Method and system for preventing sensitive data leakage of database
A sensitive data and database technology, applied in the field of anti-database sensitive data leakage, can solve sensitive data leakage and other problems, achieve the effect of improving the effect, avoiding sensitive data leakage, and improving the security of data access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
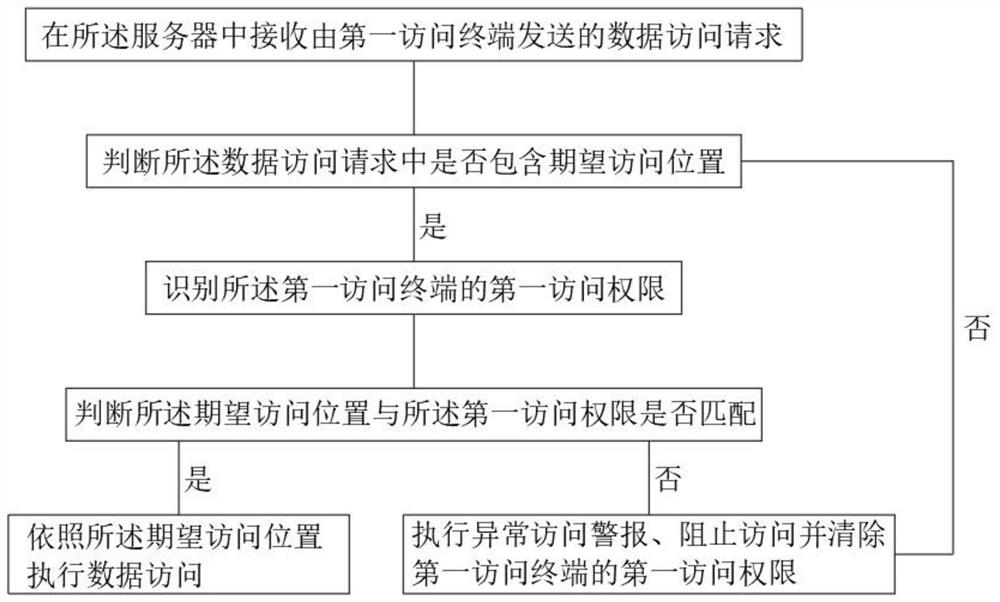
[0051] see figure 1 As shown, an embodiment of the present invention provides a method for preventing database sensitive data leakage, and the method includes the following steps:
[0052] S1. Receive a data access request sent by the first access terminal in the server;
[0053] S2. Determine whether the desired access location is included in the data access request; yes, proceed to step S3; no, proceed to step S4; specifically, the desired access location is the sub-library that the first access terminal expects to access;
[0054] S3. Identify the first access authority of the first access terminal; specifically, the first access authority is the sub-library that the first access terminal can access under the current restricted authority;
[0055] S4. Determine whether the desired access location matches the first access authority; if yes, proceed to step S5; if no, proceed to step S6;
[0056] S5. Execute data access according to the desired access location;
[0057] S6...
Embodiment 2
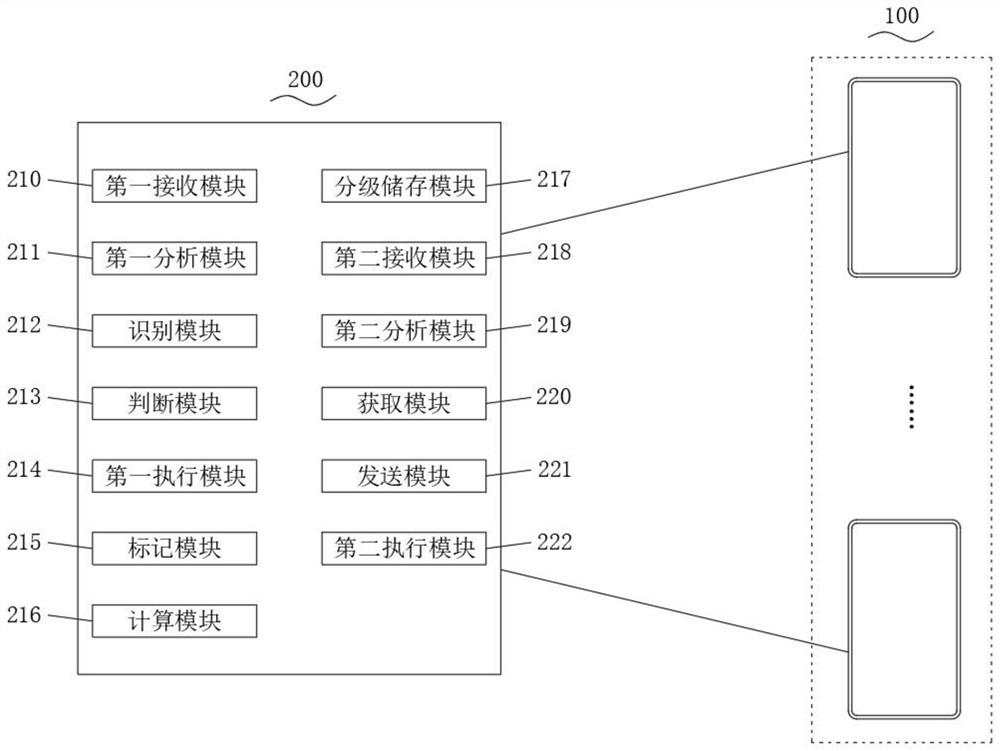
[0071] see figure 2 As shown, an embodiment of the present invention provides a system for preventing database sensitive data leakage, and the system includes:
[0072] The first receiving module 210; set in the server 200, and used for receiving the data access request sent by the first access terminal 100;
[0073] The first analysis module 211 is set in the server 200, and is used to analyze and obtain the expected access location of the first access terminal 100 from the data access request received by the first receiving module 210;
[0074] Identification module 212; set in the server 200, and used to identify the first access authority of the first access terminal 100;
[0075] Judging module 213; set in the server 200, and used to judge whether the desired access location matches the first access right;
[0076] The first execution module 214; is set in the server 200, and is used for performing alarm or access according to the analysis result of the first analysis ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com