Data processing method and device and computer readable storage medium
A data processing and data technology, applied in the field of data processing, can solve the problems of data leakage, affecting data storage, poor data distribution processing security, etc., to achieve the effect of improving security and preventing data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
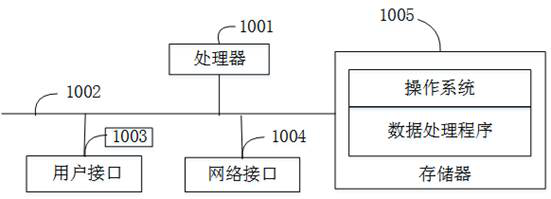
Image
Examples
no. 1 example
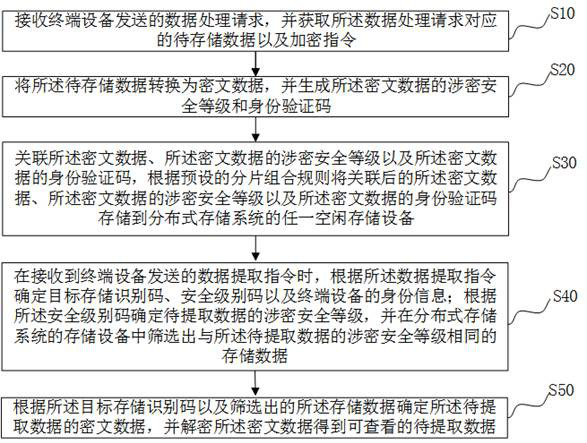
[0103] refer to image 3 , image 3 It is a schematic flow chart of the second embodiment of the data processing method of the present invention. Based on the first embodiment, the steps of S40 above include:
[0104] Step S41, upon receiving the data extraction instruction sent by the terminal device, parsing the data extraction instruction to obtain the data access information in the data extraction instruction;
[0105] Step S42: Obtain the security level code of the data access information, the target storage identification code, and the identity information of the terminal device; determine the secret-related security level of the data to be extracted according to the security level code, and store it in the storage device of the distributed storage system Filter out the stored data with the same confidentiality security level as the data to be extracted.
[0106] In this example, refer to Figure 6 After the data processing device 02 receives the data extraction instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com