Android application classification authorization method for quantitative judgment of suspicious behaviors
A technology of application classification and behavior, applied in computer security devices, instruments, digital data authentication, etc., can solve problems such as leakage of personal information, user harm, and difficulty for users to perceive malicious behavior, so as to protect private information and enhance security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
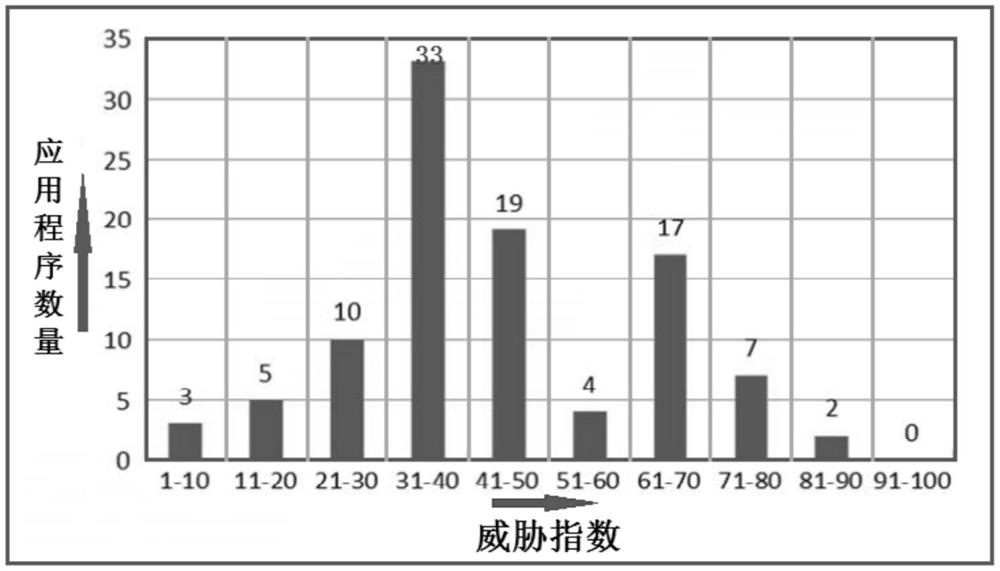
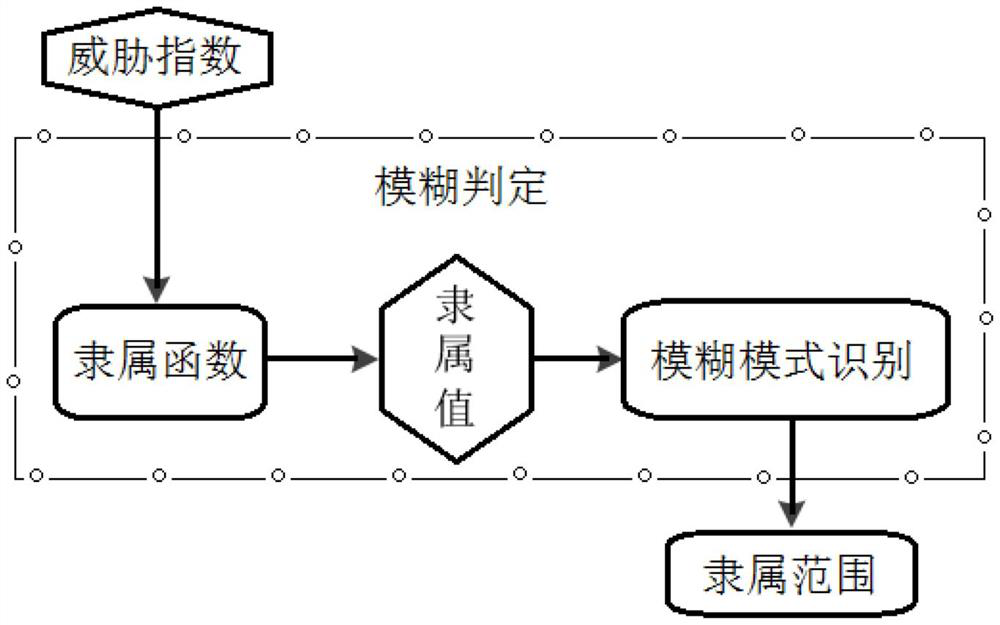
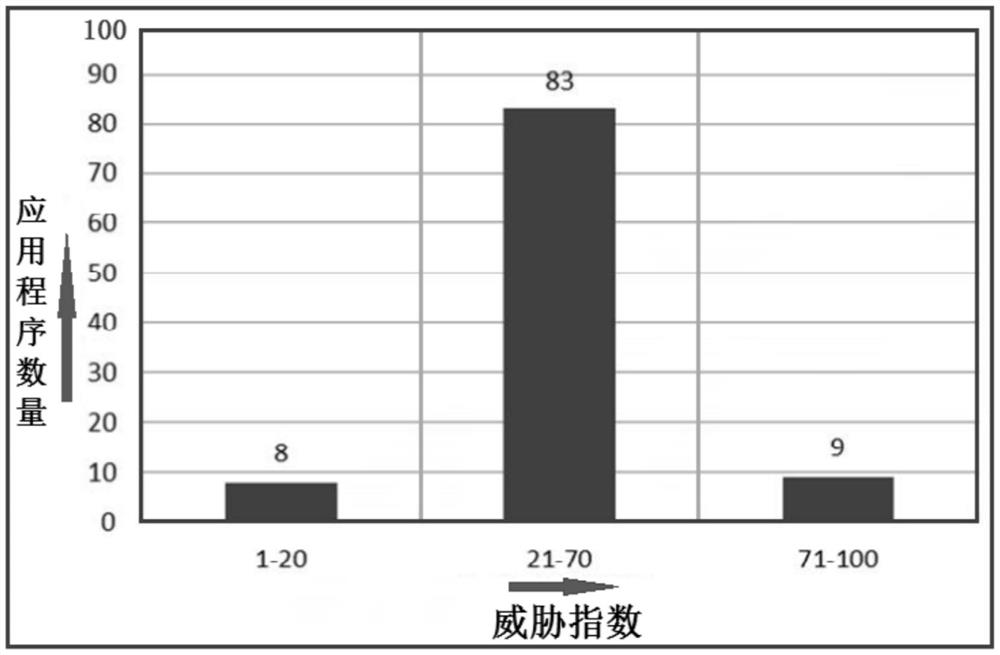
[0065] The following is a further description of the technical solution of the Android application classification and authorization method for quantitative evaluation of suspicious behavior provided by the present invention in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention and implement it.
[0066] With the rapid popularization of smart phones, all kinds of applications have begun to affect people's lives, and while the number of APPs has proliferated, the number of malicious programs is also increasing, posing a serious threat to the security and privacy of users' mobile phones. The Android system uses a set of security measures to protect the security of smartphones, and the permission system is the most important one, which restricts the access control of smartphones by granting APP permissions. However, both legitimate apps and malicious programs can obtain these permissions, making it difficult for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com