessNetwork, AN) 102, user plane function (User Plane Function, UPF) entity 103, data network (Datanetwork, DN) 104, Access and mobility management function (Access Mobility Management Function, AMF) entity 105, session management function (Session Management Function, SMF) entity 106, policy control function (Policy Control Function, PCF) entity 107, application function (Application Function, AF ) entity 108 , an Authentication Server Func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com